Cybersecurity Penetration Testing and Web Basics and Vulnerabilities
1/19
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
20 Terms
Penetration Testing
test the effectiveness of security
controls OR find vulnerabilities in a web application or other software.
▪ Also known as: ethical hacking or security auditing
▪ At completion, a pentester must deliver a detailed report of the pentest
results and recommendations for improving security
Why Pen test?
Check to see if there are holes in security configurations.
▪ Compliance - industries like healthcare and finance require regular
pentesting.
▪ Validate expense of security controls – “do I really need this?”
Red Team
•Offensive Security
•“We Break Things”
‒Penetration Tests
‒Vulnerability Assessments
‒Social Engineering
Blue Team
•Defensive Security
•“We Protect Things”
‒Monitoring
‒Incident Response
‒Setting up Controls
Penetration Testing vs Vulnerability Assessment
Goal - identify where defenses need strengthening.
▪ Vulnerability Assessment method: check for known
vulnerabilities and identify the highest threat risks.
▪ Penetration Testing method: identify weaknesses by trying to
break through the defenses.
Pen testing vs attacking
Same Goal: find vulnerabilities in systems or software that can
be exploited to bypass security controls.
Q: To do their job a pentester must think and act like a hacker. So, what
is the difference between pentesting (good) and attacking (bad)?
A: Permission! A Pentester will get a signed “scope of work” contract
from the organization giving detailed list of what they can try to test and
what is off limits
White hat
Authorized hacker. good intentions, have
explicit permission to look for vulnerabilities, actions are legal.
Black hat
Unauthorized hacker. intends mal-actions,
NO permission to access system, actions are illegal.
Grey hat
Semi-Authorized Hacker = (Formerly Grey Hat) - often has
good intentions, but they don’t have permission. Need caution
as can easily step over line into legal issues.
▪ Example: an independent researcher finds a vulnerability OR a user
finds one accidentally.
▪ Responsible disclosure is KEY → contact the organization, provide
documentation, don’t share publicly.
▪ In some cases, the discovery is eligible for a bug bounty =
organizations offer a monetary reward for discoveries of a bug, error or
vulnerability.
Exploit
Pentesters or hackers look for a way into places they don’t belong. To do
this, they need an exploit.
Definition: Exploit - software, code, or commands used to take advantage
of a vulnerability (glitch in code) on a computer system.
Exploits can be used to:
▪ Get access to the system to remotely perform actions on the target PC
▪ Disable the system by creating an OS or system crash for a DoS.
▪ Change attacker’s permissions to root or administrator.
▪ Steal data like passwords or valuable documents.
▪ Install a method to easily gain future access (backdoor).
Metasploit Framework
The Metasploit Framework is an exploit toolkit = an application
that has a bundle of exploits that will work on multiple
vulnerabilities.
• Open-source tool that works as a pentesting code repository.
• New exploits are added regularly through contributions from the cyber
community.
• Used by security professionals globally, it
is taught in cybersecurity courses and is
part of certification exams.
Metasploit payload
An exploit is the way into a system to deliver a payload.
The payload is the attack code to execute after you are in the
system.
Examples:
▪ command line access (aka reverse shell)
▪ upload and execute a file
▪ start a screen capture
▪ look for passwords
▪ keylogging
▪ install a backdoor
Metasploit is modular which means you can mix and match the
exploit and payload.

Exploring Metasploit lab


Threat hunting
Threst hunting lab


Threat hunting lab


Web basics


Web basics lab

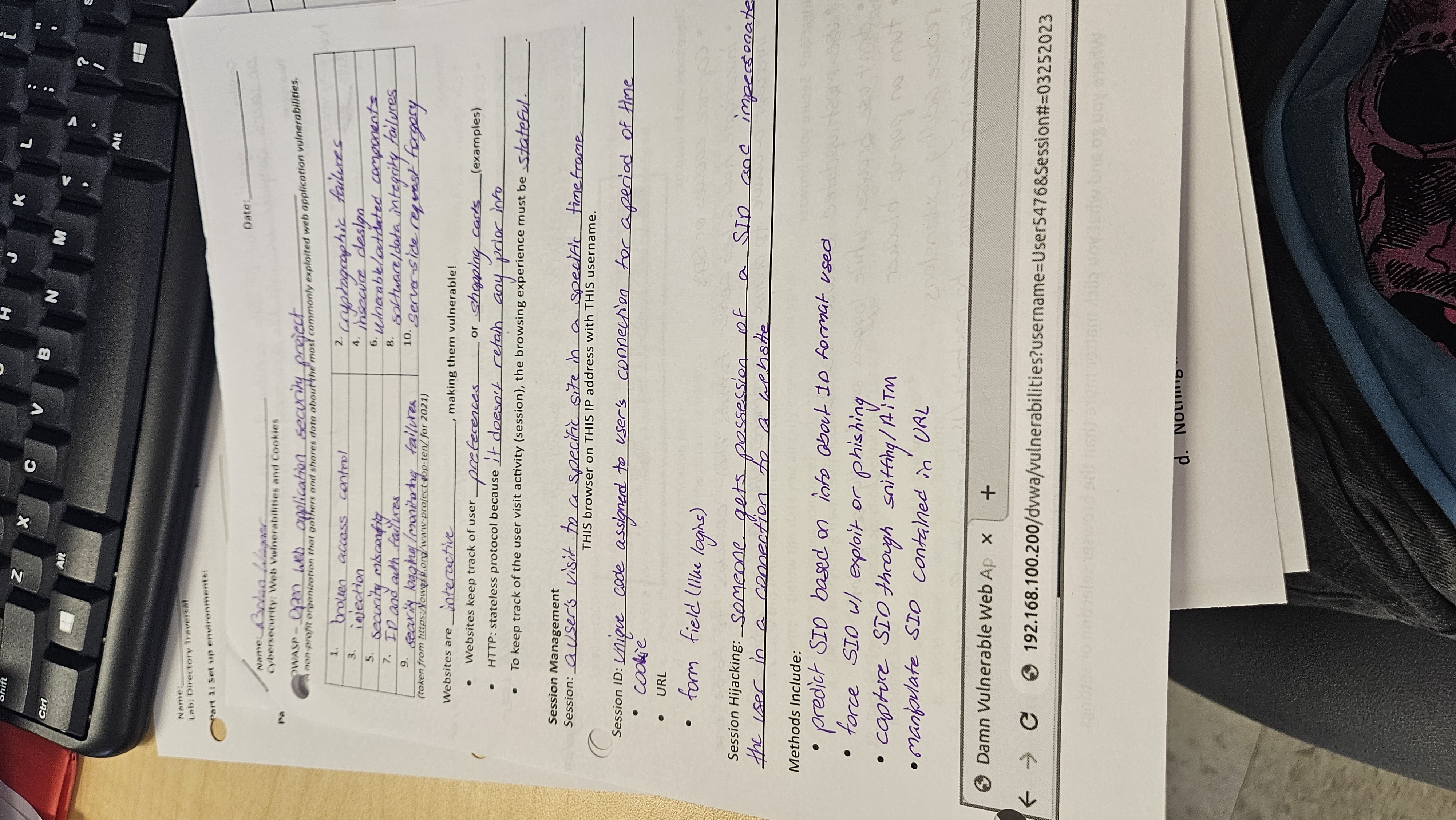
Web vulnerabilities and cookies


Web vulnerabilities and cookies lab


User input threats