3.5- Fundamentals of Computer Networks
1/62
Earn XP
Description and Tags
computer science
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
63 Terms
What is a network?
A series of computers and other devices that are connected together and can share data resources.
What are the advantages of networking
Sharing resources
Files can be stored on centralised servers and be accessed by anyone authorised
peripheral devices like printers can be shared
internet connection can be shared
Centralised management
User profiles and security can be managed centrally
Software can be distributed across the network rather than onto to each computer individually
All files can be backed up onto a central server
What is the internet?
An international collection of networks.
What is the World Wide Web?
A collection of websites and other resources.
What is Packet Switching?
When messages are broken down into small data packets and sent individually across a network and reassembled at the receiving end.
What is a Domain Name System (DNS)?
A system where a web address is translated into an IP address.
What are DNS servers?
A collection of web addresses and their associated IP addresses. There are 13 Root DNS Servers worldwide.
What is an IP Address?
The identifier of a network connected device that allows the device to communicate across the Internet. 2 Types: IPv4 (192.168.0.1) and IPv6.
What is a MAC Address
A unique identifier of a Network Interface Card. It is used to assist with packet switching.
What is a Network Interface Card (NIC)?
Allows you to connect to a network. Can be used to connect to a wired or wireless network.
What is a Router?
A device that sends data packets on their way in the best direction.
What is a switch?
A device that sends packets to its intended recipient using the recipient's MAC Address.
What is Wi-Fi?
A way of connecting to a network wirelessly using radio waves. This is normally susceptible to interference from objects and other nearby devices. Wifi is a trademark name for a family of related protocols for a WLAN
What is a Wireless Access Point?
A device that allows wireless devices to connect to a wired network using Wi-Fi. These are normally integrated into the Router but can be a standalone device.
What is a WAN (Wide Area Network)?
Cover a wide geographical area
Often under collective or distributed ownership.
The biggest example of a WAN is the internet
What is a LAN network (Local Area Network)?
Cover a relatively small geographical area
These are often owned and controlled/managed by a single person or organisation.
Have less users than WANs
What is a Personal Area Network (PAN)?
Centred around a single user or device
Limited area- around 10m
What is Bandwidth?
The amount of data that can be carried at any one time.
What is Latency?
The time delay of transmitted data travelling from the sender to the recipient.
What is a Star Topology?
Each device has its own connection to the central switch
Switch routes transmission to devices using their MAC address
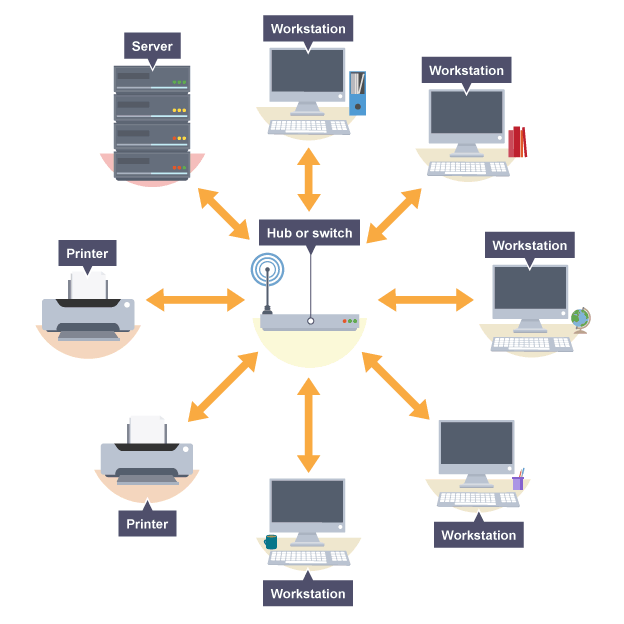
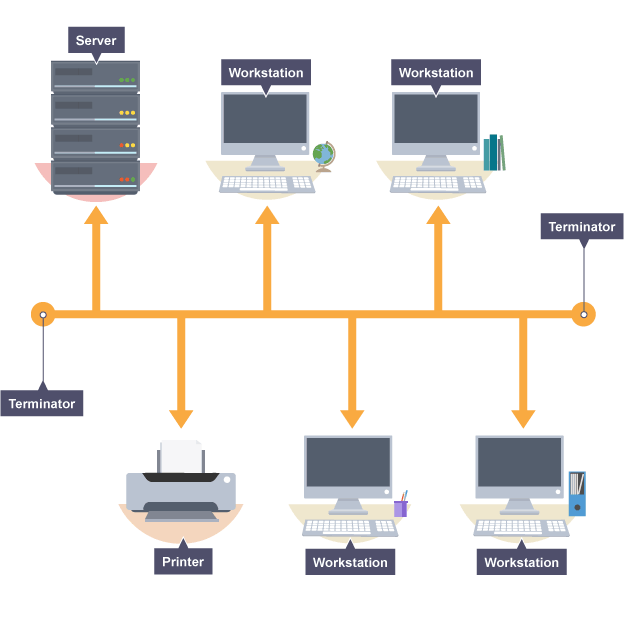
What is a Bus Topology?
All signals transmitted through the central backbone
Terminators on either end to prevent stray signals bouncing back down the cable
Advantages of Bus over Star
Cheaper as there is significantly less cabling
Simpler to install
Advantages of Star over Bus
If the main cables breaks on a bus, the whole network goes down, while this will not happen in star
As more users are added to bus, performance of the network depletes, as there will be more data collisions, as data will travel in both directions on the network, meaning data will have to be retransmitted; this does not happen on star as each device has its own connection and packets will be routed by the switch
Greater security risk as all devices on a bus network can see all the data being transmitted across it, while this doesn’t happen on star
What is a Fiber Optic Cable?
Uses light waves transmitted in a glass tube to transmit data.
What are Copper cables?
Uses electrical signals transmitted in a wire to transmit data
Used in ethernet cables
Vulnerable to electromagnetic interference
What is needed to connect to a wireless network
NIC (Network Interface Card)
Advantages of Wired over Wireless
Faster and more consistent transmission
While copper cables can be susceptible to electromagnetic interference, fibre optic cables can avoid this, and prevent interference for higher quality transmission- wireless can have signal reduced by walls and other wireless devices
Maintains a good strength for longer (especially if fibre optic is used)- wireless have a limited area and require repeater devices to expand the range
Cannot be easily intercepted- without encryption wireless can be easily intercepted
Advantages of wireless over wired
Cheaper to add a new device, as no new additional cabling required
Easier to add new devices as no new cabling required
What is a Network Protocol?
A set of rules that allows devices to communicate on a network
What is Ethernet?
A family of standard local network protocols.
What is Tethering?
Linking devices using Bluetooth by creating a PAN.
What is Authentication?
Verifying that a user is allowed to access content on a device.
What is Encryption?
Encoding of data so it can no longer be easily read (Plaintext to Ciphertext)
What is Plaintext?
The message that the user wants to encrypt.
What is Ciphertext?
The encrypted data.
What is a Key?
A sequence of numbers used to encrypt and decrypt data.
What is an Encryption Algorithm?
The formula used to encrypt the plaintext.
What is Symmetric Encryption?
A single key is used to encrypt and decrypt data.
What is an Asymmetric Encryption?
Two keys are used to encrypt and decrypt the data.
What is a Public Key?
The key used to encrypt the data. This is normally made publicly available.
What is a Private Key?
The key used to decrypt the data. This is normally kept with the recipient.
What is a Caesar Cipher Shift?
A method of encryption involving moving positions left and right.
What is Cryptanalysis?
The objective of trying to decode the ciphertext. This is normally found by finding out the key.
What is a Brute Force Attack?
A method of cryptanalysis where every possible key is tried until the correct key is found and the message can be decrypted
What is the Key Strength?
2^no of bits
What is frequency analysis?
Using how common letters are to decrypt messages.
What are Wireless Encryption Standards?
A method of encrypting wireless broadcasts while data is being transmitted. There is 2 common types: WEP and WPA
What is a Firewall?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
What is MAC Address Filtering?
MAC address filtering allows devices to access, or be blocked from accessing a network based on their physical address embedded within the device’s network adapter- blocks based on the NIC
What is HTTP?
HyperText Transfer Protocol
Provides a way for users to interact with web resources. Transmits messages between client and server using hypertext
What is HTTPS?
HyperText Transfer Protocol Secure
A secure protocol that encrypts information transmitted when on the internet so it can't be hacked.
HTTPS is an extension of HTTP and allows secure transfer of data between a browser and a website by encrypting data. The web browser will check the website server’s security certificate and ensure it is legitimate. This means it’s not possible to see or eavesdrop on what you’re browsing or for your data to be stolen
What is FTP?
File Transfer Protocol
Allows secure transfer of files between client and server.
Files are uploaded to and downloaded from the server using FTP.
What is a Simple Mail Transfer Protocol (SMTP)
Enables users to send (and receive) email messages. Initiates sessions between user and mail server.
Server then forwards messages.
Uses a process called ‘store and forward’ to store messages and forward as necessary.
The server decides which server to send the message to and the inbox provider then downloads the message and places it in the recipient’s inbox.
Often used in conjunction with IMAP
What is IMAP
Internet Mail Access Protocol
Stores email messages on an ISP server but allows user to manipulate messages as though on a local device.
Local devices access the ISP server to access the messages.
IMAP works with desktop clients and webmail clients.
Allows simultaneous logins from different devices to one account
What is POP3?
Post Office Protocol
A protocol used to receive emails. It downloads the entire message to the device and removes the email from the server.
What is a User Datagram Protocol?
Communications protocol that establishes low latency and loss- tolerating connections between applications.
Enables the transfer of data before an agreement is provided by the receiving party.
This speeds up transfers.
Continuous flow of data without checking for lost packets
What is transmission control protocol
Connects network devices to the Internet. It defines how applications can create channels of communication across a network.
It manages how a message is assembled into smaller packets before transmission and reassembles packets in the correct order at destination.
It checks to make sure all the packets have arrived and if not sends a message to resend the lost packets
What is internet protocol (IP)?
Relays data across network boundaries.
It defines how to address and route each packet to make sure it reaches the right destination.
What is a TCP/IP Stack
Defines how different protocols operate to pass data packets across a network.
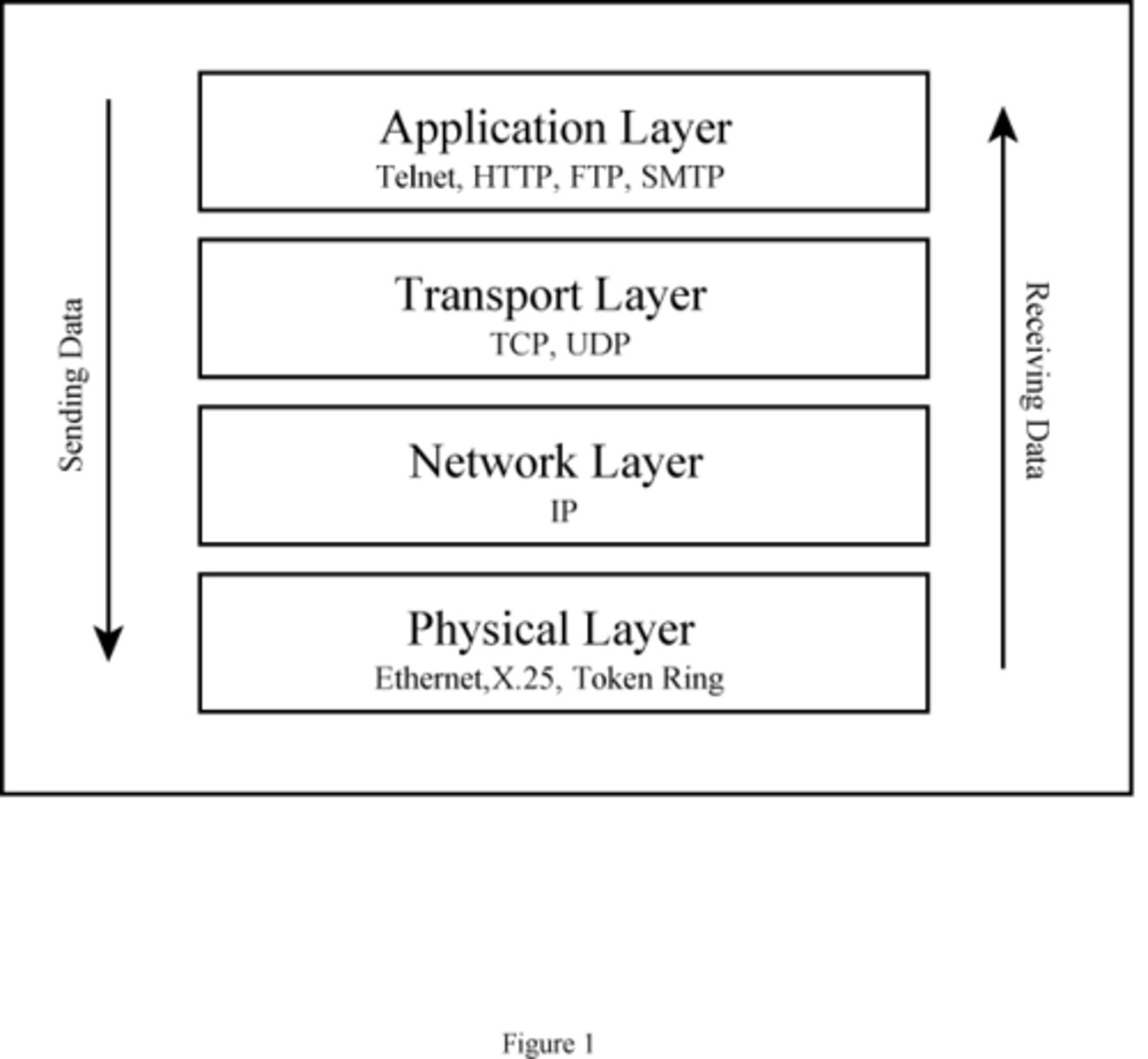
What is the application layer?
The layer that selects the correct protocol to use depending on the application in use and what you are trying to do.
This is where the network applications, such as web browsers or email programs, operate.
HTTP, HTTPS SMTP, IMAP and FTP protocols operate in this layer.
What is the transport layer?
The layer that creates the connection between the 2 hosts,
Agrees the communication settings such as the size of the packets.
Reassembles the packets at the other end
Sends messages to resend any lost packets
TCP and UDP operate in this layer.
What is the internet layer?
Addresses and packages data for transmission.
Routes the packets across the network.
IP operates in this layer.
What is the Link layer?
The layer that is the physical hardware that connects the 2 hosts together.
This is where the network hardware such as the NIC (network interface card) is located. OS device drivers also sit here.