Computer Networks
Computer Network Definition: A computer network is a collection of computers and other hardware devices connected together so users can share hardware, software, and data, and electronically communicate.
Internet: The Internet is a global network of computer networks utilizing a suite of protocols called TCP/IP (Transmission Control Protocol/Internet Protocol) that supports interconnection of a number of different computer networks
Various Definitions:
Protocols – standardized rules that define how computers communicate and exchange data. Protocols define the format and order of messages sent and received among network entities, and the actions taken upon message transmission and receipt.
Standard: A set of criteria or requirements approved by a recognized standards organization
Networking standards: Address how networked computers connect and communicate. Needed to ensure products can work with other product
IP address – unique number used to identify computers on the Internet
Domain name – structured naming system to locate computers on the Internet
URL – uniform naming scheme that specifies unique addresses of Internet resources
Client and server – computing architecture used by most Internet services
Key Protocols:
TCP/IP: The Transmission Control Protocol (TCP) operates at the Transport layer of the protocol stack and facilitates the reliable, ordered and error-checked delivery of data
Ethernet (802.3): This is the predominant wired networking standard, commonly used to connect computers in a LAN. It supports high-speed data transfer and is characterized by its use of twisted-pair cables and fiber optics.
Wi-Fi (802.11): This standard governs wireless networking, allowing devices to connect to the Internet without physical cables. It is essential for modern computing and is widely used in both residential and commercial environments.
Network Types/Characteristics:
Wired networks are networks that utilize physical cables for connections. Examples of wired networks include twisted pair cables, coaxial cables, and fiber optic cables. Commonly found in homes and schools
Twisted-pair cable:
• Pairs of wires twisted together
• Used for telephone and network connectionsCoaxial cable:
• Thick center wire
• Used for computer networks, short-run telephone transmissions, cable television deliveryFiber-optic cable:
• Glass or fiber strands through which light can pass
• Used for high-speed communications, offering greater bandwidth and faster data transmission rates.
Wireless networks on the other hand are connected to the internet without the use of physical ables and instead rely on radio waves for communication. Examples of wireless networks include Wi-Fi, Bluetooth, and cellular networks. Wifi hotspots found in businesses, homes, and schools.
Wireless connections use radio signals
The electromagnetic spectrum is the range of common electromagnetic radiation (energy) that travels in waves
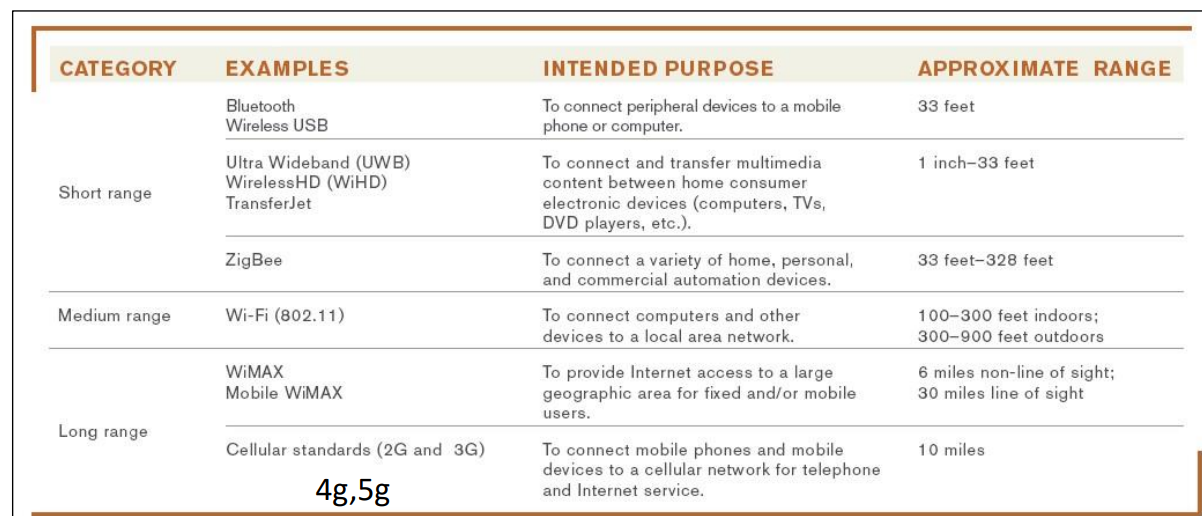
Short-range (such as Bluetooth) can connect a wireless keyboard or mouse to a computer
Medium-range (such as Wi-Fi) are used for wireless LANs and to connect portable computer users to the Internet at public hotspots
Longer-range (WiMAX) can be used to provide Internet access to wide geographic areas
Network Topologies:
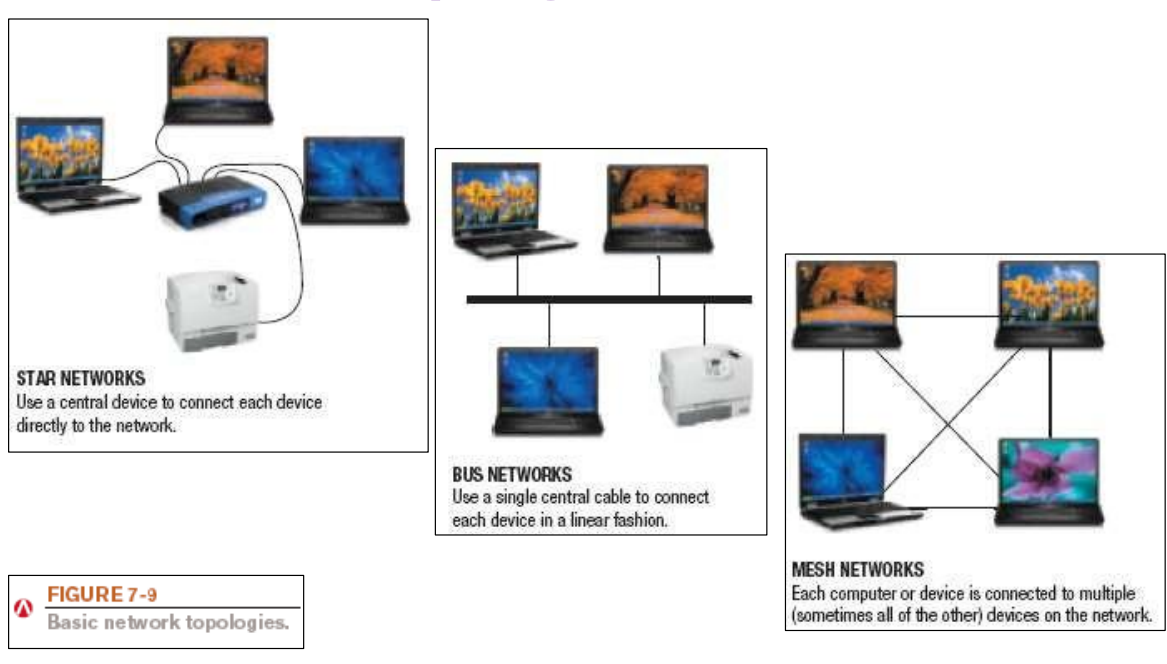
Star: A network that uses a host device connected directly to several other devices
Bus: A network consisting of a central cable to which all network devices are attached
Mesh: A network in which there are multiple connections between the devices on the network so that messages can take any one of several paths
Network Architectures :
Network architecture refers to the structural design of a network, which encompasses both the physical and logical layout of the network components. This includes the arrangement of hardware and software, as well as the data transmission protocols and procedures used to facilitate communication and data exchange. Two main architectures are commonly referenced:
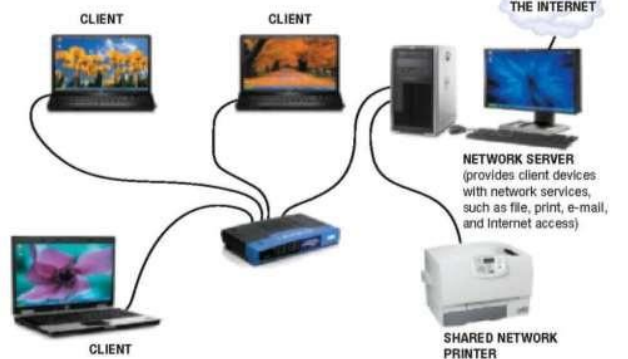
Client-Server Architecture: A client-server network architecture is a computing model where a centralized server provides resources and services to multiple clients over a network
Peer-to-Peer Architecture: Here, each computer or device can act as both a client and a server, allowing for direct communication and resource sharing among users without the need for a centralized server.

Network Size/ Coverage:
Personal area network (PAN): Connects an individual’s personal devices that are located close together.
Local area network (LAN): Connects devices located in a small geographic area , such as a home, office building, or campus, enabling high-speed connections over limited distances.
Metropolitan area network (MAN): Serves a metropolitan area by interconnecting multiple LANs, providing high-speed data transfer for businesses and organizations within the city.
Wide area network (WAN) – Large geographic area that connects multiple LANs and MANs, utilizing various transmission media such as leased lines and satellite links.
Intranet: Private network set up by an organization for use by its employees
Extranet: Intranet that is at least partially accessible to authorized outsiders
Virtual private network (VPN): Secure path over the Internet that provides authorized users a secure means of accessing a private network via the Internet
Data Transmission:
Transmission Direction:
Simplex Transmission: Data travels in a single direction only, meaning that one device transmits data while the other device only receives it, such as in a keyboard to a computer scenario.
Half-Duplex Transmission: Data travels in either direction but only one way at a time ; for example, a walkie-talkie system where one party speaks while the other listens, preventing simultaneous communication.
Full-Duplex Transmission: Data can travel in both directions simultaneously, allowing both devices to transmit and receive data at the same time, similar to a telephone conversation where both parties can talk and listen simultaneously.
Bandwidth: The amount of data that can be transferred in a given period of time – Measured in bits per second (bps)
Timing:
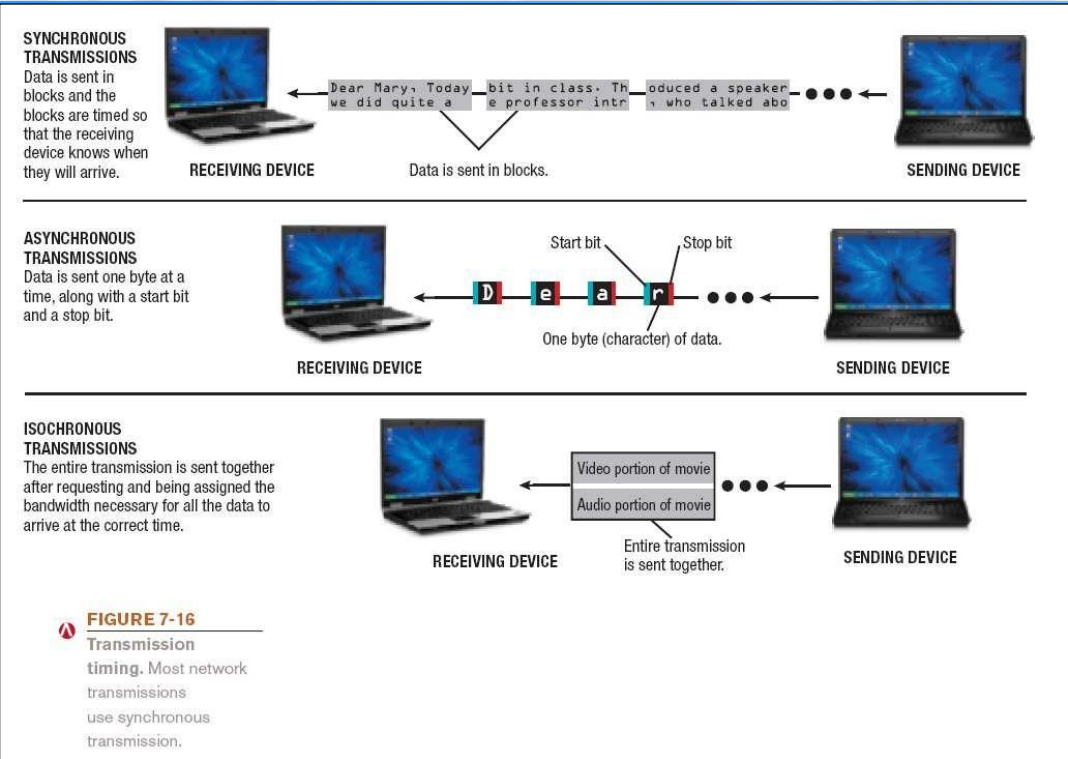
Synchronous transmission - Data is sent in blocks and the blocks are timed so that the receiving device knows when they will arrive.
Asynchronous transmission - Data is sent one byte at a time, along with a start bit and a stop bit
Isochronous transmission - The entire transmission is sent together after requesting and being assigned the bandwidth necessary for all the data to arrive at the correct time.
Connections:
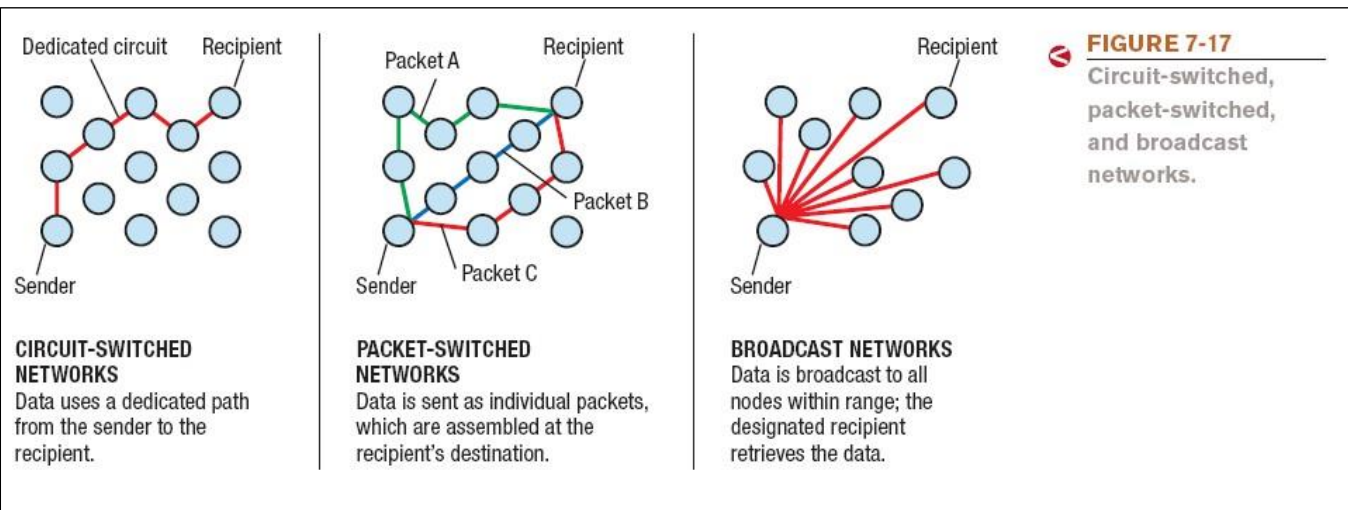
Circuit-switched: Dedicated path over a network is established and all data follows that path
Packet-switched: Messages are separated into small units called packets and travel along the network separately. Used to send data over the Internet
Broadcast: Data is sent out to all other nodes on the network. Primarily used with LANs
Common Applications:
Telecommunication: Facilitates voice and video calls, allowing people to connect globally.
Multimedia Networking and Broadcasting: Supports streaming services and other media-sharing platforms.
GPS and Tracking Systems: Assist with navigation and real-time location tracking.
Telemedicine Services: Enable healthcare professionals to provide remote consultations and patient monitoring.
Networking Hardware:
Network Adapters: Hardware that facilitates connections between a computer and a network. Examples of network adapters: USB, PCI, PCIE, and Express Card
Modems: Device that connects a computer to the Internet or to another computer
Switches: Connects devices in a network like a hub but only sends data to the device for which the data is intended
Routers: Devices that route data between different networks, directing traffic based on IP addresses.
Repeaters: Amplify signals in a network to extend transmission distances.
Hub: Central device that connects all of the devices on the network
Bridge: Connects two or more separate LANs, allowing communication and data transfer between them.
Security Concerns:
Malware: Includes viruses, worms, and spyware that can infiltrate networks, causing data breaches and system failures.
Denial of Service Attacks: attackers make resources (server, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus traffic
Packet Sniffing: The practice of intercepting data packets as they travel through networks, which could lead to unauthorized access to sensitive information.
A switch is generally considered better than a hub for several reasons:
Traffic Management: A switch intelligently manages data traffic. It sends data only to the device that needs it rather than broadcasting it to all connected devices like a hub does.
Efficiency: Because switches minimize unnecessary data transmission, they result in lower traffic congestion and improved network performance.
Full-Duplex Communication: Switches can simulate full-duplex communication, allowing devices to send and receive data simultaneously. In contrast, hubs typically operate in half-duplex mode, where devices cannot communicate at the same time.
Security: Using a switch offers enhanced security because data is sent directly to specific devices, making it harder for unauthorized users to eavesdrop on other traffic.
Improved Bandwidth Utilization: Switches allow multiple communication paths, enabling more efficient use of available bandwidth. Each connection can operate independently, which is not the case with hubs.
A circuit-switched network is a type of communication network where a dedicated communication path or circuit is established between two endpoints for the duration of their communication session. This process involves the following key characteristics:
Dedicated Connection: Once the circuit is established, the entire bandwidth of the connection is reserved for the two communicating parties, allowing for a consistent and stable connection.
Call Setup: Before communication begins, a call setup phase is required to establish the dedicated path. This process can introduce latency before data transmission starts.
Continuous Stream of Data: During the communication, data flows continuously over the established circuit, resulting in low latency and a predictable quality of service.
Resource Inefficiency: Resources may remain idle if one end of the communication is silent, as the dedicated circuit cannot be utilized by other users until the connection is terminated.
Circuit switching is traditionally used in telephone networks and is ideal for applications requiring consistent communication quality, such as voice calls.
Analog Signals:
Continuous waveforms that represent physical measurements.
Can take any value in a given range, depicting a smooth variation over time.
Examples include sound waves and temperature readings.
Typically more susceptible to noise and interference during transmission, which can distort the signal.
Digital Signals:
Discrete signals that represent data as a sequence of distinct values (usually binary).
Typically encoded in bits, making them less prone to interference and noise, which enhances transmission quality.
Examples include computer data and digital audio.
More efficient for storage and transmission in modern communication
RFID (Radio Frequency Identification) is a technology that uses electromagnetic fields to automatically identify and track tags attached to objects. Here’s how it works:
Components: RFID systems consist of three main components:
RFID Tags: These are small devices consisting of a chip (that stores data) and an antenna (that transmits the data). Tags can be either passive (powered by the reader’s signal) or active (battery-powered).
RFID Readers: Devices that emit radio waves to activate the RFID tags and read their information.
Middleware: Software that processes and manages the data collected from RFID tags.
Operation:
When an RFID reader sends out a radio signal, it provides energy for passive tags to become active. Active tags do not require this energy from the reader.
Once activated, the RFID tag transmits its stored data back to the reader via radio waves.
The reader then captures the information and sends it to the middleware for processing.
Applications:
RFID technology is widely used in various applications, including inventory management, asset tracking, access control, and identification systems. Its ability to read tags without line-of-sight, and from various distances, makes it versatile and efficient.
Cable used for providing cable television is designed to carry many television signals through a process called multiplexing. Here’s how it works:
Broadband Capacity: The cables (typically coaxial or fiber optic cables) have a high bandwidth capacity that allows them to transmit multiple signals simultaneously.
Multiplexing Techniques: Signals are combined using multiplexing techniques, which allow multiple signals to share the same physical medium without interference. This is accomplished through:
Frequency Division Multiplexing (FDM): Different television channels are assigned specific frequency ranges within the same cable, enabling the simultaneous transmission of multiple programs.
Time Division Multiplexing (TDM): Channels are allocated specific time slots on the cable, allowing channels to take turns transmitting data.
High Signal Quality: Coaxial cables are designed to minimize signal loss and interference, ensuring that multiple signals can be transmitted over long distances without significant degradation in quality. Fiber optic cables, on the other hand, use light signals to transmit data, allowing for even more channels and higher quality.
Signal Modulation: Television signals are modulated onto these multiplexed signals, allowing efficient transmission and reception. Different modulation techniques (such as QAM) are used to encode the signal, improving the ability to carry more channels.
Amplifiers and Splitters: In the cable network infrastructure, amplifiers are used to boost signals and splitters allow signals to be distributed to multiple outlets within homes, maintaining signal strength and quality.
In a star network topology, data transmission is managed through a central hub or switch that connects all devices in the network. Here’s how data is transmitted:
Device Connection: Each device (computer, printer, etc.) is connected directly to the central hub/switch through individual cables.
Data Sending: When a device wants to send data to another device, it sends the data to the hub first.
Data Processing: The hub processes the incoming data and determines the destination device.
Data Forwarding: The hub then forwards the data to the specific device that it was intended for, rather than broadcasting it to all connected devices.
Efficient Traffic Management: This method allows for efficient network traffic management, minimizes collisions, and facilitates easier troubleshooting since issues can be isolated to specific connections.
Client-Server Architecture:
In this model, a centralized server provides resources and services to multiple client machines, managing the requests and responses within the network.
This centralized approach allows for better control of resources, enhanced security, and easier management, as the server can monitor and handle multiple client requests efficiently.
However, a single point of failure risks the entire network if the server goes down.
Peer-to-Peer Architecture:
In this model, each computer or device can act as both a client and a server, allowing for direct communication and resource sharing among users without the need for a centralized server.
This decentralized structure increases redundancy and can enhance reliability, as there is no single point of failure.
However, it may lead to challenges in managing resources and security since each peer operates independently.