CH 02 : Communication And Internet Technologies
Data Transmission
- Factors to be considered while transmitting data between devices:
- Direction of transmission
- Method of transmission
- Method of synchronisation
Simplex, Half Duplex And Full Duplex
- ==Simplex Data Transmission==: Transmission in one direction only, from sender to receiver.
- ==Half Duplex Data Transmission==: Transmission in both directions but not at the same time (Back and forth transmission).
- ==Full Duplex Data Transmission==: Bi-directional ^^simultaneous^^ transmission.
Serial And Parallel
- Serial Data Transmission: Transmitting data one bit at a time, using a single channel/wire.
- Slower Transmission than Parallel.
- No risk of data being out of sync (also called being Skewed).
- Suitable for long distance transmission.
Parallel Data Transmission: Several bits of data transmitted at a time, using several channels/wires.
- Faster transmission than Serial.
- Risk of data being Skewed.
- Suitable for shorter distances.
- Used in circuits and internal electronics of computers and devices.
- An internal clock ensures data is in sync.
Asynchronous And Synchronous
- ==Asynchronous Data Transmission==: Data sent in goups in an agreed bit pattern. Groups of bits are sent with two Control bits (start and stop), each at either end, for the receiver to know when one group begins and ends.
- ==Synchronous Data Transmission:== Data sent in a continuous stream accompanied by timing signals generated by an ^^internal clock.^^ The receiver counts how many bits (1s and 0s) were sent and then reassembles them into bytes of data.
Universal Serial Bus (USB)
- ^^An Asynchronous Serial data transmission method.^^
- A USB consists of:
- Two wires for earth and power.
- Two wires for data transmission.
- What happens when a device is plugged into a USB port?
- Computer detects the device due to small difference in voltage level.
- Appropriate Device Driver is loaded up, or if not available, user is prompted to install one.
- Benefits of USB:
- Automatic detection of devices by the computer.
- Connectors only fit one way, thus no risk of incorrect insertion.
- Industry standard and common.
- Several data transmission rates supported.
- New USB standards backward compatible with old ones.
- Drawbacks of USB:
- Maximum cable length is 5 metres.
- Transmission rate less than 500 Megabits per second.
- Older standards might not be supported in near future.
Error Checking Methods
- It is essential to check whether data has been corrupted or damaged during transmission.
Parity Checking
In every byte of data, a Parity bit is sent.
It is agreed between sender and receiver on whether to use even or odd parity system.
If Even Parity is being used, there will be an even ^^number of 1s^^ in this byte. And odd if Odd Parity is used.
If Even Parity is used, and the byte, including parity bit, does not have even number of 1s, then data is corrupted.
This method shows whether a byte is corrupted, but does not show which bit has been changed.
==Parity Blocks== are used to solve this problem.
Even Parity is used in this example.
As there is an odd number of 1s in column 5 and row 8, their intersection must be the incorrect bit, because changing it can fix both.
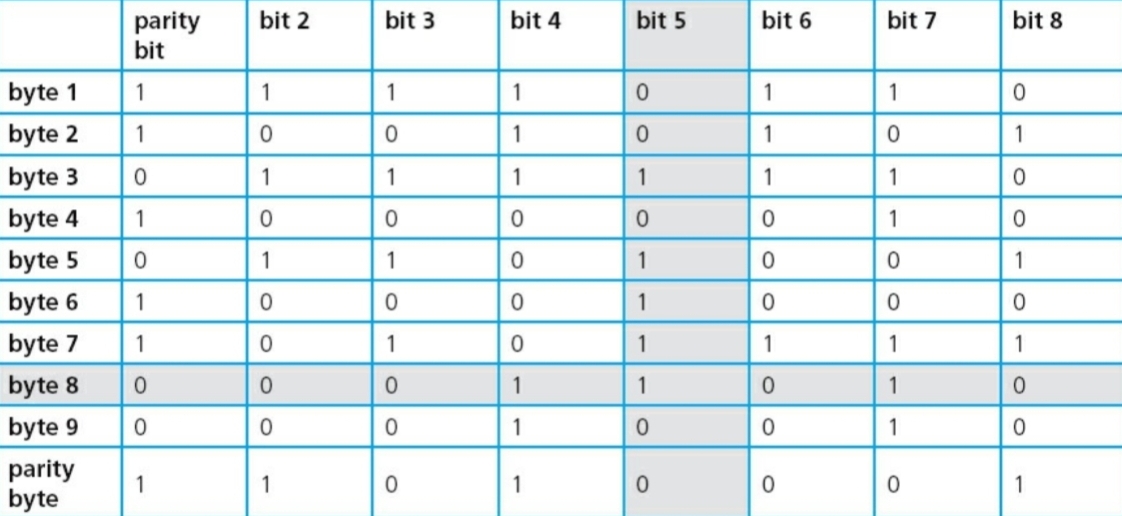
As apparent, though, if more than one bits are changed in a fashion that the number of 1s remains even in a byte, it will be impossible to locate error even by using a Parity block.
Automatic Repeat Request (ARQ)
- ==ARQ==: A message sent to the receiver requesting confirmation of correctly received data.
- ==Acknowledgement==: A message is sent by the receiver confirming that data has been received correctly.
- ==Timeout==: A time period which is allowed to elapse before an Acknowledgement is received.
- If an acknowledgement isn’t sent back to the sender before timeout occurs, then the ARQ is automatically resent.
Checksum
- It is an additional value ^^calculated^^ from the data being sent, and is sent with this data.
- The calculation is done through an ^^algorithm^^.
- On being received, the same calculation is performed by the receiver to obtain the checksum.
- If this value is not equal to the sent checksum, data has been corrupted.
Echocheck
- The data is sent ^^twice^^.
- Receiver compares the two sets to see whether the originally sent data is correct.
- However, through this method it is not possible to see whether the error (if any) occured in transmission during the first time data was sent or the second.
Internet Technologies
==Internet Service Provide==r: Companies which provide the user with ^^paid^^ access to the Internet.
==Internet Protocol (IP) Address:== A unique address given to each device on the Internet.
- It is assigned by the ISP for every Internet session.
- The IP address gives the ^^location^^ of a device on the internet, while a MAC address merely identifies the device.
- IP adresses change often, while MAC addresses do not.
==Hyper Text Markup Language (HTML)==: A markup language used in developing webpages.
- A mark-up language is used in the processing, definition and presentation of text.
- ==HTML Structure:== The meaning and structural mark up of the document.
- ==HTML Presentation==: The style and how the document will lookor sound (if includes multimedia).
- Structure and Presentation are kept separate while making an HTML document.
- Once finished, the author should have an HTML document (containing Structure), and a CSS (Cascading Style Sheet) File (to control Presentation).
==Hypertext Transfer Protocol (http):== A set of rules that must be obeyed while transferring files across the internet.
- It turns to “https” if some form of security is used online.
==Web Browser: A== software which allows a user to display a web page on their computer screen.
- Web browsers translate the HTML to display the web page.
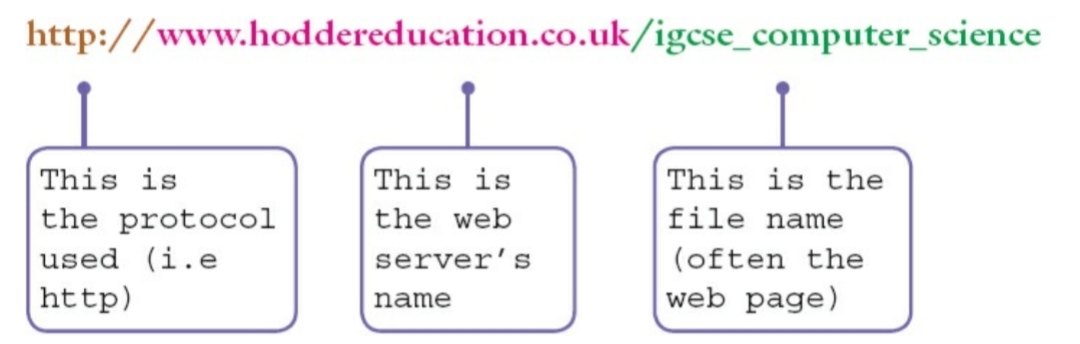
- Entering a ^^URL^^ like below in a browser gets you to a web page: