IB Digital Society - Paper 1 - Section 3: Content (3.4: Networks and The Internet)
3.4: Networks and The Internet
Key ideas
Networks connect computers, people and communities, allowing data to be created, accessed and shared in a distributed manner.
Networks and the internet are defining features of digital society.
Networks and the internet pose significant opportunities and dilemmas for life within a digital society.
Network: a series of interconnected nodes (connection points) that transmit, receive and exchange data, which can range from text, sound to video.
Examples of nodes include computers, servers and routers.
3.4A Types of computing networks
Networks are categorized depending their physical size, type of connectivity or how data is shared. Different networks are suitable for different purposes and situations.
Networks by size
Personal area network (PAN): the smallest type of network, consisting of connected devices in close proximity to an individual.
Examples: wirelessly connecting to a phone, a laptop connected to a printer, a smartwatch wirelessly synching data to a phone.
Local area network (LAN): a group of computers or devices connected on a single site, which is set up to help the sharing of resources.
This can be done on a small scale (a home with more than two users) or a larger scale (office or school, with hundreds of users)
Examples: sharing resources to centralized data in an office, giving access to printer at home
Metropolitan area network (MAN): network that covers a larger geographical area, ranging from 5 to 50 km.
Examples: cities that provide free WiFi, municipalities that connect traffic lights
MAN could be used in road infrastructure transited by autonomous vehicles.
Real-World Example: New York’s Free Wi-Fi
New York City provides free Wi-Fi to all their residents, as well as wirelessly connecting traffic lights and parking meters.
Wide area network (WAN): the largest type of network, which is commonly used by businesses through a collection of LANs.
The collection of LANs can either be available to the public or may be limited to be used by an organization.
For organizations and businesses, WANs present an advantage - it eliminates the need to have servers in each of their offices. Additionally, they can lease an exclusive line from their internet service provider (ISP), to avoid sharing their network.
Example: the largest publicly available WAN is the internet - a collection of networks and networking technologies which connects users.
Type of connectivity
Wired networks: devices connected with copper ethernet cables which plug into an ethernet port (which were either integrated onto the motherboard or installed as a separate interface card). It also uses a router or a switch
Fiber-optic cables are now being used, given they provide better connectivity over greater distances.
Some businesses and governments still used wired networks - these are considered to be more reliable to transfer data and work at a faster speed.
Wireless networks: devices embedded with wireless network interface cards connect either through a wireless access point or router.
Wireless connections use radio signals to send data across the network, although it still uses cables to connect access points to a wired backbone.
The major difference is that devices (laptops, printers) can connect wirelessly.
Wireless networks are widely used - they are easy to set up (no need to connect devices through cables) and offer flexibility, since devices can connect from within a geographical range.
Cloud networks: incorporate some or all network capabilities to a cloud platform,
Cloud-based networks still use access points on site, but cloud platforms have the ability to be managed or host data off-site.
This type of network can be configured by accessing the IP (internet protocol) address of the hardware controlling the network.
Cloud networks are used by organizations - they are easy to station, save costs and allow for scalability.
Sharing data
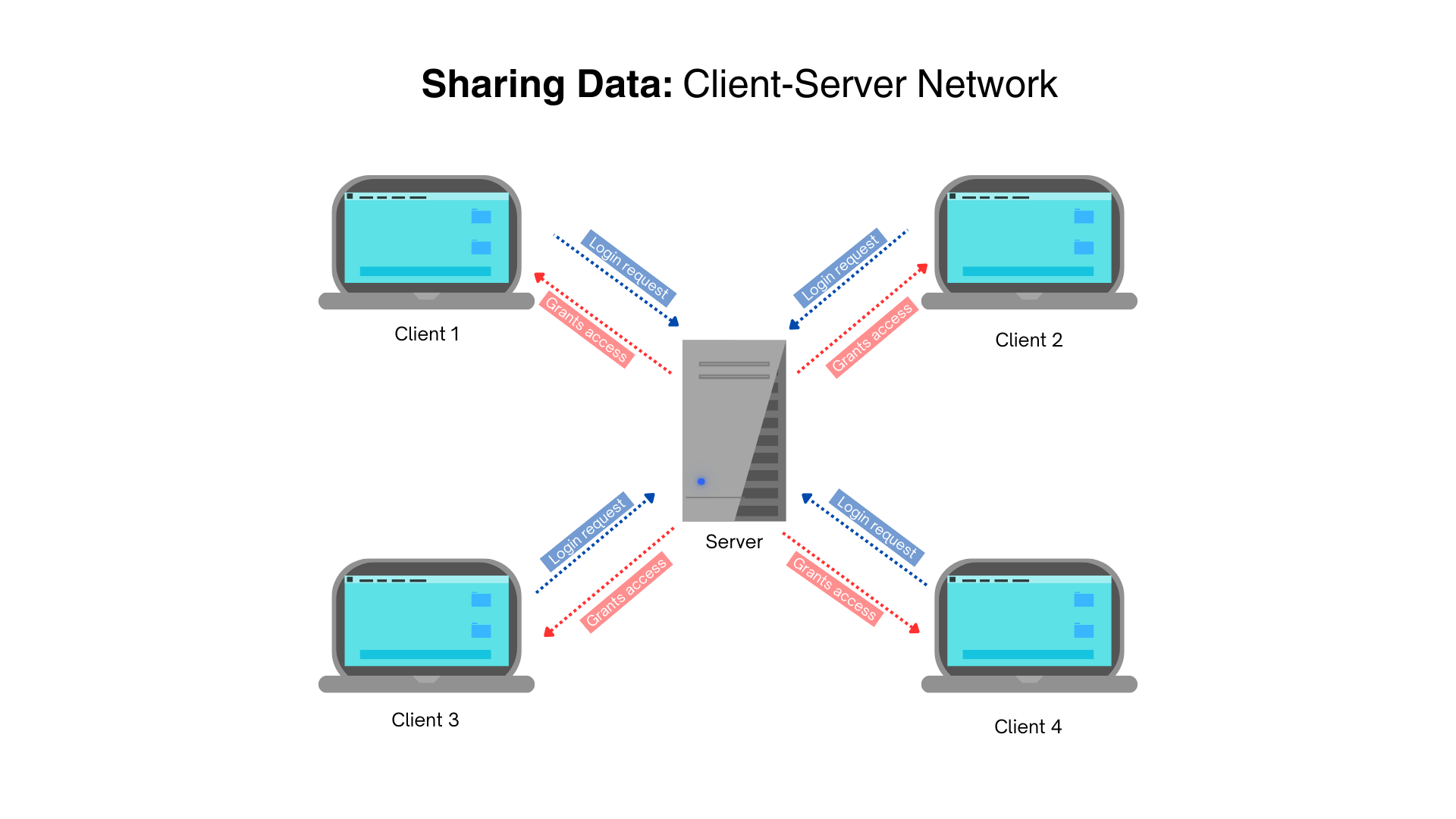
Client-server networks: data is stored centrally on a server and access is granted to connected devices (also referred as ‘clients’)
Servers can either be hosted internally (e.g. by an organization) or externally in the cloud.
Many organizations see an advantage in this network - it allows them to prioritize IT resources that will secure and backup data.
Nonetheless, there are some disadvantages - setting up and configuration are expensive which requires expert staff. Additionally, adequate bandwidth is needed to ensure equal access is given to all clients.
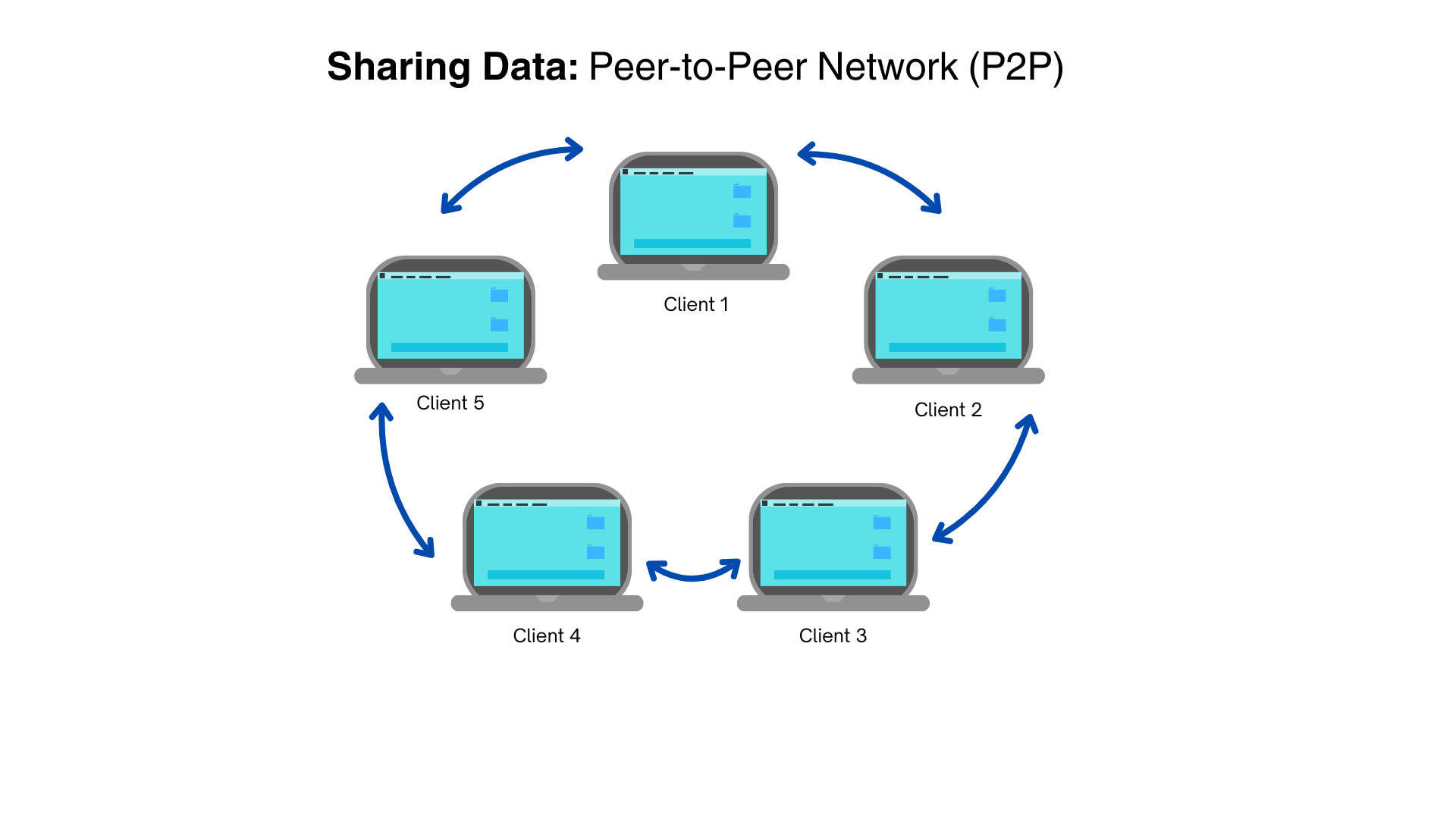
Peer-to-peer network (P2P): a decentralized network - each device is equally responsible for sharing and storing data.
A major advantage is that the network is not dependent on one server. Likewise, it is easy to set up.
P2P is therefore popular for sharing large files over the internet, although at the expense of not being able to manage or control the security of the data.
Example: online gaming platforms - Blizzard Entertainment and Wargaming
A downside to P2Ps is the ease of sharing illegal copyright material. Since it does not depend on a server, it is difficult for authorities to track them and shut them down.
3.4B: Components of computing networks
Network interface card: a device (typically a circuit board or chip) which is either installed (wired) or not (wireless) on a computer (or node).
The card is responsible for converting data into a digital signal and communicating this data to a network.
MAC address: Media Access Control Address - a unique number assigned to every network device.
Usually, MAC addresses are stored within a device’s ROM (Read-Only Memory), thus the are sometimes called a ‘hardware address’
MAC addresses are unique (unlike IP addresses) and are not designed to be changed although it is easy for a skilled user to alter or spoof theirs.
Router: a networking device which connects two or more separate networks.
This is done by transferring data from one network from another - routers forward data packets through the most efficient route available.
The router acts as a gateway, where all data entering and leaving the network passes, therefore, it enables a router to perform additional tasks such as filtering information.
Example: a router at a school will connect the school network to an external one, such as the internet.
Modem: a device which converts digital data into analogue data. It usually converts data to an ethernet connection, which allows ISP to provide WiFi to a user’s home.
Wireless access point (WAP): a device that creates a wireless local area network to improve coverage throughout a building.
A WAP works by setting up a number of dedicated radio channels that the computers can connect to.
Each WAP will be connected to either a hub or a switch.
Hub: the most basic and cheapest network device - when it receives data, it re-broadcasts the data to all connected devices.
There is a downside to this device - it uses a lot of bandwidth because it sends unnecessary data all over the network, including to non-intended devices.
Example: game consoles for a local multiplayer game.
Switches: a more upgraded version of hubs - they inspect data they receive before sending it to the intended recipient.
Switches saves bandwidth and also gives more control over how data is shared.
*Hubs, routers and switches perform similar basic tasks but they differ in the way they broadcast data.
3.4C: Characteristics of computing networks
Network standards and protocols
Network protocol: a set of rules which outlines how data is sent, formatted and received.
The protocols include different layers which govern different parts of a communication. These four layers are:
Application layer: set of protocols used by applications. Example: web browser
Transport layer: oversee communication between hosts using the following protocols:
Transmission Control Protocol (TCP): ensures data is sent and received correctly. TCP needs to make a request if data is lost in order to re-send it.
Internet Protocol (IP): deals with the addressing of individual devices and routing data.
Collectively, the Transmission Control Protocol/Internet Protocol (TCP/IP) is a set of rules which governs how data is sent within a network and also demands that an IP address is used to identify machines on said network.
Internet layer: concerned with the sender and the recipients’ IP address. Additionally, it routes the data packets across a network.
IP (Internet Protocol) address: a numeric address assigned to every node (device) which identifies them within a network.
IP address is assigned by the Dynamic Host Configuration Protocol Server (DHCP), to avoid address conflict (having more than one device with the same IP address number) and to keep track of each assigned number.
Physical network layer: protocols which allow different networking technologies to work together.
Example: networking technologies - ethernet
When a user types a website address into a web browser, it consists of a domain name. The domain name is send as a request a;
Domain name server (DNS): a server which translates the domain name into IP addresses.
The server searches for an IP address in its database and will forward data to that address.
Example: Twitter’s IP address is 104.244.42.1.
Network capacity
This takes in consideration how much data can be transferred in any given time.
Bandwidth: the amount of data a network can transfer at once. It is measured in hertz (Hz).
Speed: the length of time it takes for data to be transferred. It is measured in megabits per second (Mbps).
Data Compression: process which reduces size of a file by re-coding it with fewer bits of storage.
This process is commonly done to reduce the amount of space needed to store a file.
There are two types of compression algorithms;
Lossy Compression: reduces file size by permanently removing unimportant data.
Example: JPG and MP4
Lossless Compression: reduces file size but without losing data and the possibility of turning the file to its original data.
Example: PNG and BMP
Net neutrality: the notion that all data requests on the internet are equally important and thus should be treated as such by internet service providers (ISPs) companies.
Net neutrality is encouraged to avoid some websites running faster than others and to avoid ISPs from proposing to charge extra to view specific content.
Security
Data on a network is always vulnerable to threats.
Networking and security professionals need to ensure all measures are taken to protect data. Users have the obligation to be educated and responsible on how they protect their data.
Controlling access from within
A network can be configured to control how users access physical resources and data.
The simplest form was through authentication - a user uses a unique username and strong password.
Authentication has been replaced by the more reliable multi-factor authentication;
Multi-factor authentication: a user is subject to multiple methods of authentication to verify its identity.
Two or more credentials are used, which can include a mix of physical or biometric measures:
Examples: physical - token, card or text message, biometric - faceprint, PIN, or phrase.
Controlling access from outside threats
Firewall: a hardware or software which determines which data is allowed to enter the network.
Hardware firewalls may be used by large organizations, while a software firewall is part of an operating system and can be turned on.
A firewall works by inspecting incoming and outgoing data, thereby preventing unauthorized access to a network and controlling which users and programs are allowed to connect to the network.
Proxy Server: a computing system which acts as an intermediary between the client on the network and the internet.
Because all communication passes through a proxy, it is able to perform additional tasks such as caching, filtering and logging data, adding a layer of security.
3.4D: Computing network providers and services
To gain access to the internet a user must be registered to a mobile service provider (MSP) or an internet service provider (ISP).
Mobile service provider (MSP): commonly known as mobile carrier or mobile phone operator — a company that offers cellular connection to mobile phone subscribers.
MSPs purchase a license to transmit radio signals over a specific range and within a particular frequency.
Radio signals between 1800 to 2100 MHz are 4G and 5G networks.
MSP subscribers use this service to make phone calls, send, receive messages and use data to navigate the internet. It is now possible to make calls using the internet with VoIP
VoIP (Voice Over Internet Protocol): allows users to make calls using a broadband internet connection instead of an analogue phone line.
In a VoIP, audio data is transformed into digital packets which are sent via the internet to other devices.
Examples: VoIP services - Skype, WhatsApp, Facebook Messenger.
Internet Service Provider (ISP): a company which provides access to the internet and other related services, which include email, domain registration and web hosting.
3.4E: The World Wide Web
Internet: global collection of networks and networking technologies that link users.
World Wide Web (WWW): collection of websites and web services which can be viewed and that are hosted on web servers.
Three technologies have allowed the interoperability between all technologies on the internet;
URL (Unique Resource Locator): a unique address for each resource on the web, which can include the address of a web page or a file hosted by a web server.
HTTP (Hypertext Transfer Protocol) or HTTPS (Secure Hypertext Transfer Protocol): determines how web resources are transmitted between the web browser and the web server.
HTTPS is more secure and now a requirement for many web browsers.
Web-hosting companies add a security certificate to their web servers, guaranteeing sensitive data is encrypted.
HTML (Hyper Text Markup Language): format of web pages - allows documents to be displayed as web pages and web pages to be linked together.
3.4F: Evolution of the internet and the web
The early days of the internet (1969–2000)
1965: First computer network established - a computer from the University of California, Los Angeles, sent a message to a computer at Stanford University, causing a system crash.
1969: Creation of the ARPANET (Advanced Research Projects Agency), the second (and only successful) attempt to create the internet.
The ARPANET included 30 academic, military and research institutions across the world (Hawaii, Norway and the UK).
The TCP/IP Protocol was introduced and operational until 1990.
1989: The WWW (World Wide Web) created by Sir Tim Berners-Lee - by this time, the nodes connected to the internet grew from 2000 to 30,000.
Berners-Lee proposed that the information being shared should be structured and linked in a way that made it quicker and easier to access.
The web browser was introduced, making the WWW more accessible.
1994: World Wide Web Consortium (W3C) formed - the organization aims to promote the evolution and interoperability of the WWW through the development of protocols and guidelines.
The W3C consults a wide range of members who work for organizations before implementing any protocols or guidelines.
1996: The number of websites grew to 100,000. In 1993, there were only 130 websites.
The expansion of the web (2000–20)
Web 1.0: A version of the web which was characterized by static web pages. During this time, a change of content within web pages required programming, a skill few people knew.
Web 2.0 (2000): Also known as ‘social web’, a version of the web which saw a democratization of the internet.
Users could generate their own content, without programmers through the use of XML and RSS to structure and format websites.
Additionally, users could upload their own content to web pages.
These changes were also possible due to the development of new technologies and protocols.
Social media platforms, blogging, podcasting, social bookmarking and tagging were introduced during this period, many which are still popular today.
Web 3.0: the semantic web (2020–present)
An era which aimed to innovate the user experience - focused shifted to back end (data and logistics of how an app works), with the promise of being more intelligent.
One feature is the focus on generating a greater understanding of the meaning of the words used when creating, sharing and searching content.
This generation heavily uses artificial and natural language processing - websites can display 3D graphics and demand for internet of things (IoT) is growing.
The internet of things (IoT)
IoT: Refers to all devices which are connected to the internet - this does not only include phones or laptops but also smart appliances and autonomous vehicles.
Other items such a smart light bulb or a jet engine are also included - devices could be either small or large.
IoT devices work by using sensors which collect data and communicate with each other over the network, with the purposes of providing assistance or increasing efficiency.
Example: smart home technologies - smart door locks allow delivery drivers to drop off packages.
Some criticism and concerns over IoT revolve around the issues of privacy and security.
3.4G: Internet dilemmas
Understanding the risks to data
Specific risk which threat to lose, damage and misuse data include;
Spamming: sending unsolicited emails with the purpose of advertising.
With development in email filters, a user can eliminate unwanted messages before reaching their inbox.
Hacking: defined as the unauthorized access to a computer or network, which can be accomplished through tools such as:
Social engineering: tricking a user into sharing credentials (username and password). It is an umbrella term to refer to all techniques aiming to obtain user’s data.
Example: hackers impersonating an IT staff, offering to conduct routine maintenance.
Phishing: a type of social engineering - hackers send fraudulent emails designed to trick users into revealing sensitive information.
Real-World Example: Phishing at Google and Facebook (2013 - 2015)
Evaldas Rimasauskas, a Lithuanian national, established a fake computer manufacturer company which pretended to work with Google and Facebook.
Rimasauskas sent phishing emails with invoices to employees, deceiving both companies into paying US$ 100 million.
Viruses: a type of malicious software (or malware) composed of small pieces of code.
Viruses are often attached to legitimate programs or emails and are activated when the user launches or opens either.
Real-World Example: Bangladesh Bank Hack (2016)
Lazarus group, a North Korea group of hackers, launched an attack with the aim of stealing US$1 billion.
The group used a range of social engineering methods, including viruses - these were attached to the CV of a hacker who presented himself as an intern.
The hackers needed to reach and shut down the printer, which had a paper backup system of all bank transactions, risking exposing the hackers’ scheme.
Ransomware: a malware which locks a user out of their device, demanding a payment to release them.
Ransomware can be activated when clicking an email attachment, visiting a malicious website or link and can be hidden when downloading a software.
Real-World Example: WannaCry Ransomware (2017)
A global attack which affected 230,000 computers. Users needed to pay a ransom in Bitcoins.
The hackers used ransomware to take advantage of a vulnerability in the Windows operating system.
Although Windows released a security patch, many institutions had not updated their computers, resulting in US$4 billion losses worldwide.
Distributed denial of service (DDOS): an attack which overwhelms (disrupts the normal traffic) a site or service, making it unavailable to intended users.
Hackers who carry out this attack install malware in a network of computers (botnet) which are instructed to make a connection to the target web server. The web server can’t cope with the increased demand, preventing users from accessing the website.
Example: DDOS attack on Amazon (February 2020) - resulted in loss of revenue and reputation.
Example: The Meris Botnet (2021): The Meris, which was the largest botnet available to hackers (with 250,000 infected devices) was taken down after an attack by the security division of Rostelecom, the largest provider of digital services in Russia.
Hacking a website/Penetrating a network: methods which can include gaining back-end database of user information or redirecting users to a different website.
Exploiting a security flaw: a network is vulnerable if it doesn’t have adequate malware, virus protection or firewall.
Real-World Example: Log4J attack (2021):
A security flaw in the Java code ‘Log4shell’ made many corporate networks vulnerable to hackers.
The flaw gained prominence after it was revealed that it affected some sites hosting Minecraft.
Consequences of the risks to data
This includes measures to counter exposure; such as (although it includes ill-intentioned)
Anonymity: the use of digital technology to conceal a person’s true identity.
This is the most extreme form of privacy and can be potentially liberating for users which can confidently express themselves.
However, some users can take advantage of anonymity with malicious intent, such as cyberbullies and internet trolls.
Internet trolls: people who deliberately leave provocative or offensive messages with the intention to draw attention, cause trouble or upset someone.
Real-World Example: Online harassment survey (Australia)
A survey showed 1 in every 3 Australians have experienced online harassment, resulting in US$ 2.6 billion in health costs and lost income for the government.
Identity theft: when a person steals another’s personal information with the intention of committing fraud.
The information can be used to apply for a credit card, gaining access to medical services and/or other financial benefits.
Many users go into anonymity as a way to counter identity theft, especially because many sites and services now require users to sign up.
Some governments are enforcing the right to be forgotten (RTBF), to help users keep their data safe.
Right To Be Forgotten (RTBF): right to have personal information removed from internet searches and other directories under certain circumstances
Example: GDPR: the organizing which governs data protection in Europe states personal information should be removed when:
The user’s consent has been withdrawn
The personal data is no longer needed