Week 2: Arrays
1/21
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
22 Terms
Encryption
the act of hiding plain text from prying eyes.
Decryption
the act of taking an encrypted piece of text and returning it to a human-readable form.
Steps of Compiling
preprocessing
compiling
assembling
linking
preprocessing
1st step of compiling; where the header files in your code, designated by a # (such as #include <cs50.h>) are effectively copied and pasted into your file. During this step, the code from cs50.h is copied into your program.
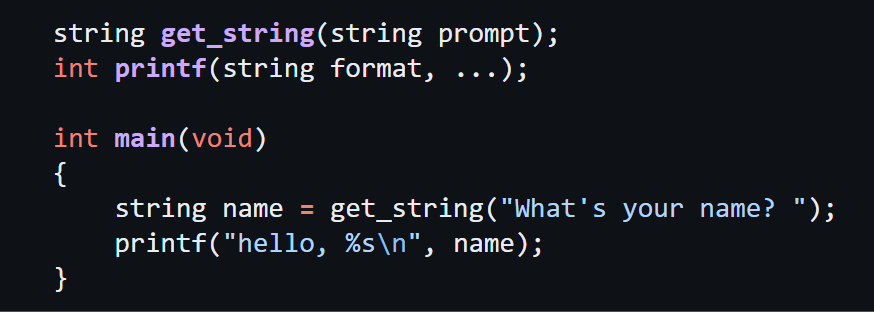
compiling
2nd step of compiling; where your program is converted into assembly code
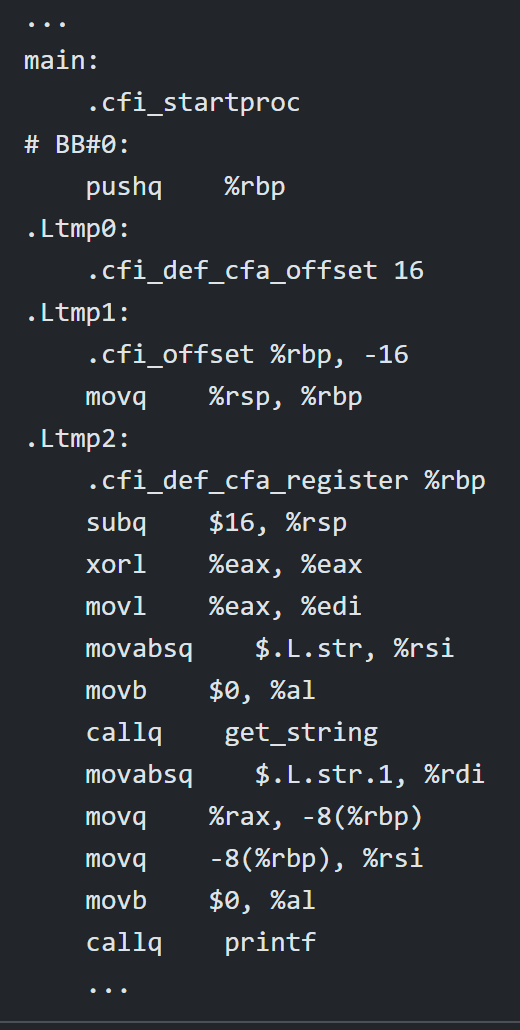
assembling
3rd step of compiling; involves the compiler converting your assembly code into machine code
linking
last step of compiling; code from your included libraries is converted also into machine code and combined with your code. The final executable file is then outputted.
Debugging
the process of locating and removing bugs from your code.
Rubber duck debugging
debugging technique where you can talk to an inanimate object (or yourself) to help think through your code and why it is not working as intended
debugger
a software tool created by programmers to help track down bugs in code.
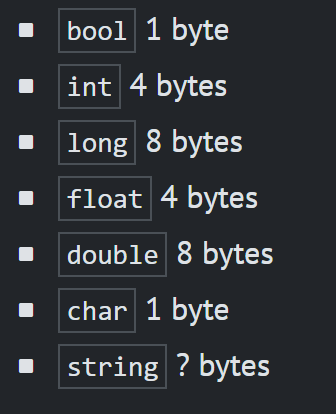
System Resources required by each data type
Arrays
a sequence of values that are stored back-to-back in memory; containers that can also be passed between functions
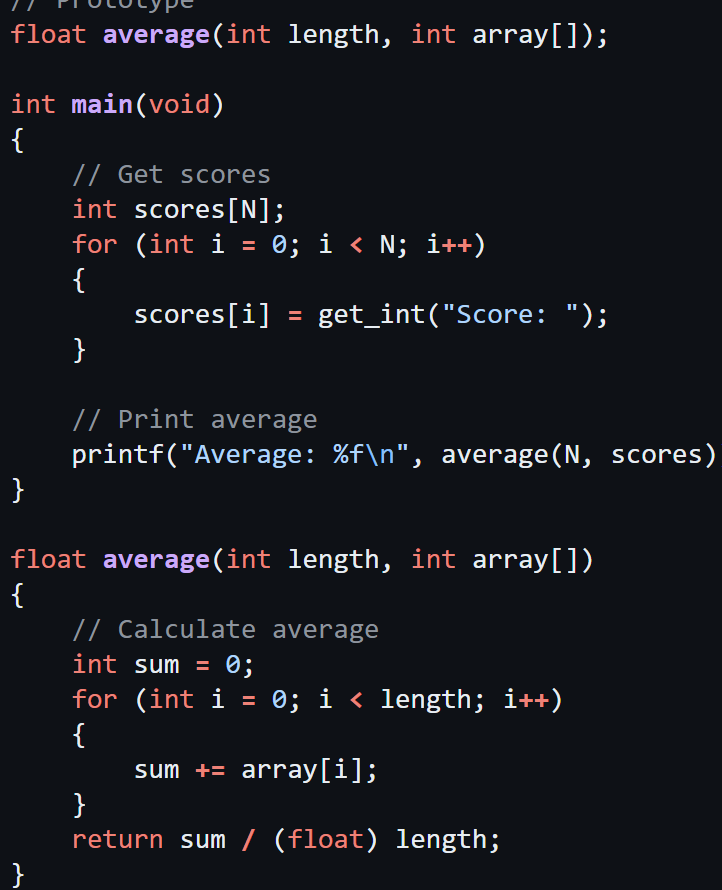
string vs char
A string is simply an array of variables of type char: an array of characters.
Command-line arguements
arguments that are passed to your program at the command line.
argc
the number of command line arguments
argv
an array of the characters passed as arguments at the command line.
Exit Status
When a program exits without error, a status code of 0 is provided to the computer. Often, when an error occurs that results in the program ending, a status of 1 is provided by the computer.
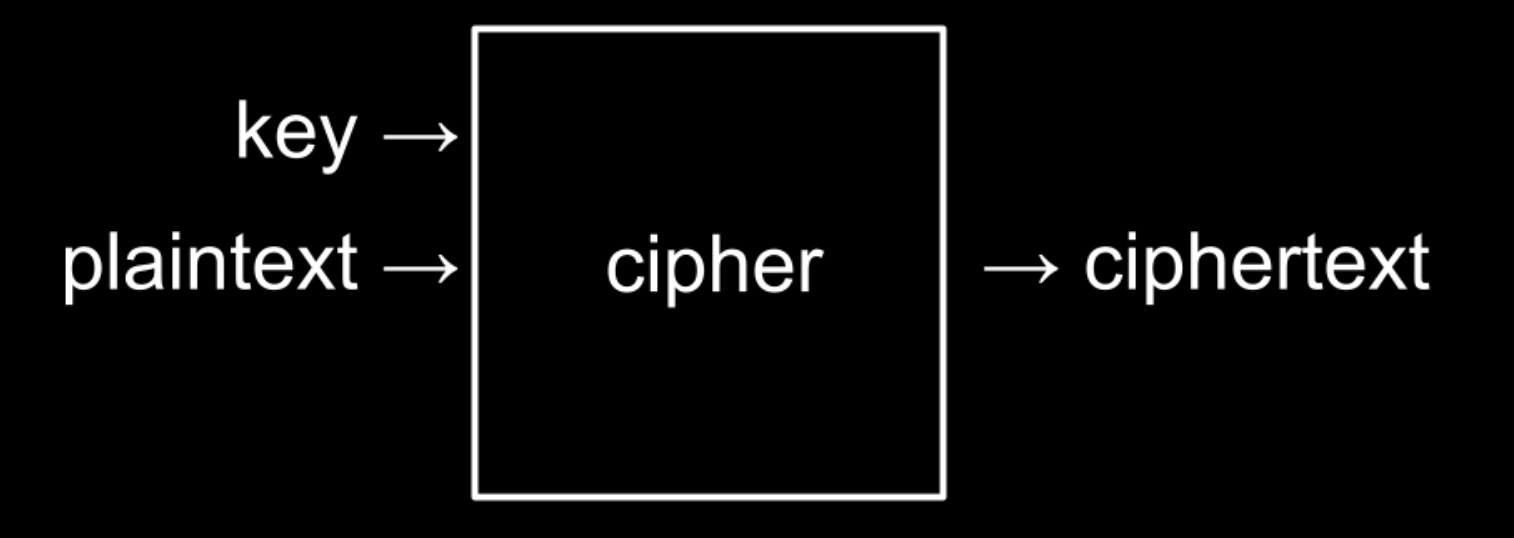
Cryptography
the art of ciphering and deciphering a message.
ciphering a message
The key is a special argument passed to the cipher along with the plaintext. The cipher uses the key to make decisions about how to implement its cipher algorithm.
reading levels
typically refer to how you read input from a user or a file
Reverse engineering
intellectual property; involves analyzing a compiled executable or library to understand its functionality, design, and internal workings without access to the original source code.
echo $?
useful for testing code in industry in automated processes