2.1 - CompTIA A+ Core 2
2.1a - Physical Security: Professor Messer
Physical security
Bollards
Bollards/barricades: Used to limit access by vehicles to a particular area - used to channel pedestrian traffic to a location; avoids injuries/safety concerns.
Access control vestibule
Access control vestibule: Space that serves as an entryway or transitional area - used to limit access to secured areas, and typically includes a biometric scanner or badge reader.
Badge reader

Badge reader: A device that allows authorized users to gain access by scanning an identification badge, usually equipped with magnetic stripes, barcodes, or RFID/NFC technology. Also used for time clocks.
Video surveillance

Video surveillance: Refers to CCTV (closed-circuit television) - allows you to see activity occurring in a specific room/area without being physically present. Camera features are important here - object detection is needed to identify license plates/human faces.
Networked together and have recorded footage over time.
Alarm systems

Alarm systems: Device/set of devices designed to alert to a specific event that requires attention (e.g., a security/perimeter breach).
Circuit-based alarm system: Designed to ring when a circuit is opened or closed. Placed on doors, windows, or fences, and useful on the perimeter of a secured area.
Duress alarm: A specialized alarm system that is triggered by a user in distress, typically requiring only a discreet action or button press, often used in situations such as bank tellers or emergency service personnel to signal for immediate assistance.
Motion sensors
Motion detection alarm system/motion sensors: Designed to ring/alarm when motion is detected in front of the camera. Even if there is no camera footage, it sends a notification that motion is detected in the sensitive area.
Door locks
Door lock: A security device that ensures a door stays in a closed/locked position.
Conventional door lock: A door lock that uses a traditional lock and key to open.
Deadbolt: A door lock that uses a thumb turn/second key mechanism to provide enhanced security and prevent unauthorized access.
Electronic door lock: A door lock that uses a keyless/PIN mechanism to open.
Token-based lock: A door lock that uses a physical token to open (e.g., RFID badge, magnetic swipe, key fob).
Biometric lock: Locks that use biometric/physical features to provide access (e.g., fingerprints, retina/facial scans).
Equipment locks

Equipment locks: Used to ensure sensitive hardware (e.g., servers), can only be managed by authorized personnel.
Server racks are installed side-by-side, in enclosed cabinets with ventilation (perforations in the cabinets). Accessing the servers requires the use of keys.
Security guards
Security guards: Personnel responsible for the physical protection of a facility/reception area. Also provides identification of existing employees/guest access.
ID badge: A card or credential issued to employees that allows access to secured areas and systems within the facility. Contains the person’s name, picture, and other details - must be worn at all times.
Access list: Physical list of names/credentials that can enter a secured building - enforced by a security guard.
Provides a visitor log/audit trail - prevents unauthorized/unaccounted movement of individuals in a building.
Fences
Fences: Barrier/upright structure enclosing an area - used to mark a boundary or control access. Designed to be robust and high (difficult to climb over). In some cases, razor wire may be applied on top of the fence.
2.1b - Physical Access Security: Professor Messer
Physical access security
Key fobs

Key fobs: Small devices used to grant access to secured areas, typically added to a physical keychain. These devices often use RFID technology to communicate with card readers, allowing users to unlock doors or access systems without a traditional key.
Smart cards

Smart cards: Plastic cards that contain embedded digital circuits - provide authentication based on signed digital certificates. Typically used with other forms of identification (PIN, biometrics).
Can use an integrated card reader (built into a laptop), or a USB-connected external reader.
Mobile digital key
Mobile digital key: Replaces digital keys with your phone - typically used for automobile unlocking/starting, hotel or office door locks, or home doors. Provides better authentication than a physical key - you must (1) have phone access, and (2) be able to unlock the phone for authentication.
Keys

Keys: Shaped metal with incisions designed to insert into a lock to open or close it. Used to secure areas that should not be locked electronically for power loss risks (e.g., safes).
Often use a key cabinet to provide formal check in/check out - some organizations take your license/identification while you hold the key, and return your ID when you return the key - allows for auditing.
Biometrics
Biometrics: Authentication using a unique physical/biological component. These authentication types typically store a mathematical representation of your biometric - the actual biometric (e.g., your fingerprint, retina), isn’t normally saved.
Retina scanner: A device that reads and analyzes the unique capillary (blood vessel) patterns in the retina, helping to verify the identity of an individual accurately and securely.
Fingerprint scanner: A device that analyzes the ridge patterns of fingerprints to provide authentication.
Palm print scanner: A device that scans the shape of a person’s hand and fingers to provide authentication.
Facial recognition technology (FRT): Technology that creates a digital “key” from facial features and uses that to provide authentication. Relatively secure method - 1/1,000,000 false positive rate.
Voice recognition technology: Technology that uses an individual’s voice to provide authentication - the system is typically “trained” by speaking phrases, then the results are evaluated and stored to create a biometric pattern of the user’s voice (i.e., mannerisms, pace, accents). Questionable security - best to combine with other factors, and doesn’t work if the user is unable to speak or your voice changes (e.g., if you’re sick).
Lighting
Lighting: Adequate lighting conditions ensure that the camera can capture clear images, reducing the risk of false negatives or positives. Also serves as a psychological deterrent for attackers.
Magnetometers

Magnetometers: Devices used to measure magnetic fields, aiding in detecting metal objects and ensuring the security of sensitive areas. Not useful for non-metallic objects (e.g., weapons made of ceramic or plastic).
2.1c - Logical Security: Professor Messer
Logical security
Logical security: Encompasses the safeguards put in place to protect digital data and resources from unauthorized access and exploitation.
Principle of least privilege
Principle of least privilege: Security concept that states rights and permissions should be set to the bare minimum - users should only get exactly what they need to complete their objectives/job.
Idea behind the principle of least privilege: Prevents attackers/malware from gaining complete access to all devices on a network if full admin permissions were granted to all devices.
Zero Trust model
Zero Trust model: A security model that dictates that no entity, whether inside or outside the network, should be trusted by default, and every access request must be verified (e.g., by MFA, data encryption/PKI, permissions) to ensure that only authenticated and authorized users can access sensitive resources.
Access control lists (ACLs)

Access Control Lists (ACLs): A technology used to allow/deny traffic on a network point - commonly used on the ingress/egress of a router interface. Filter traffic by Source/Destination IP, TCP/UDP ports, and network protocols (inc. ICMP). Allows/denies packets based on predefined filters.
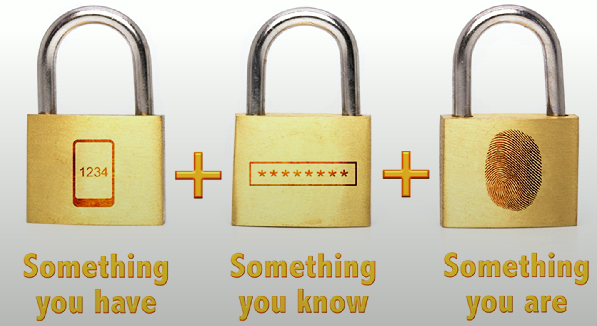
Multifactor authentication (MFA)
Multifactor authentication (MFA): Use of two or more methods to prove your identity and log into an application/service.
Email: MFA method used to associate a person with a particular email address, often requiring verification through a one-time code sent to the email before access is granted.
Hardware token: A physical device that generates a one-time code for user authentication, ensuring that only the individual with the hardware token can access the application or service. Typically attached to a keychain for easy access.
Authenticator application: Application that provides a pseudo-random number token to log into an app/service.
Short Message Service (SMS): Use of a stored phone number to send a login factor via a text message, allowing users to receive a one-time code that must be entered for authentication.
Has significant security problems - the phone number can be reassigned to a different phone, SMS messages can be intercepted by attackers, and SMS spoofing
SMS spoofing: Changing a SMS sender ID to match a trusted organization.
Voice call: Provision of a security token via a phone call - the user receives a numeric code given from a phone call and enters it to provide authentication. Similar disadvantages to SMS - phone calls can be intercepted or forwarded, and a phone number could be switched to another phone.
Time-based one-time password (TOTP): A temporary numeric code generated based on the current time and a shared secret key, providing an additional layer of security for two-factor authentication. Timestamps normally change in 30-second or 60-second intervals. One of the more common OTP methods.
One-time password/passcode (OTP): One-time authentication code - can only be used once per session/authentication attempt.
2.1d - Authentication and Access: Professor Messer
Security Assertions Markup Language (SAML)
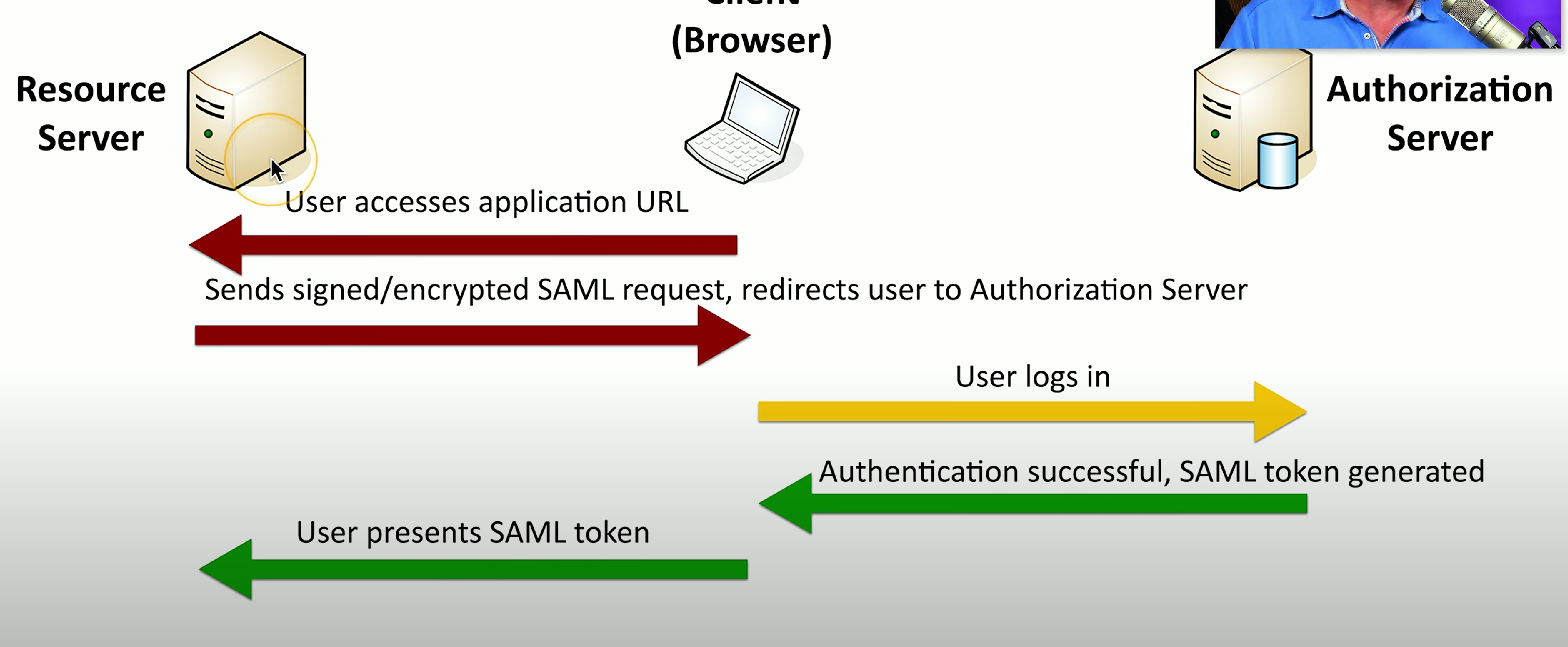
Security Assertions Markup Language (SAML): An open standard for authentication/authorization used by many third-party applications. Not applicable for mobile devices.
SAML process: (1) Client device/browser accesses an application URL from the SAML resource server, (2) SAML resource server sends a signed/encrypted SAML request and redirects the client to the SAML authorization server, (3) Client device logs in, (4) SAML authorization server generates a SAML token and sends it to the client device, (5) Client device presents SAML token to the SAML resource server.
Single sign-on (SSO)
Single-sign-on: A user authentication process that allows a user to access multiple applications with one set of login credentials, streamlining the user experience while enhancing security by reducing the number of passwords needed.
Just-in-time access
Just-in-time access: Granting administrator/root privileges to IT support accounts for a limited time to avoid security risks associated with long-term access.
Process: IT support must request admin/root access from a central clearinghouse that grants/denies access based on predefined security policies. The just-in-time process creates a time-limited account with temporary root credentials.
Privileged access management (PAM): Security approach for managing root/privileged account access - stores privileged account credentials in a digital vault, and these temporary account credentials are released from the vault by request.
Mobile device management (MDM)
Mobile device management (MDM): Centralized management/administration of company-owned and user-owned devices.
MDM policies can define applications that can run on the device or access to corporate data - they can enforce security configurations on the entire device or a corporate data partition.
Bring-your-own-device (BYOD): MDM policy that allows individuals to bring their own personal devices for work use.
Data loss prevention (DLP)
Data loss prevention (DLP): Allows administration/management of sensitive personal data - dictates how the data is transferred to prevent leakage/unauthorized acquisition of sensitive data.
Identity access management (IAM)
Identity access management (IAM): A security framework that dictates authorized access and ensures the correct people/entities have access to the correct data at the correct times. Typically ensures:
Identification: Account creation for unique representation.
Authentication: Verification of claims (e.g., passwords, digital certificates).
Authorization: Assignment of rights and enforcement of access rules.
Accounting: Monitoring usage and alerting unauthorized access
Directory services

Directory services: Provides a database of everything on a network (computers, user accounts, file shares, printers) - primarily Windows-based and uses Active Directory for centralized authentication, authorization (access control), and tech support/provisioning.