Networking Essentials Lesson 19: Applying Network Hardening Techniques
1/38
Earn XP
Description and Tags
Applying Network Hardening Techniques Objectives: - Compare and contrast types of attacks - Apply network hardening techniques
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
39 Terms
General Attack Types
Understanding attacker types and their motivations
Footprinting and fingerprinting
Discover how the network and its security systems are configured
Enumeration: Attack that aims to list resources on the network, host, or system as a whole to identify potential targets for further attack.
Information gathering attacks
Spoofing
Any type of attack where the attacker disguises his or her identity
Things like phishing and pharming
Denial of Service Attacks (DoS)
Any attack that causes a service to become unavailable to users
May be purely destructive or may allow attacker to spoof the legitimate service
On-path Attacks
Threat actor intercepts communication
path“Man-in-the-Middle (MitM)”
Where a threat actor compromises the connections between two hosts and transparently intercepts and relays all communications between them.
MAC spoofing and IP spoofing
Arbitrarily change address value in packet
Try and circumvent an ACL (access control list) or impersonate a legitimate server
ARP spoofing
Broadcast unsolicited/gratuitous ARP
repliesBecause ARP has no security, all devices in the same broadcast domain as the rogue host trust this communication and update their MAC:IP address cache table with the spoofed address.
Masquerade as MAC address of default gateway
If the attack is successful, all traffic destined for remote networks will be sent to the attacker
Because the threat actor broadcasts endless ARP replies, it overwhelms the legitimate interface.
Rogue DHCP
Configure clients with malicious default gateway/DNS server IP
DHCP communications cannot be authenticated, so a host will generally trust the first offer packet that it receives.
Threat actor can take advantage of this to set their machine to the subnet’s default gateway of DNS resolver.
DNS Poisoning Attacks
DNS poisoning: Attack where a threat actor injects false resource records into a client or server cache to redirect a domain name to an IP address of the attacker's choosing.
Spoofing trusted hosts/sites
(pharming)The attacker can then intercept all the packets directed to mybank.example and bounce them to the real site, leaving the victim unaware of what is happening (referred to as pharming).
Denial of Service (DoS)
Directing all traffic for a particular FQDN to an invalid IP address (a black hole)
Client-side attacks (corrupting the client’s name resolution process)
Change/intercept resolver traffic
Modify HOSTS
Server-side attacks
Hack server and change name records
Pollute server cache
VLAN Hopping Attacks
Send traffic to VLAN that would not normally be accessible
Double tag exploit against weakly configured native VLANs
Masquerade as trunk
Wireless Network Attacks
Rogue access points
Definition: Wireless access point that has been enabled on the network without authorization.
Unauthorized AP creates a Potential backdoor to attack the network
Risks from shadow IT
Evil twins
Definition: Wireless access point that deceives users into believing that it is a legitimate network access point.
Spoofs SSID and BSSID (MAC) of
legitimate AP“compeny” vs “company”
when a user connects to an evil twin, it might be able to harvest authentication information and, if it is able to provide wider network or Internet access, execute an on-path attack to snoop on connections established with servers or websites.
Deauthentication attacks
Definition: Spoofing frames to disconnect a wireless station to try to obtain authentication data to crack.
Cause client(s) to disconnect from AP
This might allow the attacker to interpose the evil twin, sniff information about the authentication process, or perform a denial of service (DoS) attack against the wireless infrastructure.
Distributed DoS Attacks and Botnets
DDoS definition: Attack that involves the use of infected Internet-connected computers and devices to disrupt the normal flow of traffic of a server or service by overwhelming the target with traffic.
Co-ordinated attacks launched by multiple hosts simultaneously
Overwhelm bandwidth
Overwhelm processing resource (flood state table)
Or potentially crash the host system completely
Distributed reflection DoS
Amplification attack
Spoof victim IP to overwhelm it with responses (trying to open connections with multiple servers)
The SYN/ACK responses go to the victim server, rapidly consuming the victim’s available bandwidth
Botnets
Group of compromised hosts used to perpetrate DDoS/DRDoS)
Handler/herders versus bots
Command and control (C&C/C2) network
Malware and Ransomware Attacks
Malware classification by vector
Viruses and worms
These represent some of the first types of malware and spread without any authorization from the user by being concealed within the executable code of another process.
Trojan
Malware concealed within an installer package for software that appears to be legitimate. This type of malware does not seek any type of consent for installation and is actively designed to operate secretly.
Potentially unwanted programs
(PUPs)/Potentially unwanted applications (PUAs)Software installed alongside a package selected by the user or perhaps bundled with a new computer system.
Malware classification by payload
Spyware, rootkit, remote access Trojan
(RAT), ransomware, ...
Ransomware
Spoof shell/dialogs/notifications
Crypto-malware
Password Attacks
Passwords or password hashes can be captured by obtaining a password file or by sniffing the network. If the protocol uses cleartext credentials, then the threat actor can simply read the cleartext password from the captured frames.
Password capture
Plaintext storage and transmission
Password hashes
Password hash cracking
Dictionary
Brute force
The software tries to match the hash against one of every possible combination it could be. If the password is short (under eight characters) and non-complex (using only letters, for instance), a password might be cracked in minutes. Longer and more complex passwords increase the amount of time the attack takes to run.
Protecting password hashes
A threat actor might obtain password hashes from a protocol such as SMB with no encryption configured.
The risks posed by cracking software mean that it is more secure to use end-to-end encryption, such as IPSec or Transport Layer Security (TLS).
This means that all payload data is encrypted, and a network sniffer cannot even recover the password hashes.
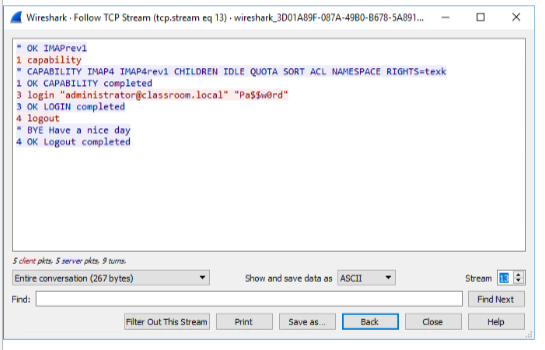
Human and Environmental Attacks
Social engineering or hacking the
humanReasons for effectiveness
Phishing
Social engineering over email
Also uses spoofed resource (website)
Shoulder surfing
Observing password/PIN entry. Like. With your Eyes.
Tailgating and piggybacking
Gaining unauthorized entry to premises
Following closely behind whoever opened the door
Response time on the website that hosts the online version of your product catalog is getting slower and slower. Customers are complaining that they cannot browse the catalog items or search for products. What type of attack do you suspect?
This is some type of Denial of Service (DoS) attack. Specifically, you might suspect a distributed DoS (DDoS) or distributed reflection DoS (DRDoS).
The network administrator at your organization analyzes a network trace capture file and discovers that packets have been intercepted and retransmitted to both a sender and a receiver during an active session. What class of attack has been detected?
On-path attack. Note that this was previously referred to as a man-in-the-middle (MitM) attack.
True or false? To perpetrate an ARP spoofing attack, the threat actor spoofs the IP address of a legitimate host, typically the subnet’s default gateway.
True. The threat actor sends gratuitous ARP replies claiming to own the IP address of the target.
A threat actor forces clients to disconnect from a legitimate access point to try to force them to reconnect to an access point controlled by the attacker using the same network name. What two attack types are being used?
Disconnections are performed using a deauthentication attack, while using a rogue access point to masquerade as a legitimate one is referred to as an evil twin attack.
Analysis of outgoing traffic shows connections by IP cameras to unidentifiable domain names. What type of traffic has been detected?
This is command and control (C-and-C or C2) traffic between a handler and botnet of compromised IP camera devices, often called an Internet of Things (IoT) botnet.
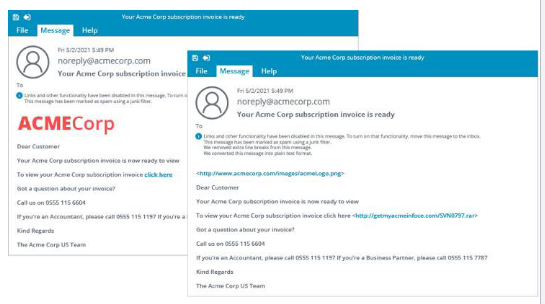
Employees have received emails prompting them to register for a new benefit package. The link in the mail resolves to a malicious IP address. What type of attack is being performed?
This is a phishing attack that combines social engineering (techniques that convince users that a message is genuine) with a spoofed resource.
Device and Service Hardening
Hardening means applying a secure configuration to each network
host or applianceChange default passwords
Enforce password complexity/length requirements
Configure role-based access
Disable unneeded network services
Disable unsecure protocols
Endpoint Security and Switchport Protection
What is endpoint security? Endpoint security is a set of security procedures and technologies designed to restrict network access at a device level.
Endpoint security contrasts with the focus on perimeter security established by topologies such as screened subnets and technologies such as firewalls.
Endpoint security is designed not to replace perimeter security but to supplement it, creating defense in depth.
Disable unneeded switchports
Restrict physical access/unplug patch cord
Administratively disable port
Assign to black hole VLAN
Configure protection mechanisms
MAC Filtering and Dynamic ARP Inspection
Applying an access control list to a switch or access point so that only clients with approved MAC addresses can connect to it.
dynamic ARP inspection (DAI): a switch port security feature that prevents a host attached to an untrustued port from flooding the segment with tons of ARP replies
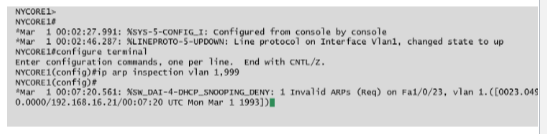
DHCP Snooping
Configuring DHCP snooping causes the switch to inspect DHCP traffic arriving on access ports to ensure that a host is not trying to spoof its MAC address.
It can also be used to prevent rogue DHCP servers from operating on the network.
With DHCP snooping, only DHCP offers from ports configured as trusted are allowed.
Neighbor Discovery (ND) Inspection and
Router Advertisement (RA) GuardPerform similar functions to DAI and DHCP snooping for IPv6 networks
Port Security (IEEE 802.1X Port-Based
Network Access Control)Preventing a device attached to a switch port from communicating on the network unless it matches a given MAC address or other protection profile.
VLAN and PVLAN Best Practices
Private VLAN (PVLAN)
What is it? Method of isolating hosts to prevent hosts within the same VLAN from communicating directly.
Further segment traffic within host/primary VLAN
Promiscuous, isolated, and community ports
Promiscuous - can communicate with all ports in all domains within the PVLAN. Usually the port which routed or DHCP traffic is sent
Isolated - can communicate with the promiscuous port only.
Community - can communicate with the promiscuous port and with other ports in the same community.
Default VLAN and native VLAN
VLAN ID 1 is default VLAN
Default VLAN ID (1) for all unconfigured switch ports.
Native VLAN contains untagged traffic on trunks
VLAN ID used for any untagged frames received on a trunk port.
The same ID should be used on both ends of the trunk and the ID should not be left as the default VLAN ID (1).
Native VLAN is also VLAN 1 by default
Change to unique value on both ends of trunk
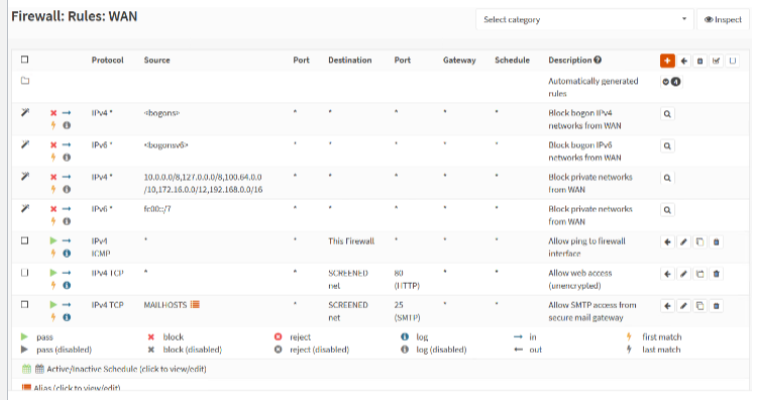
Firewall Rules and ACL Configuration
Implicit deny: Firewall ACL rule configured by default to block any traffic not matched by previous rules.
Explicit deny: Firewall ACL rule configured manually to block any traffic not matched by previous rules.
Network access control list (ACL)
Top-to-bottom
Default block (implicit deny)
Explicit deny
Tuples
iptables
Chains (INPUT, OUTPUT, and
FORWARD)INPUT: affecting incoming connections. For example, if a user attempts to SSH into the Linux server, iptables will attempt to match the source IP address and destination port to a rule in the input chain.
OUTPUT: For outgoing connections. For example, if you try to ping an FQDN such as comptia.org, iptables will check its output chain to see what the rules are regarding ping and comptia.org (or the IP address that comptia.org resolves to) before deciding to allow or deny the connection attempt.
FORWARD: Used for connections that are passing through the host, rather than being delivered locally. Used when configuring the host as a network firewall.
Stateful rules
Rules can be assigned to these chains, or new chains can be created and then linked to the standard system chains to affect traffic flow. To view the current status of the iptables and the volume of traffic using the chains, use the command:
iptables -L -v
Control Plane Policing
Control, data, and management planes
Control and management require CPU resource
Control and management must always by kept “open”
Sufficient bandwidth
Sufficient processing resource
Control plane policing policy
Designed to mitigate route processor vulnerabilities
ACL-based filters
Rate-limiting
Wireless Security
Preshared keys (PSKs)
Group authentication allows stations to connect to the network using a shared passphrase
Extensible Authentication Protocol
An AP to implement a similar port security mechanism to switches
Captive portal
Redirecting stations to a secure web page
MAC filtering
Accept or deny list of known MAC addresses
Geofencing
Used to ensure that the station is within a valid geographic area to access the network
Antenna placement and power levels
The prescence of an unusually strong transmitter may mean an evil twin rogue access point
Wireless client isolation
Can configure access point to change it so that stations can only communicate via gateway rather than client to client. Peer-to-peer traffic is dropped by the AP.
You can do this through a VLAN
Guest network isolation
IoT Access Considerations
Audits to prevent use of shadow IT
Secure administration interfaces
Include IoT in patch and vulnerability management
Isolate management and monitoring traffic for embedded systems
Audit supplier security policies and procedures regularly
Patch and Firmware Management
Monitor security and patch advisories
Appliance firmware updates versus OS patches
Firmware upgrade procedure
Downgrading/rollback firmware
Configuration backup
The network administrator configures a switch with custom privilege levels and assigns commands to each. What type of best practice network hardening will this configuration support?
Role-based access, where different administrator and operator groups are assigned least privilege permissions.
A technician configures a switch with an IP address and shared secret of a network authentication server. What type of best practice network hardening is being performed?
Port security or IEEE 802.1X Port-Based Network Access Control.
What switch configuration feature could you use to prevent web servers in the same subnet from communicating with one another?
This can be configured using a private VLAN. The servers are all placed in the same host VLAN and communicate out of the VLAN/subnet via the promiscuous port. Each server port is configured as an isolated port. The isolated ports are not able to communicate directly.
What is the default rule on a firewall?
A system-defined rule that denies anything not permitted by the preceding rules. This is also referred to as an implicit deny rule. An explicit deny is one configured manually by the administrator.
Network hosts are flooding a switch’s SSH port with malicious traffic. The switch applies a rate-limiting mechanism to drop the traffic. What best practice network hardening control is being used?
Control plane policing. The SSH port carries management traffic. Malicious management or control traffic can be used to perform a denial of service (DoS) attack against a network appliance by overloading its general purpose CPU. A control plane policing policy protects both control and management channels against this type of attack.
How would a router appliance be patched to protect against a specific vulnerability described in a security advisory?
This type of OS does not support patching of individual files, so the whole OS has to be replaced with a new version. Vendors keep track of which version first addresses a specific security advisory.
A cyber security technician is requested to investigate a matter in which several customers have lodged complaints about computer issues after visiting the company site. Upon closer observation, the technician discovers that an unknown IP address replaced the valid IP address. What type of attack occurred in this incident?
On-path attack
DNS Poisoning
Malware
Distributed DoS (DDoS)
Answer: 2 (DNS Poisoning)
DNS poisoning is an attack that compromises the name resolution process.
An on-path attack is a specific spoofing attack where a threat actor compromises the connection between two hosts and transparently intercepts and relays all communications between them.
Many of the intrusion attempts perpetrated against computer networks depend on the use of malicious software or malware. Malware can be defined simply as software that does something bad from the perspective of the system owner.
A distributed DoS (DDoS) attack is launched simultaneously by multiple hosts. Some types of DDoS attacks aim to consume network bandwidth, denying it to legitimate hosts. Others cause resource exhaustion on the hosts processing requests, consuming CPU cycles and memory.
A cyber consultant is brought into a department to create security procedures and technologies designed to restrict network access at an end user device level. What is the consultant focusing on?
Firewall access control lists (ACLs)
Control plane policing
Endpoint security
Hardening
Answer: 3 (Endpoint security)
Endpoint security is a set of security procedures and technologies designed to restrict network access at a device level.
A network technician configures firewall access control lists (ACLs) based on the principle of least access. This is the same as the principle of least privilege; only allow the minimum amount of traffic required to operate valid network services and no more.
A control plane policing policy mitigates the risk from route processor vulnerabilities. Such a policy can use ACLs to allow or deny control traffic from certain sources and apply rate-limiting if a source threatens to overwhelm the route processor.
Deploying systems in a secure configuration are known as device hardening.
A network technician needs to strengthen the security of the company network by minimizing the amount of traffic required for the operation of the valid network services, and no additional access to be permitted. What is the technician placing into the network?
Firewall access control lists (ACLs)
Control plane policing
Endpoint security
Hardening
Answer: 1 (Firewall access control lists (ACLs)
A network technician configures firewall access control lists (ACLs) based on the principle of least access. This is the same as the principle of least privilege; only allow the minimum amount of traffic required to operate valid network services and no more.
A control plane policing policy mitigates the risk from route processor vulnerabilities. Such a policy can use ACLs to allow or deny control traffic from certain sources and apply rate-limiting if a source threatens to overwhelm the route processor.
Endpoint security is a set of security procedures and technologies designed to restrict network access at a device level.
Deploying systems in a secure configuration are known as device hardening.
A department head contacts a cyber consultant declaring that the team is locked out and cannot conduct any activity. While working on the system, the consultant notices a demand for money, or the department will never get their data back. What is this type of attack called?
DRDoS
DDoS
Trojan
Ransomware
Answer: 4 (Ransomware)
Ransomware is malware that extorts money from victims. One class displays threatening messages, requiring Windows be reactivated or suggesting police locked the computer for illegal activity.
A more powerful TCP SYN flood attack is distributed reflection DoS (DRDoS) or amplification attack. The adversary spoofs an IP address and opens connections with multiple servers directing their SYN/ACK responses to the victim server.
A distributed denial of service (DDoS) attack is launched simultaneously by multiple hosts. Some attacks aim to consume network bandwidth. Others cause resource exhaustion on the hosts' processing requests.
A trojan is a malware concealed within an installer package for software that appears to be legitimate. A trojan does not seek consent for installation and operates secretly.
A cyber security technician speaks with a department that has voiced concern regarding tech issues. The technician discovered that the employee had received an email containing an attachment from an outside party. Curious about what the document contained, the employee clicked on the link. The next day, the employee noticed that some of the software was not working correctly, and some important documents were no longer accessible. What was likely the cause of this issue?
On-path attack
DNS Poisoning
Malware
DDoS
Answer: 3 (Malware)
Many of the intrusion attempts perpetrated against computer networks depend on malicious software or malware. Malware can be defined simply as software that does something bad from the perspective of the system owner.
An on-path attack is a specific spoofing attack where a threat actor compromises the connection between two hosts and transparently intercepts and relays all communications between them.
DNS poisoning is an attack that compromises the name resolution process.
A distributed DoS (DoS) attack is launched simultaneously by multiple hosts. Some types of DDoS attacks aim to consume network bandwidth, denying it to legitimate hosts
A cyber security technician responds to a department experiencing degraded network bandwidth, and customers call the department saying they cannot visit the company website. What is likely causing the issue?
On-path attack
DNS Poisoning
Malware
Distributed DoS (DDoS)
Answer: 4 (Distributed DoS (DDoS))
A distributed DoS (DoS) attack is launched simultaneously by multiple hosts. Some types of DoS attacks aim to consume network bandwidth, denying it to legitimate hosts.
An on-path attack is a specific spoofing attack where a threat actor compromises the connection between two hosts and transparently intercepts and relays all communications between them.
DNS poisoning is an attack that compromises the name resolution process.
Many of the intrusion attempts perpetrated against computer networks depend on malicious software or malware. Malware can be defined simply as software that does something bad from the perspective of the system owner.
During a routine investigation of the network, the cyber specialist identifies that an on-path attack has compromised the network. What is another name for this type of attack?
MitM
DDoS
VLAN Hopping
DNS Poisoning
Answer: 1 (MitM)
On-path attacks are also called "Man-in-the-Middle (MitM)" attacks.
A distributed denial of service (DDoS) attack is launched simultaneously by multiple hosts. Some types of DDoS attacks aim to consume network bandwidth, denying it legitimate hosts. Others cause resource exhaustion on the hosts processing requests, consuming CPU cycles and memory.
VLAN hopping is an attack designed to send traffic to a VLAN other than the one the host system is in.
DNS poisoning is an attack that compromises the name resolution process. The attacker replaces a valid IP address for a trusted website, such as mybank.example, with the attacker's IP address. The attacker then intercepts the packets directed to mybank.example, and bounces them to the real site, leaving the victim unaware.
A cyber consultant needs to modify the company's access control lists to minimize network traffic. During configuration, the consultant can use a command-line utility provided by many Linux distributions that allow administrators to edit the rules enforced by the Linux kernel firewall. What is the command-line utility used?
iptables
ipconfig
nmap
tcpdump
Answer: 1 (iptables)
iptables is a command-line utility provided by many Linux distributions that allow administrators to edit the rules enforced by the Linux kernel firewall. Iptables works with the firewall chains, which apply to the different types of traffic passing through the system.
ipconfig is a tool used to gather information about the IP configuration of a Windows host.
Nmap is an ideal tool for scanning remote hosts to discover which ports they have open and the applications or services running them. It does not capture data packets.
The tcpdump command-line utility is a common packet analyzer used to display the contents of the .pcap file.
An organization contacts the cyber security team and requests a feature to provide secure wireless network access. Select the appropriate answers that support this request. (Select all that apply.)
Preshared keys (PSKs)
Captive Portal
Geofencing
VLAN
Answer: 1, 2, 3 (Preshared keys (PSKs), Cpative Portal, Geofencing, VLAN)
Group authentication allows stations to connect to the network using a shared passphrase, which generates a preshared key (PSK).
A guest network might redirect stations to a secure web page to perform authentication. The user must authenticate to the page and meet other administrator-set requirements, such as accepting a use policy, before the station can use the network.
Geofencing can be used to ensure that the station is within a valid geographic area to access the network, such as ensuring the device is within a building rather than trying to access the WLAN from a car park or other external location.
The virtual LAN (VLAN) feature of managed Ethernet switches typically deploys to enforce segmentation policies.
A cyber technician needs to draft a policy for the organization to mitigate the risk from route processor vulnerabilities. What is the name of this type of policy?
Firewall access control lists (ACLs)
Control plane policing
Endpoint security
Hardening
Answer: 2 (Control plane policing)
A control plane policing policy mitigates the risk from route processor vulnerabilities. Such a policy can use ACLs to allow or deny control traffic from certain sources and apply rate-limiting if a source threatens to overwhelm the route processor.
A network technician configures firewall access control lists (ACLs) based on the principle of least access. This is the same as the principle of least privilege; only allow the minimum amount of traffic required to operate valid network services and no more.
Endpoint security is a set of security procedures and technologies designed to restrict network access at a device level.
Deploying systems in a secure configuration are known as device hardening.