ITN 101 Mod 08
Module Objectives
Explain the purposes of network segmentation
Describe how subnetting works
Calculate subnets
Configure VLANs
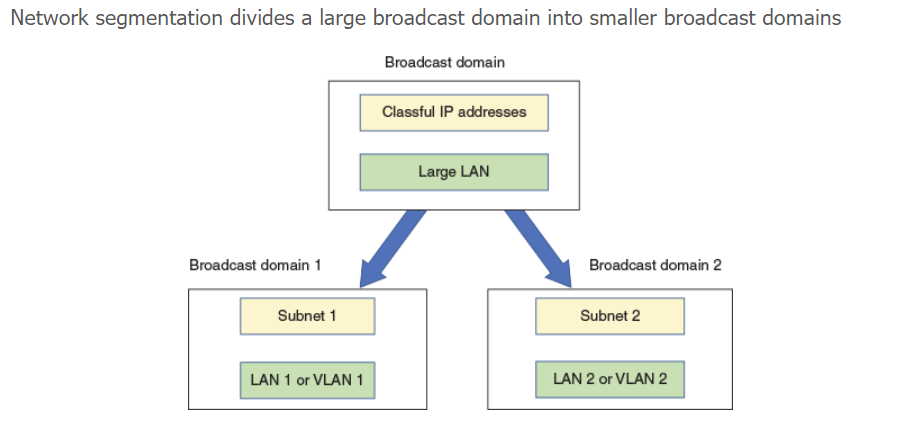
Network Segmentation
Overview
Definition: Dividing a computer network into smaller, manageable segments.
Benefits
Traffic Separation: Ensures that traffic from one segment doesn't interfere with another segment, enhancing overall network performance.
Broadcast Domains: Each segment has its own broadcast domain, which is crucial for limiting broadcast traffic.
Goals of Segmentation:
Enhance Security: By isolating sensitive data, organizations can minimize the risk of unauthorized access and data breaches.
Improve Performance: Reducing broadcast traffic leads to better network efficiency and speed.
Simplify Troubleshooting: Segmentation allows network administrators to isolate problems more quickly, leading to faster resolutions.
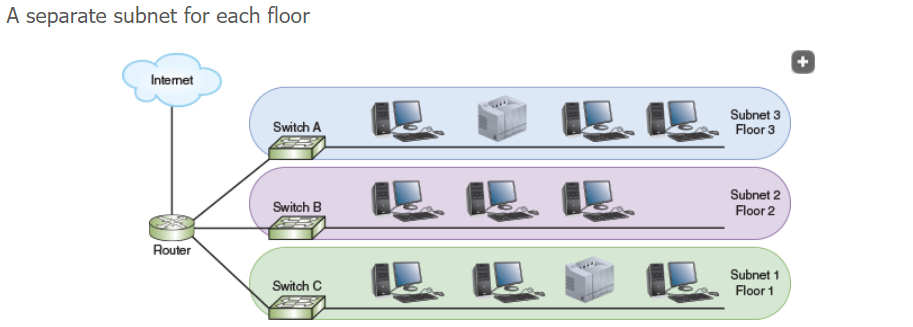
Common Groupings for Segmentation
By geographic location: For example, segments could be based on the floor of a building connected by a LAN or different buildings connected via a WAN.
By departmental boundaries: Examples may include segments created for departments like accounting, human resources, and sales, allowing for specialized resource allocation.
By device types: Devices can be grouped into segments based on their functions, such as printers, desktops, and IP phones to facilitate management.
Subnet Masks
Concept of Subnetting
Importance: Subnetting is essential for efficient network management, especially when the network grows from a small number of devices to hundreds.
Example Scenario: Transitioning from 20-30 computers to a few hundred necessitates careful planning and segmentation of local area networks (LANs).
Techniques
Subnetting: This involves dividing a pool of IP addresses into multiple groups, which improves organization and resource allocation.
Client Device Configuration: All client devices within each subnet must be configured properly to locate and communicate with other devices within their segment.
Example of a Subnet Mask
IP Address: 192.168.123.132
Binary: 11000000.10101000.01111011.10000100
Subnet Mask: 255.255.255.0
Binary: 11111111.11111111.11111111.00000000
Identifies:
Network ID: 192.168.123.0
Host Portion: 0.0.0.132
Calculating Subnets
Classless Addressing
Basis: Borrowing host bits for network information allows for the creation of additional network IDs while decreasing the possible identifiers for hosts.
Steps to Subnetting
Borrow bits from the host section of the IP address.
Determine new subnet mask through calculation.
Define network IDs based on the new subnet configuration.
Calculate the valid IP address ranges for hosts within each subnet.
Example: Subnetting the network ID 192.168.89.0 with an original subnet mask of 255.255.255.0.
IPv4 Subnet Calculation in Binary
Calculation Steps:
Borrow bits from host bits.
Neutralize existing subnet masks to redefine the structure.
Determine the new Network ID based on the new masks.
Identify valid host address ranges for efficient network design.
Implementing Subnets on a Network
DHCP and Subnets
A centralized DHCP server can efficiently manage IP assignments across different subnets by utilizing DHCP relay agents for effective communication and management.
VLSM (Variable Length Subnet Mask)
VLSM allows for further subdivision of existing subnets as network needs evolve. Each subnet can be customized based on specific requirements, starting with the largest subnet and progressively creating smaller ones per demand.
Subnets in IPv6
Simplicity Compared to IPv4: IPv6 simplifies network design by eliminating traditional addressing classes and not relying on standard subnet masks.
Scalability: It can accommodate an extensive number of addresses for each subnet without the constraints seen in IPv4 addressing.
Address Structure
Addressing is characterized as eight blocks of four hexadecimal digits, allowing for efficient determination of both network and interface IDs.
VLANs (Virtual Local Area Networks)
Functionality
VLANs play a crucial role in limiting traffic within smaller broadcast domains, which significantly impacts overall network efficiency and performance.
Configuration
Managed Switches: Used for segmenting network traffic into different VLANs based on port grouping strategies.
VLANs can prioritize specific types of traffic through user-defined policies to ensure quality of service (QoS).
VLAN Types
Default VLAN: Pre-configured to handle all ports within the switch.
Data VLAN: Primarily carries general data traffic for the network.
Voice VLAN: Exclusively dedicated to VoIP traffic to prioritize voice communications.
Private VLAN: Additional segmentation within the VLAN to restrict communication between devices within the same VLAN.
VLAN Security Risks
Common Errors: Incorrect VLAN assignments can inadvertently grant unauthorized access to sensitive areas of the network.
VLAN Hopping: This is an attack method where intruders bypass VLAN security to send traffic into unauthorized VLANs, posing significant security risks.
Troubleshooting VLANs
Common Issues
Incorrect VLAN assignments may disrupt connectivity among legitimate users.
VLAN isolation can prevent users from accessing necessary resources, leading to productivity loss.
Mitigation Strategies
Avoid reliance on default VLANs to enhance security.
Change native VLAN IDs to prevent predictable traffic patterns.
Carefully configure trunk lines to restrict VLAN access only to known VLANs.
Summary
Knowledge attained through this module includes understanding network segmentation, mastering the subnetting process, calculating subnets effectively, and configuring VLAN setups.
Benefits of Well-Chosen Subnets
Easier Network Documentation: Properly chosen subnets simplify the documentation processes for network management, making it systematic.
Easier Problem Resolution: Troubleshooting becomes more efficient as issues can be traced back directly to specific subnets.
Efficient Router Management: Routers can manage IP address spaces effectively, reducing configuration issues.
Enhanced Routing Efficiency: Larger networks benefit from increased efficiency in routing, especially when IP address spaces are closely related mathematically, fostering