[2] Understanding Spam and Phishing in Networked Communications
1/22
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
23 Terms
Spam
Unwanted messages sent via email or social media.
Anti-Spam Industry
Multi-billion dollar sector combating spam messages.
Spam Detection Challenge
Balancing precision and recall in identifying spam.
Precision
Avoiding false positives in spam detection.
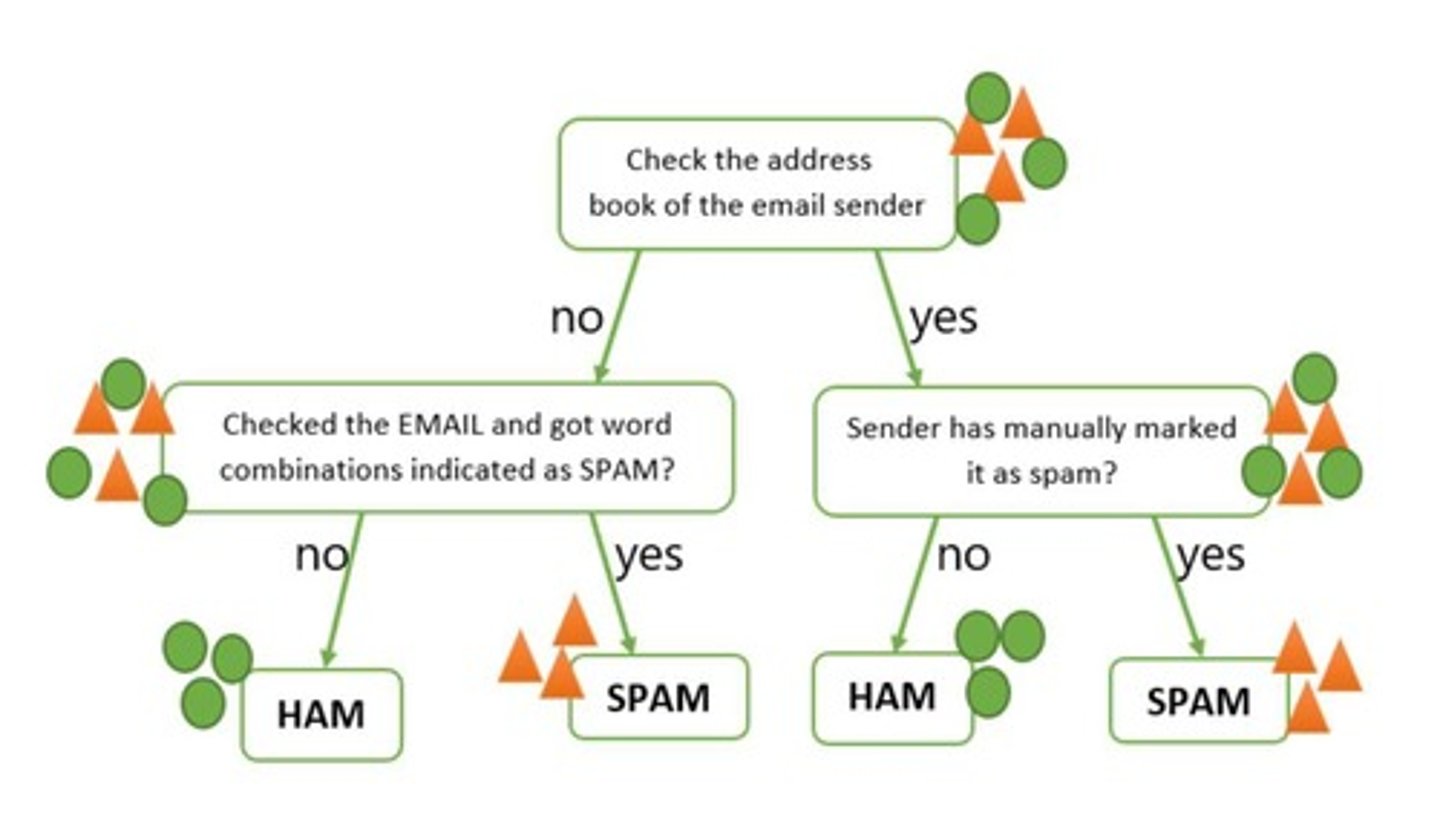
Bayesian Filtering
Analyzes words to classify messages as spam.
Random Forests
Machine learning model for spam detection.
Support Vector Machines (SVM)
Algorithm used to classify spam messages.
Neural Networks
Advanced model for processing spam data.
Canadian Anti-Spam Legislation (CASL)
Regulates commercial electronic messages in Canada.
Commercial Electronic Message (CEM)
Message encouraging participation in commercial activities.
Express Consent
Explicit permission required to send CEMs.
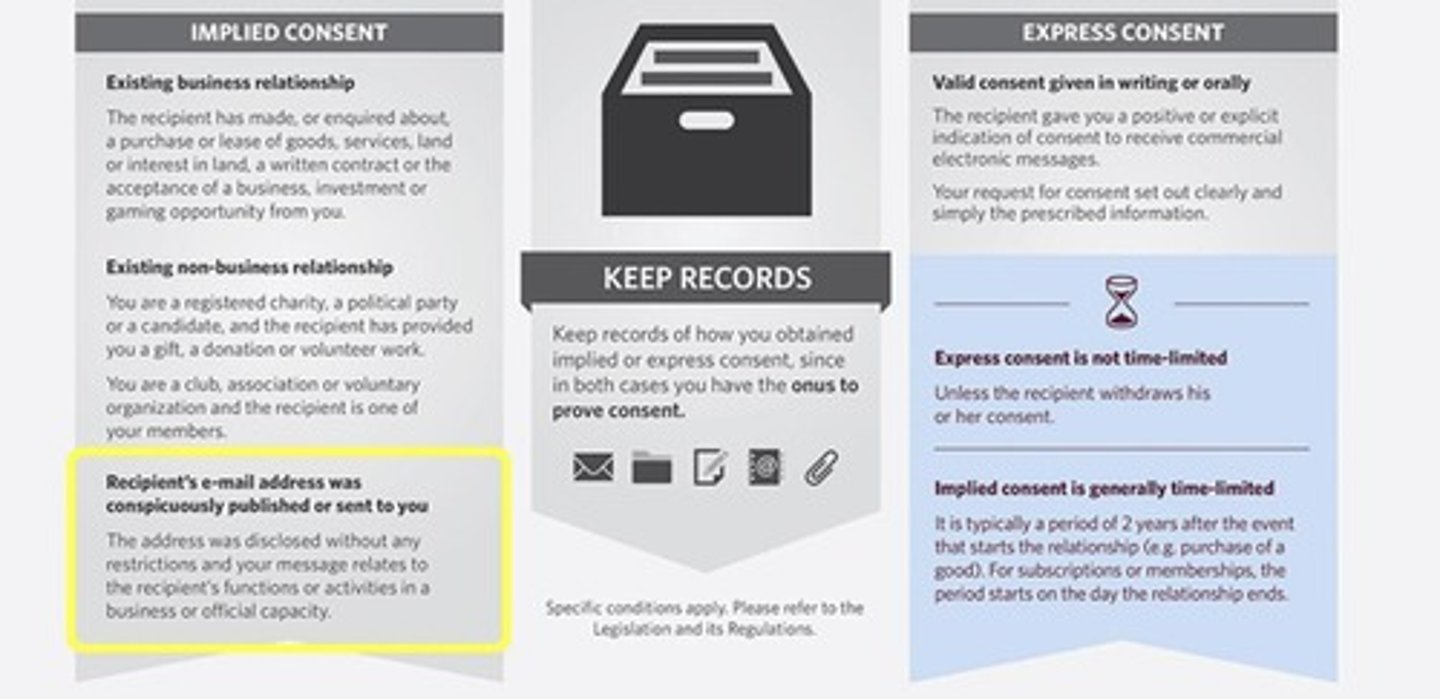
Implied Consent
Assumed permission based on prior interactions.
Phishing
Cybercrime to acquire private information via deception.
Vishing
Voice phishing conducted through phone calls.
Smishing
Phishing via deceptive text messages.
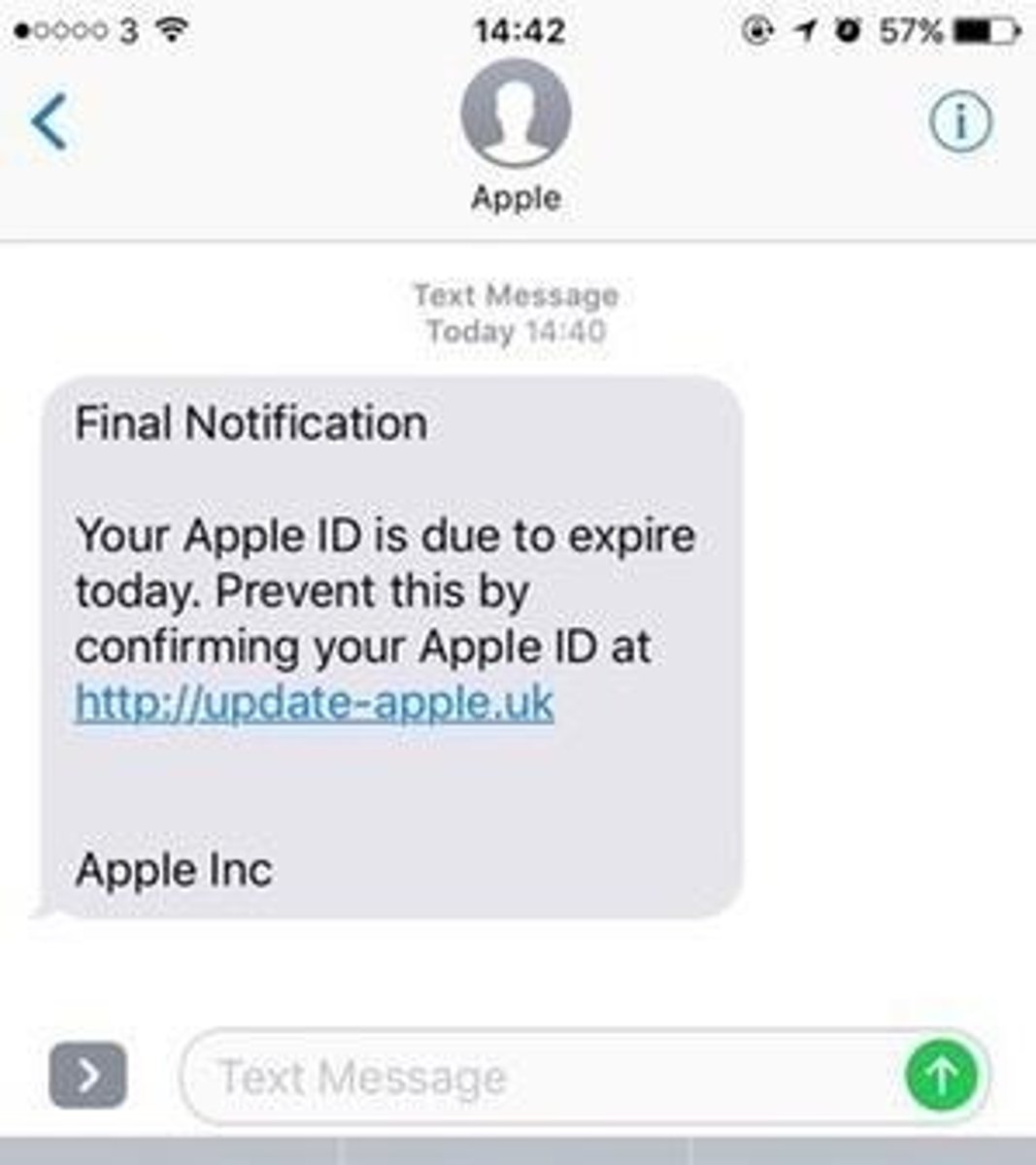
Phishing Email Signs
Unidentified sender, urgency, suspicious links.
Identity Theft
Stealing personal information for fraudulent use.
Telegraph
Early communication technology using electrical signals.
Mass Communication
Dissemination of information to large audiences.
Big Data
Large datasets analyzed for insights and trends.
Surveillance Risks
Potential dangers associated with monitoring technologies.
Spam-based Advertising
Profitable business model leveraging spam messages.
Spam Detection Models
Algorithms processing metadata, content, and context.