8.4
1/14
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
15 Terms
Howard is a security analyst working with an experienced computer forensics investigator. The investigator asks him to retrieve a forensic drive controller, but Howard cannot locate a device in the storage room with this name.
What is another name for a forensic drive controller?
Write blocker
Jasper Diamonds is a jewelry manufacturer that markets and sells custom jewelry through its website. Bethany is the manager of Jasper's software development organization, and she is working to bring the company into line with industry-standard practices. She is developing a new change management process for the organization and wants to follow commonly accepted approaches.
Bethany would like to put in place controls that provide an organized framework for company employees to suggest new website features that her team will develop.
What change management process facilitates this?
Request control
Jasper Diamonds is a jewelry manufacturer that markets and sells custom jewelry through its website. Bethany is the manager of Jasper's software development organization, and she is working to bring the company into line with industry-standard practices. She is developing a new change management process for the organization and wants to follow commonly accepted approaches.
Bethany would also like to create a process that helps multiple developers work on code at the same time.
What change management process facilitates this?
Change control
Jasper Diamonds is a jewelry manufacturer that markets and sells custom jewelry through its website. Bethany is the manager of Jasper's software development organization, and she is working to bring the company into line with industry-standard practices. She is developing a new change management process for the organization and wants to follow commonly accepted approaches.
Bethany is working with her colleagues to conduct user acceptance testing.
What change management process includes this task?
Release control
Jasper Diamonds is a jewelry manufacturer that markets and sells custom jewelry through its website. Bethany is the manager of Jasper's software development organization, and she is working to bring the company into line with industry-standard practices. She is developing a new change management process for the organization and wants to follow commonly accepted approaches.
Bethany noticed that some problems arise when system administrators update libraries without informing developers.
What change management process can assist with this problem?
Configuration control
Place the list of disaster recovery test types in order of their potential impact on the business, starting with the least impactful and progressing through the most impactful.
Checklist review
Parallel test
Tabletop exercise
Full interruption test
1, 3, 2, 4
What step is missing from the IR process cycle diagram shown here?
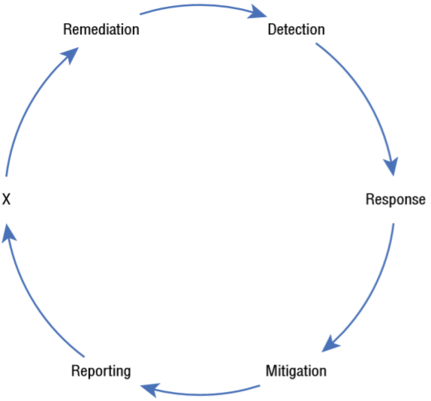
Recovery
Megan wants to ensure that the new software as a service provider that her company is signing a contract with will make sure the service works all the time without disruptions.
Which of the following is often part of contracts to provide that assurance?
SLA
Norm would like to conduct a disaster recovery test for his organization and wants to choose the most thorough type of test, recognizing that it may be quite disruptive.
What type of test should Norm choose?
Full interruption test
Tammy is selecting a disaster recovery facility for her organization. She would like to choose a facility that balances the time required to recover operations with the cost involved.
What type of facility should she choose?
Warm site
Some adversaries use DoS attacks as their primary weapon to harm targets, whereas others may use them as weapons of last resort when all other attempts to intrude on a target fail.
Which of the following is most likely to detect DoS attacks?
Network-based IDS
Unfortunately, attackers have many options of attacks to perform against their targets.
Which of the following is considered a denial-of-service (DoS) attack?
While surfing the web, sending to a web server a malformed URL that causes the system to consume 100 percent of the CPU
Which type of firewall automatically adjusts its filtering rules based on the content and context of the traffic of existing sessions?
Stateful inspection
Collusion is when two or more people work together to commit a crime or violate a company policy.
Which of the following is not a defense against collusion?
Group user accounts
Any evidence to be used in a court proceeding must abide by the Rules of Evidence to be admissible.
What type of evidence refers to written documents that are brought into court to prove a fact?
Documentary