2.2 - CompTIA A+ Core 2
2.2a - Windows Defender Antivirus: Professor Messer
Defender Antivirus
Windows Defender: Built-in anti-malware/anti-virus for Windows. All information found for Windows Defender was found via the “Windows Security” app
Activate/deactivate
Avoid disabling Defender Antivirus - deactivation increases risk of malware infection.
Windows Defender Antivirus operates in real-time, although this feature can be disabled: Virus & threat protection settings → Manage settings → Real-time protection. Click the toggle to deactivate (or reactivate) Real-time protection.
Update definitions
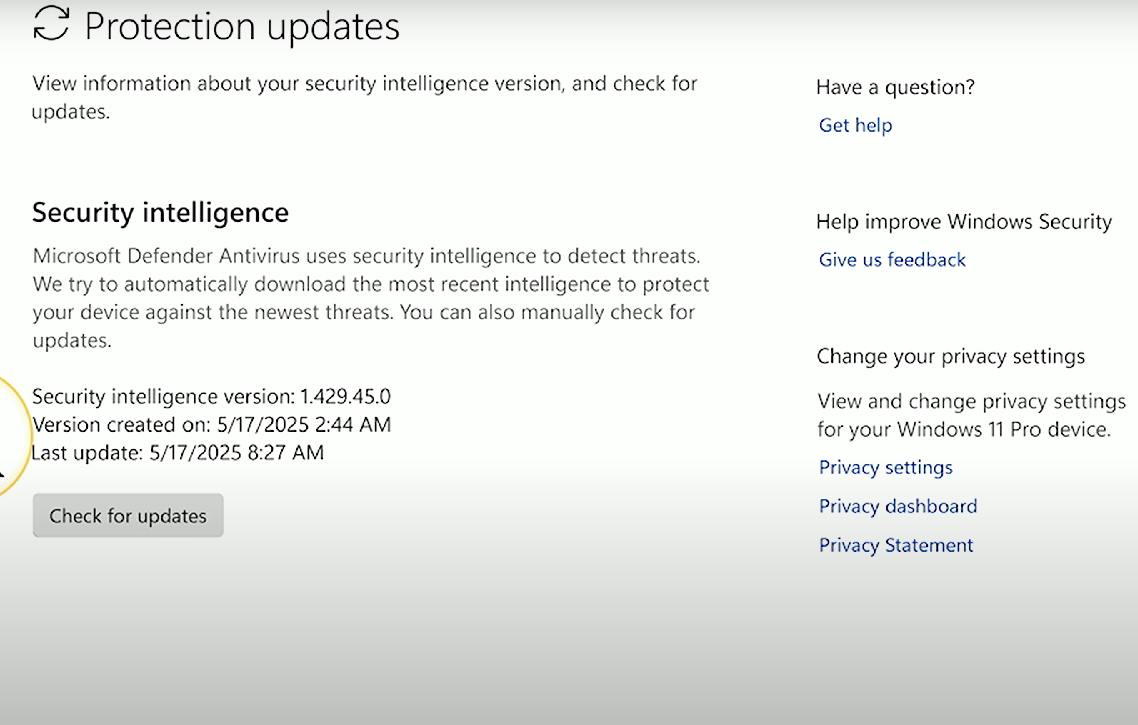
Update definitions: Refers to updating AV signatures to allow Windows Defender to identify new malicious software. To manually update, click on Virus & threat protection updates (or Current Threats), then click the “Check for updates” button.
2.2b - Windows Firewall: Professor Messer
Firewall
Windows Firewall: Security feature that monitors ingress/egress network traffic on a Windows machine for malicious activity.
Windows Firewall should always be enabled, but it can be temporarily disabled for troubleshooting.
Activate/deactivate
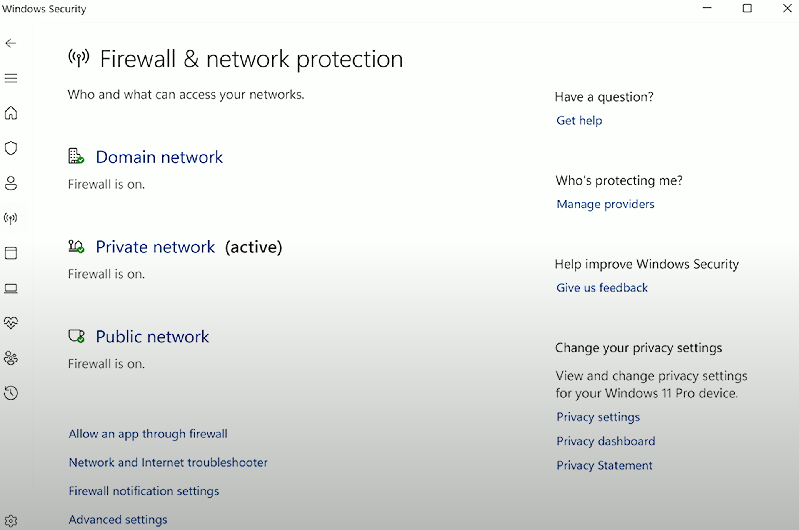
Activate/deactivate Windows Firewall: Accessible from the Windows Control Panel (Windows Security Firewall applet) or the Windows Security app, allowing users to toggle the firewall settings as needed. Requires Administrator/elevated permissions to activate or deactivate. Navigate to the active network profile, then click the toggle under the “Microsoft Defender Firewall” heading to activate/deactivate.
Port security
Port security: Refers to Windows Firewall rules that allow/deny traffic on a specific port.
Example rule - blocking HTTP traffic (TCP port 80):
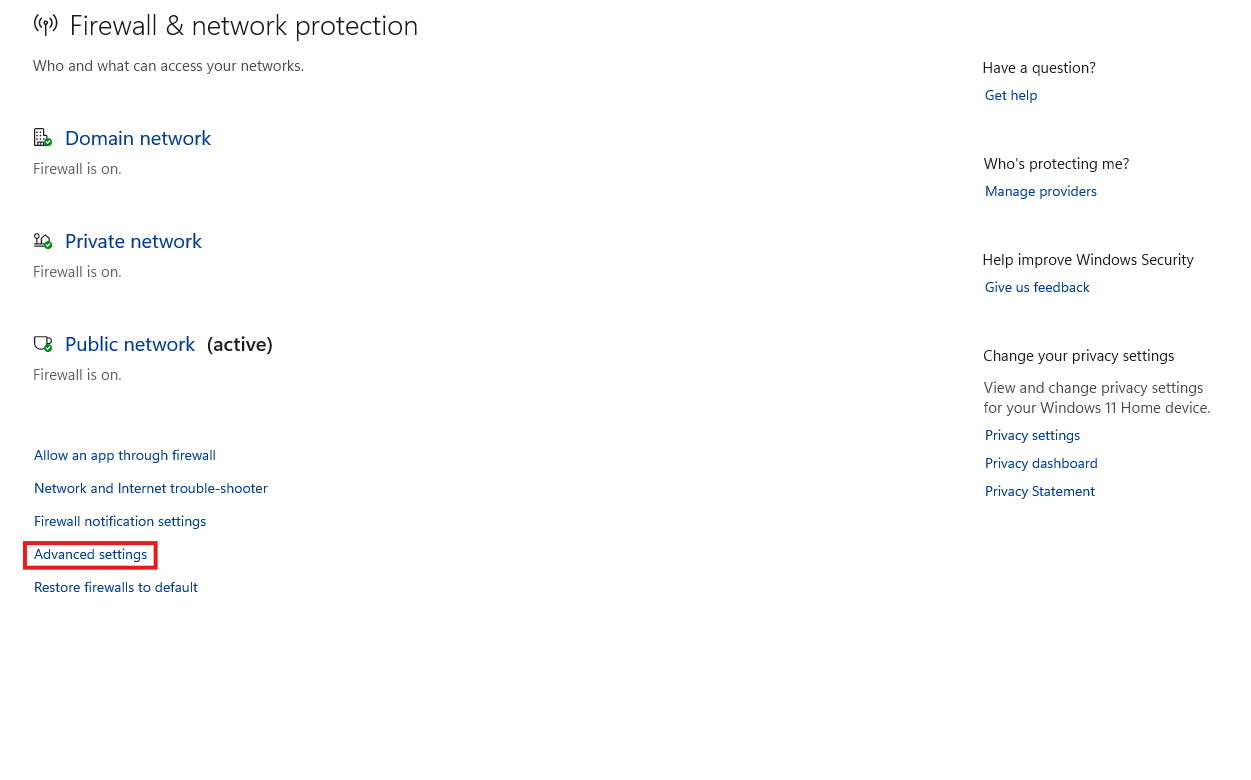
To create this rule, navigate to the Windows Firewall settings, select 'Advanced settings'
Click on 'Inbound Rules' and ‘New rule’ to activate the “New Inbound Rule Wizard.”
From there, you select “Custom” to configure a new rule
Select “All Programs.”
Select TCP from the “Protocol type” dropdown and select 4 (or 6) from the “Protocol number” up-down control
Add port 80 to the “Local port:” field - leave the “Remote port:” field empty.
Select 'Block the connection' on the to prevent HTTP traffic.
Application security
Application security: Refers to Windows Firewall rules that allow/deny traffic related to a specific application.
Notifications
Notifications: Windows Security feature that allows users to receive alerts for firewall/network protection. These can be toggled on/off by profile (i.e., public, private networks). Accessible via the Windows Security app: Settings → Manage notifications and displays options for Virus protection, account protection, and firewall/network protection.
2.2c - Windows Security Settings: Professor Messer
User and groups
Accessible via Local Users and Groups in the MMC (
lusrmgr.msc).
Local vs. Microsoft account
Local account: A user account that is associated with a specific Windows device.
Microsoft account: A user account that allows settings to be synced between devices and integrates with Microsoft applications (Skype, Office, OneDrive).
Domain account
Domain account: Windows account centrally managed via Active Directory - commonly used for business/work environments.
Standard account
Standard account: A typical user account within Windows.
Administrator
Administrator: The Windows super-user account with full access/privileges on the system.
Guest user
Guest account: A Windows account with limited access to the system.
Power user
Power user: A standard account with elevated privileges that allows slightly more control over the system settings than a typical user account. Permissions are removed for Windows Vista and later.
Log-in OS options
Username and password
Username/password: Common method to authenticate or log-in to a Windows OS. Includes a name, and a unique character string associated with an account.
Personal identification number (PIN)
Personal identification number (PIN): Authentication/log-in method that involves the use of a 4-digit number.
Fingerprint
Fingerprint: A biometric authentication method that scans and compares the ridges on someone’s fingers to a stored template.
Facial recognition
Facial recognition: A biometric authentication method that scans a person’s face.
SSO
Single-sign on (SSO): A user authentication process that allows a user to access multiple applications (or in this case, the OS), with one set of login credentials - typically Windows Domain/AD credentials.
Passwordless/Windows Hello
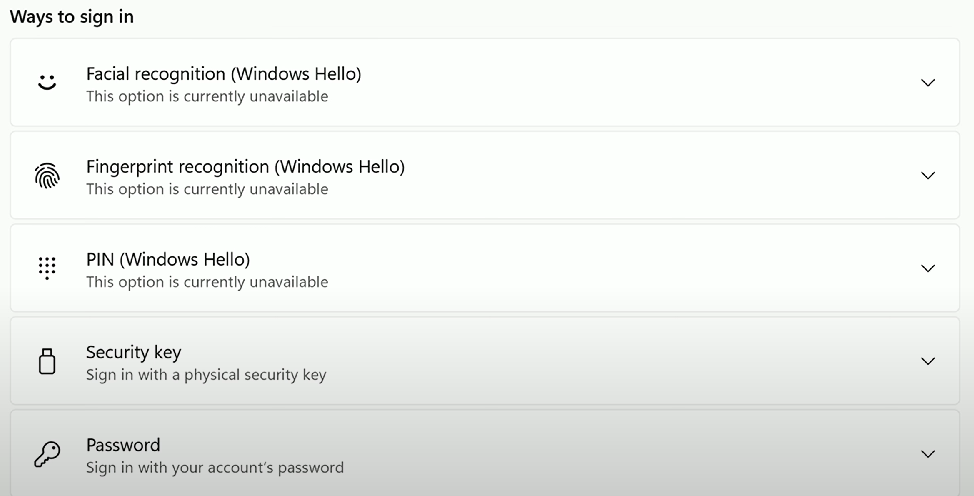
Passwordless authentication: A secure method that allows users to log in without traditional passwords, often using biometrics such as facial recognition or PIN codes, exemplified by Windows Hello.
Not typically used as the primary authentication method, typically combined with a password for multi-factor authentication.
NTFS vs. share permissions
NTFS permissions: File system permissions that provide fine-grained control over access to files and folders - apply from both local and network connections. NTFS permissions also exhibit inheritance for files regulated by their parent folder.
Share permissions: Permissions that are applied when a user accesses a shared folder over a network - only applies for network connections.
NTFS vs. network share perms contrast: If there is a contrast between access settings (e.g, Deny for Shares and allow for NTFS - or vice versa), the most restrictive setting wins.
File and folder attributes
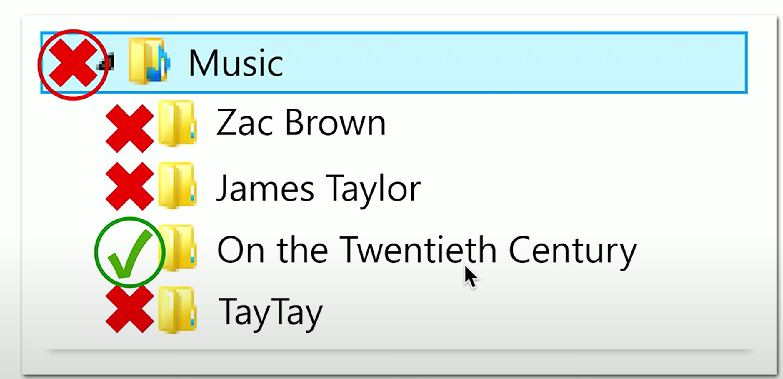
Explicit permissions: Default permissions for a file/folder.
Inherited permissions: Permissions taken from the parent object (e.g., a folder) to the child object (sub-files, sub-folders). A permission is set once, and it applies to everything underneath.
Explicit vs. inherited permissions conflict: Explicit permissions take precedence over inherited permissions.
Inheritance
Run as administrator vs. standard user
Run as administrator vs. standard user: When running programs, a standard user may face limitations that an administrator would not, such as restricted access to system files or settings. This requires a user to select the "Run as administrator" option for an application, even if they’re in the Administrators group.
User Account Control (UAC)
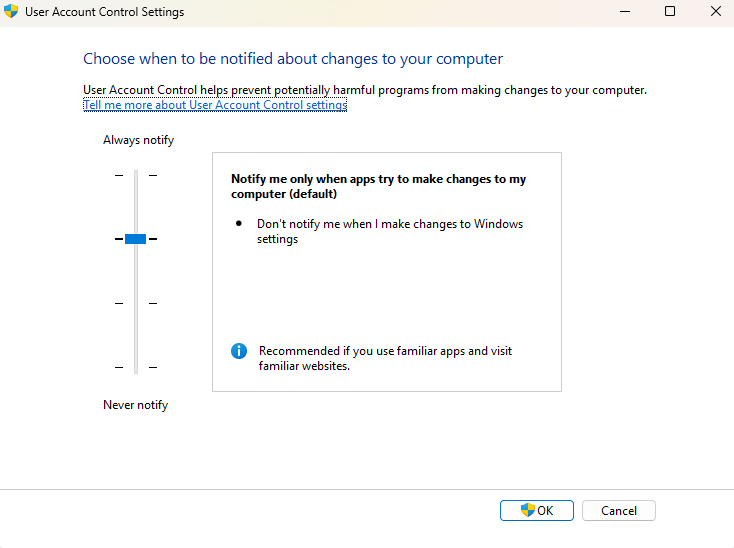
User Account Control (UAC): Windows utility that allows notifications to the user when a program attempts to make changes that require administrative privileges (e.g., installing applications or configuring RDP).
BitLocker
BitLocker: A feature included with Windows that helps protect data by full disk encryption (FDE), requiring authentication before allowing access to the encrypted volume. Supported by all Windows editions except Home.
Ensures confidentiality by encrypting the entire drive, thereby protecting sensitive information from unauthorized access, even if the drive is removed from the system.
BitLocker-To-Go
BitLocker-To-Go: A feature that extends BitLocker encryption to removable drives, allowing users to secure data on USB drives and other portable storage devices.
Encrypting File System (EFS)
Encrypting File System (EFS): Allows encryption of data with filesystems - requires the NTFS file system to operate. Available in all Windows editions except Home. Administrative password resets will delete data protected by EFS, so ensure that you have a backup of system files.
2.2d - Active Directory: Professor Messer
Active Directory

Active Directory: A centralized database of everything on a network (computers, users accounts, file shares, printers, groups) provided by Windows. AD also allows authentication by logging in with AD credentials, and centralized access control - admins can determine which users can access which resources.
Joining a domain
Domain: Name associated with a related group of users, computers, and resources - every domain has a name.
Domain controller (DC): Centralized server that stores all information related to the AD domain database.
Often referenced when troubleshooting - e.g., to check if a computer is on the domain, or if you can reset the domain password.
Joining a domain (process): Navigate to your computer’s information in Windows Settings: (System → About). Click on “Domain or workgroup”: Enter the domain name you wish to join, then click OK to proceed with the authentication process and follow any on-screen prompts. Navigate to the Scripts from User Configuration → Policies → Software Settings → Scripts. Click “Add,” and then
“Browse…” to check/add a configured script.
Assigning a log-in script
Log-in script: A script that automates a series of tasks at login. Can be assigned to a specific user, group, or OU.
Assigning a log-in script: Access the Domain Controller for the relevant domain, and select “Group Policy Management Editor” from the “Tools” drop-down. Right-click the relevant OU, and then select the “Create a GPO in this domain” option.
Moving objects within organizational units
Organizational units (OU): Logical sections to organize objects/devices in Active Directory.
Moving objects within organizational units: Requires the Active Directory Users and Computers (ADUC) tool. Within ADUC, right-click on the object, click the “Move” option, and select the OU to which the object will be relocated.
Assigning home folders
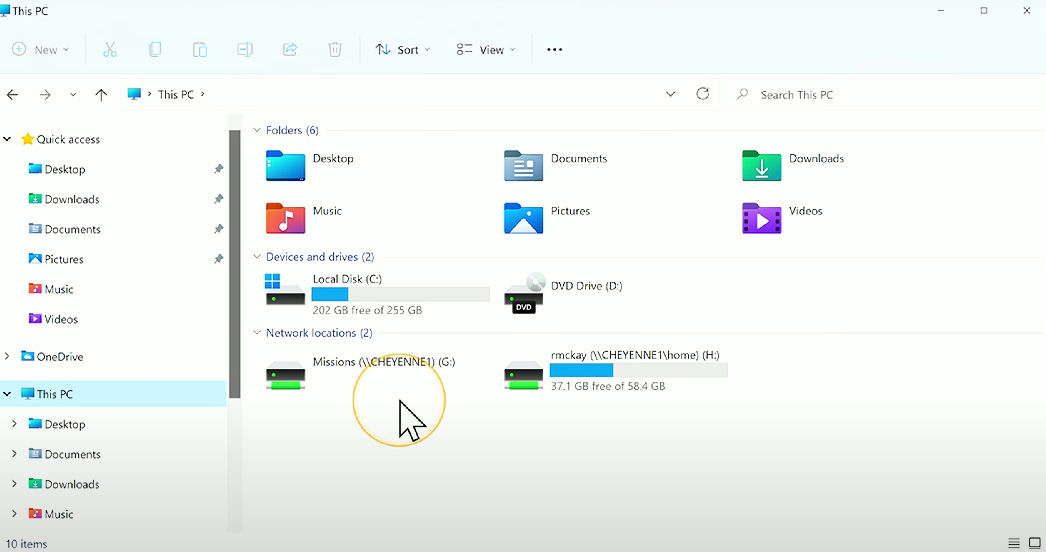
Home folders: Networked folders designed to be used as an alternative to users’ local drives.
Assigning home folders: Within Active Directory Users and Computers (ADUC), click on the relevant OU, then right-click + drag to select all users. Right-click, then select “Properties...”. Navigate to the “Profile” tab, click the “Home folder,” then “Connect:,” select the relevant drive letter (e.g., “H:”), then specify the share location (e.g.,
\\SERVER\home\%username%). Sign out, then sign in again for a relevant user to view the change.
Applying Group Policy
Applying Group Policy: Access the Domain Controller for the relevant domain, and select “Group Policy Management Editor” from the “Tools” drop-down. Right-click the relevant OU, and then select the “Create a GPO in this domain” option. Navigate to the policy you want to enable, Double-click to open its dialog box, then click “Enabled” to enable the policy. Run the
gpupdate /forcecommand to force an update to Group Policy settings on the relevant systems.Group Policy: Managed within the Group Policy Management Editor (
gpmc.msc), and provides a central console for login scripts, quality of service (QoS) network configs, and security parameters.
Selecting security groups
Security group: Groups used to assign permissions to shared resources.
Selecting security groups: Navigate to Active Directory Users and Computers, then to the particular user you want to add to a security group. Right-click, then click “Properties…”, click the “Member Of” tab, and click the “Add…” button. Type in the group/object name, then select your desired security group.
Configuring folder redirection
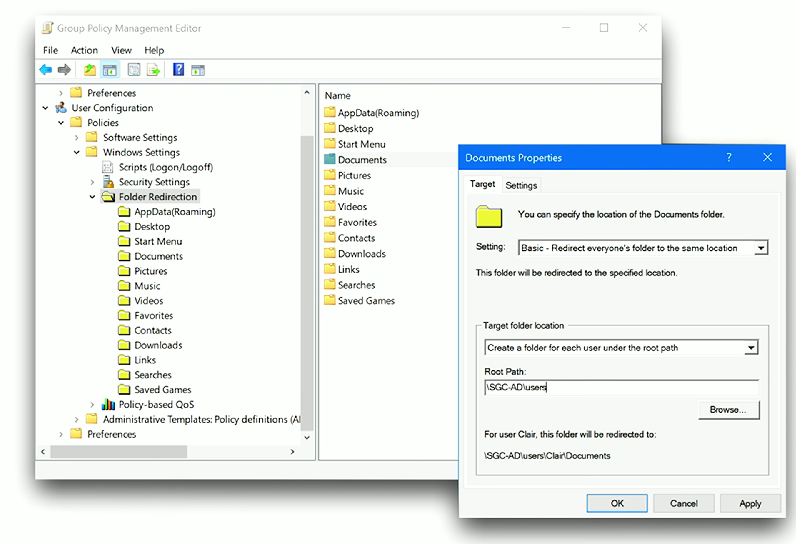
Folder redirection: Redirects the path of user folders to a networked share. Users can still save files/interact with the folders (e.g., Desktop, Downloads, Documents, Pictures), in File Explorer as if they were a part of the local drive, but the contents/folders are saved onto a local share. Often paired with the “Offline Files” feature.
Configuring folder redirection: Navigate to Folder Redirection - Group Policy Management Editor → User Configuration → Folder Redirection. Click + drag to select all folders (or click on a single folder), change the “Setting:” field to Basic, then enter the redirected folder path (e.g.,
\\SERVER\home\%username%\Documents).