AP Computer Science Principles Unit 2 Notes
Resources:
Lesson 1: Welcome to the Internet
Internet Simulator (in this lesson)
Similar to the Internet
Send Info to others
Has a Network
Only allows us to contact one person
Different to the Internet
Can only send text
Takes a little time to send
What is the Internet? (Video Notes)
Vint Cerf + Bob Kahn created the Internet
result of another experiment called the Arpanent
Paul Baren was trying to figure out how to build a communications system that might actually survive a nuclear attack
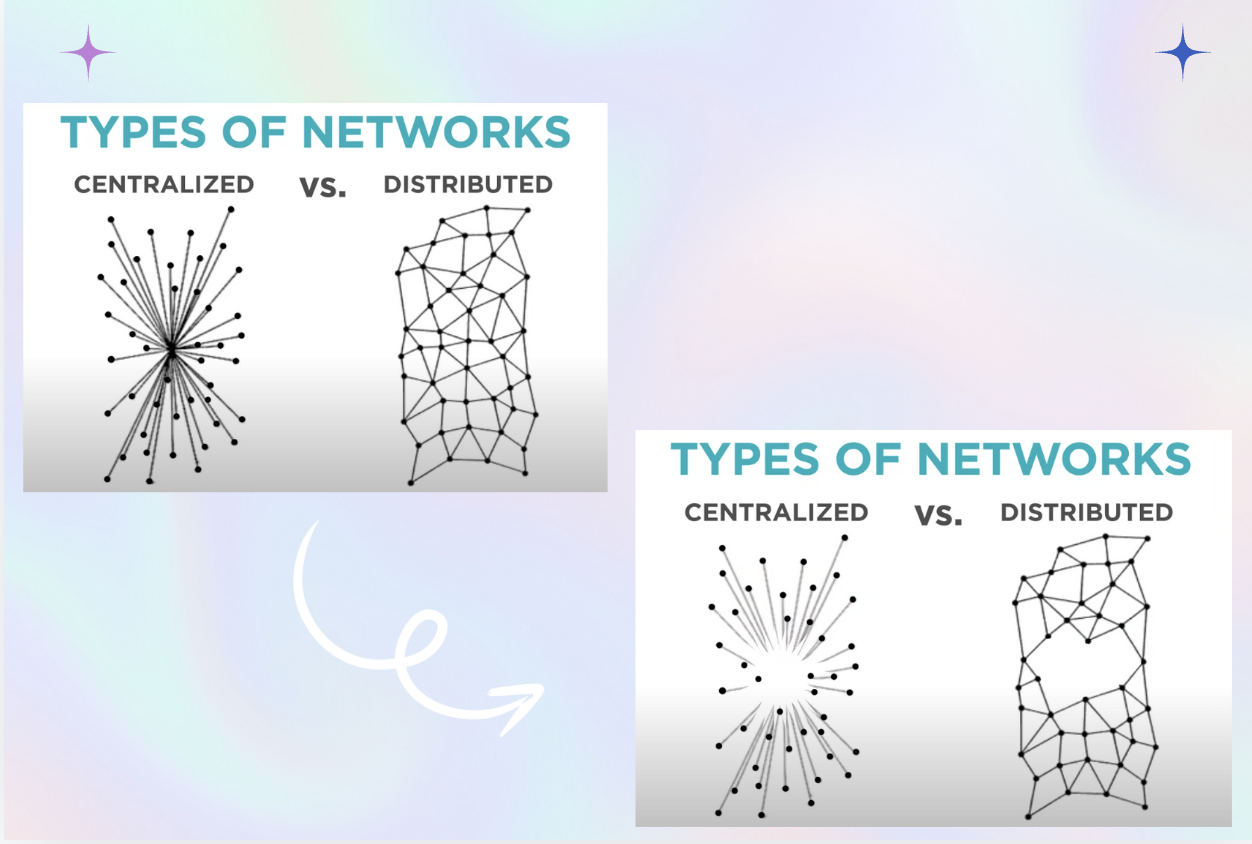
Baren thought of breaking the messages into blocks and sending the message as quickly as he could through the mess network (Distributed model)
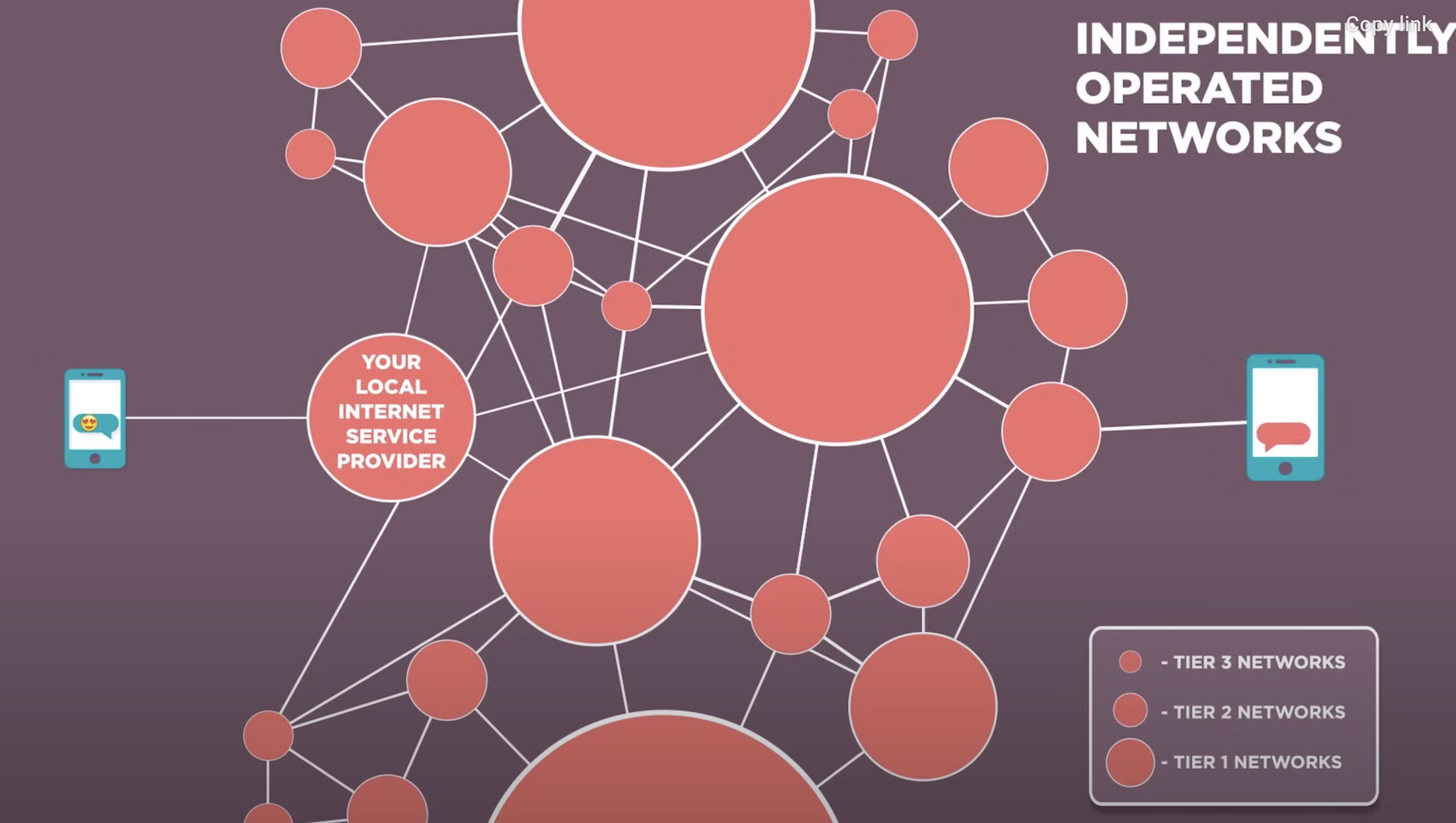
The Internet is made up of many independently operated networks
no one owns the internet
no central control
fully distributed
any device can communicate w any device
Major Issues In Society (because of the internet) ==> add tech behind it
Net Neutrality:
principle advocating for all internet traffic to be treated equally => free access to all internet information
no discrimination or different charges based on the user, content, site, or platform
keeping the digital playing field level for everyone
from startups to tech giants
prohibits internet service providers from blocking, throttling, or engaging in paid prioritization of lawful content
Internet Censorship:
blocking certain websites because they do not align w a value (could be political)
Digital Divide:
the gap between those who have access to technology, the internet and digital literacy training and those who do not
Lesson 2: Building a Network
The process of data finding a path from sender to receiver is considered routing.
When data is routed across a network, how fast the msg arrives is determined by bandwidth.
Bandwidth: is the maximum amount of data that can be sent in a fixed amount of time, usually measured in bits per second
message arrives quickly: maybe because of high bandwidth (many bits can be sent per second)
message arrives slowly: could be due to low bandwidth
Computing Device: a machine that can run a program, including computers, tablets, servers, routers, and smart sensors (usually singular)

Computing System: a group of computing devices and programs working together for a common purpose

Computing Network: a group of interconnected computing devices capable of sending or receiving data.

Lesson 3: Need For Addressing
IP Address + DNS Video Notes
Connection Chain
you → your device →your internet service provider → billions of devices
Protocol: a well-known set of rules + standards used to communicate between machines
The Internet has a design philosophy
able to absorb + adapt to new internet communication tech
IP Address (internet protocol)
All the different devices on the internet have a unique address
address on internet = a number
Structure:
That version of IP Address is called: IPv4
makes over 4 billion unique addresses
4 Billion is not enough, into the transition to IPv6
allows for longer IP addresses
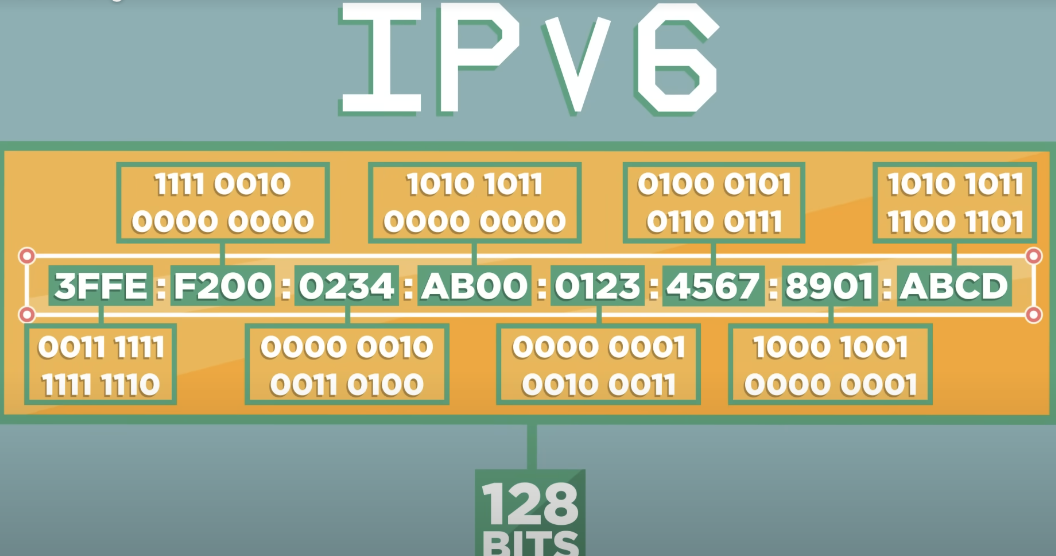
creates over 340 undecillion unique address
DNS (Domain Name System)
turns domain names into IP addresses, which browsers use to load internet pages.
DNS servers are connected in a Distributed Hierachy,
DNA is meant to be open and public communication protocol
soooo…lots of cyberattacks
DNS Spoofing
hacker changes IP address and sends person to hacker website :(((((
people use fake websites as real => more problems yay
Vocabulary Protocol: An agreed-upon set of rules that specify the behavior of some system IP Address: The unique number assigned to each device on the Internet. Internet Protocol (IP): a protocol for sending data across the Internet that assigns unique numbers (IP addresses) to each connected device |
Lesson 4: Routers and Redundancy
IP = open protocol that all devices use.
ensures that all devices can connect to one another simply by knowing their IP address
The IP addresses of the sender and receiver are converted to binary so that devices know which messages are for them and which device should get a response.
Messages are sent from router to router → bouncing between different routers in the network.
Not all messages take the same path to get to their destination.
When sending multiple messages to the same person→ messages may take different path
Vocabulary:
|
Lesson 5: Packets
Intro:
information traveling over the Internet is divided into many packets
these packets travel separately through the network
as well as the protocols that allow this process to work even when some packets are lost or delayed
Packets Chart (examples)
User Datagram Protocol (UDP) “useless” | Transmission Control Protocol (TCP) |
goal: send info as quick as possible, don’t worry about accuracy | goal: numbering every packet: It’s slower but more accurate |
How it works: send all the packets w/o checking if they all get through or arrive in the right order. | How it works: Number packets so they can be re-ordered, confirm all were received, resend any missing packets. Multiple back and forth confirmations between sender and receiver. |
Use: when time matters more than errors:
| Use: accuracy matters more than saving time
|
Vocabulary: Datastream: Information passed through the internet in packets. Packet: A chunk of data sent over a network. Larger messages are divided into packets that may arrive at the destination in order, out-of-order, or not at all. Packet Metadata: Data is added to packets to help route them through the network and reassemble the original message.
Transmission Control Protocol (TCP): A protocol for sending packets that does error-checking to ensure all packets are received and properly ordered User Datagram Protocol (UDP): A protocol for sending packets quickly with minimal error-checking and no resending of dropped packets |
The Internet: Packets, Routing & Reliability Video Notes
Internet is NOT made of direct dedicated connections
Information goes from one computer to another in a Packet
could take different routes to get to different places
Many types of Infomation can be sent through IP packets
One image can be broken up into different packets because the entire image might be to big to send in one packet!
Routers act like traffic monitors to keep the packets moving smoothly
Having options for paths makes the network fault-tolerant → keeps the key principle of the internet Reliability
TCP helps with checking and allowing for reliability to occur
TCP + Router Systems are scalable
More Routers = More Reliablable
Lesson 6: HTTP and DNS
IP Addresses can change
The Domain Name System (DNS) plays a critical role in translating human-readable domain names, like example.com, into IP addresses (e.g., 192.0.2.1), which computers use to identify each other on the Internet.
How does the DNS solve the problem of translating domain names like example.com into IP addresses?
it as able to correspond different names with IP address
How does the DNS help the Internet scale?
DNS Servers are connected in a Distributed Hierachy
Able to split up responsibilities for major domains like (.org, .com, .net)
DNS = created to be open and public protocol
DNS and IP are designed to SCALE, always NO MATTER how much the internet grows
Overall Notes:
DNS is a network of servers that track the IP addresses of different domain names like example.com
When you try to visit a website you first ask the DNS for the IP address of the domain you want to visit.
first server may have to ask other servers for this information
DNS allows billions of devices to get added to the network w/o putting pressure on one computer/server to know all the IP addresses in the world
DNS lets you talk to people even if you do not know there IP address
HTTP and HTML Video Notes
HTTP = Language use to communicate between Web Browers and Servers
Mainly made up of Get Requests

allows the HTML code to get across to the computer


SSL/TLS = adds layer of security from people tampering or snopping
What problem is HTTP solving?
When visiting a website, you’re getting sent a file by a server.
HTTP solves the problem of how to ask for that file.
Your computer and that server communicate using HTTP.
What is a GET request and what are you requesting?
Requests those files or to send data
How does HTTP rely on the other layers of the Internet?
Communications are sent over the Internet so the requests are sent inside TCP/IP packets, over the physical wires of the Internet.
Why are SSL/TLS, and HTTPS necessary?
To secure information online, using HTTP, information would be plain text.??
What do certificate authorities do and why are they necessary?
Ensure when you start a secure connection you're talking to the website you think you're talking to.
When you type a website url in, what happens? |
Information
|
VOCABULARY Scalability: the capacity for the system to change in size and scale to meet new demands The Domain Name System (DNS): system responsible for translating domain names like example.com into IP addresses World Wide Web: a system of linked pages, programs, and files HyperText Transfer Protocol (HTTP): a protocol for computers to request and share pages that make up the WWW on the Internet
|
Ap Classroom Break Down Notes
fault-tolerant = redundancy **not that the components are foolproof
People do not have access to the internet
meaning putting applications for jobs online does not help
IPv6 allows more more IP address than IPv4 ==> more devices connected to the internet
Redundancy often allows messages to be sent even if some network devices or connections have failed!
fault-tolerant: The ability to provide data transmission even when some connections have failed
internet allows for more perspectives and ability to quickly update content as new info becomes available
an advantage that online newspapers have over social media sites: ability to provide credibility to the information distributed
printed material is more credible
Both online newspapers and social media sites provide media-rich content at a low cost to the user.
packets assembled in internet: Each packet contains data to be transmitted, along with metadata containing information used for routing the data.
NOT TRUE: packet contains an encrypted version of the data to be transmitted, along with metadata containing the key needed to decrypt the data.
Lower Bandwidth: will be restricted in the maximum amount of data that they can send and receive per second.
WILL NOT
be prevented from having fault-tolerant routing on the Internet.
Data is broken into packets and then reassembled upon arrival.
Using open protocols ensures that all devices are using the same communication rules but does not necessarily provide fault tolerance.
Monitoring network traffic can help administrators be aware of component failures but does not necessarily provide fault tolerance.
Providing high-bandwidth connections can improve transmission speeds but does not provide fault tolerance.
The message is broken into packets. The packets can be received in any order and still be reassembled by the recipient’s device.
NO central monitoring computer is used to track and maintain the connections of the Internet.
Protocols for packets and routing are used so that computers from different manufacturers can communicate in a standard way.
Packets are pieces of data that travel the Internet. They do not represent the devices themselves.
Digital certificates are used to verify encrypted keys. They are not assigned to every device connected to the Internet.
Redundant routing on the Internet is not dependent on the bandwidth of a connection.
Devices running different operating systems can communicate over the Internet.
Open standards and protocols cannot be used to allow copyrighted materials to be shared freely.
As a new device is connected to the Internet, it is assigned an IP address to enable communication on the network.

3 connections that must be broken or removed in the network before computer E can no longer communicate with computer F
Computers B and C can communicate with each other without additional computers being aware of the communication.
Making a computer system fault-tolerant often increases pathways between devices and components, which can increase the possibility of a successful hacking attempt.
Making a computer system fault-tolerant often requires additional resources, which can increase expenses.
Making a computer system fault-tolerant increases reliability but may not necessarily increase efficiency.
Protocols are unable to ensure that all Internet connections have the same bandwidth.
Open protocols provide a way to standardize data transmission between different devices.
Protocols for Internet communication, such as TCP/IP, are intended to define a standard format for messages sent between devices on the Internet.
Removing Digital Divide: Providing accessibility features may allow some groups to access technology and content that they previously could not access.
Actions to reduce digital divide:
I. Providing free education and training on how to use computing devices
II. Providing free or low-cost computing devices to low-income individuals
III. Providing networks and infrastructure to people in remote area

Redundant routing is impossible if there is only one possible path from one device to another. There is only one possible path from P to S (P to R to Q to S).
The World Wide Web is a system of linked pages, programs, and files that is accessed via a network called the Internet.
The Internet is designed to scale to support an increasing number of users. ==> DNS help
The computers can communicate directly because Internet communication uses standard protocols.
 Knowt
Knowt
