Network+ N10-009
1/684
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
685 Terms
Network security lists:
Consists of a set of ingress and egress security rules that apply to all the VNICs in any subnet that the list is associated with.
Class E IPv4:
240.x.x.x - 255.x.x.x
Supervisory control and data
acquisition (SCADA):
A type of industrial control system that manages large-scale, multiple-site devices and equipment spread over geographically large areas.
Cyclic redundancy check
(CRC):
An error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data.
Which of the following answers refer(s) to the characteristic features of MPLS (Multiprotocol Label Switching)?
- Used for connecting devices on a WAN.
- Unencrypted network traffic.
- Enables sending packets over a single, faster network path (routing decisions based on labels).
- Enables delivery of various data packet types over the same network link.
Which of the following answers lists the broadcast address for the 192.168.50.155/20 network?
192.168.63.255
The process of combining multiple physical network adapters into a single logical interface for increased throughput and redundancy is known as:
NIC teaming.
Which of the following answers refers to a dedicated security mechanism that prevents ARP attacks?
DAI (Dynamic ARP Inspection).
Which of the following examples do not fall into the category of physical security detective controls?
- Access control vestibules.
- Access control hardware.
- Employee training.
Multipathing:
Creates more than one physical path between the server and its storage devices for better fault tolerance and performance.
Virtual Network Computing (VNC):
A program that allows you to control a computer at a remote location.
Server Message Block (SMB):
- A protocol used by Windows to share files and printers on a network.
- Port 445.
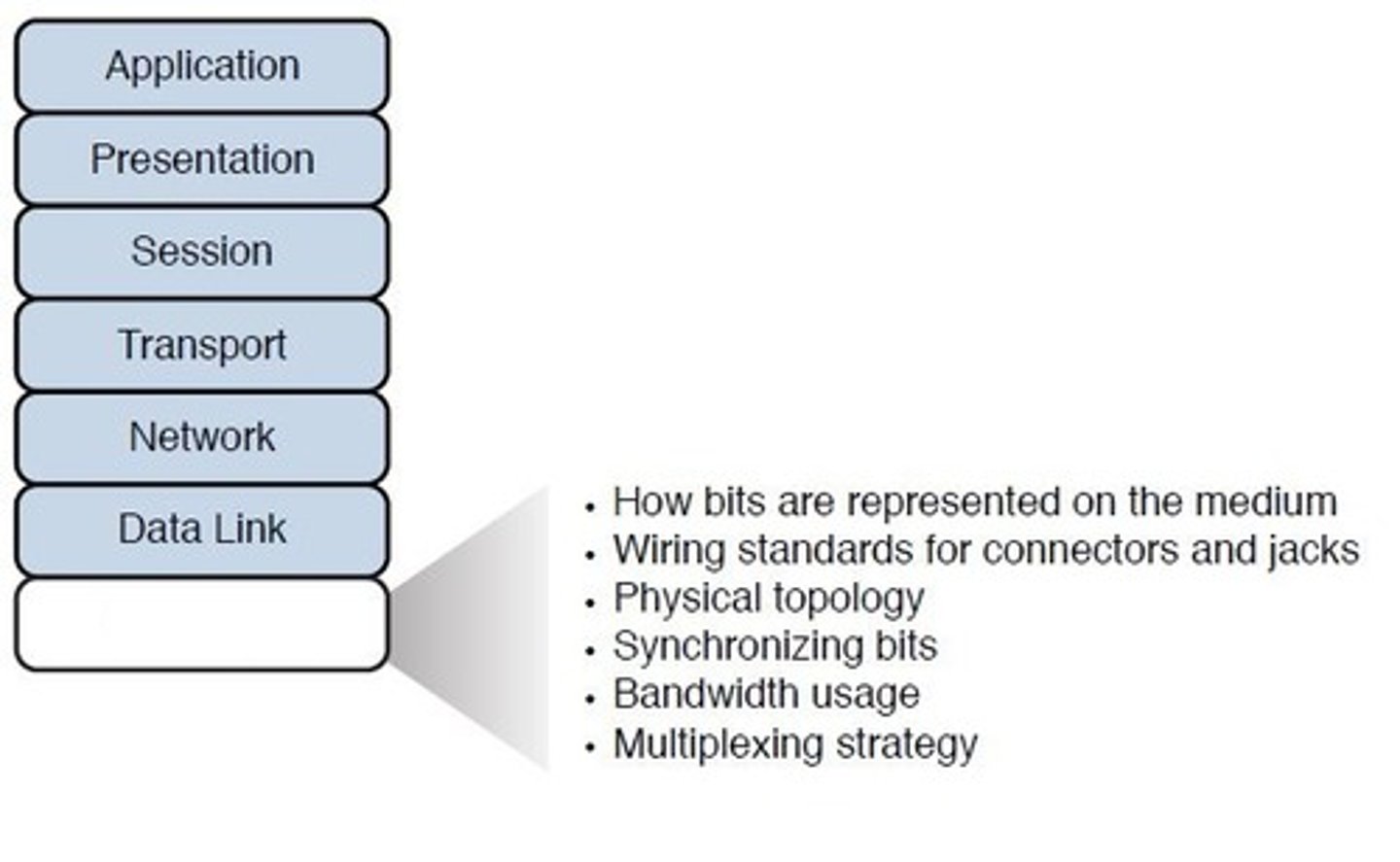
Layer 1 - Physical:
Receives the frames and data and sends them via the local media (copper wires, fiber-optic cables, etc.) to the switches, routers, etc., along the network path.
Wireless Controller:
A central management console for all of the APs on a network.
Content delivery network (CDN):
- An information system that serves content to Web pages over the Internet.
- To reduce wait time, data is typically stored and served from many geographic locations.
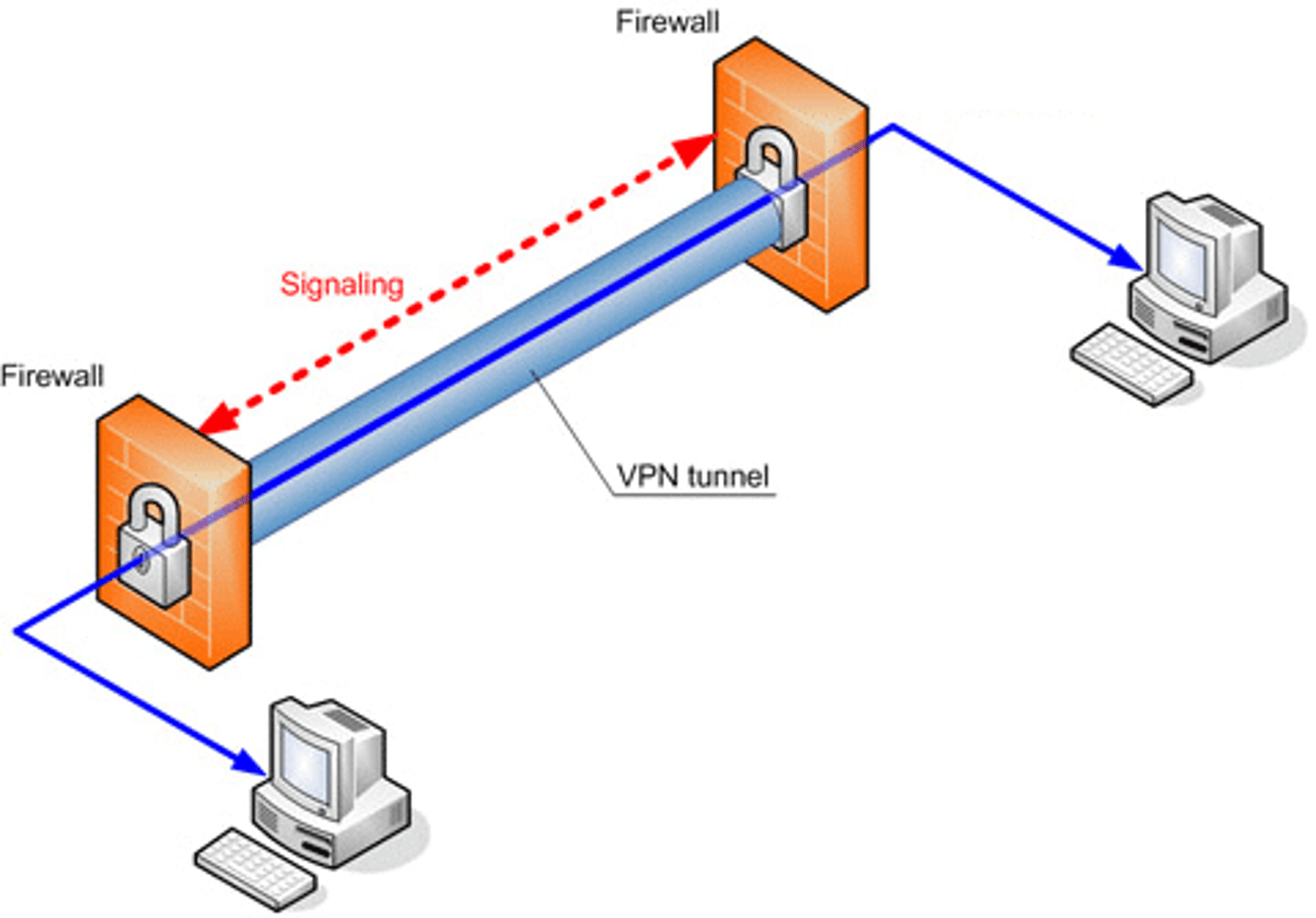
Virtual private network (VPN):
A private data network that creates secure connections, or "tunnels," over regular Internet lines.
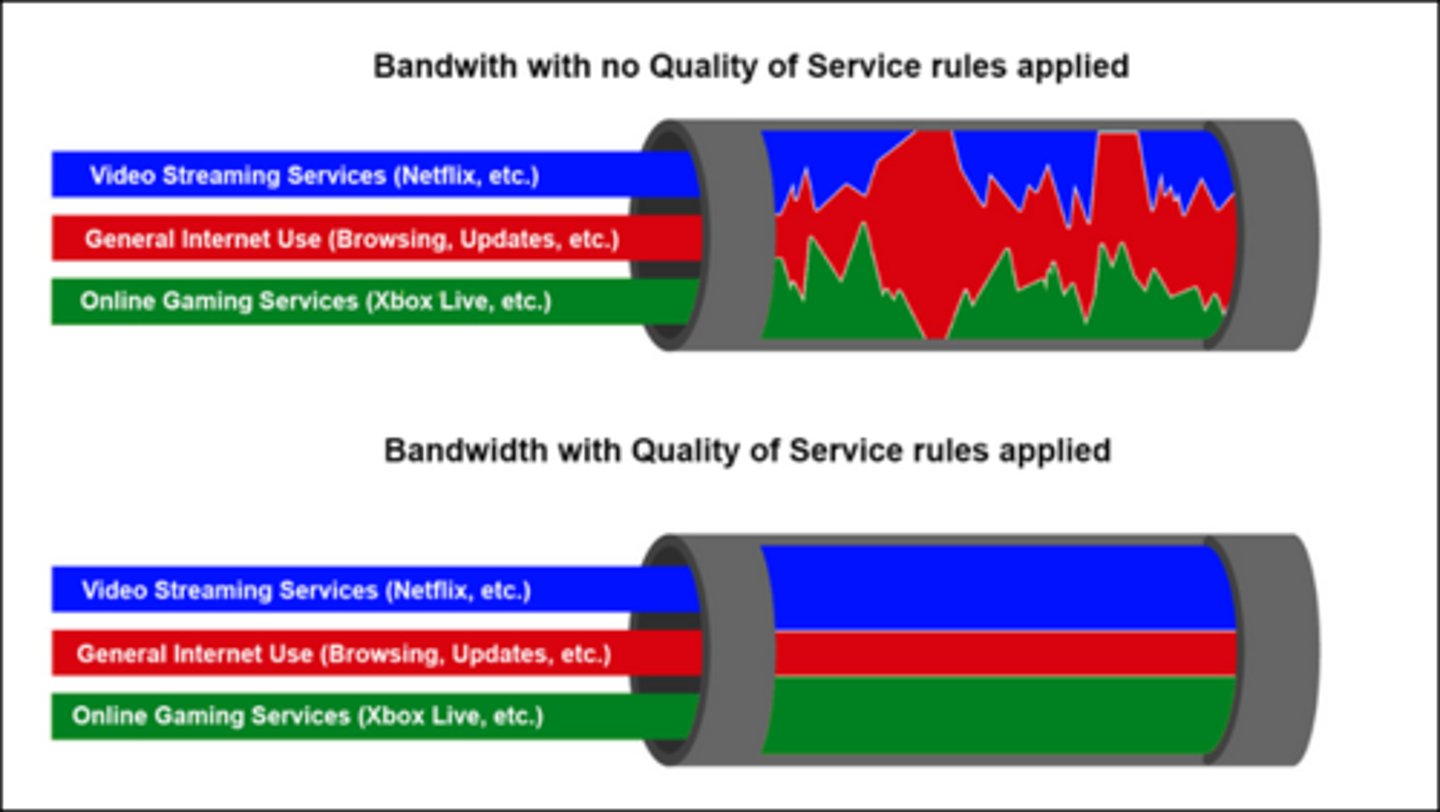
Quality of service (QoS):
Policies that control how much bandwidth a protocol, PC, user, VLAN, or IP address may use.
Time to live (TTL):
The maximum amount of time a packet is allowed to circulate through a network before it is destroyed.
Network functions virtualization (NFV):
Provisioning virtual network appliances, such as switches, routers, and firewalls, via VMs and containers.
Virtual private cloud (VPC):
A private network segment made available to a single cloud consumer within a public cloud.
Network security groups:
Allows you to filter network traffic. Can contain multiple inbound and outbound security rules that enable you to filter traffic to and from resources.
Internet gateway:
A device or node that connects networks by translating protocols.
Generic Routing Encapsulation (GRE):
Method of encapsulation of IP packet in a GRE header which hides the original IP packet.
Subnetting:
The act of dividing a network into smaller logical subnetworks.
Zero trust architecture (ZTA):
An approach to access control in IT networks that does not rely on trusting devices or network connections; rather, it relies on mutual authentication to verify the identity and integrity of devices, regardless of their location.
Maximum transmission unit (MTU):
The largest packet size supported on an interface.
Security information and
event management (SIEM):
An application that collects and analyzes log data to monitor critical activities in an organization.
Client-to-site VPN:
Clients from the Internet can connect to the server to access the corporate network or Local Area Network (LAN) behind the server but still maintains the security of the network and its resources.
Internet of Things (IoT):
The network of products embedded with connectivity-enabled electronics.
Denial-of-service (DoS):
Attack floods a network or server with service requests to prevent legitimate users' access to the system.
Incorrect VLAN assignment:
- Symptoms: No connectivity between devices.
- Causes: Devices are configured to use different VLANs.
- Resolution: Reconfigure devices to use the same VLANs.
Channel overlap:
Drawback of 2.4-GHz wireless networks where channels shared some bandwidth with other channels.
Which of the following protocols reside(s) at the application layer of the OSI model?
- HTTP.
- FTP.
- SMTP.
What are the characteristic features of the 1000BASE-T Ethernet standard?
- Maximum cable segment length of 100 meters.
- Twisted-pair copper cabling (Cat 5 or higher).
- Uses all four pairs of wires in a cable for data transmission.
In active-active configuration, network traffic is distributed across:
All designated network infrastructure devices.
What are the characteristics of TACACS+?
- Encrypts the entire payload of the access-request packet.
- Primarily used for device administration.
- Separates authentication and authorization.
What is the function of a C2 server?
Botnet control.
Which of the following actions would be of help in the process of web server hardening?
- Removing server version banner.
- Disabling unnecessary ports, services, and accounts.
- Keeping the system up to date via updates and patches.
- Enabling and monitoring logs.
- Permissions audits.
Deauthentication attack:
DoS strike that disconnects a wireless host from a WAP so that the victim is forced to reconnect and exchange the wireless key multiple times; an attacker can then perform an offline brute-force cracking of the password.
SQLnet Protocol:
- Used for communication from a client to an Oracle database.
- Port 1521.
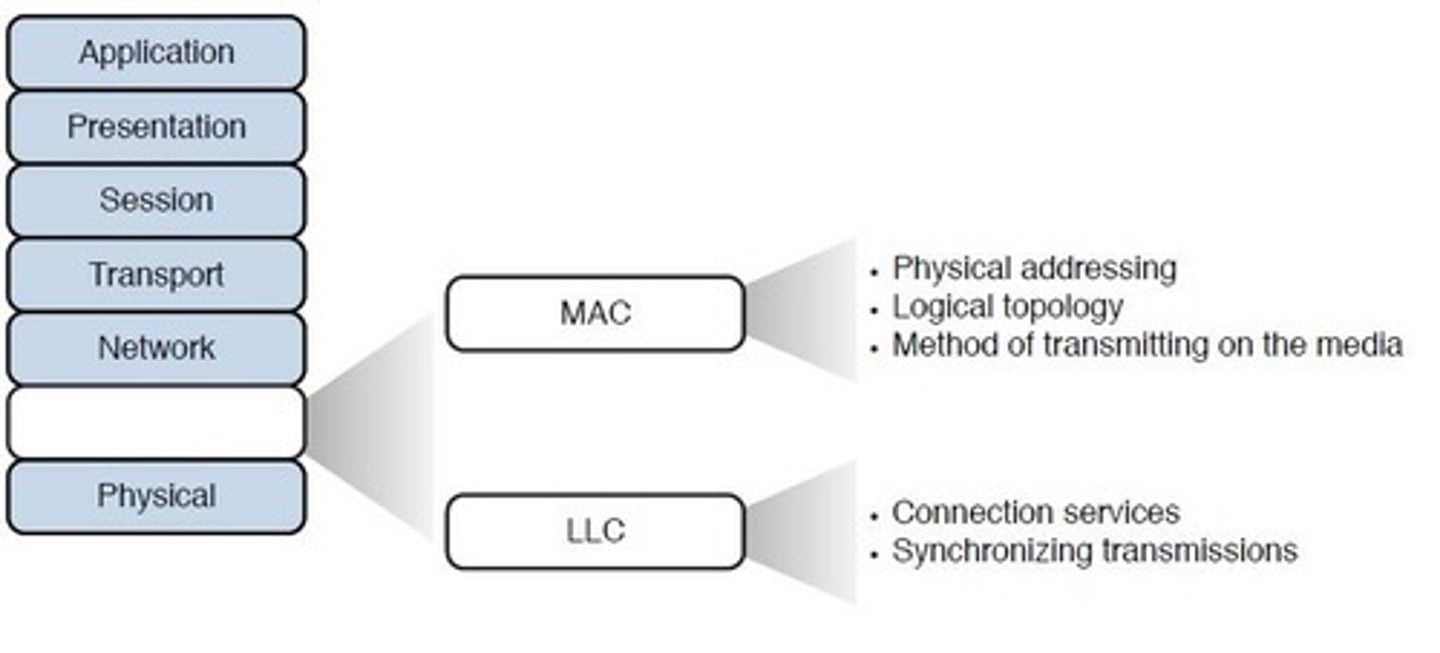
Layer 2 - Data link:
- Receives the packets and adds physical addressing by adding sender and receiver MAC addresses to each data packet.
- This information forms a unit called a frame.
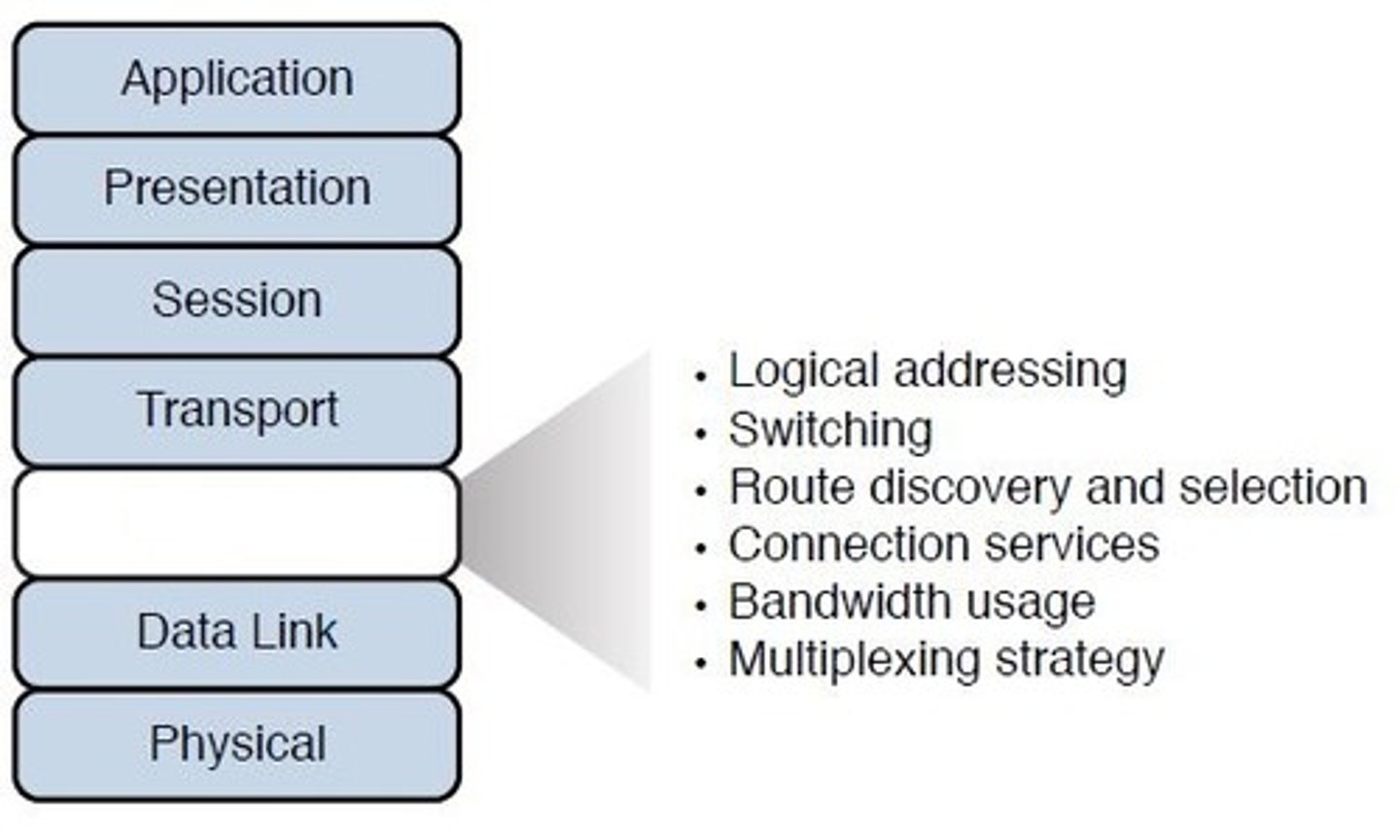
Layer 3 - Network:
The routing layer (IP addresses, routers, packets).
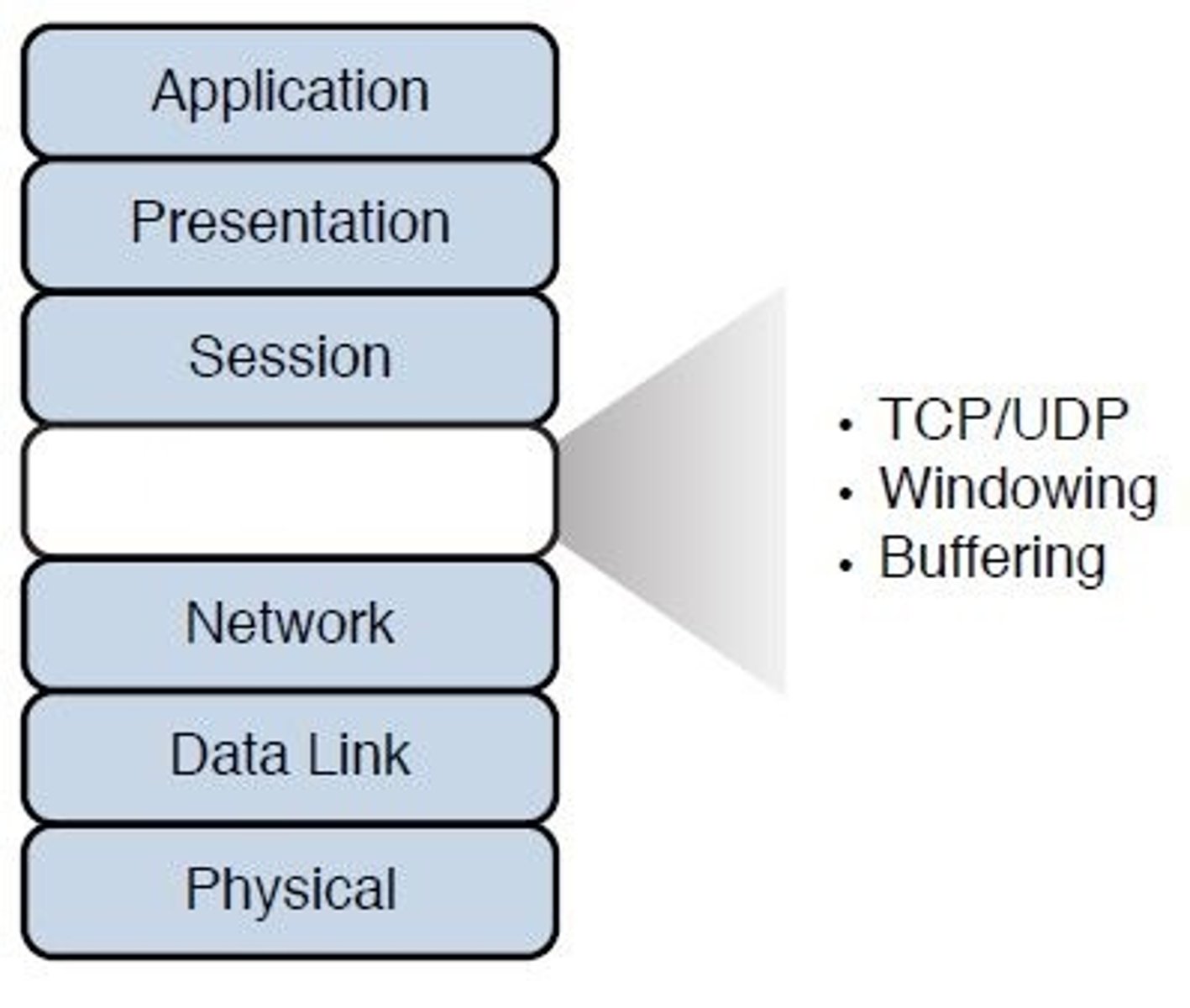
Layer 4 - Transport:
The functions defined in this layer provide for the reliable transmission of data segments, as well as the disassembly and assembly of the data before and after transmission.
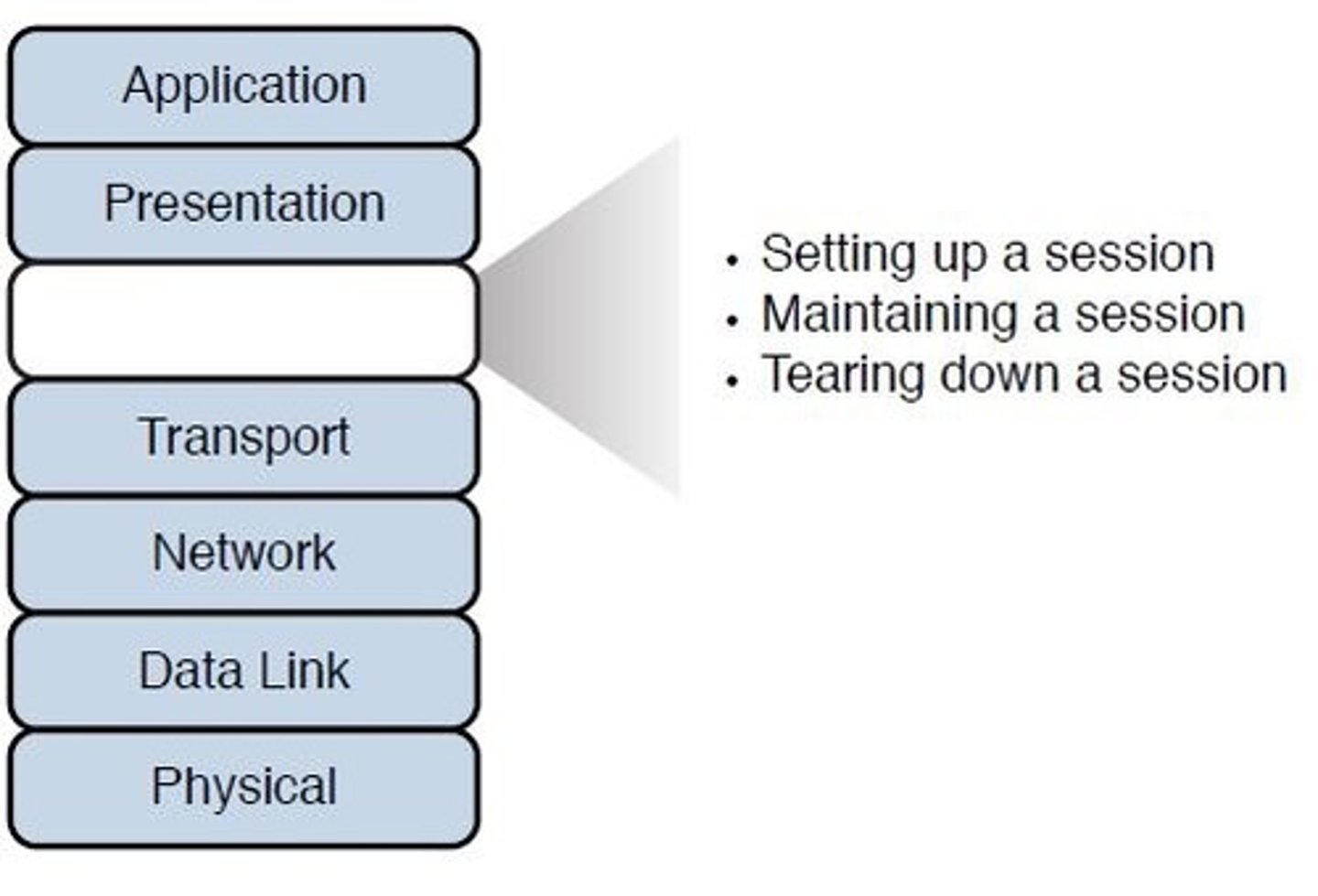
Layer 5 - Session:
- Establishes, manages, and terminates sessions between two communicating hosts.
- Synchronizes dialog between the presentation layers of the two hosts and manages their data exchange.
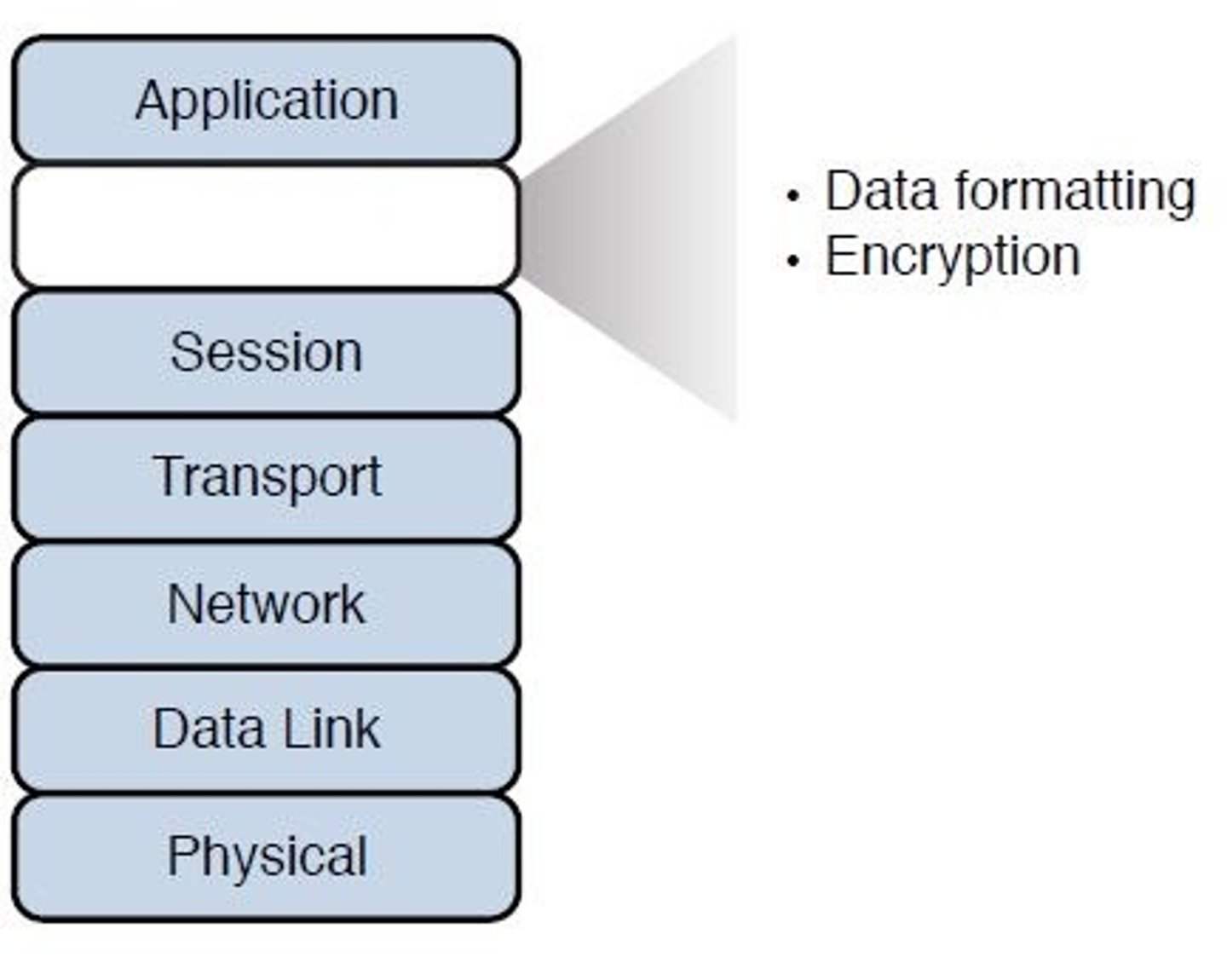
Layer 6 - Presentation:
- Ensures that info sent at application layer of one system is readable by the application layer of another system.
- May translate between multiple data formats by using a common format.
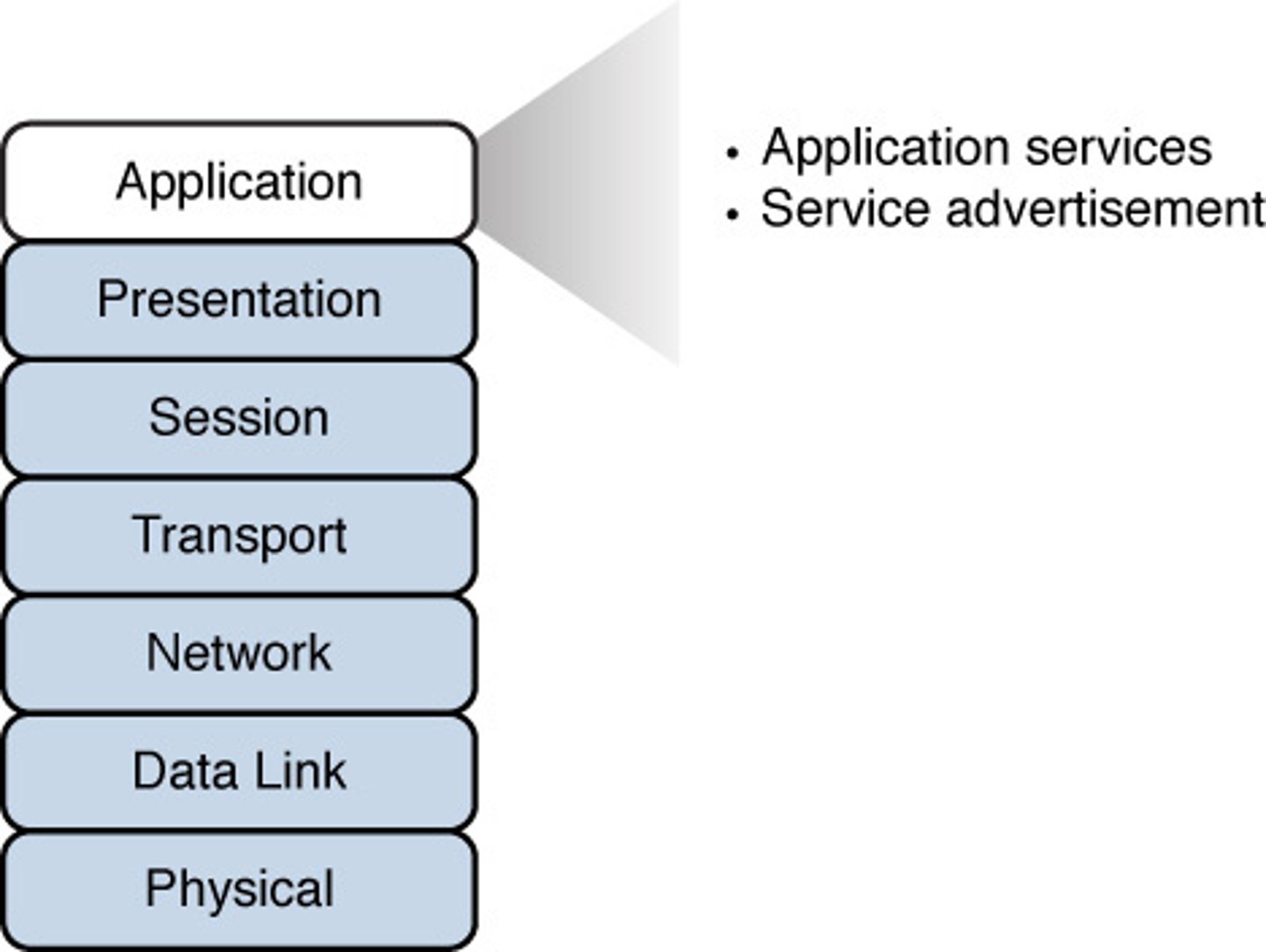
Layer 7 - Application:
- Closest to the user.
- Provides network services to the applications of the user, such as email, file transfer, and terminal emulation.
Router:
A device that forwards data packets between computer networks.

Switch:
A computer networking device that connects network segments.

Firewall:
A part of a computer system or network that is designed to block unauthorized access while permitting outward communication.
Intrusion detection system (IDS):
Monitors network traffic to identify possible malicious activity and log information about it.
Intrusion prevention system (IPS):
Sits behind the firewall and uses anomaly detection or signature-based detection to identify and respond to network threats.
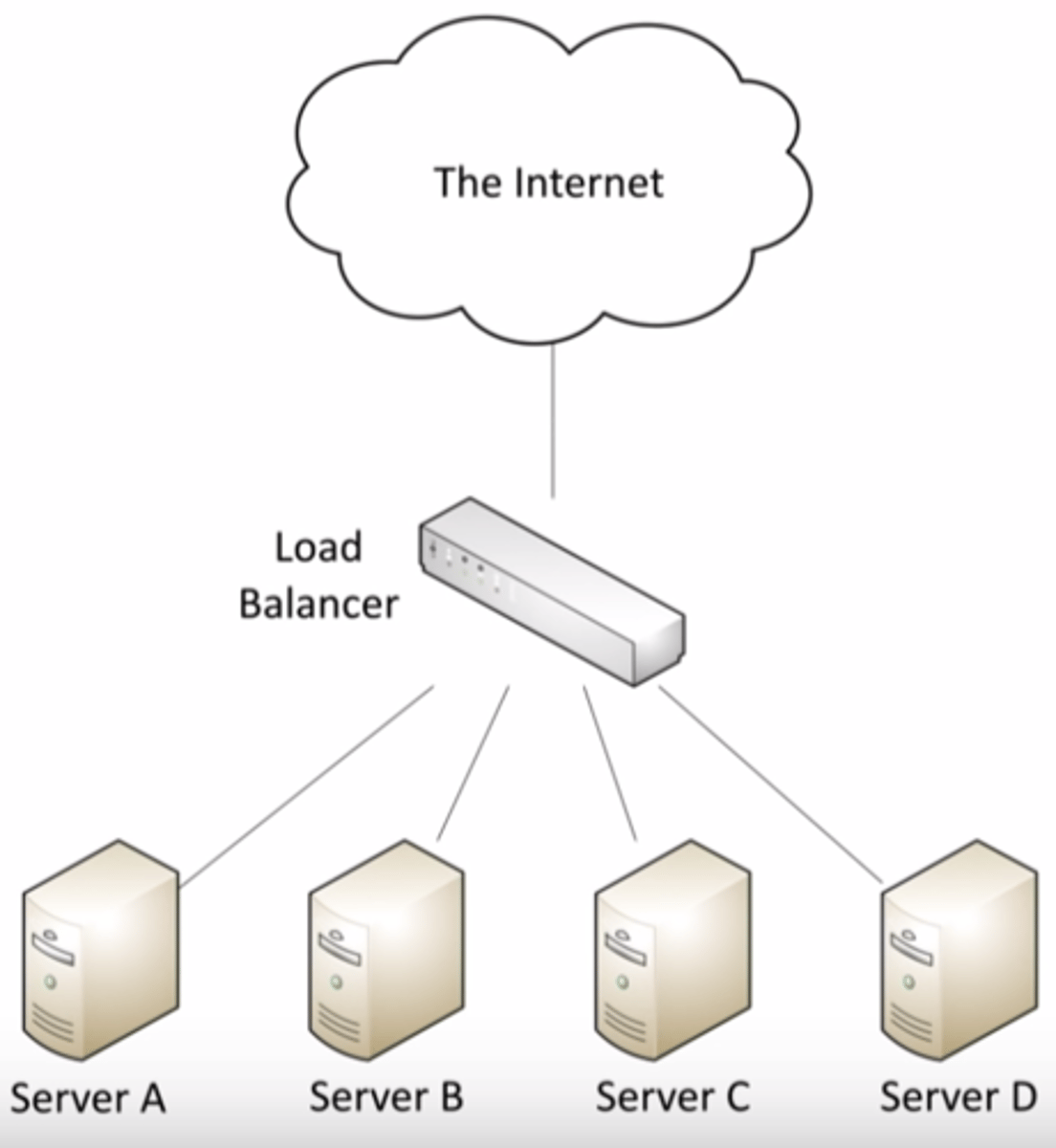
Load Balancer:
Hardware or software that balances the load between two or more servers.
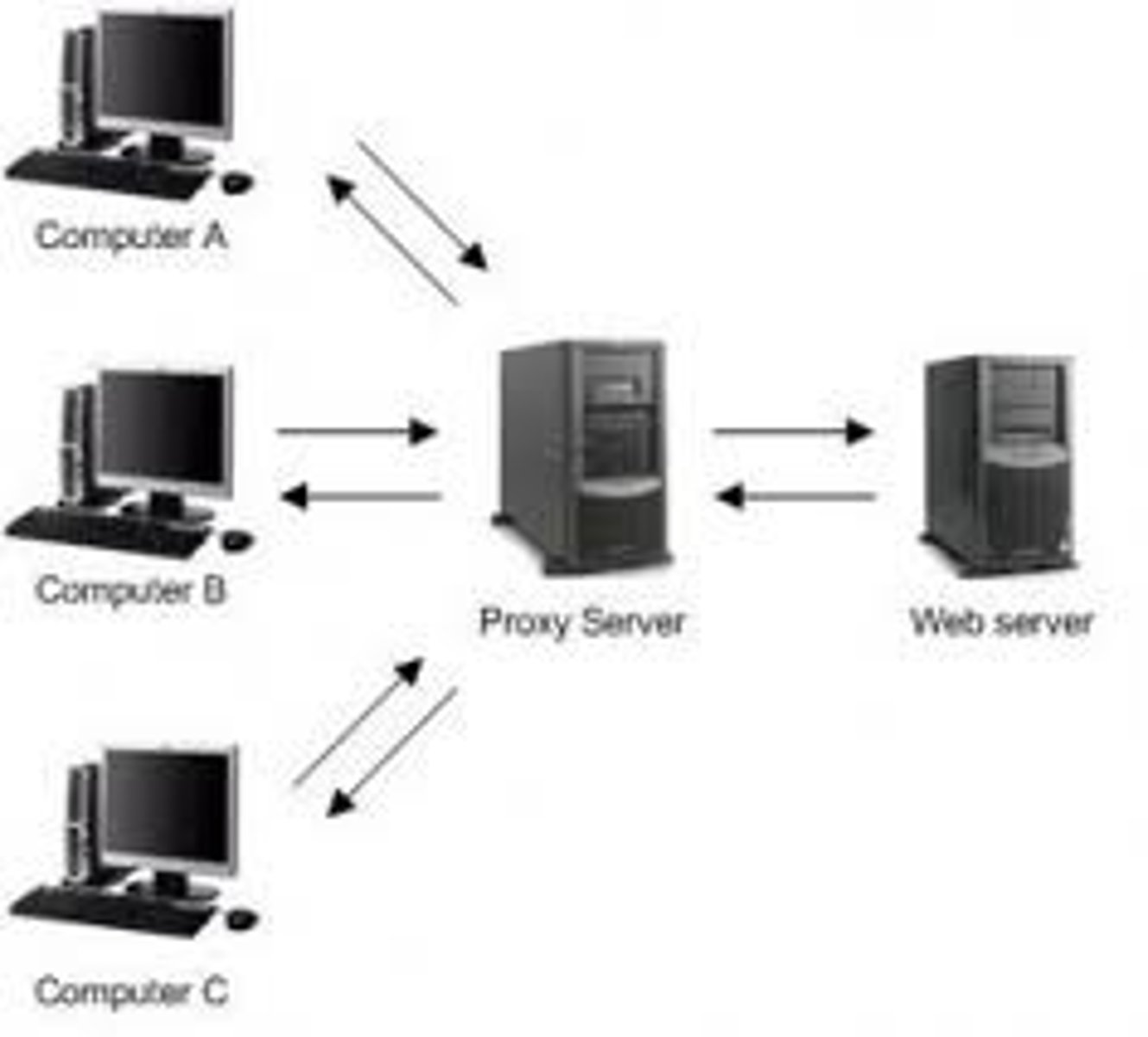
Proxy:
A system or router that provides a gateway between users and the internet.
Network-attached storage (NAS):
A server that is placed on a network with the sole purpose of providing storage to users, computers, and devices attached to the network.

Storage area network (SAN):
A high-speed network with the sole purpose of providing storage to other attached servers.
Wireless Access point (AP):
A device that enables wireless systems to communicate with each other, provided that they are on the same network.
Network address translation (NAT) gateway:
You can use this so that instances in a private subnet can connect to services outside your VPC, but external services cannot initiate a connection with those instances.
Public cloud:
Provides cloud services to just about anyone.
Private cloud:
Serves only one customer or organization and can be located on the customer's premises or off the customer's premises.
Hybrid cloud:
A mixed computing environment where applications are run using a combination of computing, storage, and services in different environments.
Software as a service (SaaS):
A form of cloud computing where a firm subscribes to a third-party software and receives a service that is delivered online.
Infrastructure as a service (IaaS):
Delivers hardware networking capabilities, including the use of servers, networking, and storage, over the cloud using a pay-per-use revenue model.
Platform as a service (PaaS):
Supports the deployment of entire systems including hardware, networking, and applications using a pay-per-use revenue model.
Scalability:
Refers to how well a system can adapt to increased demands.
Elasticity:
Refers to the ability of a cloud to automatically expand or compress the infrastructural resources on a sudden up and down.
Multitenancy:
A single instance of a system serves multiple customers.
Internet Control Message Protocol (ICMP):
- An IP network protocol used to determine if a particular service or host is available.
Transmission Control Protocol (TCP):
A protocol for sending packets that does error-checking to ensure all packets are received and properly ordered.
User Datagram Protocol (UDP):
A protocol for sending packets quickly with minimal error-checking and no resending of dropped packets.
Internet Protocol Security (IPSec):
A set of protocols developed to support the secure exchange of packets between hosts or networks.
Authentication Header (AH):
An IPsec protocol that authenticates that packets received were sent from the source identified in the header of the packet.
Encapsulating Security Payload (ESP):
An IPsec protocol that provides authentication, integrity, and encryption services.
Internet Key Exchange (IKE):
Method used by IPSec to create a secure tunnel by encrypting the connection between authenticated peers.
Unicast:
A form of message delivery in which a message is delivered to a single destination.
Multicast:
A form of transmission in which a message is delivered to a group of hosts.
Anycast:
A network addressing and routing method in which incoming requests can be routed to a variety of different locations or "nodes."
Broadcast:
Used to transmit a message to any reachable destination in the network without the need to know any information about the receiving party.
Frequency bands used by 802.11 networks include:
- 5.0 GHz.
- 2.4 GHz.
IEEE 802.11a wireless standard:
- 5.0 GHz frequency band.
- Maximum data signaling rate of 54 Mbps.
IEEE 802.11b wireless standard:
- 2.4 GHz frequency range.
- Maximum data signaling rate of 11 Mbps.
IEEE 802.11g wireless standard:
- 2.4 GHz frequency range.
- Maximum data signaling rate of 54 Mbps.
IEEE 802.11n wireless standard:
- 2.4 GHz frequency band.
- 5.0 GHz frequency band.
- Maximum data signaling rate of up to 600 Mbps.
- Multiple Input / Multiple Output (MIMO).
IEEE 802.11ac (WiFi 5) wireless standard:
- 5.0 GHz frequency band.
- Maximum data signaling rate of up to 6.933 Gbps.
- Multi-User Multiple Input / Multiple Output (MU-MIMO).
IEEE 802.11ax (WiFi 6) wireless standard:
- 2.4 GHz frequency band.
- 5.0 GHz frequency band.
- Maximum data signaling rate of up to 9.607 Gbps.
- Multi-User Multiple Input / Multiple Output (MU-MIMO).
Refers to directional antenna types suitable for long-range point-to-point bridging links?
- Yagi antenna.
- Dish antenna.
- Parabolic antenna.
Cellular:
- Radio network distributed over land through cells where each cell includes a fixed location transceiver known as base station.
- These cells together provide radio coverage over larger geographical areas.
IEEE 802.3af:
PoE (Power over Ethernet).
IEEE 802.3at:
PoE+.
IEEE 802.3bt:
- PoE++.
- 4PPoE.
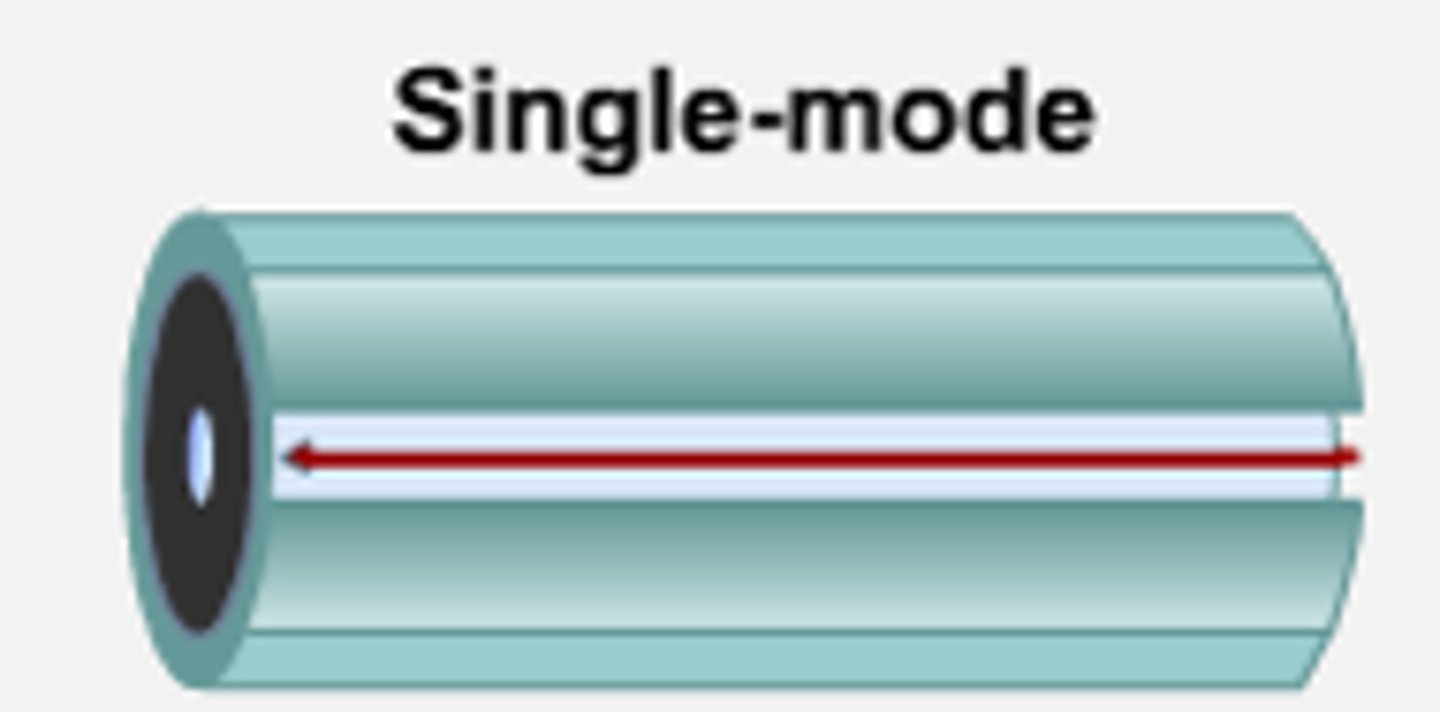
Single-mode Fiber (SMF):
- Uses lasers.
- Longer distance and smaller diameter.
- Used in telecom and CATV networks.
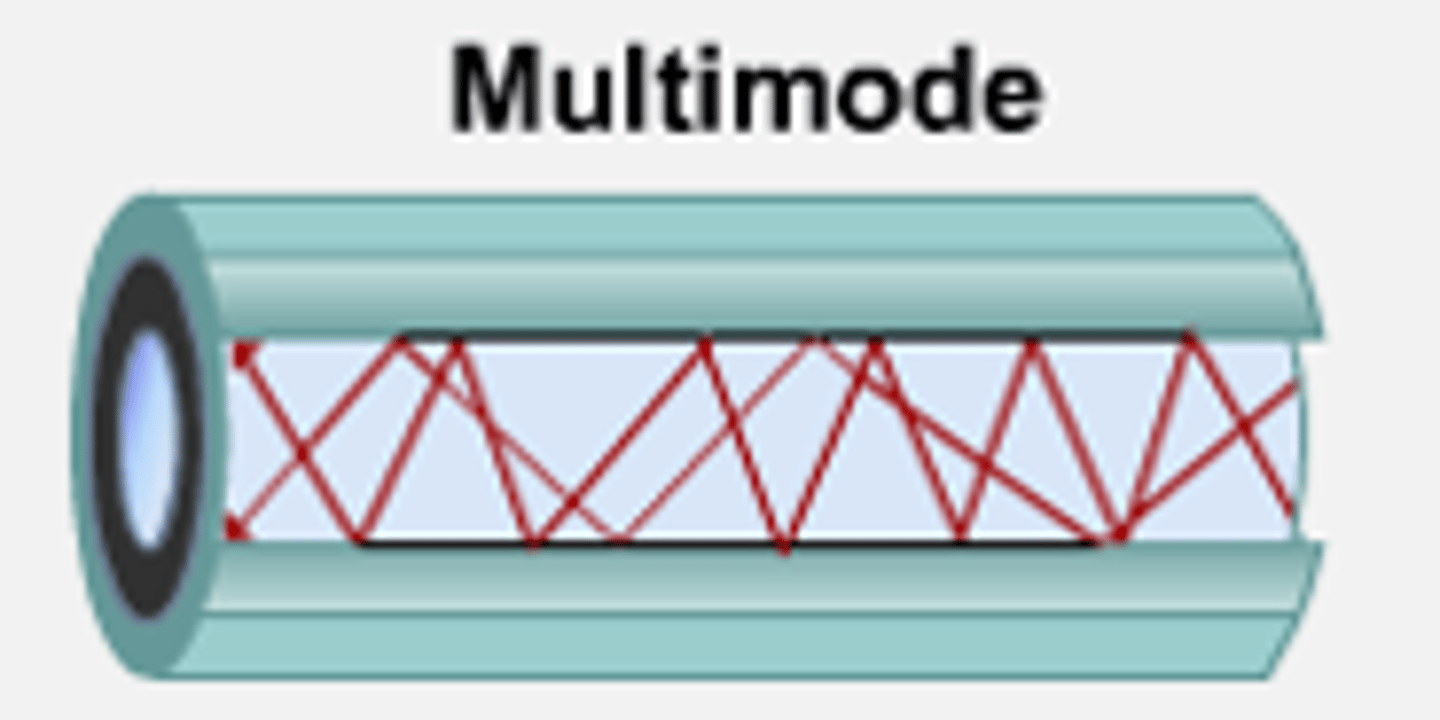
Multimode fiber (MMF):
- Uses LEDs.
- Shorter distance and wider diameter.
- Used in LAN, security systems, and CCTV.
Direct attach copper (DAC) cable:
Allows direct communication between devices over copper wire.

Twinaxial cable:
A variant of coaxial cables, which features two inner conductors instead of one and is used for very-short-range high-speed signals.

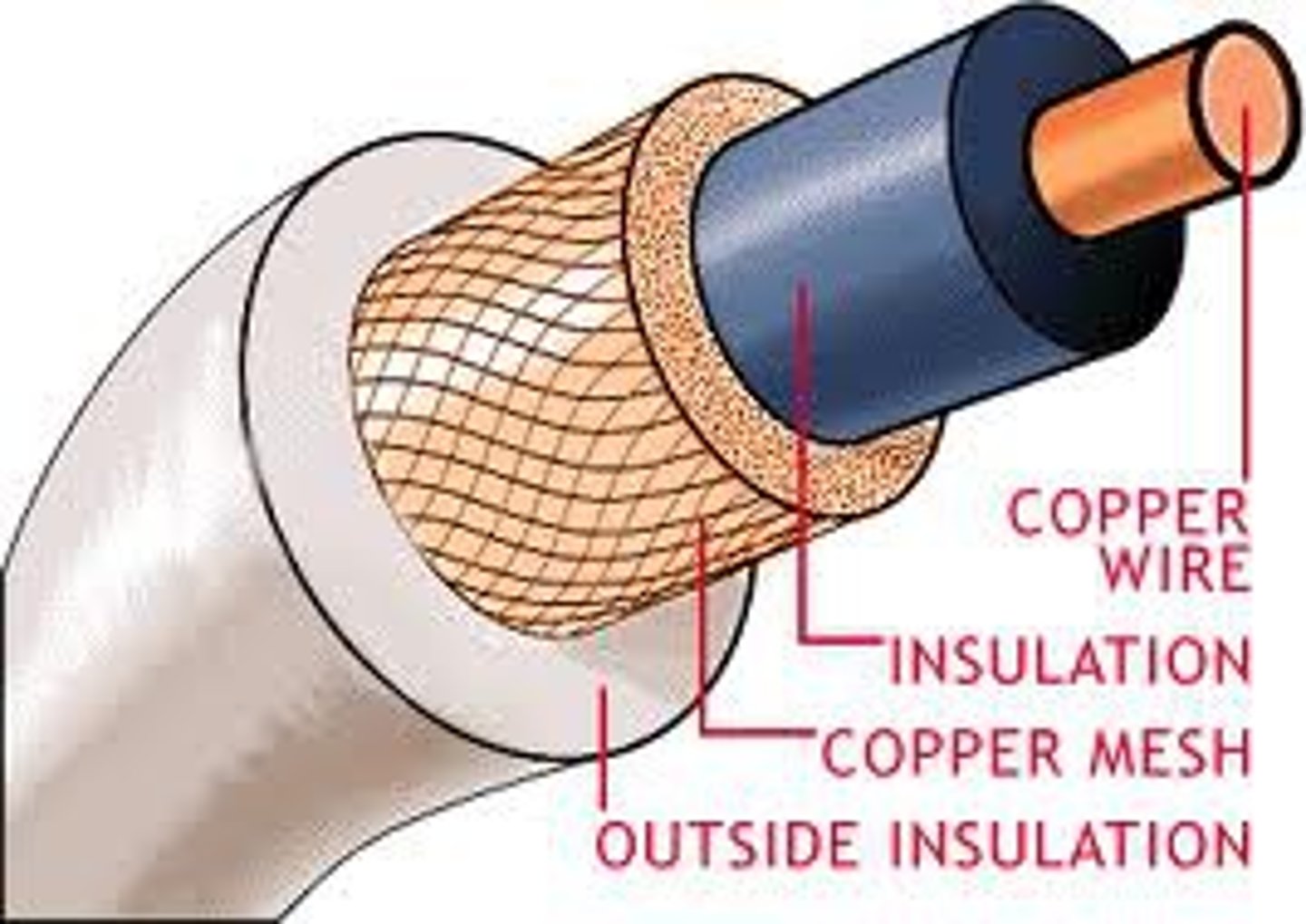
Coaxial cable:
Insulated copper wire; used to carry high-speed data traffic and television signals.
Plenum vs. Non-Plenum Cables:
- Plenum cables are engineered with fire-retardant materials, emitting minimal smoke and toxic fumes in case of fire.
- Non-plenum cables often come at a lower cost than plenum cables.
Ethernet:
A physical and data layer technology for LAN networking.
Protocol:
A set of rules governing the exchange or transmission of data between devices.
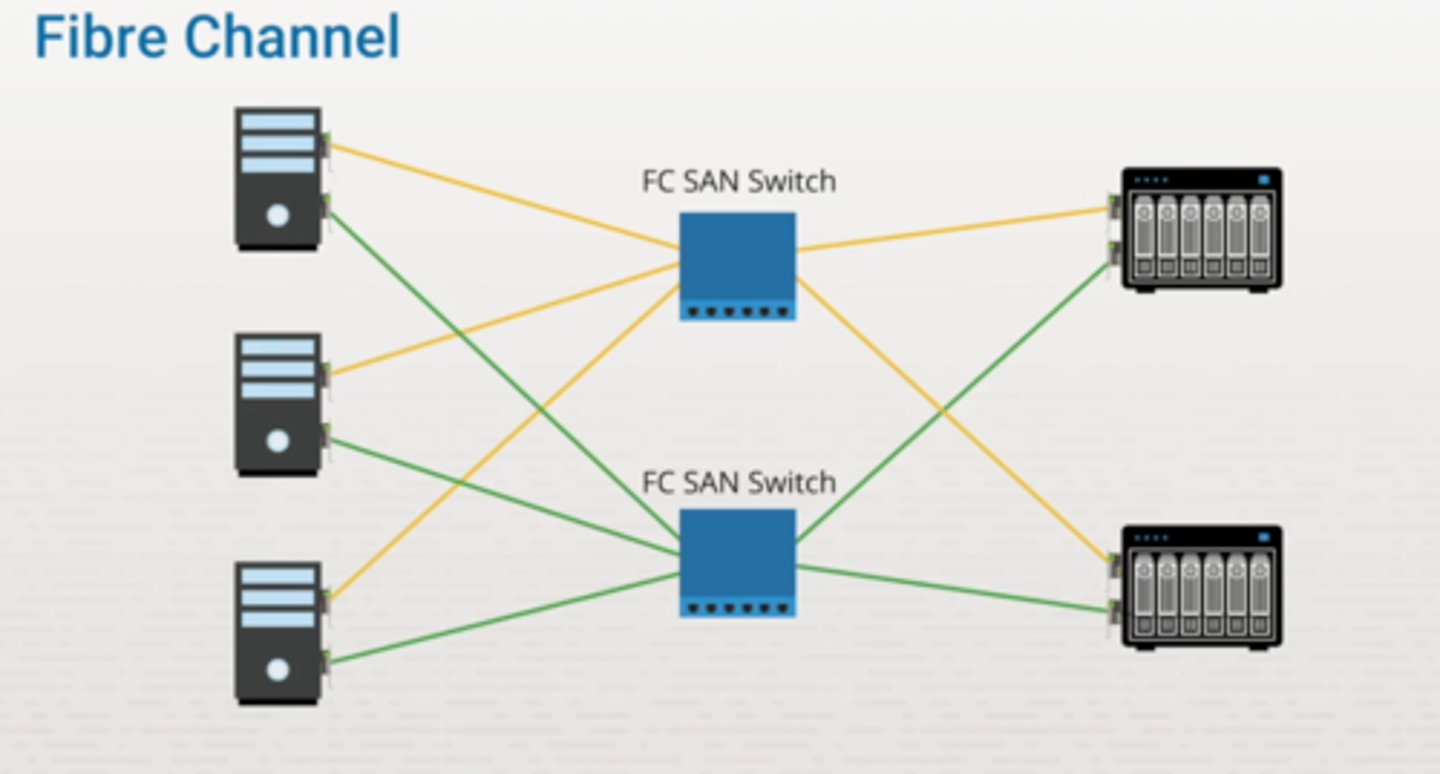
Fibre Channel (FC):
- A high-speed data transfer protocol providing in-order, lossless delivery of raw block data.
- Primarily used to connect computer data storage to servers in storage area networks (SAN) in commercial data centers.
Small form-factor pluggable (SFP):
Fiber optic transceiver module type supporting duplex 1 Gbps (SFP) or 10 Gbps (SFP+) links.

Quad small form-factor pluggable (QSFP):
- Small, high-density pluggable interface used for high-speed data transmission.
- It connects between network devices and fiber optic or copper cables, providing multiple channels for simultaneous data transmission.
