Chapter 5 ■ Cloud Platform, Infrastructure, and Operational Security
1/20
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
21 Terms
Improving practices
Charles is working with internal auditors to review his organization’s cloud infrastructure. Which of the following is not a common goal of internal audits?
Geofencing
Maria’s organization wants to ensure that logins by most malicious actors would be prohibited if a system administrator’s credentials were compromised. What technology is commonly used to check for potential malicious logins from international attacks?
Disk or volume encryption
Alaina wants to ensure that her system instances for a web application hosted in her cloud data center have proper security for data at rest. What solution should she select to help ensure this?
Hashing
Jason wants to validate that the open-source software package he has downloaded matches the official release. What technique is commonly used to validate packages?
A security baseline
Naomi’s organization has adopted the CIS security controls for Windows. What type of solution have they adopted?
Dedicated hardware instances
Yarif’s organization wants to process sensitive information in a cloud environment. The organization is concerned about data throughout its lifecycle. What protection should it select for its compute elements if security is a priority and cost is less important?
Removing anti-malware agents
Valerie’s organization uses a security baseline as part of its systems configuration process. Which of the following is not a typical part of a baselining process?
Use end-to-end encryption for all communications.
Hrant wants to ensure that traffic inside of his organization’s Azure Virtual Network (VNet), Azure’s basic building block for customer IaaS instances, is secure. What should he do to protect it?
A snapshot
Asha is configuring a virtualized environment and wants to back up a virtualized server, including its memory state. What type of backup should she perform?
Operating system logs
Felix is planning for his organization’s third-party audit process after recently switching to a cloud SaaS provider. What information will Felix most likely be unable to provide?
Maintenance
Mark has set up a series of tasks that make up a workflow to ensure that his cloud-hosted web application environment scales, updates, and maintains itself. What cloud management plane feature is he leveraging?
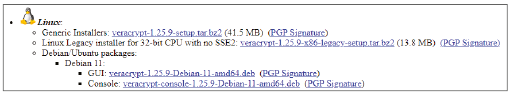
VeraCrypt’s public key
Amanda downloads VeraCrypt, a free, open-source disk encryption software package. When she downloads the software, she sees the following information on the downloads page:
What will she need to validate the signature and ensure that the software is legitimate?
A bastion host
Ting sets a system up in her Amazon VPC that exists in a low-security, public internet–facing zone and also has an interface connected to a high-security subnet that is used to house application servers so that she can administer those systems. What type of security solution has she configured?
Control of the underlying host operating system
Lisa’s organization installs virtualization tools on each virtual machine it sets up. Which of the following is not a common function of virtualization tools?
Type 1
Susan’s organization is a cloud service provider that runs its hypervisor directly on the underlying hardware for its systems. What type of hypervisor is Susan running?
Audits may disrupt their other customers or lead to risks of data exposure for those customers.
The CIO of Gurvinder’s company wants him to have its audit company perform an audit of its cloud infrastructure provider. Why are cloud infrastructure vendors unlikely to allow audits of their systems and infrastructure by customer-sponsored third parties?
HSM as a service
Michelle wants to securely store her organization’s secrets using a cloud service. What tool should she select?
Security groups
Helen wants to apply rules to traffic in her cloud-hosted environment. What cloud tool allows rules permitting traffic to pass or be blocked to be set based on information like the destination or source host or IP address, port, and protocol?
A honeypot
Jaime wants to set up a tool that will allow him to capture and analyze attacker behavior, including command-line activity and uploaded toolkits targeted at systems in his environment. What type of tool should he deploy?
Zero-day exploits
Chris is using a third-party vulnerability scanning application in his cloud-hosted environment. Which of the following issues is he unlikely to be able to detect with a vulnerability scanner?