Auditor
1/11
Earn XP
Description and Tags
Things to know.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No study sessions yet.
12 Terms
Auditor
A person authorized to examine and verify accounts.
Cybersecurity
Measures taken to protect a computer or computer system (as on the Internet) against unauthorized access or attack.
CMMC
Cybersecurity Maturity Model Certification
NIST SP 800-171
National Institute of Standards and Technology, Special Publication 800-171: Protecting Controlled Unclassified Information (CUI) in Nonfederal Systems and Organizations.
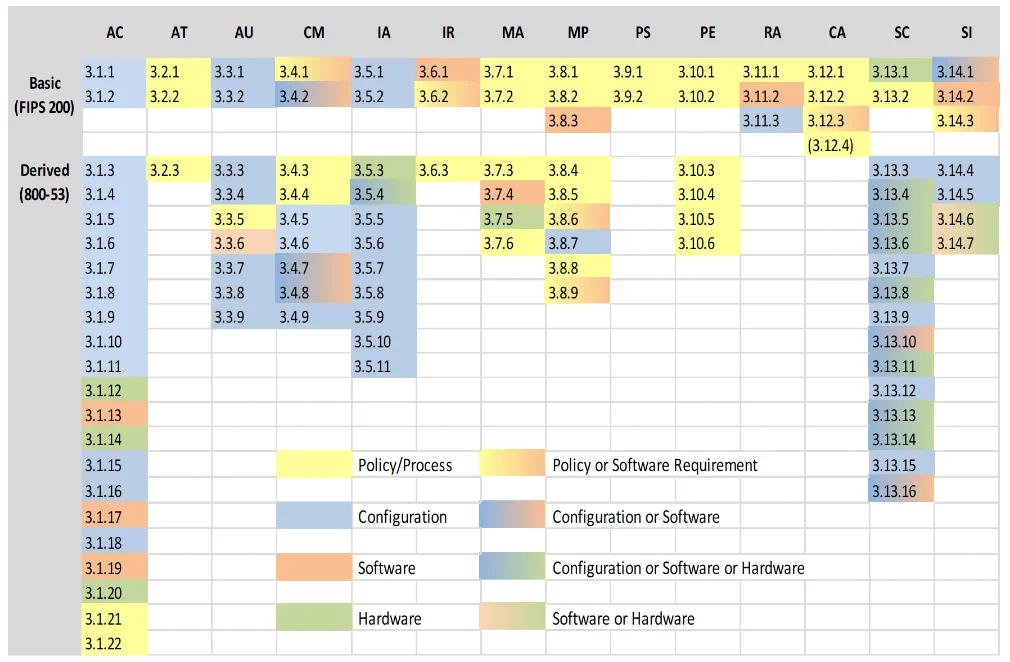
110 controls organized by the following 14 control families:
3.1 Access Control (AC)
3.2 Awareness and Training (AT)
3.3 Audit and Accountability (AU)
3.4 Configuration Management (CM)
3.5 Identification and Authentication (IA)
3.6 Incident Response (IR)
3.7 Maintenance (MA)
3.8 Media Protection (MP)
3.9 Personnel Security (PS)
3.10 Physical Protection (PE)
3.11 Risk Assessment (RA)
3.12 Security Assessment (CA)
3.13 System and Communications Protection (SC)
3.14 System and Information Integrity (SI)
IOC
Indicators of Compromise.
APT
Advanced Persistent Threat.
ISO/IEC 27001
international standard concerning information security management system.
DDoS Attack
Distributed Denial-of-Service attack.
SQL injection attack
Man-in-the-middle attack
Phishing Attack