Business Continuity 1
1/44
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
45 Terms
Risk
An uncertain event that, if it occurs, has a positive or negative impact on objectives
Risk Management
A proactive attempt to recognize and manage internal events and external threats that affect the likelihood of success
· What can go wrong (risk event)
· How to minimize the risk event’s impact (consequences)
· What can be done before an event occurs (anticipation)
· What to do when an event occurs (contingency plans)
three stages of risk management plan
planning, perform risk analysis, define recommendations
planning
a. Identify team
b. Identify scope
c. Identify method
d. Identify tools
e. Understand acceptable risk level
risk analysis
a. Identify assets
b. Assign value to assets
c. Identify vulnerabilities and threats
d. Calculate risks
e. Cost/benefit analysis
f. Uncertainty analysis
define recommendations
a. Defend the risk: lock the door, install IDS, block specific ports associated with specific attacks
b. Mitigate the risk: incident response, disaster recovery, and business continuity plans
c. Transfer the risk: outsource
d. Avoid/terminate the risk: disable USB port
e. Accept the risk: do nothing
inherit risk
The risk present in any scenario where no attempts at mitigation have been made and no controls or other measures have been applied to reduce the risk from initial levels to levels more acceptable to the organization.
residual risk
The risk that remains after efforts to identify and eliminate some or all types of risk have been made.
why is residual risk more important
First to consider is that residual risk is the risk "left over" after security controls and process improvements have been applied. This means that residual risk is something organizations might need to live with based on choices they've made regarding risk mitigation. Or they could opt to transfer the residual risk, for example, by purchasing insurance to offload the risk to an insurance company.
how is residual risk calculated
residual risk = inherit risk - impact of risk controls
why does residual risk exist
Security controls are not perfect – They can reduce risk but not eliminate it entirely.
New threats may emerge – Attackers continuously find new ways to exploit vulnerabilities.
Resource constraints – Organizations may not have the budget or capability to implement the most advanced security measures.
how to determine risk
· Loss/damage
· Likelihood
· Effectiveness of existing controls
· Uncertainty of vulnerability knowledge
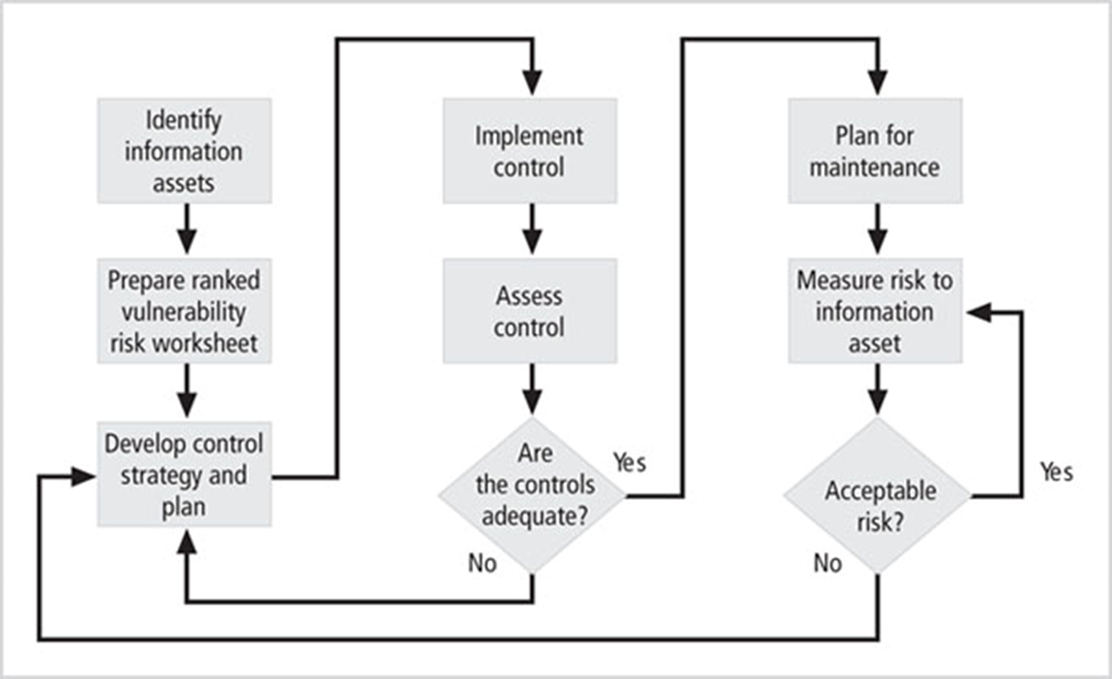
risk control llifecycle
what is likelihood
Likelihood is the probability that a specific vulnerability will be the object of a successful attack.
major undertakings of risk management
· Risk identification is the examination and documentation of the security posture of an organization’s information technology and the risks it faces.
· Risk assessment is the determination of the extent to which the organization’s information assets are exposed or at risk.
· Risk control is the application of controls to reduce the risks to an organization’s data and information systems
explain risk assessment
· The risk assessment must be a formal process.
· The process must be planned, and the input data, their analysis and the results should all be recorded.
· ‘Formal’ does not mean that risk assessment tools must be used, even though they can turn time-consuming tasks in a faster pace.
· Risk assessments must also produce ‘comparable and reproducible results’; this requirement tends to support the use of a purpose-developed tool and a well-defined methodology.
· The complexity of the risk assessment will depend on the complexity of the organization and of the risks under review.
what are the two issues to consider before deciding who undertakes risk assessment, and how
o The standard expects that periodic reviews of security risks and related controls will be carried out – taking account of new threats and vulnerabilities, assessing the impact of changes in the business, its goals or processes, technology and/or its external environment (such as legislation, regulation or society) and simply to confirm that controls remain effective and appropriate. Periodic review is a fundamental requirement of any risk assessment or risk management strategy.
o It is essential that risk assessment – the core competency of information security management – is conducted by an appropriately qualified and experienced person. This is logical; the key step on which the entire ISMS will be built needs, itself, to be solid.
quantitative risk assessment
Attempts to assign numerical values to different risk elements to provide a measurable assessment of risk.
key elements of quantitative risk assessment
· Safeguard costs – Cost of implementing security measures.
· Asset value – Monetary worth of assets at risk.
· Business impact – Financial and operational consequences of a risk event.
· Threat frequency – Estimated occurrence rate of a risk event.
· Safeguard effectiveness – How well a security measure reduces risk.
· Exploit probabilities – Likelihood of a vulnerability being exploited by a threat actor.
limitations of quantitative risk assessment
· Purely quantitative analysis is not possible because:
o Some risk factors are subjective and cannot be precisely measured.
o There is always uncertainty in estimated values.
· Common issues include:
o Probability estimations are subjective – often based on expert judgment rather than precise data.
o Financial loss estimates are difficult to quantify – especially for non-monetary losses like reputation damage.
o Interrelated risks can be overlooked – numerical ranking of risks might fail to capture relationships between threats.
key formulas in quantitative risk assessment
ALE = potential loss (SLE) * Probabibilty (ARO)
SLE = asset value * exposure factor (EF)
ARO = likelihood of a risk event occuring in a year
CBA = ALE(prior) - ALE(post) - ACS
Qualitative risk assessment
Qualitative risk assessment: Assesses risks without assigning numerical values.
Focus:
· Uses expert opinions and historical data to evaluate threats.
· Relies on scenario-based discussions rather than financial estimates.
Strengths:
· Easier to implement and does not require complex calculations.
· Considers non-monetary impacts, such as brand reputation or customer trust.
Limitations:
· Highly subjective – relies on human judgement.
· Lacks precision – harder to compare risks numerically.
Techniques used in qualitative assessment
· Scenario Analysis: Examining real-world risk situations and discussing their impact.
· Best Practices & Expert Judgment: Consulting industry standards and experienced professionals.
data collection methods for qualitative risk assessment
· Delphi Method – Reaching expert consensus through anonymous surveys.
· Brainstorming – Generating ideas on potential risks and countermeasures.
· Storyboarding – Creating visual narratives of risk scenarios.
· Focus Groups – Discussing risk in teams for multiple perspectives.
· Surveys & Questionnaires – Gathering structured feedback.
· Checklists – Verifying security gaps based on standardized guidelines.
· Interviews – Speaking with security personnel to understand risk concerns.
issues to consider when assigning values to assets
· Cost to acquire or develop the asset
· Cost to maintain and protect the asset
· Value of the asset to owners and users
· Value of the asset to adversaries
· Value of intellectual property that went into developing the information
· Price others are willing to pay for the asset
· Cost to replace the asset if lost
· Operational and production activities affected if the asset is unavailable
· Liability issues if the asset is compromised
· Usefulness and role of the asset in the organization
what does risk analysis ensure
· Cost effective
· Relevant
· Timely
· Responsive to threats
key benefits of risk analysis
· Helps prioritize risks and allocate security budgets efficiently.
· Provides a cost/benefit comparison, ensuring that the cost of safeguards does not exceed the potential cost of loss.
o Example: If a facility is worth $100,000, spending $150,000 on security is not justified.
four main goals of risk analysis
1. Identify assets and their value to the organization.
2. Identify vulnerabilities and threats.
3. Assess the probability and impact of threats.
4. Find an economic balance between threat impact and countermeasure cost.
risk assessment process
· Project Sizing: Before starting, identify what assets and threats to evaluate (e.g., physical security, technology security, personnel security).
· Asset Valuation Report:
o Created by the risk analysis team.
o Reviewed and approved by senior management to set the scope of the assessment.
o Assets deemed unimportant should not consume resources.
· Scope Definition:
o Guided by governance, risk management, compliance, and budget constraints.
roles of senior management
· Defining purpose and scope.
· Appointing a risk assessment team.
· Allocating time and funds.
· Reviewing and acting on findings.
alignment with business objectives
· Risk analysis helps align security program objectives with business goals.
· Leads to a better budget for security programs.
· Ensures both security and business objectives are successful.
selecting a risk assessment tool
· Compare tools based on:
o Automation effectiveness: How well it automates the risk assessment and statement of applicability process.
o Paperwork generation: Minimize unnecessary documentation.
o Flexibility: Ability to adapt to changing conditions and perform frequent, smaller-scale assessments.
o Result quality: Produces clear, meaningful, and actionable results.
· Conduct due diligence on the supplier to ensure:
o Reliable support.
o Long-term product sustainability.
· Seek references from satisfied customers.
strategies to address risks
defend - It is the implementation of security controls and safeguards to deflect attacks on systems and therefore minimize the probability that an attack will be successful.
transfer - It attempts to shift risk to other assets, other processes, or other organizations.
mitigate - The objective is to reduce the risk to an acceptable level
terminate/avoid - It directs the organization to avoid those business activities that introduce uncontrollable risks.
accept - It is the choice to do nothing to protect a vulnerability and to accept the outcome of its exploitation.
goals of a change control procedure
minimal disruption to services
reduction in back-out activities
cost-effective utilization of resources involved in implementing changes
what is a change
it is an event that is:
· Approved by management
· Implemented with a minimised and accepted risk to existing IT infrastructure
· Results in a new status of one or more Configuration Items (CIs)
· Provides increased value to the business (increased revenue, avoided cost, or improved service) from the use of the new or enhanced IT systems.
types of changes
· Emergency change is a change that should be evaluated and implemented as soon as possible after the occurrence of a disaster or a damaging incident, and it is implemented as a solution.
· Standard change is a low-risk change in which a specific procedure to follow is usually already documented, and which is generally pre-approved to make the process shorter.
· Major change is a high-risk change with potential financial consequences. The change request in this case should be comprehensive with appropriate financial arguments and necessary hierarchic approvals.
· Normal change is a considerable change in a service or IT infrastructure and needs to be reviewed and approved by the change advisory board prior to its implementation.
necessity of a change control policy
Every company should have a clear policy on:
· How changes are made within a facility.
· Who is authorized to make changes.
· How changes are approved.
· How changes are documented and communicated.
Without a policy, unauthorized changes can occur, leading to confusion or even operational failure.
strict regulations in certain industries
Heavily regulated industries (finance, pharmaceuticals, energy) follow strict change guidelines.
Regulations define:
· What can be changed.
· When changes can occur.
· Conditions under which changes are permitted.
The purpose is to prevent risks that could impact large populations or business partners
risks of poor change control
Without strict controls:
· Vulnerabilities can be introduced.
· Reversing unauthorized changes is difficult or impossible.
Areas affected by uncontrolled changes:
· Network configurations (firewall rules, IP changes).
· System parameters (security settings, permissions).
· Applications & settings (software updates, integrations).
· Facility environmental systems (power, cooling, access controls).
change in control in product development
· Change control is vital during a product's development and life cycle.
· Changes should be effective and orderly to prevent wasted time and money.
· Frequent, uncoordinated changes can hinder progress toward a final goal.
changes that can take place in a company
· New computers installed
· New applications installed
· Different configurations implemented
· Patches and updates installed
· New technologies integrated
· Policies, procedures, and standards updated
· New regulations and requirements implemented
· Network or system problems identified, and fixes implemented
· Different network configuration implemented
· New networking devices integrated into the network
· Company acquired by, or merged with, another company
change ramifications included resulting from a particular change
o how much downtime will be incurred?
o What is the cost associated with the change and any resulting downtime?
o Will the change impact other services?
o What is the schedule for the change
o Will it conflict with any other changes?
change procedure
requests
impact assessment
approval/disapproval
build and test
notification
implementation
validation
documentation
common roles in the change management
· Change Advisory Board (CAB): management responsibilities for the change management process
· Change manager: responsible for managing the activities of the change management process for the IT organization
· Change Administrator: The Change Administrator directly supports the change manager and is responsible for all of the administrative functions associated with the Change Management program.
· Change Initiator: The Change Initiator (normally someone within the IT Business Unit) originates changes by submitting a Request for Change (RFC) to the Help Desk or the Change Coordinator in the appropriate IT Business Unit.
· Change Coordinator: responsible for planning and coordinating all of the phases of the change from initiation through acceptance and documentation. The Change Coordinator will document all relevant information in the company’s selected technology platform.