Professor Messor 2.2 | Dynamic Routing & Routing Technologies
1/15
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
16 Terms
Dynamic routing protocols
When you visit various websites, the information travels from your computer to remote servers and back through a network of routers. Each router uses routing tables to determine the next hop for your data. These tables are continuously updated through a process that involves:
Listening for Subnet Information: Routers listen to subnet information from other routers to learn about available routes.
Sharing subnet Information: They send and receive this information to and from other routers.
Determining the Best Path: Each router uses the updated information to determine the most efficient path for data transmission.
Updating available routes: Based on the gathered data, routers update their routing tables, informing others about the routes they know.
Which routing protocol to use?
A route is a defined path that network traffic follows from its source to its destination. Routing protocols determine the best path based on different criteria. Some protocols evaluate the state of the link (such as bandwidth, delay, and reliability), while others consider the distance or hop count to the destination.
The best path is determined using a formula that calculates a metric based on these criteria. The protocol then ranks the routes from best to worst and updates the routing table accordingly.
Routing protocols must also recover and converge after network changes. Convergence time, which is the time it takes for the network to recognize and adapt to a change, can vary widely between protocols.
There are both standard and proprietary routing protocols. For instance, OSPF (Open Shortest Path First) and RIP (Routing Information Protocol) are standard protocols, while some functions of EIGRP (Enhanced Interior Gateway Routing Protocol) are proprietary to Cisco. Each protocol has its advantages and is suited to different types of network environments.
Distance-vector routing protocols
Determine what the best route might be based on how far away a particular connection is. They pass information between routers, including network details and the number of "hops" away another network is. The deciding "vector" in these protocols is the distance, typically measured in hops. Usually require little configuration and are good for smaller networks but do not scale well to larger networks. Examples include RIP (Routing Information Protocol), which is a standard protocol, and EIGRP (Enhanced Interior Gateway Routing Protocol), which is a Cisco proprietary protocol.
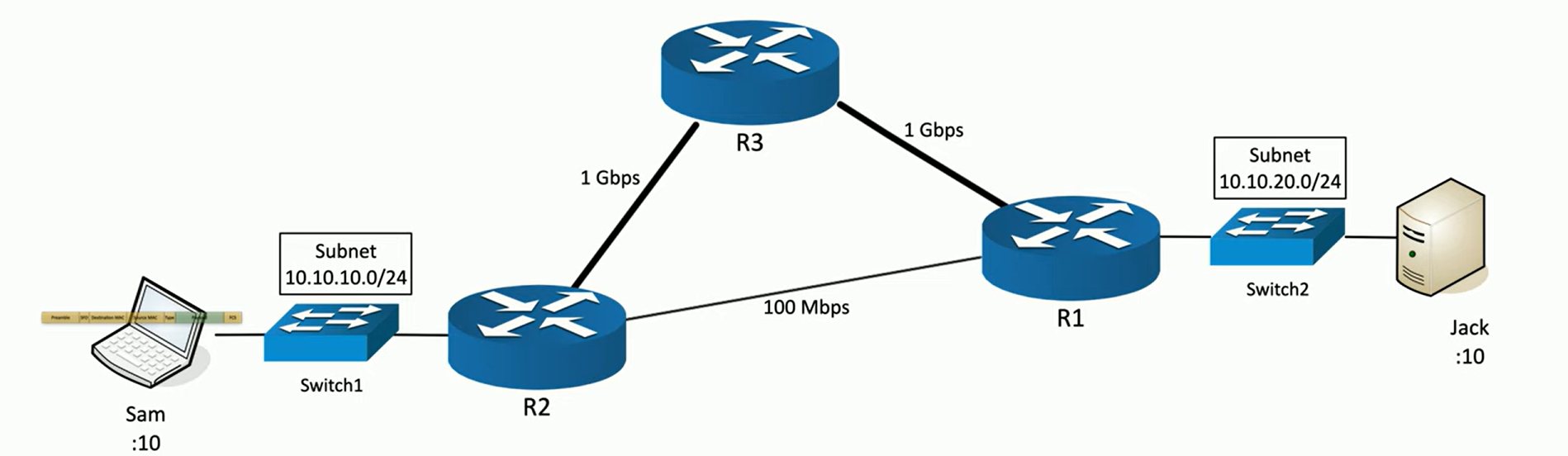
Distance vector routing example
Imagine we have Sam on one side of the network, and Sam wants to send some traffic to Jack. There are a couple of different paths the traffic could take. It could go through R2 and then directly to R1, which then sends the traffic to Jack. This connection has a 100-megabit per second link.
The primary criteria are the number of hops, or the distance. Since the shortest number of hops to communicate between Sam and Jack is two hops (via R2 to R1), the protocol will choose this path.
Link-state routing protocols
Operate by sharing information between routers about the current state of their connections. If a link is operational, the router will consider it as a viable path; if a link is down, the path is no longer viable. Takes into account the speed of the connection, favoring faster links when determining the best route.
These protocols are highly scalable and are particularly well-suited for large networks. One of the most common link-state routing protocols is OSPF (Open Shortest Path First). OSPF efficiently handles large and complex networks.
Link-state routing example:
Even though there are more hops via R3, the faster links (1 gigabit per second) make this route more desirable than the direct but slower R2 to R1 connection (100 megabits per second).
Hybrid routing protocols:
Combine elements of both link-state and distance-vector routing protocols. They incorporate aspects such as the best path determination based on distance and the state of the link. A notable example of a is BGP (Border Gateway Protocol).
Routing tables
Are crucial for determining the path that packets should take across a network. Essentially, they act as a list of directions for your packets, providing a set of rules that guide data from one point to another. Each one contains many possible routes to a destination, and as packets move through the network, they stop at every router to check this for the next hop. These tables are not only found in routers but also in workstations and other network devices.
The hop
Refers to each time a packet passes through a router on its way to its destination. The "next BLANK" is the address of the next gateway that the packet should be sent to. Routers don't need to know the entire path to the final destination; they only need to know the next BLANK keep the packet moving in the right direction.
Routers use a default route to handle packets destined for addresses not specifically listed in their routing tables. This default route acts as a catch-all, ensuring that packets have a way out of the local network when no explicit path is defined.
To prevent packets from looping indefinitely, the Internet Protocol (IP) includes a "Time to Live" (TTL) field in IPv4 and a "hop limit" in IPv6.
Configuring the next hop
Each router in a network must know where to send traffic, ensuring that packets can reach their destination efficiently. When a packet arrives at a router, the router examines its routing table to determine the next hop for that packet. If a router is configured with an incorrect next hop, it will lead to routing problems, potentially causing data to be sent in the wrong direction.
An incorrect next hop can also create routing loops, where packets circulate endlessly between routers. Routing loops are typically easy to detect because they result in network performance issues or packet loss.
Default routes
Are used by routers when no other specific route in the routing table matches the destination of a packet. Often referred to as the "gateway of last resort", provides a fallback path for traffic that cannot be directed based on more specific routes.
Is represented by the destination 0.0.0.0/0, which matches any destination IP address not explicitly listed in the routing table. This configuration greatly simplifies routing. Works in conjunction with all other routing methods.
Routing metrics
Each routing protocol—such as RIPv2, OSPF, or EIGRP—employs its own method for calculating and assigning metric values, which are used to evaluate and select the optimal route.
When multiple paths exist between two points, the routing protocol uses these metrics to decide which path to use. We usually choose the lowest metric, I.E 1 is better than 2.
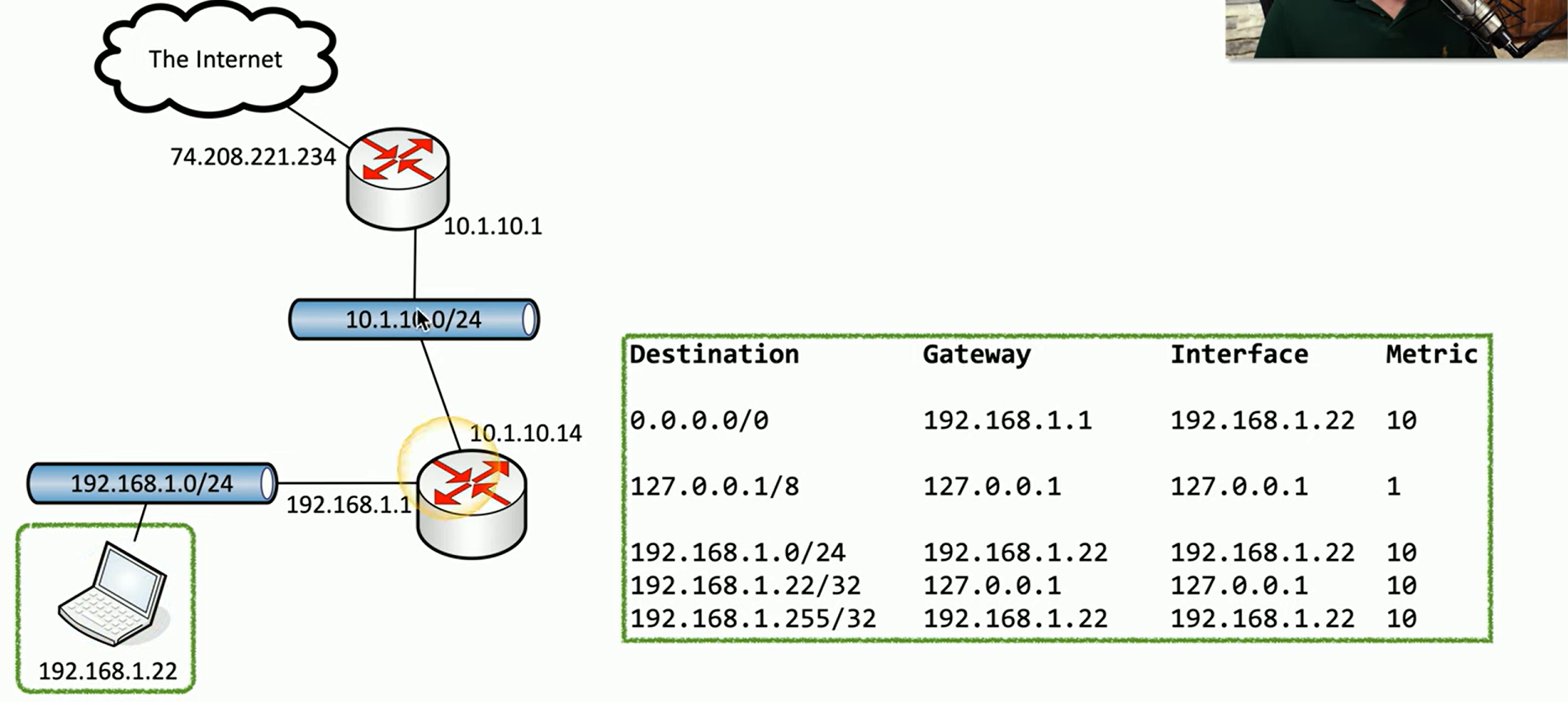
Routing table example
In a network diagram involving a laptop and two routers, each device has its own routing table, which plays a crucial role in determining how data packets are forwarded.
For the laptop with the IP address 192.168.1.22, which is on the 192.168.1.0/24 network, its routing table includes several key entries:
Local Network Routes: The routing table lists specific routes for local network traffic, including the exact IP address of the laptop itself (192.168.1.22/32) and the broadcast address (192.168.1.255). Traffic destined for these addresses remains within the local network.
Loopback Route: There is a route for the loopback address 127.0.0.1/8, which is used for internal testing and communication within the laptop itself.
Default Route: The default route, represented as 0.0.0.0/0, is used for any destination not explicitly listed in the routing table. This route is crucial for reaching external networks. Traffic matching this route is sent to the gateway address 192.168.1.1, which is the router interface connected to the laptop.
When the laptop needs to send data, it consults the routing table to determine the most specific route. For example, if the traffic is destined for an IP address within the 192.168.1.0/24 network, it uses the local network routes. If the destination is outside this network and not listed in the table, the laptop defaults to the route with 0.0.0.0/0, forwarding the traffic to the router at 192.168.1.1. The traffic then exits the laptop’s interface at 192.168.1.22, heading towards the router for further processing.
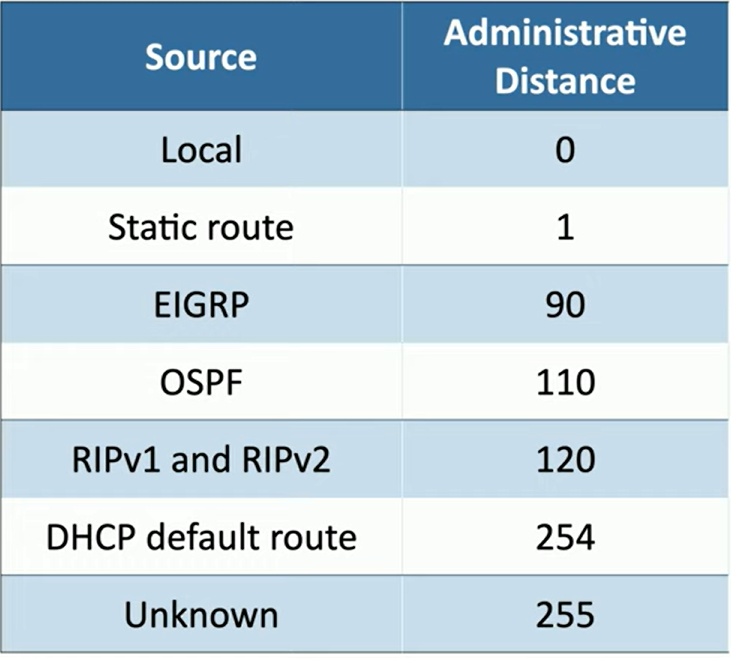
Administrative distances
This situation often arises in complex networks where different routing protocols are employed for various purposes, such as using OSPF (Open Shortest Path First) internally and BGP (Border Gateway Protocol) externally.
To resolve this, BLANK come into play as a tiebreaker to determine which routing protocol has priority.
Managing Network Utilization
In a typical network, you'll have a variety of devices such as desktops, laptops, VoIP phones, and mobile devices, all of which generate different types of traffic. Applications running on these devices can range from mission-critical systems to streaming media, each with its own network requirements.
You need to prioritize traffic based on its importance and performance needs. For example, VoIP calls are real-time applications that require low latency and minimal jitter to maintain call quality. On the other hand, streaming video or audio, which can buffer, is less sensitive to delays and can tolerate some fluctuation in network performance.
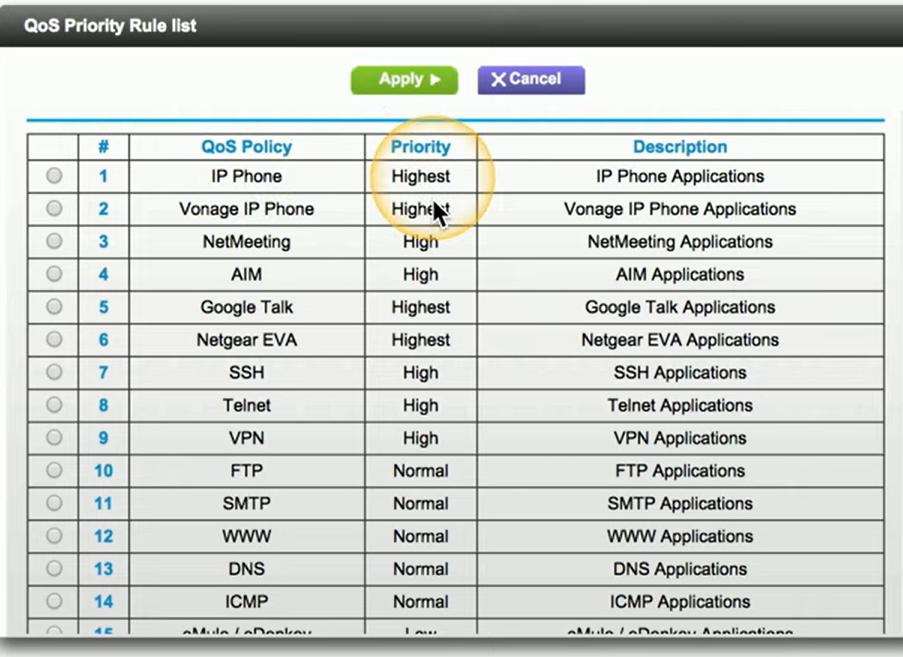
Traffic shaping
Also known as packet shaping, is a technique used to manage network traffic by controlling bandwidth usage and data rates. This process allows you to set priorities for different applications, ensuring that critical applications receive higher priority and sufficient bandwidth compared to less important ones.
Key component in managing Quality of Service (QoS), which aims to optimize network performance and user experience.