computer science aqa gcse paper 2
1/99
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced | Call with Kai |
|---|
No analytics yet
Send a link to your students to track their progress
100 Terms
What is a computer network?
two or more computers connected together to exchange data and information
what are benefits of networks
- sharing files is easier(access files at the same time)
- hardware can be shared between multiple devices
- software can be updated/ installed at more than computer at once
- communication between devices is cheaper
- user accounts can be stored centrally (log ins from any device)
what are risks of networks
- expensive to set up (extra hardware needed )
- can be vulnerable to hacking
- some networks are dependent on servers
- large networks are difficult to manage (extra people needed to manage it )
what is a PAN?
- personal area network
- connects devices in short range
- usually wireless (e.g. bluetooth)
- doesnt require extra hardware ( other than devices )
What is a LAN?
- local area network
- small geographical area located on a single site
- wired ( ethernet cables) or wireless ( wifi)
- found in offices, schools, uni's
- all hardware is owned by organisation using it
what is a WAN?
- wide area network
- connects LANs that are in different geographical locations
- conected using phone lines, satellite links, or radio waves
- bigges wan= internet
- organistations hire infrastructure due to higher price
Benefits of wireless networks
- more convenient ( you can move while using the device)
- cheaper and better for environment ( no need for wires)
- easy to add more users ( no extra wires)
risks of wireless networks
- less secure ( visible access points on wireless = easy hacking)
- distance from WAP(physical obstructions= reduced signal strength)
- lower bandwidth and less reliable
star topology
All devices are directly connected to the central switch or server that controls network
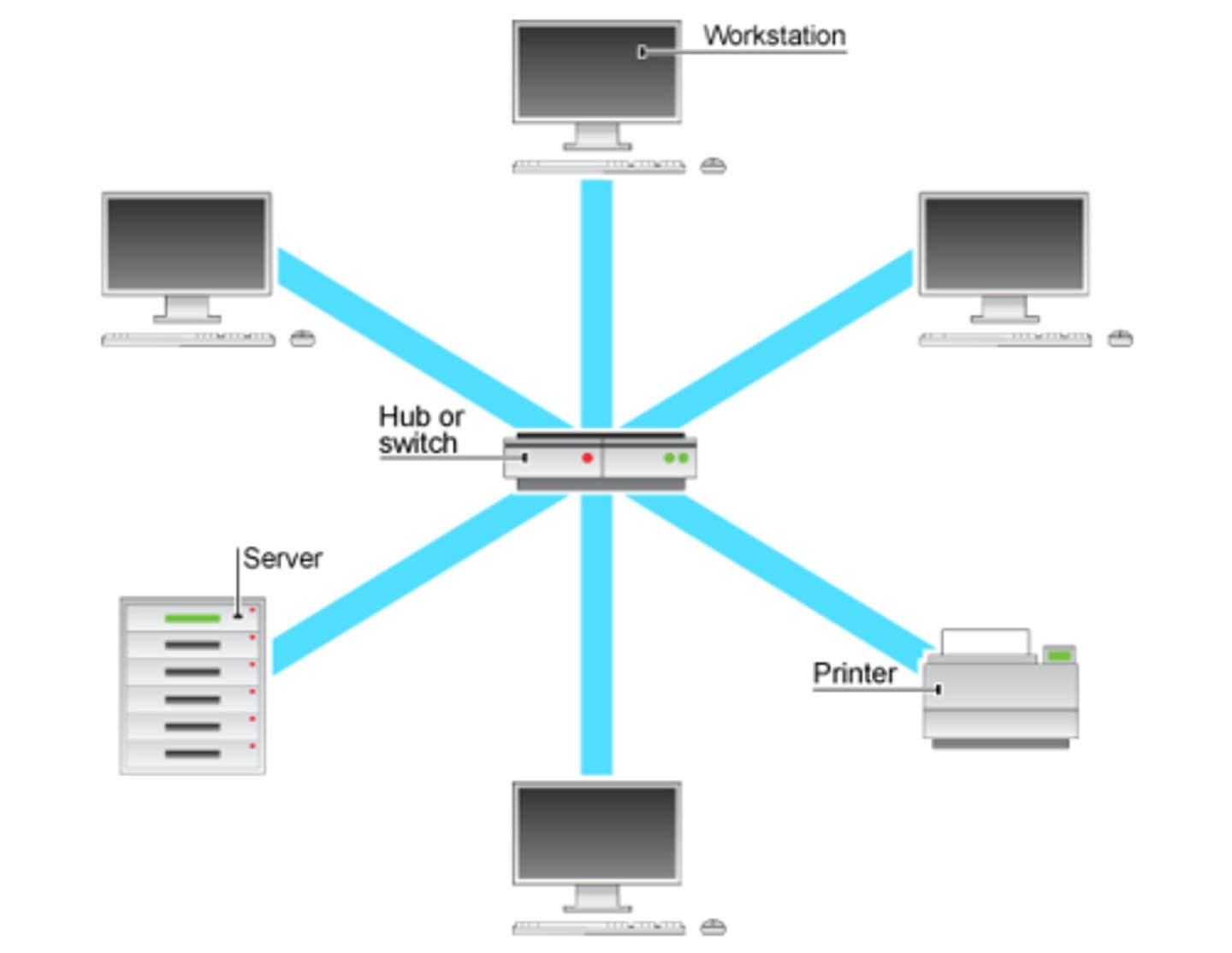
Star Topology Advantages and Disadvantages
pros:
- if 1 device fails, the rest continues to work
- easy to add more devices ( just an extra cable needed)
- tends to have better performance ( all devices can transmit at the
same time as it goes to central device)
- very few data collisions
cons:
- every device needs a cable to connect to server ( expensive)
- switch is very expensive
- is switch breaks, the whole network is affected
- maximum connections is determined by server ( if more
connections are needed a new server must be bought)
Bus Topology
Network configuration wherein all computers connect to the network via a central bus cable. two terminators are on the ends of the bus to stop data reflecting and causing interference.
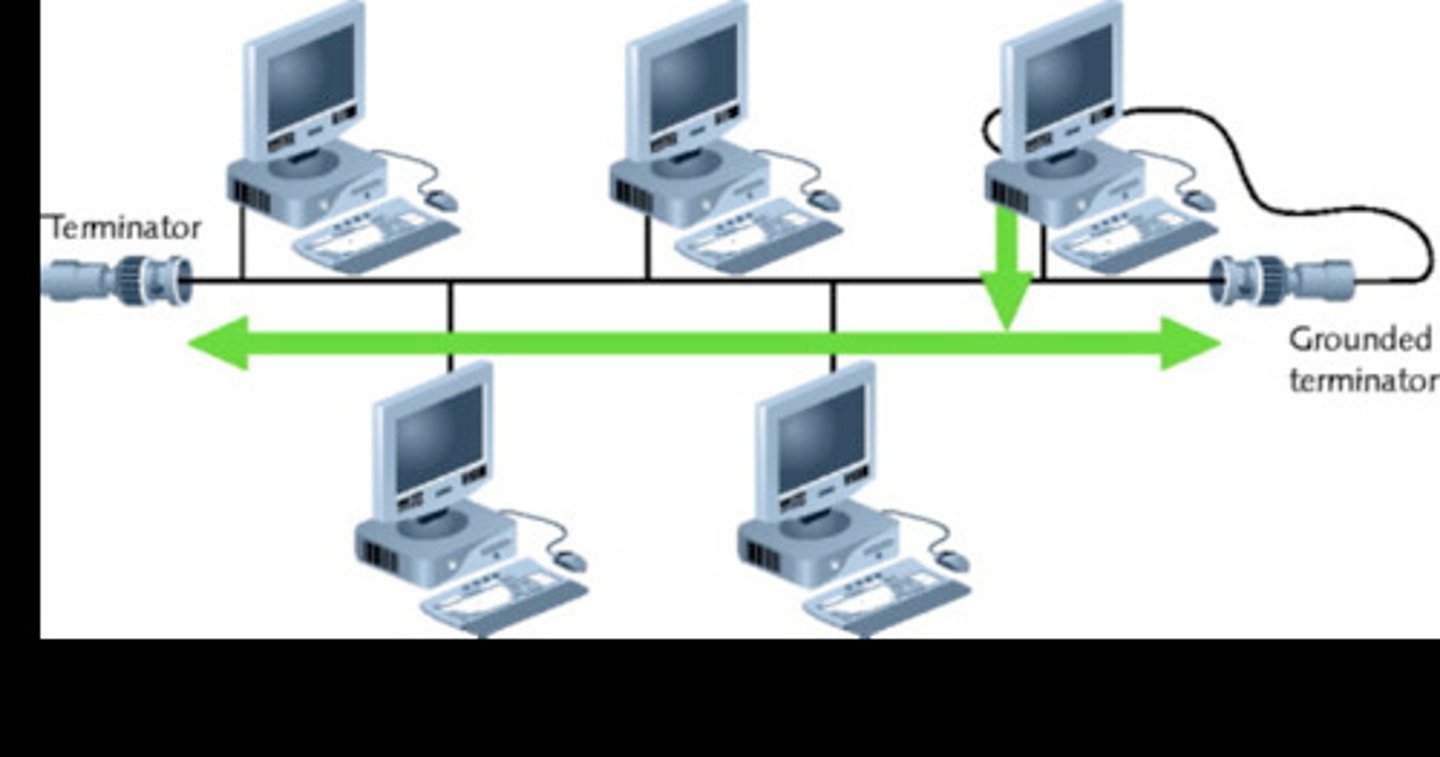
Bus Topology Advantages and Disadvantages
pros :
- network is unaffected if device fails
- arent dependent on central switch
- relatively cheaper to set up ( multiple cables not needed)
cons:
- data collisons are commen(data must then be resent= slow network)
- more devices= higher data collison chance
- slow network as there is a queue on data transmittion
- if bus cable gets broken, network splits, no terminatiors on split bus ends= data reflection= network shut down
Network Protocols
a set of rules for how devices communicate and holw data is transmitted across a network.
TCP/IP Model
4. application layer
3. transport layer
2. internet layer
1. link layer
application layer
providing networking services to applications
e.g. turning data into windows
examples: HTTP, FTP, SMTP
transport layer
setting up communications between two devices, splitting data into packets and checking packets are correctly sent and delivered
examples: TCP, UDP
internet / network layer
adding IP addresses to data packets, directig them between devices and handeling traffic. used by routes
examples: IP
link layer
passing data over the physical network. responsible for how data is sent as electrical signals over cables, wireless and other hardware,
e.g. NICs and for interpreting signals using device drivers
examples: Wi-Fi, ethernet
HTTP
-Hypertext Transfer Protocol
-used by web browsers to access websites and communicate web servers
HTTPS
-Hypertext Transfer Protocol Secure
-encrypts all HTTP information sent and received
TCP
Transmission Control Protocol
UDP
User Datagram Protocol
IP
Internet Protocol
ethernet
-a physical and data layer technology for LAN networking
- family of related protocols rather than a single
protocol
Wi-Fi
-Wireless local area network that uses radio signals to transmit data
-family of related protocols rather than a single
protocol
- Wi-Fi is a trademark and that the generic term for
networks of this nature is WLAN.
FTP
-File Transfer Protocol
- used to access, edit and move files between devices on a network.
SMTP
-Simple Mail Transfer Protocol
-used to send emails. also used to transfer emails between servers
IMAP
-Internet Mail Access Protocol
- used to retrieve emails from a server
network security
prevention of allowing unauthorised access to data, misuse, modification of data, including installing viruses or other malware.
Authentication
prevention of unauthorised access, by:
- passwords- simple method of checking someones identity
- biometrics- using scanners to identify people
- email confirmation- used by web services that require account
registration to confirm the email address belongs to the person
registering
- CAPTCHA- prevents programs from automatically creating
accounts, etc
encryption
-when data is translated into code, so that only someone with the correct key can access it, meaning unauthorised users cannot read it. -encrypted text is called cipher text, non-encrypted text is called plain text.
-encryption is essential for sending data over a network securely.
MAC address filtering
- a way of making sure the only people on the network are trusted
users.
-it checks the unique identification (MAC address) of each device that tries to connect to the network
-it only lets allowed devices join the network
-allows devices to access, or be blocked from accessing a network based on their MAC address
firewall
- example of anti-malware software
- network security system that monitors ad controls all incoming and outgoing network data transfer based on a set of 'security rules'
- usually used by companies to prevent unauthorised access on their network
anti malware software
-designed to stop malware from damaging an organisations network and the devices on it
automatic software updates
-used to patch any identified security holes in a piece of software.
- security that is unpatched or outdated could be more easily exploited by hackers, malware and viruses
cyber security
the processes, practices and technologies designed to protect networks, computers, programs and data from attack, damage or unauthorised access.
pharming
- when a user is directed to a fake version of a website
- the user is instructed in input their personal information, this is saved for the criminal to use
-pharming is often carried out using malware that autimatically directs people from legitimate sites to fake ones
- using anit-malware software reduces these risks
- internest browsers can have web filters to prevent users from accessing fake sites
phishing
- when criminals send emails or texts to people claiming to be from a well-known buisness/ known person.
- the emails often lead to fake websites
- the emails are sent out to thousands of people, in hope that some will believe the email is legitimate
- many email programs, browsers and firewalls have anti-phishing features that reduce the number of emails recieved
- giveaways of phishing= grammar and spelling errors, indirective greeting, threats
blagging
-when someone makes up a story or pretends to be someone they are not to persuade the victim to share information/ do things they would not normally do
- money is often asked for by using the story that one of the victims friends is stuck in a foreign country
- criminals use these tactics to pressure people into doing things without thinking
- to reduce this, security measures should be used that canr be given away, e.g. biometrics
shouldering
- watching and observing a persons activity (typically over their shoulder)
- e.g. spying someones PIN number at a cash machine or watching someone put their password into a secured computer
- it is easy to shoulder someone as it does not require any expertise or planning
- risks can be reduced by being discreet, e.g. covering the keypad when entering the PIN number
malicious code
- code designed to cause harm or gain unauthorised access to a computer system.
- it often downloaded on a device without someones consent
spyware
-type of malware
-gathers information about a person or organisation without their knowledge
- used to track and store users' movements on the internet
- sometimes changes are made in browser or software settings
- personal details can also be extracted
adware
- analyses which websites a user visits and then presents adverts for products the user is likely to be interested in
- sometimes integrated into free software so the developer can gain back some development costs. many companies have their products advertised in this way.
-not always illegal
trojan
- a program that hides in a desirable software but performs an alternative purpose
- users usually download trojan software thinking it will benefit them, but instead it has a negative hidden purpose
- trojan causes computer crashes, spread of malware, corruption of data, reformation of disks, or access to sensitive information
computer virus
-a program downloaded onto the computer without the users knowledge with the purpose of doing harm
-includes instructions on how to replicate
removable media
- data threat and virus infection
- e.g removable hard drives or USB's
- if something is taken from a school computer on a USB to a students home, and the home computer has a virus, the virus can be spread onto the USB. this will then affect the school computer when plugged in next, which can then affect the whole school network.
weak and default passwords
-default password= password given so that an account can be set up
- weak password= password that can be easily guessed
Misconfigured access rights
- Access rights set up what can and cannot be seen when someone logs into a system.
-If these are not set up correctly in an email server, a person may be able to see someone else's emails.
-If a person accesses an account that they do not have permission to see, they might be breaking the law.
Unpatched/outdated software
- Patching is the process of updating software to fix a problem or add a new feature.
- Many programs will automatically update to make sure they have the latest patches installed.
-This helps to ensure the program runs correctly and protects the computer from new threats.
-Most anti-virus software will frequently update itself so that it is able to recognise the latest computer viruses and malware.
-These updates will always be one step behind the people creating the malware, but regularly updating and patching software will reduce the vulnerability of a computer system.
Penetration Testing
Penetration testing is the process of attempting to gain access to resources without knowledge of usernames, passwords and other normal means of access.
white box testing
-stimulates a malicious insider who has knowledge of the current system
-they will be given user credentials to see what can be done with them
- this identifies possible weaknesses
black box testimg
- stimulates an external cyber attack
- the person carrying out the attack will not be given any credentials
- they have to try and hack the organisation in anyway possible to find gaps in the security.
how are unicode and ascii different
sample rate
number of samples of an anologue sound taken per second. the higher the samp rate is, the closer the sound is to the original
sample resolution
number of bits used per sample (bit rate/samp res = sample rate × bit depth)
sound file size formula
File size (bits) = samp rate x samp res x time
colour depth
the number of bits used for each pixel in an image file e.g colour depth of 3 can make 8 colours (2^3)
image file size formula
Size = (bits) = W x H x D
Size = (bytes) = (W x H x D)/8
W = image width
H = image height
D = colour depth in bits.
lossy compression
- some of the original data removed from file
-only used where data removed is unnecessary like pictures or videos
-after lossy the file cant go back to same quality
losless compression(RLE)
The process involves going through the text and counting the number of consecutive occurrences of each character (called "a run"). The number of occurrences of the character and the character itself are then stored in pairs. the more a character or colour is repeated the more it saves
huffman encoding (lossless)
Using a variable-length binary string to represent a character so that frequently used characters have short codes
use a tree of 0 for left and 1 for right, putting the most used characters higher so it takes less bits to get to them, so less bits to code them, so more data is saved than if ascii used
hardware
The physical components of a computer.
software
all programs that run on a computer
systems software + FIMPNAS
systems software=manages comp system resources and is a platform to run application software
OS manages:
File
Input/output
Memory
Processor
Network
Application
Security
application software
used to complete end user tasks eg powerpoint
embedded system
a computer that is part of a larger device, with usually only one purpose/function
ROM
read only memory, storage for start up instructions, non vol, can only be read no write
RAM
random access memory, storage for currently running programs, vol, can read and write
machine code (binary)
- A low level language that consists of 1s and 0s for when switches are on or off
- This is what all other "higher" levels of languages (even assembly) get translated into.
assembly code
A low level language that uses mnemonics to represent machine code instructions. have one to one relationship with machine code
high level languages
+easier to understand
+easier to spot mistakes
-slower to execute
compiler, pros and cons
translates code all in one go, and once translated can run again any time
+program runs quicker, translates all in one go
+runs quicker the second time (executable file)
-not portable, only specific to processor
-whole code has to be translated again if changes are made(not executable file)
-harder to spot errors
interpreter, pros and cons
translates line by line
+each line executed as soon as translated
+errors spotted easier, stops when error is reached
-run slower, have to wait for each line
-program has to be translated every time its run
parts of a cpu
cu- decodes data
alu-performs logic operations
registers- hold data in cpu while cu decodes
cache-stores very frequently used data to avoid bottle neck
von nuemann architecture
Computer architecture where instructions are:
-stored in memory with data
Broken into:
1) Memory
2) Input/Output Devices
3) Processor (ALU + Control Unit)
clock speed
number of fetch execute cycles performed per second (GHz)
fetch decode execute cycle
- Fetch: the next instruction is fetched from ram/memory
- Decode: the instruction is broken down to determine what data needs to be used to execute it
- Execute: action required is executed, output is stored in the registers
cache
+much faster than ram
+physically closer to cu
-much lower capacity than ram
-more expensive
factors affecting cpu speed
-clock speed: higher clock speed, more instructions per second. too high and will overheat
-cache size:more instructions can be accessed faster, level 1=fastest and smallest, level 3=largest and slowest
-number of cores: more cores= more instructions carried out simultaneously
secondary storage
data that isnt part of the cpu, needed to keep data after comp switches off
how does optical disc work, pros and cons
-disc spins quickly
-1s and 0s stored as pits and lands (variations of height of surface of disc)
-read/write head shines a laser onto the disk and records whether it hit a pit or land
-sent via on/off current to computer
-data written by laser burning into disk
pros and cons:
+easy to carry/portable
+cheap
-easily damaged, scratches affect data
-small capacity
SSD (solid state drive), pros and cons
SSDs use electrical circuits to persistently store data
+No moving parts, more robust
+silent
+very fast
-expensive
-small capacity
how does a magnetic disc work, pros and cons
has a magneitsed read/write head
-disc spins quickly
-split into data tracks, each has sectors
-sectors can either be magneitsed or demagnitised as 1s and 0s
-detected by head and sent as on/off switches of current to device
-write by magneitsing sectors
pros and cons:
+large capacity
+cheap
-not very portable
-can be noisy and generate heat
cloud storage, pros and cons
Internet service that provides storage to computer users through servers in a remote location
pros and cons:
+durable (old versions kept)
+can access data anywhere with internet
-service unreliable, could have data interruptions etc
-employees have access to data, dangerous
records and fields
record= a row of a database
field=a column of a database
primary key
field that is unique to that specific database, used to identify a record (as they will all be different)
foreign key
A field that is the primary key field in another table, and is used to link the two together
relational databases and why we use them
databases that can link together through foreign keys
+less data redundancy
+less inconsistencies (mistakes made)
how to select something in sql
SELECT Field
FROM table
WHERE condition
AND extracondition
ORDERBY (eg) asc
condition could be where name= computer science
select, from is necessary, the rest is optional
sending requests for multiple tables
WHERE Table1.foreignkey= Table2.foreignkey
How to add something in sql
INSERT INTO table (fields you want to add to)
VALUES(values you want to add)
how to delete something in sql
DELETE FROM table
WHERE field=value you want to delete
how to change something in sql
UPDATE table
SET field=value you want to change
WHERE condition
impacts of autonomous vehicles (from mark scheme)
• hard to trust computer to drive
• The car must make human-like decisions eg the 'trolley problem'.
• safer driving
• collect unauthorised data abt places visited
• Fewer roles needed for taxi drivers
• easier for disabled to drive
Legal impacts :
• Liability. There is a grey area about who is at fault (the manufacturer or the
driver) in case of an accident.
• Data protection laws still important
• Autonomous vehicles could be hacked, assasination?
environmental:
-more people can drive, more cars, more pollution
-more factories and energy used to manufacture cars
cloud storage- reasons for growth, pros and cons (from mark schem)
reasons for growth:
-Higher bandwidth mobile networks(4G)
-increased availability of mobile devices
- Reduction in cost of large capacity storage devices
- Improvements in network security
- People have a higher level of trust in cloud storage
pros:
+Enables user to access their data from more places/devices
+ Enables user to more easily share data with others
+ Increases the amount of storage available
+Reduced cost of physical storage
cons:
-Increased security risks
- Relies on internet
-Reliance on company providing the cloud service
-Increased chance of others accessing personal data
how to protect devices from malware (from the mark scheme)
-Regularly back up data and test backups
-Secure the backups o they are not lost
. -Block or remove email attachments or links., do not open attachments included in unexpected e-mails. -Disable pop-ups. Ensure the pop-up blocker is turned on
-Control software downloads. Only download software from sites you know
- Ensure software is up to date and patched to prevent any exploitation .
- Anti-virus is up to date so that the latest vulnerabilities are detected and dealt with.
- Only allow specified programs to run. Preventing any unknown programs running should prevent any malicious code .
-Manage the use of privileged accounts and access levels to files. Controlling the access to files should act as an internal firewallr to prevent illegal access of programs.
- Use network filtering or a firewall. Prevent\block access of viruses.
-Remove the ability to use removable media. Prevent unknown or unauthorised files to enter or leave the network.
-MAC address filtering. Can prevent access by unauthorised devices.
- User training. To educate staff in dangers of social engineering techniques and other unsafe practices
-penteration testing. to test programs and see if they are robust
wired vs wireless +security comparison (from mark scheme)
wired + :
• faster
• higher bandwidth
• fewer security risks
wired - :
• Cables can be hazardous
• expensive set up
wireless + :
• lower setup costs
• No wires/cables are required
• easy to connect new devices
• Users not confined to a single location
• Can connect multiple devices w/o extra hardware
wireless - :
• slower
•interference from walls and low range
• less secure
• Connections are not as stable as wired networks
Describe 3 differences between low level and high level languages
High-level languages are closer to human language and easier to understand (e.g., Python, Java). Low-level languages are closer to machine code and harder for humans to read (e.g., assembly language).
High level languages can run on any hardware while low level languages require specific hardware to run on
Explain the role of clock
Sends out regular electronic pulses that synchronises with operations of the cpu
Each cycle processes an instruction
The faster the clock speed, the more instructions are processed
Explain how compilers and interpreters operate
Compilers translate the whole program in one go
They produce an execuatable file
They show all the errors at the end
Interpreters translate the code line by line.
They do not produce an executable file
Errors are immediately shown