200-201 dumps exam questions
QUESTION 1
Which security technology allows only a set of pre-approved applications to run on a system?
A. application-level blacklisting
B. host-based IPS
C. application-level whitelisting
D. antivirus
Correct Answer: C
QUESTION 2
DRAG DROP
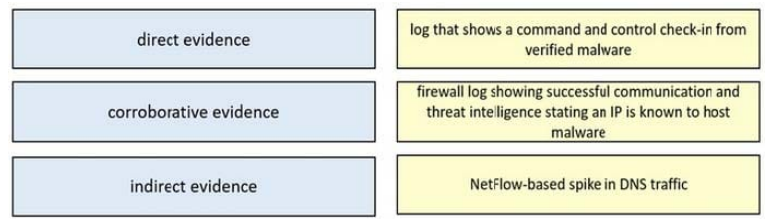
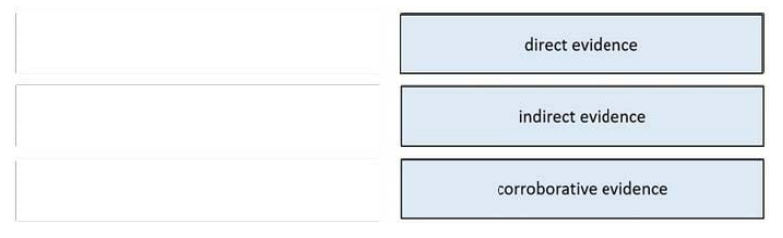
Drag and drop the type of evidence from the left onto the description of that evidence on the right.
Select and Place:
Correct Answer
QUESTION 3
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
A. swap files
B. temporary files
C. login sessions
D. dump files
E. free space
Correct Answer: CE
QUESTION 4
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A. file extension associations
B. hardware, software, and security settings for the system
C. currently logged in users, including folders and control panel settings
D. all users on the system, including visual settings
Correct Answer: B
https://docs.microsoft.com/en-us/troubleshoot/windows-server/performance/windows- registry-advanced-users
QUESTION 5
How does certificate authority impact a security system?
A. It authenticates client identity when requesting SSL certificate
B. It validates domain identity of a SSL certificate
C. It authenticates domain identity when requesting SSL certificate
D. It validates client identity when communicating with the server
Correct Answer: B
QUESTION 6
Refer to the exhibit.
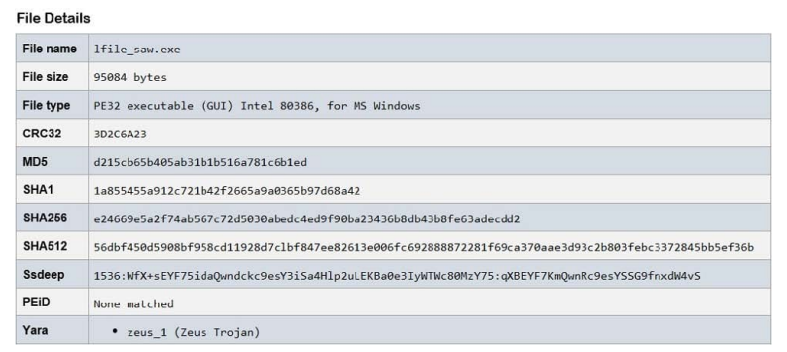
A SOC engineer is analyzing the provided Cuckoo Sandbox report for a file that has been downloaded from an URL,
received via email. What is the state of this file?
A. The file was identified as PE32 executable for MS Windows and the Yara filed lists it as Trojan.
B. The file was detected as executable and was matched by PEiD threat signatures for further analysis.
C. The file was detected as executable, but no suspicious features are identified.
D. The calculated SHA256 hash of the file was matched and identified as malicious.
Correct Answer: A
QUESTION 7
Which two measures are used by the defense-in-depth strategy? (Choose two.)
A. Bridge the single connection into multiple.
B. Divide the network into parts.
C. Split packets into pieces.
D. Implement the patch management process.
E. Reduce the load on network devices.
Correct Answer: BD
QUESTION 8
What is sliding window anomaly detection?
A. Detect changes in operations and management processes.
B. Define response times for requests for owned applications.
C. Apply lowest privilege/permission level to software.
D. Identify uncommon patterns that do not fit usual behavior.
Correct Answer: D
QUESTION 9
A network engineer discovers that a foreign government hacked one of the defense contractors in their home country
and stole intellectual property. What is the threat agent in this situation?
A. the intellectual property that was stolen
B. the defense contractor who stored the intellectual property
C. the method used to conduct the attack
D. the foreign government that conducted the attack
Correct Answer: D
QUESTION 10
Refer to the exhibit.
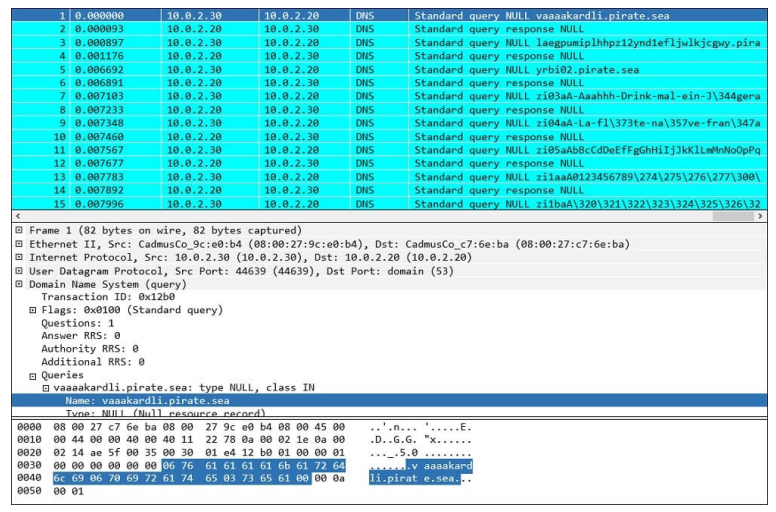
What is occurring?
A. ARP flood
B. DNS amplification
C. ARP poisoning
D. DNS tunneling
Correct Answer: B
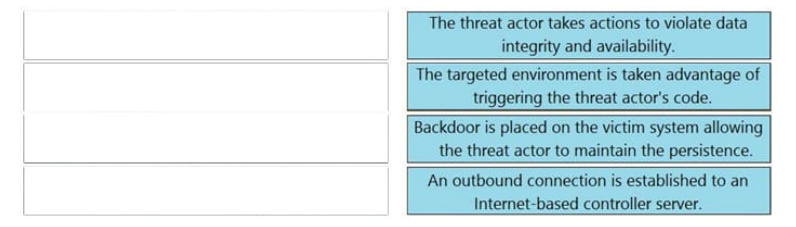
QUESTION 11
DRAG DROP
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber
Kill Chain model.
Select and Place:
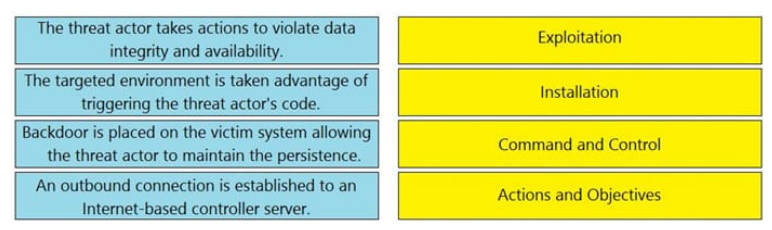
Correct Answer
QUESTION 12
How is attacking a vulnerability categorized?
A. action on objectives
B. delivery
C. exploitation
D. installation
Correct Answer: C
Leads4pass provides more latest Cisco 200-201 practice materials
Finally, I wish everyone good luck!
 Knowt
Knowt
