Computer Architectures II
1/99
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
100 Terms
T/F: Compilers perform the translation of a program written in high-level language, such as C++ or Java into instructions that the hardware can execute
True
T/F: Assembly language is another name of machine language.
False
T/F: A high-level programming language is portable language such as C++ or Java that is composed of words and algebraic notation that can be translated by a compiler into assembly language.
True
T/F: A datapath is the component of the processor that performs arithmetic operations.
True
T/F: A control is the component of the processor that commands the datapath, memory, and I/O devices according to the instructions of the program.
True
T/F: Dynamic random access memory (DRAM) is a memory built as an integrated circuit; it provides random access at any location.
True
T/F: Static random access memory (SRAM) is a memory built as an integrated circuit, but faster and less dense than DRAM.
True
Instruction set architecture (ISA) is an abstract interface between the:
(a) Compiler and assembler.
(b) Hardware and the lowest-level software.
(c) Operating system and the user-program.
(d) Internet and the CPU.
(b) Hardware and the lowest-level software
Application binary interface (ABI) is the user portion of the instruction set plus the operating system interfaces used by:
(a) application programmers
(b) the compier
(c) the operating system
(d) none of the above
(a) application programmers
The main memory or the primary memory is the memory that is used to hold programs while they are:
(a) terminated.
(b) running
(c) queued.
(d) None of the above.
(b) running
Yield is the percentage of good dies from the total number of dies on:
(a) the chip
(b) the computer
(c) the wafer
(d) None of the above
(c) the wafer
CPU execution time for a program is equal to CPU clock cycles for a program divided by:
(a) clock cycle
(b) clock rate
(c) instruction count
(d) None of the above
(b) clock rate
T/F: The term clock cycles per instruction (CPI) is the average number of clock cycles each instruction takes to execute.
True
T/F: The compiler's role can be very simple and can hardly affect the CPI in any ways.
False
T/F: Asserted and deasserted signals are not always complementing each other.
False
T/F: Truth table can completely describe any sequential logic function.
False
T/F: In Boolean algebra, all variables have the values 0 or 1 and, in typical formulations, there are only two operations.
False
T/F: NOR and NAND gates are inverted OR and AND gates.
True
T/F: Multiplexer can have only two inputs and one output since its output is one of the inputs that is selected by a control.
False
T/F: The logical representation that employs a logical OR in terms joined using the AND operator is called Sum of Product.
True
T/F: Clocks are needed in sequential logic to decide when an element that contains state should be updated.
True
T/F: ALU is the device that can only perform the arithmetic operation like addition and subtraction and Logic gates the components can perform logical operations like AND and OR.
False
T/F: In edge triggered methodology either the rising edge or the falling edge of the clock is active and cause state changes to occur.
True
How many voltage levels are there in digital electronic?
(a) Five
(b) Two
(c) Four
(d) Eight
(e) All of the above
(b) Two
Logic blocks without memory are called:
(a) Deasserted
(b) Asserted
(c) Combinational
(d) Complementary
(e) All of the above
(c) Combinational
The result of NOT operator is 1 only if the input is:
(a) Asserted
(b) Sequential
(c) Logical
(d) Deasserted
(e) All of the above
(d) Deasserted
Which of the following gates are called universal gates?
(a) OR and NOR
(b) AND and OR
(c) AND and NAND
(d) NAND and NOR
(e) OR and NAND
(d) NAND and NOR
The computer ___________ provides a continuous stream of pulses to the computer processor.
(a) clock
(b) storage
(c) network
(d) None of the above
(a) clock
T/F: A latch is a temporary storage device that has two stable states (bistable).
True
T/F: A control signal is a signal that is used for multiplexor selection or for directing the operation of a functional unit.
True
T/F: Datapath is the hardware that performs all the required operations, for examples ALU, registers, and internal buses.
True
T/F: A program counter (PC) is only incremented after an arithmetic-logical instruction.
False
T/F: The register file (RF) is a hardware device that has one read port and two write ports.
False
T/F: The register number inputs are 6-bits wide to specify one of the 32 registers.
False
T/F: When the RegWrite is deasserted, data can be read or written on the WriteData input.
False
T/F: After an instruction fetch program counter always incremented by 1.
True
T/F: In case of branch taken, the branch target address becomes the new PC.
True
T/F: The value stored into a destination register comes from the ALU for R type instructions and load instruction.
False
T/F: The store instruction moves a word into a register from memory, and the load instruction moves word from a register into memory.
False
How many outputs are there in the Register File?
(a) 2
(b) 4
(c) 6
(d) 8
(a) 2
Which one of the following is correct for a load instruction?
(a) MemtoReg should be reset to cause the instruction from CPU to be received from the register file.
(b) MemtoReg should be set to cause the correct register destination to be sent to the register file.
(c) MemtoReg should be set to cause the data from memory to be sent to the register file.
(d) We do not care about the setting of MemtoReg for loads.
(c) MemtoReg should be set to cause the data from memory to be sent to the register file.
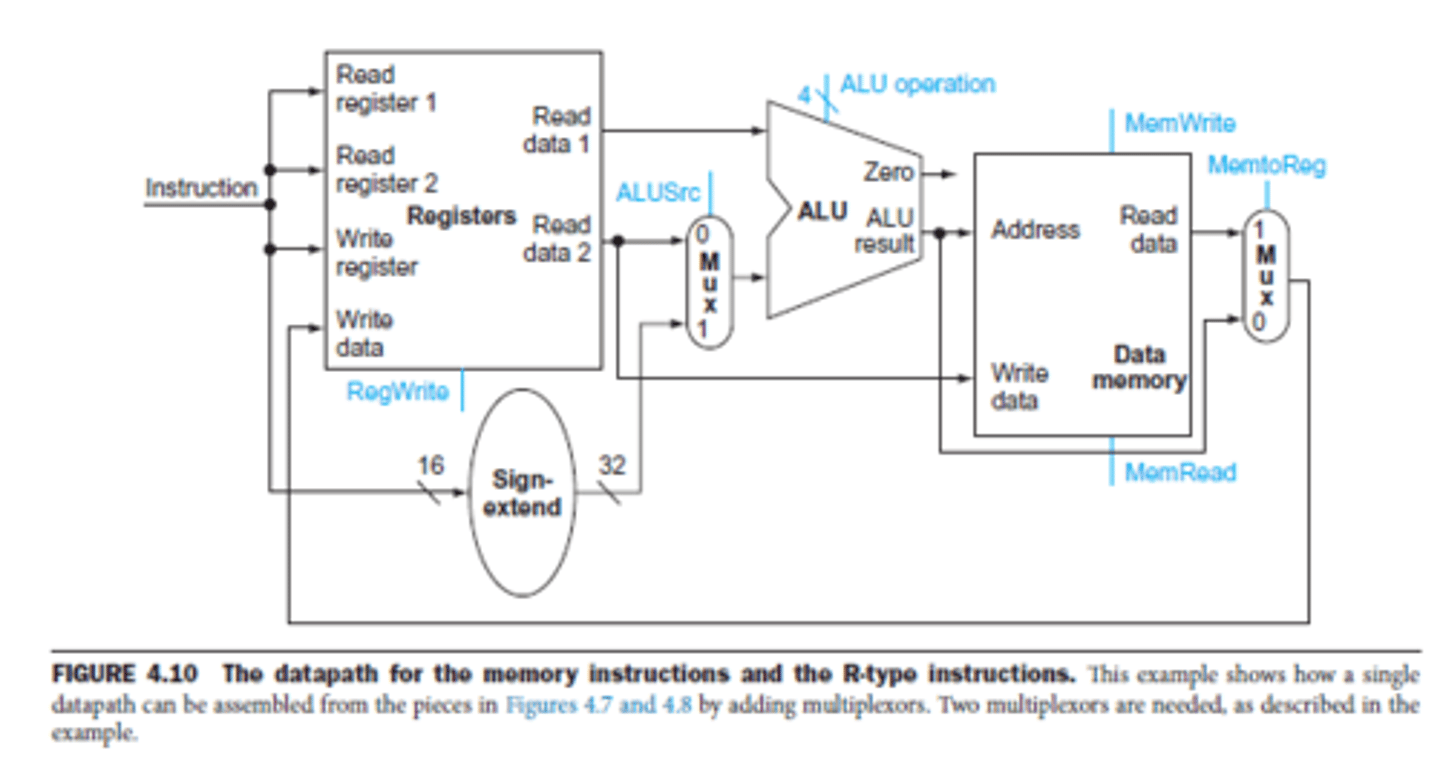
The memory instructions use the ________ to do the address calculation.
(a) Adder
(b) ALU
(c) Register
(d) Multiplexer
(b) ALU
The arithmetic-logical instructions use the ALU, with the inputs coming from
(a) 2 registers
(b) 3 registers
(c) 4 registers
(d) 6 registers
(a) 2 registers
T/F: Suppose a CPU contains 8 registers. Within a machine-language instruction, at least 3 bits would be required to uniquely identify one of the registers.
True
T/F: For load word and store word instructions, we use the ALU to compute the memory address by adding destination register value.
False
T/F: A don't-care term in a truth table indicates that the output does not depend on the value of the input corresponding to that column.
True
T/F: The opcode for R-Format instructions is always 0.
True
T/F: We can generate the 3-bit ALU control input using a small control unit.
False
T/F: The two source registers are always specified by the rs and rd fields, at positions 25:21 and 20:16 for the R-Type instructions.
False
T/F: The 16-bit off set for branch equal instruction and R format instruction is always in position 15:0.
False
T/F: We can only write on register file when data is available at write data port and RegDst is asserted and MemWrite is asserted.
False
T/F: The jump instruction looks somewhat like a branch instruction but computes the target PC differently.
True
T/F: The PC does not require a write control since it is written once at the end of every clock cycle.
True
For the R-type instructions, the ALU has to perform one of the five actions (AND,OR, subtract, add, or set on less than), depending on the value of ________.
(a) the 6-bit opcode
(b) the 5-bit source register rs
(c) the 5-bit destination register rd
(d) the 6-bit funct field
(d) the 6-bit funct field
For evaluating branch equal result, the ALU must perform a ________ operation.
(a) addition
(b) subtraction
(c) multiplication
(d) division
(b) subtraction
The value of 2 bit ALU op for R-format instruction is:
(a) 00
(b) 01
(c) 10
(d) 11
(c) 10
Shift left 2 is important in the calculation of PC value in a __________ instruction.
(a) load
(b) store
(c) branch
(d) add
(c) branch
The single-cycle design will work correctly, but it would not be used in modern designs because it is _________.
(a) slow
(b) error-prone
(c) inefficient
(d) hard to implement in hardware
(c) inefficient
T/F: The pipelining would decrease the time to complete an instruction on the datapath.
False
T/F: The situations in pipelining is called clock-cycle error then the next instruction cannot execute in the following clock cycle.
False
T/F: MIPS instruction set was designed to be pipelined, making it fairly easy for designers to avoid structural hazards.
True
T/F: Data hazards occur when the pipeline must be stalled because one step must wait for another to complete.
True
T/F: Pipeline stall is also called bubble. A stall initiated in order to resolve a hazard.
True
T/F: Load-use data hazard is a specific form of data hazard in which the data being loaded by a store instruction has not yet become available when it is needed by another instruction.
False
T/F: The shading on the right half of the register file or memory means the element is written in that stage, and shading of the left half means it is read in that stage.
False
T/F: Forwarding cannot prevent all pipeline stalls.
True
T/F: Branch prediction is a solution of control hazard.
True
MIPS instruction set architecture was designed for pipelined execution because:
(a) MIPS instruction are the same length
(b) MIPS has only a few instruction formats
(c) Memory operands in MIPS only appear in loads and store
(d) All of the above
(d) All of the above
Data hazards can be resolved by _________.
(a) forwarding
(b) bypassing
(c) reordering code
(d) all of the above
(d) all of the above
Control hazards are also called __________ hazards.
(a) load
(b) store
(c) branch
(d) jump
(c) branch
A method of resolving a data hazard by retrieving the missing data element from internal buffers rather than waiting for it to arrive is called __________.
(a) register retrieving
(b) bypassing
(c) data mining
(d) memory research
(b) bypassing
ALU operations always take place in _________ stage of instruction cycle.
(a) EX
(b) ID
(c) IF
(d) all of the above
(a) EX
T/F: Pipelining is a technique that exploits parallelism among the instructions in a sequential instruction stream.
True
T/F: Pipelining does reduce the time it takes to complete an individual instruction, also called latency.
False
T/F: The division of an instruction into n-stages means n-stage pipeline.
True
T/F: Each step of the instruction can be mapped onto the datapath from right to left, however two exceptions to this.
False
T/F: The pipeline registers separate each pipeline stage. They are labeled by the stages that separate them.
True
T/F: The memory access stage is only active in load instruction.
False
T/F: Allowing jumps, branches, and ALU instructions to take fewer stages than the five required by the load instruction will increase pipeline performance under all circumstances.
False
T/F: The pipeline registers are updating during each clock cycle in pipelined approach.
True
T/F: The ALU control is only operated by 2 bits ALU op for all MIPS instructions.
False
T/F: In a single-cycle implementation, we assume that the PC is written 6 times in each clock cycle.
False
Only control lines that are set in memory access stage are:
(a) MemRead, MemWrite, and RegWrite
(b) MemRead, MemWrite, and Branch
(c) MemWrite, MemRead, and RegDst
(d) Branch, MemRead and RegWrite
(b) MemRead, MemWrite, and Branch
The registers must be wide enough to _____________.
(a) store only 32-bits data
(b) store all the data corresponding to the lines
(c) store only 8 bits data
(d) store only control signals
(a) store only 32-bits data
Two control lines for Write Back are ___________.
(a) MemtoReg and MemWrite
(b) MemtoReg and MemRead
(c) MemtoReg and RegWrite
(d) MemWrite and RegWrite
(c) MemtoReg and RegWrite
Execution and address calculation stage only uses 4 bits control lines that are ____________.
(a) RegDst, ALUSrc, Branch, and ALUOp
(b) ALUOp, RegDest, and ALUSrc
(c) ALUSrc, JumpTarget, ALUOp, and RegDest
(d) ALUOp, ALUSrc and RegWrite
(b) ALUOp, RegDest, and ALUSrc
T/F: Three common types of hazards are data hazards, structural hazards, and control hazards (branching hazards).
True
T/F: The control values for the last three stages are created during the instruction decode stage and then placed in the MEM/WB pipeline register.
False
T/F: Structural hazards arise because there are too many duplications of resources.
False
T/F: Data hazard is caused by data dependencies in pipelined datapath.
True
T/F: In case of branch-not-taken prediction designed processor, if branch is not taken, then our pipeline will function properly, and we have no stalls at all.
True
T/F: Target address is computed at the end of MEM stage of a branch instruction. If at the time we find out that the branch is taken, we must flush out all instructions in branch not taken prediction pipeline.
False
T/F: In MIPS architecture, a branch delay slot is filled by a bubble which does not affect the branch.
False
T/F: As a processor designer attempts to incorporate both longer pipelines and issuing multiple instructions per clock cycle in a processor, the branch delay becomes longer, and a single delay slot is insufficient.
True
Hazards are problems with the instruction pipeline when the _______ instruction cannot execute the following clock cycle.
(a) previous
(b) next
(c) first
(d) last
(b) next
Suppose processor A executes instructions in the following 4 stages IF&ID - 30ns, EX - 30ns, MEM - 40ns, WB - 20ns. The performance ratio of unpipelined vs pipelined implementation of processor A is __________. (Assuming no stalls)
(a) 5/2
(b) 3/2
(c) 3/1
(d) 4/3
(b) 3/2
How many states are there in a 2-bit prediction scheme?
(a) 2
(b) 4
(c) 8
(d) All of the above
(b) 4
Control hazards can be resolved by _______.
(a) dynamic prediction
(b) predict not taken
(c) predict taken
(d) all of the above
(d) all of the above
A small memory that contains one or more bits indicating whether the branch was recently taken or not is called ___________.
(a) branch target buffer
(b) correlating predictor
(c) tournament branch predictor
(d) branch prediction buffer
(d) branch prediction buffer
Match the words and definitions:
1. Data Hazards
2. Structural Hazards
3. Control Hazards
(a) Hardware cannot support certain combinations of instructions (two instructions in the pipeline require the same resource).
(b) Instruction depends on result of prior instruction still in the pipeline.
(c) Caused by delay between the fetching of instructions and decisions about changes in control flow (branches and jumps).
Data Hazards - (b)
Structural Hazards - (a)
Control Hazards - (c)