2.5 - CompTIA A+ Core 2
2.5a - Social Engineering: Professor Messer
Social engineering
Phishing
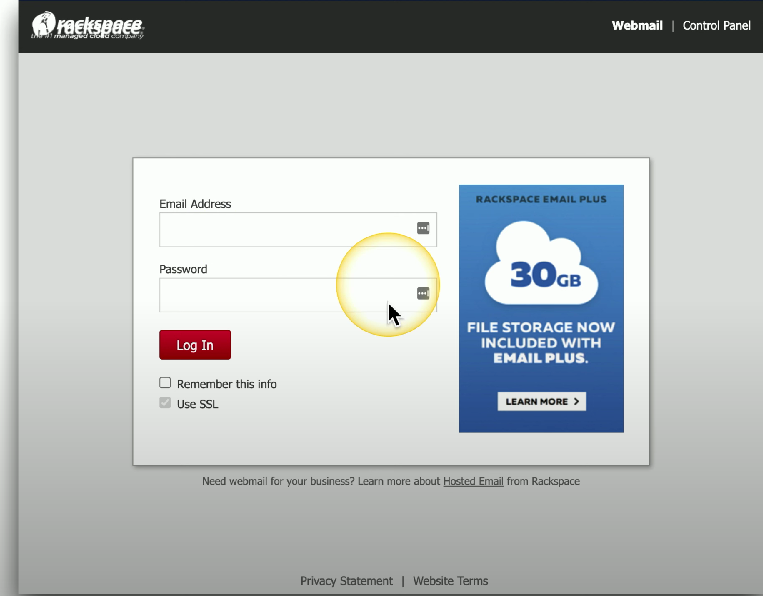
Phishing: A social engineering attack that involves impersonation of a legitimate organization, often delivered by email or text. The text/UI of the phishing site typically seems a bit “off”.
Vishing: A phishing attack conducted over a phone call.
Smishing/SMS-shing: A phishing attack conducted with SMS messages.
QR code phishing: A phishing attack conducted via QR codes.
Spear phishing: A phishing attack that targets a specific person or group and often includes information that interests the target.
Whaling: A phishing attack targeting senior-level executives, such as CEOs, CFOs, or other C-suite executives.
Shoulder surfing

Shoulder surfing: A social engineering attack involving an individual looking over their target's shoulder to see the information on their display. It can also be done over long distances via binoculars or telescopes. Mitigated by being aware of your surroundings in public places, or using a privacy filter on your screen. impersonating
Tailgating
Tailgating: A security breach method in which an unauthorized person follows an authorized individual into a secured area by taking advantage of their access. Mitigated by organizations having clear policies on visitors (no tailgating signs, one person at a time, questioning individuals with no name badge).
Piggybacking: A similar security breach method to tailgating, where an authorized person allows an unauthorized individual to gain access to a secured area.
Impersonation
Impersonation: Pretending to be someone else to gain unauthorized access to systems or sensitive information. Some attackers may pretend to be someone higher in rank to pressure victims, or throw a lot of jargon around to confuse victims.
Dumpster diving
Dumpster diving is searching through trash or recycling bins to find discarded items that can provide personal information, such as paper documents containing credit card or account details.
Threats
Evil twin
Evil twin: A spoofing attack where an attacker creates a fraudulent Wi-Fi point that appears legitimate, with the same (or similar) SSID settings/captive portal. Use encryption (HTTPS and a VPN) to mitigate.
2.5b - Denial of Service: Professor Messer
Threats
Denial of service (DoS)
Denial of service (DoS): A cyber attack where an attacker causes a service to fail/overloading it. Can be executed accidentally (e.g., turning off power from a server accidentally, or overloading a slower network connection with large downloads).
Distributed denial of service (DDoS)
Distributed denial of service (DDoS): A type of DoS attack where multiple compromised systems are used to flood the target with traffic, making it harder to mitigate or trace the attack.
DDoS attack mitigation: Filtering out DDoS/botnet-specific traffic patterns, anti-DDoS technology from internet service providers, and DDoS attack blocking from third-party network providers like Cloudflare
2.5c - Zero-Day Attacks: Professor Messer
Threats
Zero-day Attacks
Zero-day Attacks: Attacks based on unpatched vulnerabilities in software that are exploited before the software vendor releases a fix or update.
Common Vulnerabilities or Exposures Database (CVE): Database offered by the MITRE corporation that tracks vulnerabilities and the operating systems/software they target.
2.5d - On-Path Attacks: Professor Messer
Threats
On-Path Attacks
On-path attack: Sometimes called a man-in-the-middle attack (MiTM) - occurs when an attacker intercepts a conversation by placing themselves between a receiving and sending device. The attacker can read and alter the data sent between the two devices.
ARP poisoning attack: Occurs when an attacker manipulates the Address Resolution Protocol (ARP) cache in a network, allowing them to intercept traffic intended for a different device by associating their MAC address with the IP address of the target device.
On-path browser attack: Uses a malware or a Trojan to set up a proxy that enables the attacker to intercept and manipulate web traffic without the user's knowledge, often capturing sensitive information such as login credentials or financial data.
2.5e - Password Attacks: Professor Messer
Hash: Translates data (e.g., passwords) into a fixed-length text string. When a user inputs their password, the hashing algorithm translates the input and then compares it to the user’s stored password.
Threats
Brute-force attack
Brute-force attack: A password attack that cracks passwords by trying every possible combination of characters until the correct password is found, often utilizing automated tools to expedite the process.
Dictionary Attack
Dictionary attack: A password attack that uses a set of words and phrases, typically from a predefined list or dictionary, to guess the user's password, making it quicker than brute-force attacks when the target uses common or predictable passwords.
2.5f - Insider Threats: Professor Messer
Threats
Insider Threats
Insider Threats: Refers to risks that originate from within an organization, primarily involving employees, contractors, and other internal resources who may exploit their access to systems and data for malicious purposes.
Protecting against insider attacks: Solid security fundamentals - proper privilege/data access control, zero trust models, and robust backups of any sensitive data.
2.5g - SQL Injection: Professor Messer
Threats
SQL Injection
SQL injection: A security attack that uses crafted SQL queries to manipulate a database and view sensitive information.
Protecting against SQL injections: Use input validation to remove any potentially harmful characters or patterns from user input before processing it.
2.5h - Cross-site Scripting (XSS)
Threats
Cross-site scripting (XSS)
Cross-site scripting (XSS): An injection attack where malicious scripts (typically written via JavaScript) are inserted into otherwise non-malicious and trusted websites and are then returned to users.
Reflected Cross-site scripting (Reflected XSS): A cross-site scripting (XSS) attack where an attacker injects malicious code into a web application, and the application immediately reflects the user's input back to the user in the response.
Stored Cross-site scripting (Stored XSS): A type of cross-site scripting (XSS) attack where the injected malicious script is permanently stored on the target server, and is served to users who access the page containing the script at a later time.
2.5i - Security Vulnerabilities
Vulnerabilities
Non-compliant systems
Non-compliant systems: Occurs when a computer fails to adhere to established security controls or standards (typically an SOE/standard operating environment), leading to security risks related to the mismatched configurations.
Solving non-compliant systems: Performing periodic scans to check for non-compliance, and applying policies that will prevent non-compliant policies or require correction before systems are given access.
Unpatched systems
Unpatched systems: Occurs when a system is missing relevant OS manufacturer patches or software updates, making it vulnerable to exploitation from malware and other security threats.
Unprotected systems (missing antivirus/missing firewall)
Unprotected systems: Occurs when a system misses a crucial security component (e.g., antivirus, firewall). Typically results from an application that cannot function with the proper security controls, and requires balancing application troubleshooting without removing security controls.
EOL
End of life (EOL): A point when a manufacturer provides no additional updates to an operating system or software, leaving it vulnerable to security risks and lacking necessary patches. Requires finding another way to perform a job function, such as using alternative software or upgrading to a more secure system, to continue productivity.
Bring your own device (BYOD)
Bring your own device (BYOD): A policy that allows employees to use their personal devices, such as smartphones, tablets, and laptops, for work purposes, which can improve productivity but also raises security concerns regarding sensitive data protection and privacy.
Other Threats
Spoofing
Spoofing: A fraudulent practice in which an attacker disguises themselves as a legitimate entity to gain unauthorized access to sensitive information or systems, often through techniques like email spoofing, MAC address spoofing, or IP address spoofing.