IS 101 module 1
Course Overview
TestOut Office Pro helps you learn how to use Microsoft Office apps and basic computer skills through interactive exercises. The course covers Microsoft Word, Excel, PowerPoint, Access, and Outlook. It prepares students for Microsoft Office Specialist (MOS) exams, which test your knowledge in different Office apps. The exams covered include:
Microsoft 365 MOS Exams: Word, Excel, PowerPoint
Office 2019 MOS Exams: Word, Excel, PowerPoint, Outlook, Access
The course has 8 chapters:
Online Essentials
This chapter covers the basics of using the internet and digital tools, such as understanding file types, using web browsers, social media, email, and cloud services. Students will practice browsing websites, sending emails, and setting up privacy and security online.
Computer Essentials
Here, students learn about computer parts, operating systems, and software. Topics include file management, installing apps, networking, and using databases. Students will also practice tasks like connecting to a wireless network and managing files.
Common Office Features
This chapter covers features common in Microsoft Office apps, like using the ribbon (the toolbar), dialog boxes, and print settings. Students will learn how to navigate documents, format images, and customize their workspace.
Microsoft Word
In this chapter, students practice using Word to create and format documents. They'll learn how to add images, tables, and headers, use themes, and track changes in collaborative documents.
Microsoft Excel
Students will practice using Excel to create and manage spreadsheets. They’ll learn how to enter data, perform calculations, organize data in charts, and use PivotTables to summarize information.
Microsoft PowerPoint
This chapter teaches how to create and deliver slide presentations. Students will learn how to add images, tables, videos, and animations to slides, as well as how to format and manage presentations.
Microsoft Access
In this chapter, students learn how to use Access to create and manage databases. They will practice building forms, generating reports, and writing queries to find data.
Microsoft Outlook
This chapter focuses on managing email, calendars, and contacts in Outlook. Students will learn how to send emails, schedule appointments, and organize contacts.
0.5 how to use simulated labs
Simulated Labs Overview
The labs in this course help you learn and remember the basic skills needed to use Microsoft Office. To explore the features more deeply, you should also use live Office apps. Below are tips to help you get the most out of the labs.
Maximizing Learning in the Simulated Labs
Skills Labs
First, watch the instructional videos. Then, try doing the tasks in the Skills lab without looking at hints or the "Show Me" video. If you can’t complete a task, try it again after going back to the end of the list.Challenge Labs
After finishing the Skills lab, complete the Challenge lab several times. Each Challenge lab has three different sets of tasks, so you’ll get a new set of tasks each time you do it. The tasks will appear in random order, so you can keep challenging yourself and try to finish faster before moving on to the Applied labs.Applied Labs
The Applied labs help you practice skills in real-life situations. Carefully read the scenario and focus on using the Office features you’ve learned so far.Note: If you're tracking progress with the LabSim course outline, you must score 100% on a lab to get a green check mark.
Re-read the Scenario
Go back and read the task instructions again. Did you miss a detail, like what to type or which cells to select?
View Hints
For Skills and Challenge labs, click "Hint" or "Show Me" to get help with the steps.
For Applied labs, read the Explanation in the Lab Report after you click "Done." Then go back to the lab and try again. If you need more help, watch the video for that skill from the table of contents.Try an Alternate Path
The simulated labs offer multiple ways to complete tasks, just like the real apps. If you're an experienced Office user, you might find some features aren't available in the labs. When this happens, you'll see a "Feature Not Simulated" message, and you’ll need to use a different method to complete the task.Close and Restart Your Web Browser
If the lab isn’t working well, try closing and restarting your web browser. Log in again to continue the lab.
0.7 keyboard Shortcuts in lab charts
Table 1: Microsoft Word | |
Shortcut | Action |
|---|---|
Ctrl + B | Bold selected characters |
Ctrl + I | Italicize selected characters |
Ctrl + U | Underline selected characters |
Ctrl + Equals Sign (=) | Apply subscript formatting to selected text |
Ctrl + Shift + Plus Sign (+) | Apply superscript formatting to selected text |
Ctrl + Spacebar | Clear formatting of selected text |
Ctrl + C | Copy selected text or objects |
Ctrl + X | Cut selected text or objects |
Ctrl + V | Paste text or objects from the clipboard |
Ctrl + Z | Undo the last action |
Ctrl + Y | Redo the last undo |
Ctrl + O | Display the Open tab in Backstage View |
Ctrl + P | Display the Print tab in Backstage View |
Ctrl + S | Save a document |
Ctrl + * | Show/hide paragraph formatting symbols |
Ctrl + F1 | Expand/collapse the ribbon |
Tab | Insert a tab character |
Ctrl + 1 | Single-space lines |
Ctrl + 2 | Double-space lines |
Ctrl + E | Center a paragraph |
Ctrl + R | Right-align a paragraph |
Ctrl + L | Left-align a paragraph |
Ctrl + J | Justify a paragraph |
Alt + Ctrl + 1 | Apply the Heading 1 Style |
Alt + Ctrl + 2 | Apply the Heading 2 Style |
Backspace | Delete one character to the left |
Delete | Delete one character to the right |
Ctrl + Enter | Insert a page break |
Ctrl + Shift + Enter | Insert a column break |
Alt + Ctrl + C | Insert a copyright symbol |
Alt + Ctrl + R | Insert a registered trademark symbol |
Alt + Ctrl + T | Insert a trademark symbol |
Shift + Right Arrow | Extend a selection one character to the right |
Shift + Left Arrow | Extend a selection one character to the left |
Shift + End | Extend a selection to the end of a line |
Shift + Home | Extend a selection to the beginning of a line |
Shift + Down Arrow | Extend a selection one line down |
Shift + Up Arrow | Extend a selection one line up |
Shift + Page Down | Extend a selection one screen down |
Shift + Page Up | Extend a selection one screen up |
Ctrl + A | Extend a selection to the entire document |
Tab (Tables) | Move the cursor to the next table cell |
Shift + Tab (Tables) | Move the cursor to the previous table cell |
Shift + Arrow | Extend a selection of table cells |
Left Arrow | Move the cursor one character to the left |
Right Arrow | Move the cursor one character to the right |
Up Arrow | Move the cursor up one line |
Down Arrow | Move the cursor down one line |
End | Move the cursor to the end of a line |
Home | Move the cursor to the beginning of a line |
F7 | Begin the spell checker |
Shift + F7 | Open the Thesaurus pane |
Shift + Click | Expand selection of text from cursor to click |
Ctrl + F | Display the Find and Replace dialog box |
Ctrl + H | Display the Find and Replace dialog box |
Ctrl + K | Display the Insert Hyperlink dialog box |
Ctrl + D | Display the Font dialog box |
Ctrl + Left Arrow | Move the cursor left one word |
Ctrl + Right Arrow | Move the cursor right one word |
Ctrl + Down Arrow | Move the cursor down one paragraph |
Ctrl + Up Arrow | Move the cursor up one paragraph |
Ctrl + Home | Move the cursor to the beginning of the document |
Ctrl + End | Move the cursor to the end of the document |
Ctrl + Shift + C | Copy the styles of selected text |
Ctrl + Shift + V | Paste the styles of selected text |
Table 2: Microsoft Excel | |
Shortcut | Action |
|---|---|
Ctrl + ` | Show Formulas |
Ctrl + 1 | Display the Format Cells dialog box |
Ctrl + 2 | Bold selected characters |
Ctrl + 3 | Italicize selected characters |
Ctrl + 4 | Underline selected characters |
Ctrl + B | Bold selected characters |
Ctrl + C | Copy selected text or cells |
Ctrl + G | Display the Go To dialog box |
Ctrl + I | Italicize selected characters |
Ctrl + O | Display the Open tab in Backstage View |
Ctrl + P | Display the Print tab in Backstage View |
Ctrl + S | Save a workbook |
Ctrl + U | Underline selected characters |
Ctrl + V | Paste selected text or cells |
Ctrl + X | Cut selected text or cells |
Ctrl + Z | Undo the last action |
Ctrl + F1 | Expand/collapse the ribbon |
Backspace (Selected Cells) | Clear the contents of the first cell in the selection |
Delete (Selected Cells) | Clear the contents of each of the selected cells |
Shift + F3 | Insert a formula |
Alt + Equals Sign (=) | AutoSum |
F2 | Enter cell edit mode |
F4 | Cycle through the combinations of absolute and relative references |
F8 | Extend a selection of cells |
Shift + Arrow keys | Extend a selection of cells |
Ctrl + Arrow keys | Jump to the end of data |
Ctrl + Shift + Arrow keys | Select to the end of data |
Table 3: Microsoft PowerPoint | |
Shortcut | Action |
|---|---|
Ctrl + B | Bold selected characters |
Ctrl + I | Italicize selected characters |
Ctrl + U | Underline selected characters |
Ctrl + Spacebar | Clear formatting of selected text |
Ctrl + C | Copy selected text or objects |
Ctrl + X | Cut selected text or objects |
Ctrl + V | Paste selected text or objects from the clipboard |
Ctrl + Z | Undo the last action |
Ctrl + K | Display the Insert Hyperlink dialog box |
Ctrl + O | Display the Open tab in Backstage View |
Ctrl + P | Display the Print tab in Backstage View |
Ctrl + S | Save a presentation |
Ctrl + F1 | Expand/collapse the ribbon |
F5 | Start a slide show from the beginning |
Tab | Insert a tab character |
Backspace | Delete one character to the left |
Delete | Delete one character to the right |
Shift + Right Arrow | Extend a selection one character to the right |
Shift + Left Arrow | Extend a selection one character to the left |
Shift + End | Extend a selection to the end of a line |
Shift + Home | Extend a selection to the beginning of a line |
Shift + Down Arrow | Extend a selection one line down |
Shift + Up Arrow | Extend a selection one line up |
Ctrl + A (Slides) | Extend a selection to all slides |
Ctrl + A (Text) | Extend a selection to the entire text within a text box |
Tab (Tables) | Move cursor to the next table cell |
Shift + Tab (Tables) | Move cursor to the previous table cell |
Shift + Arrow Keys (Tables) | Extend a selection of table cells |
Left Arrow | Move cursor one character to the left |
Right Arrow | Move cursor one character to the right |
Up Arrow | Move cursor up one line |
Down Arrow | Move cursor down one line |
End | Move cursor to the end of a line |
Home | Move cursor to the beginning of a line |
Ctrl + E | Center a paragraph |
Ctrl + R | Right-align a paragraph |
Ctrl + L | Left-align a paragraph |
Ctrl + J | Justify a paragraph |
F7 | Begin the spell checker |
Shift + F7 | Open the Thesaurus pane |
Shift + Click | Expand selection of objects to the clicked object and all objects in between |
Ctrl + Click | Expand selection of objects to the clicked object |
Enter (with object selected) | Select text within an object |
Esc (with text inside object selected) | Select the object |
Table 4: Microsoft Access | |
Shortcut | Action |
|---|---|
Ctrl + S | Save a database object |
Ctrl + O | Display the Open tab in Backstage View |
F2 | Rename a selected object in the Navigation pane |
Enter | Open the selected database object |
Tab | Move to the next field |
Shift + Tab | Move to the previous field |
Ctrl + F1 | Expand/collapse the ribbon |
Backspace | Delete the character to the left of the insertion point |
Delete | Delete the character to the right of the insertion point |
F11 | Toggle the Navigation pane |
0.8 Tips for chromebooks
F-Keys on a Chromebook
Some Office features need the F-keys (the keys at the top of your keyboard). To make them work on a Chromebook:
Click the Settings icon in the bottom-right corner.
Select Settings to open a new window.
Scroll down to Device and click Keyboard Settings.
Check the box next to Treat Top-Row Keys as Function Keys.
Click OK. This will make your Chromebook’s top-row keys work like F-keys.
Delete Key
Chromebooks don’t have a Delete key. But you can do the same thing by holding the Alt key and pressing Backspace. This will delete the character to the right of the cursor, just like on a Windows computer.
Quotation Marks Issue
If you have trouble with quotation marks (they show as two dots), it might be because your keyboard is set to International mode. Here’s how to fix it:
Click the bottom-right corner of the screen (where you see battery and clock info).
Click the down arrow next to Keyboard.
Change it to US.
How to fix Slow Labs on a Chromebook
If your labs are slow or unresponsive, try these steps:
Restart your Chromebook and close unnecessary programs and tabs to save power.
Disable browser extensions that aren’t needed while using Lab Sim.
Keep your Chromebook plugged in to avoid slower performance on battery.
If you can, do the labs on another computer that meets the recommended system requirements.
Note: for exams with multiple labs, it might help to use a different computer. If the labs freeze during an exam, contact support for help.
1.3.1 Digital communication
We need to communicate with others daily, and the global market makes our communication circle even larger. Digital communication, like email, allows us to send and receive messages almost instantly, replacing traditional mail.
Email Systems:
Web mail are accessed through a web browser like, Gmail, Yahoo Mail
Email clients software applications like Microsoft Outlook.
Types of Digital Communication
Email: apps like Gmail and Outlook
Instant Messaging: Quick, real-time chat.
Forums: Online discussion boards where people post and respond.
Texting (SMS): Short messages via phone service.
Video Calling: Apps (Skype, FaceTime) allow free video calls over the internet.
1.3.4 Digital privacy
Digital privacy is data travels through networks and is processed by various companies and software.
Privacy in Social Media, Email, Instant Messaging, and File Sharing
These services let users control who sees their information like posts, pictures, contact details.
When signing up for these services, you agree to their terms, which often involve data collection for profit.
Companies collect metadata (data about your activity), like your location, language, device, and what sites you visit.
This data is used for marketing, advertising, or even sold to other companies.
Privacy at Work
Employees may assume their work Internet access is unrestricted, but companies usually own the computers and networks.
Most companies have an acceptable use policy, which limits personal use of work computers and bans inappropriate activities (e.g., adult content).
Communications on company devices (including personal emails) might be monitored and stored, so employees should be cautious.
1.3.6 Gmail & Google calendar
Google Tools and Services
Google is a widely used company that has several tools
Docs: A tool for creating and editing documents (like Word).
Sheets: A tool for creating and working with spreadsheets (like Excel).
Slides: A tool for making presentations (like PowerPoint).
Google Drive: A cloud storage service where you can save and share files online.
Gmail: Google’s email service for sending and receiving messages.
Google Calendar: A tool for organizing and scheduling your events and task
Gmail Example
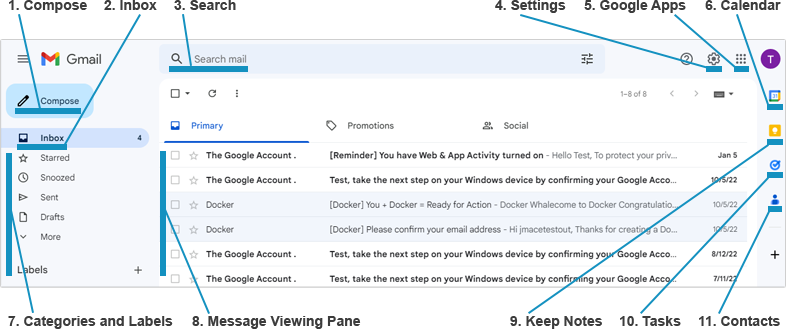
Table 1: Gmail Features | |
Feature | Description |
|---|---|
1. Compose | Select Compose to create and send a new message. The New Message window lets you attach files and insert links, emojis, and images. You can also apply formatting to text and paragraphs. |
2. Inbox | The Inbox is the default location for all messages. It is technically a system label that is always displayed in the left menu. |
3. Search | By default, the Search feature searches all of your email messages for the text you enter in the box. For advanced search options, click the bars icon at the far right of the search box. The Search feature also gives you the option of searching the web for the terms you enter into the box. |
4. Settings | The Settings option lets you modify the Gmail theme and background. You can also configure your Inbox tabs and modify the display density. Click See all settings for more advanced options, such as sending automated vacation reply messages, adding new mail accounts, blocking particular email addresses, and forwarding your mail to another address. |
5. Google Apps | This option lets you launch a new browser tab for a number of additional Google apps, such as Docs, Drive, or Calendar. |
6. Calendar | This option gives you convenient access to the Google Calendar app, for scheduling personal events or emailing meeting invitations to other users. |
7. Categories and Labels | Gmail includes a number of default categories and labels that you can use to organize and filter your messages. Select the More option to view, manage, and create additional labels. |
8. Message Viewing Pane | The message viewing pane can be filtered to show particular categories of messages. It can also be displayed in a denser format through the Settings option. |
9. Keep Notes | The Keep app provides a convenient way of recording notes that are stored in your account and made available from any device. |
10. Tasks | The Tasks app lets you create to-do lists with completion dates, subtasks, categories, and other details. |
11. Contacts | The Contacts app is a contact management service that lets you create contacts or group contacts. It is available as part of the sidebar of Gmail workspace, or as an Android mobile app or a web app. |
Google Calendar
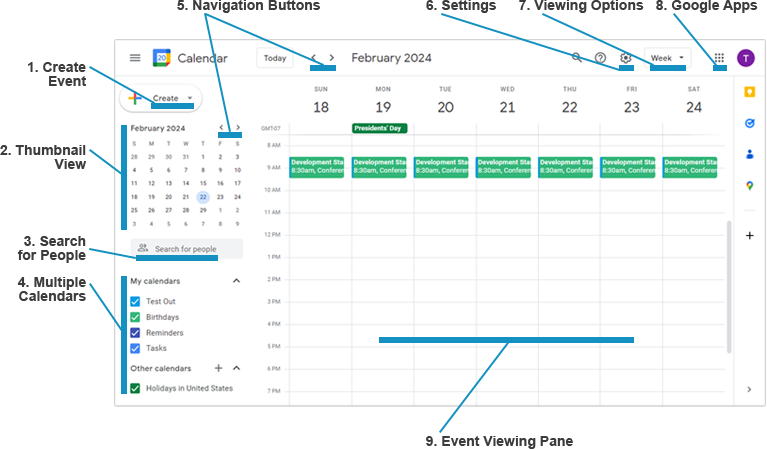
Table 2: Google Calendar Features | |
Feature | Description |
|---|---|
1. Create Event | Select this option to add a new event to the calendar. Events can be created as recurring appointments with notifications. You can also email invitations to other users and display the meeting time in a different time zone. |
2. Thumbnail View | The thumbnail view shows the entire month at a glance. It also lets you navigate quickly to a particular day, week, or month. |
3. Search for People | The Search for people option allows you to locate other users and view their calendar and events. Enter the name of the person whose calendar you would like to access. If their calendar is shared with you, you will see the information. If not, you can request that they share it with you. |
4. Multiple Calendars | Google Calendar supports multiple calendars for different purposes. When multiple calendars are selected at the same time, the calendar events are all integrated into the same view. |
5. Navigation Buttons | Depending on the calendar view option you've chosen, the navigation buttons let you move back and forth between days, weeks, or months of the year. |
6. Settings | The Settings option lets you modify the calendar color and density. Select Settings from the dropdown menu for more advanced options, such as changing the time format, adding a secondary time zone, and automatically adding events from Gmail messages to your calendar. |
7. Viewing Options | You can view calendar events a week at a time, as shown here, or you can view a single day, a month, or an entire year. Other viewing options include a list of upcoming events and a 4-day view. |
8. Google Apps | This option lets you launch a new browser tab for a number of additional Google apps, such as Docs, Contacts, Drive, and Gmail. |
9. Event Viewing Pane | Calendar events can be displayed in a number of different formats. |
1.3.7 Microsoft outlook basics
Email:
Send, receive, and store emails.
Customize messages with formatting and signatures.
Set automatic replies (e.g., when on vacation).
Calendar:
Track appointments and deadlines.
Schedule meetings with coworkers.
Contacts:
Keep track of people's information (emails, phone numbers, etc.).
Group contacts for easy collaboration.
Tasks and Notes:
Create to-do lists and assign tasks to yourself or others.
Use the Notes feature to jot down important information
1.4 online safety & security
Section overview
Configure Windows Firewall for different networks.
Evaluate email messages to determine if they represent a possible social engineering attack.
Safely spend money on the internet.
Explain why it's important to back up data.
Describe the basics of data encryption.
Describe the importance of having a secure password.
Define different kinds of malware and know how to avoid them.
Clear a browser's cache.
Configure browser privacy and security features such as pop-up blockers, location tracking, and cookies.
1.4.1 computer security risk
Computer Security: It’s about protecting important information on computers from cyber criminals.
Personal Information: Cyber criminals steal details like IDs, birth dates, addresses, emails, phone numbers, credit card info, and account logins.
Protecting Information: Protecting this data is getting harder as criminals are using more advanced methods.
Security Measures: Common ways to protect information include firewalls, anti-malware software, and anti-spam software.
Firewalls:
Firewalls control what network traffic is allowed to enter or leave a computer.
Network firewalls protect an entire network (installed at the network's border).
Host firewalls protect individual computers (usually pre-installed).
Anti-Malware: Software that prevents viruses, worms, Trojans, spyware, and adware from infecting your computer.
Windows Defender: Windows includes built-in anti-malware called Microsoft Defender, but third-party options are also available.
Anti-Spam: Spam is unwanted emails that can include viruses or phishing attempts. Anti-malware software can block it, but you may need additional software if it doesn't.
Disposing of Old Devices:
When getting rid of old computers or storage devices, use software to completely wipe data from the hard drive, as simply deleting files isn’t enough.
For extra security, consider physically destroying the hard drive.
1.4.2
Computer security is about keeping important information safe. Computers are targets for cybercriminals who go after:
Personal info like IDs, birthdates, addresses, emails, and phone numbers
Financial details like credit card and bank numbers
Login info for websites or online banking
Computer Security Measures | |
Security Measure | Description |
|---|---|
Firewall | Firewalls control the flow of network traffic and protect systems from unauthorized network connections. They are configured with a set of rules that define what kind of traffic is allowed and what kind is not allowed. For example, if a malicious user on the internet tries to establish a connection with your computer, the firewall identifies it as a violation and blocks the connection. There are two general types of firewalls.
Typically, most networks will use both types of firewalls. Network firewalls must be purchased separately and installed manually. However, host-based firewalls are usually installed and enabled by default on most modern operating systems. |
Anti-Malware Software | Anti-malware software should be installed on computer systems to detect and prevent malware infections. The following are some of the many types of malicious software, or malware:
There are countless anti-malware packages that can be used on Windows systems, including the following:
|
Anti-Spam Software | Spam is unwanted, unsolicited email that is sent to your email account. Some spam is merely annoying and doesn't present a security risk to your computer. However, spam often carries viruses, advertisements for questionable products, and phishing attacks. Some anti-malware software can also block spam for you, but others cannot. If your package does not, you should consider installing additional anti-spam software or switching to an anti-malware package that is capable of blocking spam. |
Data Destruction | There are security issues to be aware of when you get rid of old computers and storage devices. You need to dispose of devices in a manner that prevents sensitive data from being exposed. For example, if you're selling a computer, you need to remove all data from the hard disk drive. However, just deleting the files is insufficient. The data actually remains on the drive and can be easily reconstructed by someone with the right tools. To prevent this, consider the following options:
|
1.4.4 Malware protection on windows
Anti-Malware Software: It’s important to have anti-malware software to detect harmful files before they infect your system.
Microsoft Defender Antivirus:
Installed by default on Windows systems.
Monitors your system for malware unless you install other software.
To check its settings, go to the Windows Security app and look for the security shield icon.
Security Status Icons:
Green Checkmark: Everything’s fine, no issues found.
Yellow Exclamation: Something needs attention, like outdated updates.
Red X: Immediate action needed, such as a virus found.
Real-Time Protection vs. Scanning Files:
Scanning: Finds malware during scheduled scans but only after infection.
Real-Time Protection: Continuously checks for malware, preventing it before it can infect your system. Microsoft Defender has this feature always running.
Scan Options:
Quick Scan: Checks common areas for infections.
Full Scan: Checks all files and programs (may take a long time).
Custom Scan: Lets you choose areas to scan.
Offline Scan: Scans your system during reboot, useful for tough-to-remove malware like rootkits.
Updating Malware Definitions:
Keep the security updates up-to-date to protect against new threats. You can check updates manually.
Protection History:
If malware is found, it’s quarantined. You can review and remove it from the system by checking the protection history.
Note: Microsoft Defender Antivirus is the default anti-malware for Windows, but make sure to keep it updated and run regular scans to stay safe.
1.4.5 windows security
Windows Security Overview:
Windows Security helps protect your computer from malware and attackers.
Windows 11 and newer versions of Windows 10 have the Windows Security app to make managing security easier.
How to Access Windows Security:
Click the Windows Security shield icon in the taskbar (or find it in Show hidden icons).
Or, go to the Start menu and search for Windows Security.
Windows Security Options:
Virus & Threat Protection: View and set up antivirus software.
Account Protection: Manage sign-in options and account security.
Firewall & Network Protection: Configure firewall settings to protect your system.
Family Options: Set up safety measures for family members.
App & Browser Control: Protects against malware and malicious websites while browsing.
Protection History: Review recent antivirus actions and quarantined files.
Device Security: Manage built-in security features, like secure boot and TPM.
Device Performance & Health: Check system health (e.g., battery, storage, apps).
Key Areas to Know:
Virus & Threat Protection
Firewall & Network Protection
Virus & Threat Protection:
Microsoft Defender Antivirus comes pre-installed on Windows 10 and 11.
You can also use third-party anti-malware software.
Anti-malware should:
Have real-time protection (block threats instantly).
Scan regularly for any missed malware.
If malware is found, it’s quarantined. You can review and delete or restore quarantined items.
Firewall & Network Protection:
Microsoft Defender Firewall is installed by default and helps block unwanted network traffic.
It automatically starts with your computer and allows safe network activities (like browsing).
Network Location Awareness adjusts firewall settings based on your connection type (Private, Guest/Public, Domain).
Managing the Firewall:
To turn the firewall on/off:
Open Firewall & Network Protection in Windows Security.
Select the network type (Private, Public, or Domain) and toggle the firewall.
You can allow or block specific apps:
Go to Firewall & Network Protection and choose Allow an app through firewall.
Change settings and select which apps can access the network.
You can add new apps by selecting Allow another app, browsing for the app’s file, and adjusting network permissions.
1.4.7 internet safety & security
The Internet and Its Risks:
The Internet is a great resource but isn’t well-regulated.
Information online can be accurate, inaccurate, safe, or harmful.
Social Engineering Attacks:
Social engineering tricks people into revealing sensitive information.
Attacks can happen in person, by phone, through browsers, or email.
These attacks are often easier and more successful than technical ones.
Types of Social Engineering:
Reconnaissance: Gathering info about a person to later exploit them.
Shoulder surfing: Watching someone’s screen or keyboard.
Eavesdropping: Listening to private conversations.
Dumpster diving: Searching trash for sensitive documents.
Pretexting: Tricking someone into giving info under false pretenses.
Intimidation: Trying to scare someone into giving info.
Familiarity: Pretending to be a friend to get information.
Social validation: Using peer pressure to get someone to act.
Email Attacks:
Phishing: Fake emails pretending to be from trusted organizations, trying to get you to click on a harmful link.
Spear phishing: Phishing that targets individuals based on gathered info.
Nigerian scams: Emails asking for small money with the promise of bigger returns.
Email hoaxes: Fake emails tricking you into deleting important files or downloading malware.
Browser Attacks:
Pharming: Redirecting you to fake websites to steal your information.
Rogue anti-virus: Pop-up messages claiming your computer is infected to trick you into downloading malware or paying for fake software.
How to Stay Safe:
User awareness is the best defense, as tech measures are only partly effective.
Preventing Reconnaissance:
Shoulder surfing: Arrange your screen to avoid prying eyes and use screen filters.
Eavesdropping: Be cautious when sharing sensitive info in public.
Dumpster diving: Shred important documents before throwing them away.
Preventing Pretexting:
Ignore and report any suspicious requests. If someone tries to intimidate you, hang up or delete the email.
Email Attacks:
Detecting phishing:
Check the sender’s email address.
Watch out for urgency in the message.
Hover over links to check where they go.
Be cautious when clicking on links in emails and always double-check the sender’s details.
Browser-Based Attacks:
Defend against pharming:
Keep anti-malware updated.
Double-check website URLs for accuracy and security (look for "https" and the lock icon).
Defend against rogue anti-virus:
Enable pop-up blocking.
Ignore any pop-ups claiming your system is infected.
1.4.9 e-commerce safeguards
E-commerce
e-commerce is buying and selling products or services online.It includes Business to Consumer (B2C), like Amazon, and Consumer to Consumer (C2C), like eBay or Craigslist. Many businesses, such as Walmart and Amazon, sell products online. You can buy physical items or digital products, like music and videos.
How Does Ecommerce Work?
Online retailers use shopping carts to track customer orders.
A cookie is stored on your computer to remember your orders.
On mobile, apps use other methods to keep track of orders.
Online Security Issues:
The biggest concern is how payments are processed and if your financial data is secure.
Payment services like PayPal, Venmo, and Apple Pay have strong security measures.
Online Safety Tips:
Be cautious with what you share online: Only share personal info with trusted businesses.
Avoid public WiFi or public computers: They may have spyware, so use a secure home computer with updated software.
Use strong passwords: Prefer credit cards over debit cards for better fraud protection.
Look for HTTPS in web addresses: This means your payment data is encrypted and secure.
Trust only known businesses: Investigate websites before shopping, check reviews, and look for their social media presence.
Be cautious of deals that seem too good to be true: They’re often scams.
Note: E-commerce can be as safe as shopping in a store if you follow precautions: Be careful with what you share. Never shop over public WiFi. Use strong passwords. Verify secure transactions. Make sure websites are legitimate.
Table 1: Ecommerce Safeguards | |
Safeguard | Description |
|---|---|
Be Careful What You Share | Only share personal information when it's required and requested by a legitimate business that you trust. Avoid saving credit card numbers and other financial information in your online account. If you use a mobile device for ecommerce, only share your device with people you would feel comfortable sharing your wallet with. |
Don't Use Public WiFi | Never conduct ecommerce transactions using public WiFi or public computers that might have spyware installed. Ideally, you should do your online shopping on your home computer, behind a firewall with an up-to-date operating system and antivirus software installed. |
Use Passwords and Credit Cards | For online accounts, create strong passwords and use a credit card instead of a debit card whenever possible. Credit cards include better protection against online fraud. Always pay your credit card off in full every billing cycle to avoid their high interest rates. |
Use HTTP Secure | Verify that the online retailer is conducting secure transactions using HTTPS rather than simply HTTP. This ensures that your financial data will be encrypted and less likely to be stolen by a hacker. |
Shop with Legitimate Businesses | Conduct ecommerce transactions with people and businesses you trust. Investigate all online shopping websites and apps to make sure they're legitimate. Scammers keep themselves busy creating fake storefronts for unsuspecting customers. Examine URLs closely to make sure they don't include slight variations or misspellings of legitimate sites. If you're unfamiliar with an online shopping retailer, see if they have a social media presence and check out product reviews. When using peer-to-peer payment services such as Venmo, limit your transactions to people you know and trust. |
Be Suspicious | Be extremely suspicious about deals that seem too good to be true. More often than not, these deals are online scams. |
1.4.11 Encryption and Authentication
Encryption
Encryption is a way to protect your data. It scrambles the data so even if someone intercepts it, they can't read it.
Caesar cipher was one of the earliest forms of encryption, where letters were substituted by others (e.g., A → D, B → E).
Modern encryption works similarly: it turns plain text into unreadable data using a key. Only those with the key can decrypt it.
How to tell if a site is encrypted:
Look for https in the URL (the "s" stands for secure).
If the URL is just http, avoid entering private information as it’s not encrypted.
Authentication
Authentication is about proving your identity to a computer.
Common methods include fingerprint scanning, facial recognition, smart cards, and passwords.
Good password habits are essential:
Keep your password secret. Never share it over email or phone, even if someone asks.
Create a strong password: at least 16 characters, combining letters, numbers, and symbols. Avoid easily guessable ones like birthdays or family names.
Use a unique password for each account. Using the same password everywhere makes you more vulnerable.
Only enter passwords on encrypted websites (those with https) to prevent them from being intercepted.
Encryption and authentication are vital ways of keeping information safe for example:
Table 1: Terminology | |
Term | Description |
|---|---|
Encryption | Whenever you send information from one computer to another, there is an opportunity for a third party to intercept the signal. This is a major concern because private information could be used to steal a person's identity, money, or worse. Encryption algorithms scramble data to make it unreadable to anyone who doesn't have the correct key to unscramble it. Even if a criminal intercepts an encrypted signal, they won't be able to understand the information. |
WiFi Encryption | Wireless network routers often support different encryption protocol standards. For the highest level of WiFi security, use WiFi Protected Access 2 (WPA2) with AES encryption. WPA2 has replaced WPA and Wired Equivalent Privacy (WEP). Do not use the WEP standard, which is vulnerable to even the most novice hackers. In addition to using the latest wireless encryption method, be sure to use a strong network password and ensure that your wireless router has the latest firmware updates installed. |
HTTPS | Information is transferred on the World Wide Web using the HTTP protocol. However, HTTP transfers data as plain text with no encryption. To add encryption, websites use a protocol called TLS. When combined, HTTP and TLS make HTTPS, which both transmits and encrypts data. You should never enter your password or any other sensitive information into a website that uses HTTP instead of HTTPS. |
Authentication | Authentication is when a computer requires someone to prove they are who they say they are. Usernames and passwords are the most common method of authentication, but there are many others, including key cards, fobs, fingerprint readers, and retinal scans. Because your passwords are the key to accessing your personal information, cybercriminals will do whatever they can to obtain them. For this reason, it's important to develop good password habits. A good password should have at least twelve or more characters and include a combination of letters, numbers, and symbols. Never write your passwords down, and only share them with a person you trust completely, such as a parent or spouse. Finally, do not use the same password for multiple accounts. This will prevent access to additional services should one of them be compromised. |