
Copy of IGCSE COMPUTER SCIENCE
IGCSE COMPUTER SCIENCE
Chapter 1 : Data representation
1.1 Number system:
Binary is a base 2 system that only contain 1s and 0s
In digital data storage, memory or communications, or processing the 0 and 1 value are called “low" and “high" or “On” and “Off"
Hexadecimal is easier for humans to understand than binary, as it is a shorter representation of the binary
How does a computer understand binary ? (3 marks)
A computer consists of millions of tiny switches, known as micro transistors, which must be “On” or “Off" positions.
Any form of data needs to be converted to binary to be processed by a computer
Data is processed using logic gates and stored in registers
What is a bit? (2 marks)
The term “ bit “ is short for “binary digit". A bit is a basic unit of information for all computing memory terms and either 1s or 0s
1 BYTE = 8 BITS
Decimal: Denary is a base 10 system
Hexadecimal :
Uses : error codes, MAC address, IPv6 address, HTML color codes
Understand how and why hexadecimal is used as a beneficial method of data representation:
Areas within computer science that hexadecimal is used should be identified
Hexadecimal is easier for humans to understand than binary, as it is a shorter representation of the binary
MAC Address:
Media Access Control address: unique number that identifies the device that is connected to the network or internet, usually made of 48 bits
MAC doesn't change when you change device’s location
It is a part of NIC (Network Interface Card)
IPv6 Address (IP address):
Unique identification number given to every device that is connected to the internet
Identify the unique location on which you are connected to the internet
Help to transfer data globally
While connecting to the internet, you are assigned to the IP address to use for your session, this issues by network or ISP
Confusion between IP and MAC :
IP : location of devices; MAC: actual devices at location of devices
Errors code:
Hex number refers to the memory location of the error => programmers fix the problems
HTML :
HyperText Mark-up Language: used when writing and developing pages, markup language , used for presentation of a page. Using tags <> to bracket a piece of text
Calculation of binary:
Addition of binary:
Logical shift : moving binary to the left or right
Each shift left is equivalent to multiply the binary numbers by 2
Each shift left is equivalent to divide the binary numbers by 2
Bits shifted from the end of the register are lost and zeros are shifted in at the opposite end of the register
Ex: Shift denary 21 to the left
Shift left is equivalent to multiply the binary numbers by 2 = 21 x 2 = 42(10)
128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 | |
|---|---|---|---|---|---|---|---|---|
21(10) | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 1 |
After shift to the left (42(10)) | 0 | 0 | 1 | 0 | 1 | 0 | 1 | 0 |
An overflow error will occur if the value is greater than 255 in an 8-bit register
A computer or a device has a predefined limit that it can represent or store, for example 16-bit
An overflow error occurs when a value outside this limit should be returned
Two compliment (Binary Numbers):
Find how -28 would be expressed in two's complement notation:
First we write out 28 in binary form: 000011100
Then we invert the digits. 0 becomes 1, 1 becomes 0: 111100010
Then we add 1: **11100010 (**That is how one would write -28 in 8 bit binary.)
1.2: Text, sound and image:
Understand how and why a computer represents text and the use of character sets, including American standard code for information interchange (ASCII) and Unicode:
Character sets: Made of letters, numbers and various symbol, that can be encoded in a computer as patterns of binary digit
The standard ASCII code character set consists of: 7 bit codes that represent the letters, number and characters found on standard keyboards together with 32 control codes
Extended ASCII code is an 8 bit character set that represents 256 different characters
Unicode use either 8,16,32 bits per character, so it can represent characters from languages from around the world
Unicode allows for a greater range of characters and symbols than ASCII, including different languages and emojis
Unicode requires more bits per character than ASCII
Understand how and why a computer represents sound, including the effects of the sample rate and sample resolution
Sound was recorded by microphone
A sound wave is sampled for sound to be converted to binary, which is processed by a computer (Analogue to Digital Converter - ADC)
To analogue the sound, the sound waves are sampled at regular time intervals, approximate amplitude/values will be stored
Increase the number of possible values used to represent sound amplitudes also increase the accuracy of sound (range of 0 to 100 is more accurate that 0 to 10)
The sample resolution is the number of bits per sample (bit depth), in the example, the bit depth is 4 binary bits (at amplitude 9 = 1001)
The sample rate is the number of samples taken in a second, measure in Hz
The accuracy of the recording and the file size increases as the sample rate and resolution increase
Understand how sampling used to record a sound clip and benefits and drawbacks of using sampling rate to record sound:
Amplitude of sound wave is first determined at a set time interval (sampling rate). The higher the sampling rate, the better the resolution, but the larger the file
This given an approximate representation of sound waves
Each sample of sound waves then encoded by binary digits
Understand how and why a computer represents an image, including the effects of the resolution and color depth:
An (bitmap) image is a series of pixels that are converted to binary, which is processed by a computer
Each pixels can be represented by binary digit (black is 0 and white is 1)
The more bits a pixel contains, the more color we can obtain. For example, if each pixel is represented by 2 bits, then each pictures can be one of four color (2^2 = 4)
The colour depth is the number of bits used to represent each colour
8 bit COLOUR depth means each pixel can be one of 256 colours (2^8 = 256)
Modern computers will have 24 bit COLOUR depth
The resolution is the number of pixels in the image
The file size and quality of the image increases as the resolution and colour depth increase
1.3 Data storage and compression:
Understand how data storage is measured:
The byte is the smallest unit of memory in computer
1 BYTE = 8 BITS. 4 BITS is nibble, half a byte
1 MEBIBYTE = 1024 KIBIBYTES AND CONTINUE
Calculate the file size of an image file and a sound file, using information given:
Understand the purpose of and need for data compression:
Compression exists to reduce the size of the file
The advantages:
Less bandwidth required
Less storage space required
Shorter transmission time (uploading, sending, etc.)
Understand how files are compressed using lossy and lossless compression methods:
Lossless compression reduces the file size without permanent loss of data, e.g. run length encoding (RLE) :
A compression algorithm is used
No data is removed in the process // Original file can be restored
Repeated patterns are identified // Patterns in the data are identified
Patterns in the data and are indexed/put into a table
Patterns in the data and are replaced with their index
Patterns in the data and their positions are stored in the table
Patterns in the data and the number of times the word/pattern appears is stored in the table
Lossy compression reduces the file size by permanently removing data, e.g. reducing resolution or color depth, reducing sample rate or resolution
Recreates the file size using the remaining data
For images (JPEG,...) similarly coloured pixels are all made the same
It finds groups of repeating data and only records the data only once along with the number of times it was repeated
When compressing, the image file doesn’t rebuild or restore in its original form.
2. Data transmission
Understand that data is broken down into packets to be transmitted and describe the structure of a packet:
Data is broken down into packets to be transmitted, the packet is quite small, 64KiB => easier to transfer, upload,...
A packet of data in a unit of data contains:
packet header (contains a value to determine how much packets to transmit)
payload
trailer
The packet header includes the:
IP destination address
Sequence number of packet
IP originator’s address
Packet size
The payload includes:
Actual data in the packet ( approximately 64KiB)
The trailer includes:
Method of identifying the end of the packet
Some form of error checking to ensure the packet is error-free (method of checking : cyclic redundancy checks (CRCs)
Understand how cyclic redundancy checks work:
Sending computer adding up all the 1-bits in the payload and store this as a hex value in the trailer
Once packet arrives, the receiving calculator will recalculate the number of 1-bits in the payload
The receiving computer checks the value of 1 bits against the one sent in trailer
If two values match -> no errors, otherwise, the packet must be resend
Describe the process of packet switching:
Data is broken down into packets
Each packet could take a different route
A router controls the route a packet takes, routing selection depends on the number of packets waiting to be processed at each node
The shortest possible paths will be chosen - this may not always be the shortest path could be taken, since certain paths may be too busy or not suitable
Packets may arrive out of order
Once the last packet has arrived, packets are reordered
Advantages:
No need to tie up a single communication line
Easy to expand the package usage
High data transmission rate
Email and texts can be sent simply by rerouting packets
Disadvantages:
Packet can be lost
Not so good for some type of data transmission (e.g: video call)
Delay when reordered
Packets might be lost because they keep bouncing between each router and never reach the destination -> to prevent, a method “ hopping” is used.
Method of hopping:
A hopping number is added to the header of the pocket, everytime the packet bounces to other router, this number will be reduced by one every times leaving the hopper
Each packet has a maximum number of hopping number
If the hopping number runs out when the packet doesn't reach the destination, the packet will be deleted when going to the next router
Receiving computer will send request to resend the packet
Describe how data is transmitted from one device to another using different methods of data transmission:
3 factors need to be consider :
direction of data transmission
method of transmission
how will be the data synchronised
Several methods:
Copper wires
Radio frequency
Optical fibre
Infrared
Bandwidth: the amount of data that can be transmitted in one time
Serial transmission: bits are sent sequentially (one after the other) down the same wire (channel). Can use optical fibre, rate from 50 Mbs to 100 Gbs or USB
Parallel transmission: multiple bits are sent simultaneously down different wires (channels) within the same cable. Can use Computer data ribbon
Serial transmission: data transmission in one direction only. Two directional transmission is not possible. e.g. a radio station broadcast
Half duplex : Data transmission in both directions is possible, but not at the same time. e.g. walkie talkies
Full duplex: Data transmission is possible in both directions at the same time (simultaneously). e.g. telephones.
Understand the universal serial bus (USB) interface and explain how it is used to transmit data:
USB : a type of cable and connector commonly used for half-duplex or full-duplex serial data transmission between a computer and attached devices
USB consists of :
A shielded casing containing four wires.
Two wires are used for power and earth, and the other two wires are used for data transmission.
The computer will automated detect if USB plug in as small changes of voltage
The device is recognised, appropriate devices drivers software is loaded up so the computer and devices can communicate effectively
Understand the need to check for errors after data transmission and how these errors can occur:
Errors can occur during data transmission due to interference, e.g. data loss, data gain and data change (interference, problem with packet switching, skewing of data)
Describe the processes involved in each of the following error detection methods for detecting errors in data after transmission: parity check (odd and even), checksum and echo check:
Parity check: An extra bit (parity bit) added to a string of binary code to ensure the number of 1-bits are either even or odd, depending upon the parity check system used.
Before checking, an agreement between sender and receiver regarding which type of parity check will be used (odd or even)
Mechanism:
The sending and receiving computers agree the protocol to be used (even or odd)
The sending computer adds the correct parity bit to the binary data (either an extra 1 or 0)
The sending computer sends the binary data, including the parity bit
The receiving computer checks to make sure the overall parity of the data received is as agreed (an even or odd number of 1 bits)
If the parity of the data is incorrect, the receiving computer will request that the data is transmitted again
Checksum: A block of data is sent alongside a calculated checksum value. The receiving computer also calculates what it believes should be the checksum. The checksum values are then compared to see if an error has occurred during transmission.
Method:
The sending computer uses the block of data to be sent, and a predefined mathematical algorithm, to calculate a checksum value
The sending computer sends the data, plus the checksum value
The receiving computer uses the data it receives to also calculate what it believes should be the checksum, using the same mathematical algorithm
The two checksum values are compared by the receiving computer
Due to the nature of the algorithm, it is highly unlikely that corruption has occurred if the checksum values match
If the checksum values don’t match, the receiving computer requests that the data is transmitted again
Example: How to find checksum
Our data is : 30 9 28 41 2 and divider is 10
Total value of data is 30 + 9+ 28 + 41 + 2= 110
Checksum is 110/10 = 11, this will be use as a checksum to check the data
Drawbacks:
Fail to catch many common errors
If the data transfer change the value but the remainder still same-> checksum still allows to pass through
Echo check:
Definition also the methods:
With an echo check, the receiving computer sends a copy of the data immediately back to the sending computer for comparison.
The sending computer compares the two sets of data to check if any errors occurred during the transmission process.
If an error has occurred, the data will be transmitted again.
Drawbacks:
If the two sets of data are different you will have no way of knowing whether the error occurred when originally sent, or when it was sent back
Echo checks require a lot of extra data to be transmitted
Describe how a check digit is used to detect errors in data entry and identify examples of when a check digit is used, including international standard book numbers (ISBN) and barcodes:
Check digit: the final digit in a code of numbers. It is calculated from all the other digits in the code. Its purpose is to spot human errors on data entry.
Found in barcodes, product codes or ISBN book numbers.
How to find a check digit?
Step 1: Add the values at even positions: 1 + 2+7+9+5+3 = 27
Step 2 : Multiple above with 3 : 27 * 3 = 81
Step 3 :Add the values at odd positions: 5+1+3+9+9+7= 34
Step 4: Add results from step 2 and 3 : 81 +34= 115
Step 5: If result in step 4 ends in 0, for eg: 50, 60, 110, then check digit is 0. Otherwise, subtract number in step 4 with the nearest multiple of 10: 120-115= 5
Method:
The check digit is calculated and added to the barcode, packaging, product code etc at the point of manufacture
A human types the long numerical code into a computer, e.g. the cashier will type the barcode number when a scanner fails or packaging is damaged
The computer calculates what it believes should be the check digit, based on the numbers entered by the human
The computer then **compares it’s calculated check digit with the check digit typed in by the human (**the last digit in the long code)
If the two don’t match, then the human has made an error when typing in the numerical code, e.g. barcode number
The human will be asked by the computer to re-enter the numerical code
Benefits: Good for spotting human errors such as:
Incorrect digit entered
Transposition error (two numbers change order)
Omitted digit or extra digit
Describe how an automatic repeat query (ARQ) can be used to establish that data is received without error:
Automatic Repeat Request or automatic repeat query (ARQ): This form of error detection uses a system of acknowledgements and timeouts. Automatic Repeat ReQuests are often used to ensure reliable transmissions over an unreliable service.
Method:
The sending computer transmits a block of data
The sending computer waits a period of time to see if the receiving computer acknowledges receipt of the data
After no acknowledgement for a set period of time, a timeout occurs which triggers the data to be automatically resent by the sending computer
A positive acknowledgement means that the data was received and it passed an error check.
A negative acknowledgement means that the data was received but it cannot be used as it failed an error check. It needs to be sent again.
The timeout is a predetermined period of time that the sending device will wait to get some form of acknowledgement for the data it sent.
This will continue until the receiving computer acknowledges the data has been received, or a max number of re-sends occurs
Understand the need for and purpose of encryption when transmitting data:
Encryption: the process of encoding data or a message so that it can’t be understand by anyone others than its independant recipient
Why:
purchased via online are encrypted to try prevent theft or credit details
tools enable a user to encrypt the documents, such as spreadsheet, before sending to a colleague via internet
satellite TV transmission are encrypted to prevent users who are not subscribed to the platform
allows us to protect data during transmission and make it useless if hacked from a server.
Understand how data is encrypted using symmetric and asymmetric encryption:
Original data is plaintext, the data after transcript is ciphertext.
Symmetric : uses the same secret key to encrypt and decrypt the data.
Symmetric requires a safe method to transfer the key from one to another
Communication party must have the same key to ensure the safety
Addvantage:
easy to use
Disadvantage:
Key distribution problem.
The receiver will need a copy of your secret key.
Sending the secret key over the internet causes a serious security risk – a hacker could intercept the key and decrypt the ciphertext data too
To strengthen the encryption, it can increase the length of the encryption key or use a more complex encryption key.
Asymmetric : form of encryption where a pair of keys are responsible for encrypting and decrypting data.
Asymmetric encryption includes the use of public and private keys:
Public keys:
Provided by the recipient
It can be given to anyone who wishes to send encrypted data to the recipient
Safe to share as all it can do is encrypt data
Private key:
Remains private on the computer, never sent or shared
Only this key can decrypt the data encrypted using the public key
How it works:
Encryption keys can be created manually, randomly or via an algorithm
Strong encryption keys are created using a hashing algorithm
A hashing algorithm is a non-reversible mathematical algorithm that converts a given input into an output. Once the output has been generated it is unable to be converted back to the original input
Encryption keys are created by supplying a message or key to the hashing algorithm which turns it into a string of characters usually shown in hexadecimal
Sending clients sends the receiving clients public keys
Receiving clients use the public keys to encrypt the data to ciphertext
Sending clients use the matching private key to decrypt the ciphertext
3. Hardware:
Understand the role of the central processing unit (CPU) or microprocessor in a computer:
Processes instructions and data that are input into the computer so that the result can be output
Understand what is meant by a microprocessor:
a type of integrated circuit on a single chip
Understand the purpose of the components in a CPU, in a computer that has a Von Neumann architecture:
The CPU contains the ALU, CU and a variety of registers**.
Units: arithmetic logic unit (ALU) and control unit (CU)
Registers: program counter (PC), memory address register (MAR), memory data register (MDR), current instruction register (CIR) and accumulator (ACC)
Buses: address bus, data bus and control bus
Von Neumann architecture is based-on stored program concepts
Arithmetic/Logic Unit:
Allows arithmetic (add, subtract etc) and logic (AND, OR, NOT etc) operations to be carried out.
Control Unit (CU):
Controls the operation of the computer’s ALU, memory and input/output devices,
Telling them how to respond to the program instructions it has just read and interpreted from the memory unit.
The memory unit consists of RAM, sometimes referred to as primary or main memory. Unlike a hard drive (secondary memory), this memory is fast and also directly accessible by the CPU (as carries out by read/write operations)
RAM is split into partitions. Each partition consists of an address and its contents (both in binary form).
How to store data:
Data to be stored is written in MDR, this data has to be written in location with address, so address is written at MAR
A “write signal” will be sent and store at correct memory location
Describe the process of the fetch–decode–execute cycle including the role of each component in the process:
Understand what is meant by a core, cache and clock in a CPU and explain how they can affect the performance of a CPU:
System clock : sends out regular electric signals which synchronizes
Frequency of the pulse is clock speed, higher frequency = more instruction
Can overclock to perform faster, however, need to cool down the CPU
A core: most crucial part that carry the instruction, “Intel Dual Core" means two cores
Single core:
In old computer, can only execute one instruction at a time -> can’t open multiple app and tab, unsuitable for word processing and light web browsing
Dual cores CPU:
basic task: word processing, browsing, and light gaming
Quad cores CPU:
gaming performance and responsive operation
Eight cores CPU:
for great productivity of work and heavy gaming
Ten or more cores CPU:
Expensive, for really intense productivity and workload , eg NASA, Google
A cache memory: located within the CPU itself -> faster data access than RAM, store frequent instruction and data that need to be accessed -> improve CPU performance
When CPU wants to read memory, first place to check : cache
Larger cache memory size -> better CPU performance
Understand the purpose and use of an instruction set for a CPU:
An instruction set is a list of all the commands that can be processed by a CPU and the commands are machine code
Each operation will instruct the ALU and CU (which are part of the CPU)
An operation is made up of an opcode and an operand:
Opcode: informs the CPU what operation needs to be done
Operand: the data which needs to be acted on or it can refer to a register in the memory
Describe the purpose and characteristics of an embedded system and identify devices in which they are commonly used :
An embedded system is a combination of hardware and software used to perform a dedicated function, e.g. domestic appliances, cars, security systems, lighting systems or vending machines.
This is different to a general purpose computer that is used to perform many different functions, e.g. a personal computer (PC) or a laptop
Consist of :
Feedback system: compares its output to a desired input and take corrective action to force output to follow input
How washing machine works:
Has a microcontroller to control all the tasks
Has a keypad or dial to select temperature, wash cycle, duration, …
This data is input data in the embedded system, which carries further tasks
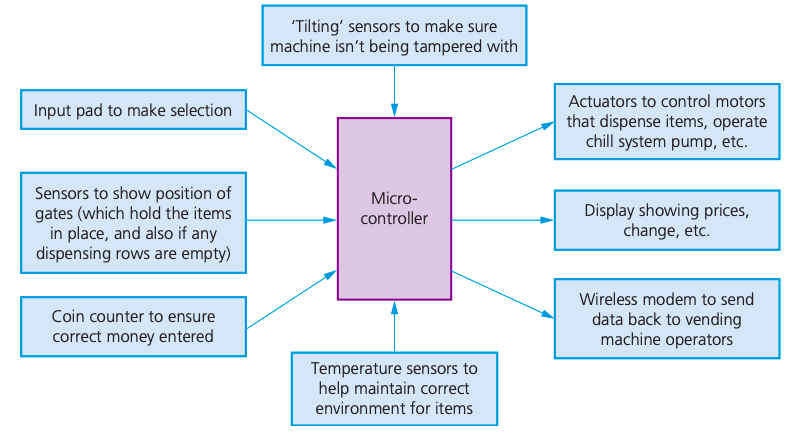
How vending machines works:
actuators to operate the motors, which drive the helixes to give the customers their selected item(s)
signals to operate the cooling system if the temperature is too high
item description and any change due shown on an LCD display panel
data sent back to the vending machine company so that they can remotely check sales activity (which could include instructions to refill the machine) without the need to visit each machine.

the time of day or day of the week
whether the room is occupied
the brightness of the natural light.
Motor vehicles :
Set top box:
Security systems:
Understand what is meant by an input device and why it is required:
An input device is a peripheral device used to provide data and control signals to a computer.
Digital camera:
The image is captured when light passes through a lens onto a light sensitive cell, this cell is made of tiny million sensors which are acting as photodiodes
Each of the sensors are often referred to as pixels since they are tiny components that make up the image
The image is converted into tiny electric charges which are then passed through ADC to form digital array
ADC converts electrical charges to level of brightness, more pixels means higher quality
Embedded in cameras:
adjust the shutter speed
focus the image automatically
operate the flash gun automatically
adjust the aperture size
adjust the size of the image
remove ‘red eye’ when the flash gun has been used
Keyboard:
There is membrane or circuit board at the base of the keys
When key is pressed and completed a circuit
CPU can determine which keys has been pressed, referring to index file to identify which can press representing
Microphone:
Sound is created by vibration of air
When diaphragm of the microphone picks up the air vibrations, the diaphragm also begins to vibrate
A copper coil is wrapped around the cone which is connected to the diaphragm
As the diaphragm vibrates, the coil moves in and out causing the copper coil to move backwards and forwards
This backwards and forwards motion causes a electric current, the current is sent to a recording devices and is analog its nature
Optical mouse:
A red LED is used in the base of the mouse and the red light is bounced off the surface and the reflection is picked up by a complementary metal oxide semiconductor (CMOS)
CMOS generates electric pulses to represent the reflected red light and these pulses are sent to a digital signal processor (DSP)
Processor can now work out the coordinates of the mouse based on the changing image patterns as it is moved about on the surface
Benefits of an optical mouse over a mechanical mouse:
There are no moving parts, therefore it is more reliable.
Dirt can’t get trapped in any of the mechanical components.
There is no need to have any special surfaces.
Drawbacks of optical mouse over a mechanical mouse:
no signal loss since there is a constant signal pathway (wire)
cheaper to operate (no need to buy new batteries or charge batteries)
fewer environmental issues (no need to dispose of old batteries)
2D scanners:
Document is placed on a glass panel
A bright light illuminates the document
A scan head moves across the document until the whole page is scanned.
And image of the document is produced and sent to a lens using a series of mirrors
The lens focuses the document image
The focused image now falls onto a charge coupled device (CCD) which consists of a numbers of integrated circuits
Software produces a digital image from the electronic form
Optical Character Recognition (OCR) is a software which converts scanned documents into a text file format
Application of 2D :
Make use of (OCR) to produce digital images which represent the passport pages
Text can be stored in ASCII format The 2D photograph in the passport is also scanned and stored as jpeg image
The passenger’s face is also photographed using a digital camera and compared using face recognition software Key parts of the face are compared (distance between eyes, width of nose
3D scanners:
Scanners take images at several points, x, y and z (lasers, magnetic, white light)
The scanned images can be used in Computer Aided Design (CAD) or to a 3D printer to produce a working model
Touch screens:
Capacitive:
Surface capacitive screen:
Sensors are placed at the corners of a screen
A finger touching the screen surface will draw current from each corner reducing the capacitance
A microcontroller measures the decrease in capacitance and hence determines the point where the finger touched the screen
Projective capacitive screen:
The transparent conductive layer is now in the form of an X-Y matrix pattern, creating a 3D electrostatic field
A finger touches the screen, it disturbs the 3D electrostatic field allowing a microcontroller to determine the coordinates of the point of contact
Infrared touch screen:
Use a glass screen with an array of sensors and infrared transmitters
The sensors detect the infrared radiation, if any beams are broken, with a finger touching screen, the infrared radiation reaching the sensor induced
The signal will be sent to a microcontroller that calculates where the screen where the screen was touched
Resistive touch screen:
Multiple layers of material that transmit electrical currents.
When the top layer (made of polyethylene) of the screen is pushed/touched into the bottom layer (made of glass with resistive coating and inert gas layer between two layers) the electrical current changes.
This allows the location of the touch to be found.
Barcode reader:
A barcode is a series of dark and light parallel lines of varying thickness. The numbers 0 to 9 are each represented by a unique series of lines
The barcode is read by a red light or laser ( light emitting diode)
Light reflected to the barcode; dark area reflects little light
Reflected light reads by sensor
The pattern is generated, which is converted into a digital data and allows computer to understand
Benefits | Drawbacks |
|---|---|
Quick and easy to identify products | If it's broken, can't use |
The use of automated stock control and sales report | Required time for making database |
Information can be easily retrieved from database | |
Faster checkout time, less errors in bill and cost saving |
QR code:
Contain more data and more rapid response for customers
Content made is accessible
Hold up to 4269 characters while barcode is 30 characters
Three square at the corner is a form of alignment
Can scan by phone, table by facing it parallel to the code
However, there are several QR code and it might contain malicious code
Understand what is meant by an output device and why it is required:
Actuators:
A device that achieves the physical movement in the machines
DLP light projector:
Uses millions of micro mirrors
The number of micro mirrors and the way they are arranged on the DLP chip determines the resolution of the image
When the micro mirrors tilt towards the light source they are on
When the micro mirrors tilt away from the light source they are off
This creates a light or dark pixel on the projection screen
A bright white light source passes through a colour filter on its way to the DLP chip
White light splits into primary colours
LCD light projector:
A powerful beam of white light is generated from a bulb
This beam of light is then sent to a group of chromatic-coated mirrors; these reflect the light back at different wavelengths
When the white light hits the mirrors, the reflected light has wavelengths corresponding to red, green and blue
These three different light pass through three LCD screens; these screens show the image to be projected as millions of pixels in grayscale
When the coloured light passes through the LCD screens, a red, green and blue version of the grey image emerges
Finally, the image passes through the projector lens onto the screen
Inkjet printer :
Data from document sent to printer driver
Printer driver ensures data is in correct format
Check made by printer driver that chosen printer is available
Data is sent to printer, stored in a temporary memory (printer buffer)
Sheet of paper is fed; sensor detects if paper is available in paper tray
Print head moves across paper printing text/image, four ink colours sprayed in exact amount
Paper is advanced so next line is printed
Repeated until buffer is empty
Once it is done, printer send an interrupt to the processor (request for more data to be sent)
Laser printer:
Data from document sent to printer driver
Printer driver ensures data is in correct format
Check made by printer driver that chosen printer is available
Data is sent to printer, stored in a temporary memory (printer buffer)
Printing drum is given a positive charge; as the drum rotates, a laser beam is scanned across it removing the positive charge leaves negatively charged areas which match the text/image
Drum is then coated with positively charged toner**,** it only sticks to negatively charged parts of the drum
A negatively charged sheet is rolled over the drum
Toner on the drum now sticks to the paper to produce copy of page
Paper finally goes through a fuser (set of heated rollers); heat melts the ink so it is permanent
Discharge lamp removes all electric charge from the drum, ready to print next page
Producing the ink droplet:
Thermal bubble and piezoelectric
3D printers:
Print 3D object and design made by CAD
Ex: making wings and other part in aerospace, fashion and art design, prosthetic limbs,
LCD screen and monitors :
Front layer of monitor is made up of Liquid Crystal Display (LCD), these tiny diodes are grouped together in threes as pixels (LCD doesn’t emit any light)
LCD monitors are back lit using Light Emitting Diode (LED) because:
LEDs reach their maximum brightness immediately
LEDs sharpens image (higher resolution), CCFL has yellow tint
LEDs improve colour image
Monitors using LED are much thinner than CCFL
LEDs consume very little power
Before LEDs, LCD monitors were backlit using CCFL
CCFL uses two fluorescent tubes behind the LCD screen which supplies the light source
Before LEDs, LCD monitors were using CCFL
CCFL uses two fluorescent tubes behind the LCD screen which supplies the light source
OLED :
These use organic materials (made up carbon compound) to create semiconductors that are very flexible
Organic films are sandwiched between two charged electrodes
When electric field is applied to electrodes, they give off light -> no forming of backlighting
Advantages :
The OLED is thinner, lighter and more flexible than LEDs or LCDs
Brighter light than LEDs and LCDs
OLED do not require light backing light LCDs, use less power than LCDs
LED technology:
Light emitting diodes, the display is made up of pixels that are arranged together as a matrix. Each is formed of three LEDs/filters, shades of colour are achieved by mixing red, blue and green. The screen can be back-lit/edge-lit
Loudspeakers:
Sound is produced by through a DAC then through amplifier and then emerges from loudspeaker
When an electric current flows through the coil of wire that is wrapped around an iron core, the core becomes a temporary electromagnet; a permanent magnet is also positioned very close to this electromagnet.
As the electric current through the coil of wire varies**, the induced magnetic field in the iron core also varies.**
This causes the iron core to be attracted towards the permanent magnet and as the current varies this will cause the iron core to vibrate.
Since the iron core is attached to a cone (made of paper or thin synthetic material), this causes the cone to vibrate, producing sound waves.
Understand what is meant by a sensor and the purposes of sensors:
Devices which read or measure physical properties
Sensor sends data to the ADC
Data needs to be converted to digital
Analogue to Digital Converter (ADC) converts physical values into digital
Digitises data and sent to the microprocessor
Microprocessor samples data every minute
If data from sensor < value stored in memory:
Signal will be positively and switch on the mechanisms
If data from sensor > value store in memory”
No action
Common sensor:
Level:
Use ultrasonic for detect level in tank : gasoline tank in car
Capacitance: refrigerator, machine in pharmaceutical factory
Flow:
Rate of flow: respiratory devices
Proximity:
Detect nearby object: Face ID
Accelerometer:
Change speed in motion: car and airbags, mobile phones to change from portrait to landscape mode
pH sensor:
Measure how acidic and alkaline is: water treatment, pollution, greenhouse
Light sensor:
Change in light intensity: light street, automatic house
Gas sensor:
Change in the proportion of gas: pollution, greenhouse, fire alarm
Pressure:
Detect pressure: burglar, traffic light control, Chemical process, liquid through pipes
Moisture:
Detect amount of water in the air: clothes drying, greenhouses, forecast
Acoustic/sound sensor:
Detect sound (vibration of air): Burglar alarm system, leak detection
Temperature:
Detect change of heat, e.g : chemical process, central heating, greenhouses,...
Infra red (passive):
Use an invisible beam to detect the change of temperature : turn on the windscreen wiper
Motion (infra-red) sensor:
Detect movement and heat, e.g: automatic door, burglar alarm systems, gaming systems, car counting system in parking, …
Magnetic field :
To detect magnetic field changes, e.g: mobile phone, anti-locking, detection of car and light trafficking
Understand what is meant by primary storage:
Primary storage is computer's main memory, directly accessed by the CPU
Including the role of:
Random access memory (RAM) :
Features of RAM:
Volatile/temporary memory (contents lost if RAM is turned off)
Used to store; data, files
It can be written to or read from and the contents from the memory can be changed
Larger the size of the RAM, faster the computer will operate
RAM never runs out of memory, continues to run slow
As RAM becomes full, the processor has to continually access the hard drive to overwrite old data on RAM with new data
There are two types of RAM:
Dynamic RAM:
Consist of : capacitor (holds bits of information 0s and 1s), transistors (chip’s controller allows to read and write data in capacitor)
Need to refresh constantly ( capacitor needs to be recharged otherwise it lose its value, leaving the all the capacitor data to 0s)
Less expensive, less power, higher capacity than SRAM
Static RAM:
Doesn't need to refresh as use flip flop to hold the each bits of data
Faster access than DRAM
Read only memory (ROM):
Non volatile and permanent memories
Can’t change, only able to read
Often used for starting of the computers (the BIOS), these are known as bootstrap
Use of RAM and ROM in computer :
Understand what is meant by secondary storage :
Secondary storage is not directly accessed by the CPU and is necessary for more permanent storage of data
Describe the operation of magnetic, optical and solid-state (flash memory) storage and give examples of each :
Magnetic:
Hard disk drive (HDD):
Data is stored in a digital format on the magnetic surface of the disks (platter)
Number of read/write heads can access all of the surfaces of the disk
Each platter will have two surfaces which can be used to store the data
Data is stored on the surfaces in sectors and tracks
HDD have very slow data access compared to RAM
Solid state drive (SSD): Most common is USB
No moving parts and all data is received at the same time (not like HDD)
Store data by controlling the movement of electrons within NAND chips, as 1s and 0s
Non-volatile rewritable memory
Benefits of using SSD rather than HDD:
More reliable (no moving parts)
Considerably lighter (suitable for laptops)
Lower power consumption
Run much cooler than HDDs
Very thin
Data access is faster than HDD
Drawback – questionable longevity (20GB per day)
Optical :
CD/DVD Disks
Laser (red) light is used to read and write data in the surface of the disk
Use a thin layer of metal alloy to store data
Both systems use a single, spiral track which runs from the centre of the disk to the edge
DVD uses Dual-Layering which increases the storage capacity (two individual recording layers)
Blu-ray Disks
Uses blue laser to carry out read and write operations
Wavelength of laser light is less than CD and DVD (stores up to five times more data than DVD)
Automatically come with secure encryption (prevent piracy and copyright infringement)
Used as back-up systems
Describe what is meant by virtual memory, how it is created and used and why it is necessary:
Pages of data are transferred between RAM and virtual memory when needed
Virtual memory is created when a computer temporarily uses secondary storage (a hard disk) to act as RAM.
Virtual memory will allow you to continue multitasking and accessing large files despite your RAM being limited or full.
This is the virtual memory diagram (must remember):
Without virtual memory, program 4 is unable to access the RAM and computer will crash
With virtual memory, one data will be removed from RAM into HDD/SSD, allowing other data accesses the RAM from HDD/SSD
After putting the data into HDD/SSD, virtual memory will now move the oldest data from RAM to the HDD/SSD to allow new data into the RAM.
This will continue until the RAM is no longer being over-utilized by competing programs running in the memory
The process above is also known as paging:
In computer OS, paging is the name given to the process of storing and retrieving data between a HDD/SSD and RAM.
A page is a fixed length contiguous (consecutive) block (unit of data) of virtual memory.
Paging is the key part how virtual memory works allowing data blocks move in and out HDD/SSD
Advantages:
Program can be larger than physical memory but still fully executed
No waste data
Reduce need of installing more expensive RAM
Disadvantages:
Secondary storage can’t have immediate access to CPU and need to pass through virtual memory -> increase workload
Thrash point :
Thrash point is achieved when most processes come to a stop because the computer is too busy dealing with virtual memory paging (moving data in and out of memory)
To prevent thrash point :
Getting more RAM
Using an SSD, not HDD
Having less programs running
Understand what is meant by cloud storage:
Cloud storage: a method of data storage where data is stored on offsite servers; the physical storage may be on hundreds of servers in many locations
Data will be saved in more than one server at the same time, in case of maintenance, clients still able to access the data. This is called data redundancy
Cloud storage can be accessed remotely in comparison to storing data locally
Physical servers and storage are needed to store data in cloud storage and it owns by a hosting company
Explain the advantages and disadvantages of storing data on the cloud in comparison to storing it locally:
Understand that a computer needs a network interface card (NIC) to access a network:
NIC: a hardware component (circuit board or chip) that is required to allow a device to connect to a network, such as the internet, it contains MAC
Understand what is meant by and the purpose of a media access control (MAC) address, including its structure:
Media Access Control address: unique number that identifies the device that is connected to the network or internet, usually made of 48 bits
MAC doesn't change when you change device’s location, can be represented by hexadecimal
It is a part of NIC (Network Interface Card)
Manufacturer's code is the unique part, if NIC was replaced, MAC will also replaced
There are two types of MAC: Universally Administered MAC Address, Locally Administered MAC Address
Reasons to change MAC address using LAA
To ensure they follow the correct formula
To bypass MAC address filter on a router or a firewall
To get past certain types of network restrictions
Understand what is meant by and the purpose of an internet protocol (IP) address and understand that there are different types of IP address:
Each device on the internet is given a unique address known as the IP address
32-bit number written in the form: 109.108.158.1
IP address gives the location of a device on the internet
IPv4 address is 32 bit numbers written in denary or hexadecimal and use (.)
IPv6 address is 128 bits and broken into 16 bit chunks and used (:)
Static IP address applied to :
Remote server of hosting websites
Online database
File transfer protocol
Describe the role of a router in a network :
Router: a device that enables data packets to be moved between different networks, for example, to join a LAN to a WAN
A router sends data to a specific destination on a network
A router can assign IP addresses
A router can connect a local network to the internet
4: Software
Describe the difference between system software and application software and provide examples of each:
System software:
Set of programs to control and manage the operation of computer hardware
Provides a platform on which other software can run
Required to allow hardware and software to run without problems
Provides a human computer interface (HCI)
Controls the allocation and usage of hardware resources.
E.g. Operating system (Microsoft Windows, macOS), BIOS, Device drivers, compilers, utilities software (software designed to carry specific tasks on a computer, this helps computer to manage, maintain and control computer resources), linkers (programs that files and compile it so it can run on computer)
Anti virus (utilities software):
Offered by operating system
Must be constantly updated
How they work:
The software is constantly running in the background
Check software of files before they are run and loaded
Compare a possible virus against a database of known viruses
Any programs or files which are affected by virus are put into quarantine
Defragmentation software (utilities software):
When the HDD is full, blocks used for files will be scattered over the disk surface. Data accessing will be faster if files could be stored in contiguous sector to reduce HDD head movements
For example, we have three files 1, 2, 3 store on track 8
Now file 2 is deleted and add some data into file 1, file 2 space will be vacant,
File 1 has now been extended to write data is sectors 10 and 11; now suppose file 3 is extended with the equivalent of 3 blocks of data;
this now requires filling up sector 9 and then finding some empty sectors to write the remainder of the data – suppose the next free sectors are on track 11:
A disk defragmenter will rearrange the blocks of data to store files in contiguous sectors wherever possible
Backup software (utilities software)
It is good practice to use the operating system system (programs that make a copy of file in case the original file is lost)
Allow a schedule for backing up files to be made
Total security:
Working version stored in SSD/HDD
Locally backup stored in removable SSD/HDD
Cloud storage
OS:
Microsoft Windows: file history
MacOS: time machine
Device drivers :
Software that connects the hardware with computer’s operating system to communicate together
Security software:
+ manages access control and user accounts (using user IDs and passwords)
links into other utility software, such as virus checkers and spyware checkers
+ protects network interfaces (for example, through the use of firewalls)
+ uses encryption and decryption to ensure any intercepted data is meaningless without a decryption key
+ oversees the updating of software (does the update request come from a legitimate source, for example).
Screensaver:
programs that supply moving and still images on the monitor screen after a period of inactivity by the computer
Virus scan
Distributed computing applications
Application software:
Allows a user to perform specific tasks using the computer’s resources
User can execute the software as and when they require.
Perform various applications (apps) on a computer
User can execute the software as and when they require.
E.g. powerpoint, word, excel
Describe the role and basic functions of an operating system:
Operating system:
The computer program responsible for the operation and smooth running of a computer
Functions of operating system:
Managing files: a file system is created to organise files and directories, which gives programs a consistent way to store and retrieve information
Handling interrupts:
An interrupt is a signal sent from a device or software to operating system
The interrupt signal causes the operating system to temporarily stop what it is doing and ‘service’ the interrupt.
The interrupt handler prioritizes interruptions as they are received, placing them into a queue as necessary.
Providing an interface: a user interface provides a way for the user to interact with the computer.
Managing peripherals and drivers: the operating system is responsible for controlling all the devices connected to the computer. It tells them how to interact and operate correctly. Device drivers are used to manage these connections.
Managing memory:
The OS is responsible for transferring programs to and from memory
It keeps track of memory usage, and decides how much should be given to each program
Managing multitasking: allows computer to carry out more than 1 task
Providing a platform for running applications: the OS runs programs, allowing them to function as designed
Providing system security: using user accounts, passwords and many utility programs, e.g. firewall to ensure the security of computer system
Managing user accounts:
Computers allows more than 1 user to log onto the system
Users’ data are stored in separate parts of the memory
Each account will have a set of username and password
Understand how hardware, firmware and an operating system are required to run applications software
When computer starts up, a part of the operating system is loaded in RAM
The start-up of the computer is handled by BIOS/Firmware
The firmware tells the computer system where the OS can be found on the hard drive, then loads the part of the OS needed and executes it
Firmware: a program that provides low level control for devices
Describe the role and operation of interrupts
An interrupt is a signal sent from a device or software to the OS
Can be caused by input/output process, software errors, hardware faults, user interaction
The interrupt causes the OS to temporarily stops what it’s doing to ‘service’ the signal
The interrupt handler is the part of the operating system which is responsible for dealing with interrupt signals.
The interrupt handler prioritizes interruptions as they are received, placing them into a queue as necessary.
For every interruption, the current task needs to be stopped, with its status saved (so it can resume later).
Software interrupts: an attempt to divide by zero, 2 processes trying to access the same memory location
Hardware interrupts: pressing a key on keyboard, moving the mouse
Explain what is meant by a high-level language and a low-level language, including the advantages and disadvantages of each
High-level language: written in a form that is close to human language, enabling programmers to just focus on the problem being solved.
Low-level language**:** used to write programs that relate to the specific architecture and hardware of a particular type of computer
Understand that assembly language is a form of low-level language that uses mnemonics, and that an assembler is needed to translate an assembly language program into machine code
Assembly language: low-level language that is used for developing code for specialist hardware, e.g. device drivers, that uses mnemonic codes
Assembler: translates an assembly language program into machine code
Describe the operation of a compiler and an interpreter, including how high-level language is translated by each and how errors are reported
Explain the advantages and disadvantages of a compiler and an interpreter
Explain the role of an IDE (integrated development environment) in writing program code and the common functions IDEs provide
An IDE is used by programmers to aid the writing and development of code. They are designed to bring together all programming tasks in 1 application; they offer a central interface with all the tools a developer needs. E.g. PyCharm, BlueJ
Code editor:
allows a program to be written and edited without the need to use a separate text editor.
speeds up the program development process, as editing can be done without changing to a different piece of software
Translator:
most IDEs provide a translator, can be a compiler or interpreter.
The interpreter is used for developing the program and compiler is used to produce the final version of the program to be used
Run-time environment:
the environment in which a program or application is executed.
It’s the hardware and software infrastructure that supports the running of a particular program/application in real time.
Error diagnostics:
errors are detected as the program code is being typed, alerts the programmer at the time
Auto-correction:
used along with error diagnostics, suggests correction when an error is detected
Prettyprint:
most code editors colour code in the program and lay out the program in a meaningful way - this is called prettyprint
Auto-completion:
code editors can offer context-sensitive prompts with text completion for variable names and reserved words
5: The internet and its use
Understand the difference between the internet and the world wide web:
The internet is the infrastructure, it relies on PHYSICAL infrastructure that allows individual devices to connect
The world wide web is the collection of websites and web pages accessed using the internet
Understand what is meant by a uniform resource locator (URL):
A URL is a text-based address for a web page; it can contain the protocol, the domain name and the web page/file name
Protocol:[http://]
Web server/domain name:[www.amongus]
Webname:[/sussy]
Filename:[/impostor.html]
Describe the purpose and operation of hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS):
It is a protocol, set of rules in order to access, transfer files across internet
HTTPS is more secure as it uses encryption methods like SSL/TSL
HTTPS have a padlock next to their URL
HTTP don't have a verification certificate but HTTPS do
Explain the purpose and functions of a web browser:
It is a software used to connect to the internet, translating the html code, ensuring SSL & TLS security can be established
Offers additional features like search history & ad blockers
Functions include:
storing bookmarks and favourites
recording user history
allowing use of multiple tabs
storing cookies
providing navigation tools
providing an address bar
Describe how web pages are located, retrieved and displayed on a device when a user enters a URL:
The user opens their browser and types in the URL and the browser asks the DNS server (1) for the IP address of the website.
In this case, let’s assume the DNS server can’t find the URL, the DNS server (2) finds the URL and can map it to the IP address is sent back to the DNS server (1) which now puts this IP address and associated URL into its cache/database.
This IP address is then sent back to the user’s computer.
The computer now sets up a communication with the website server and the required pages are downloaded. HTML files are sent from the website server to the computer. The browser interprets the HTML, which is used to structure content, and then displays the information on the user’s computer.
Explain what is meant by cookies and how they are used, including session cookies and persistent cookies:
A packet of information sent by a web server to a web browser, generating each time the user visits the website
Every time a user visits a website, cookies will have collected some key information about the user. It checks if any cookies has available before, if yes, browser will read and regain the data
Session cookies :
Store in memory and not written on the disk
It remains when browsers remain active, if browser shut down, cookies will vanish
Persistent cookies:
Authenticate with the web browser
Store on hard drive, if browser shut down, cookies will not vanish
How cookies works:
User request to login the websites
Web server sends cookies back to the user’s browser
Persistent cookies stored on hard drive, session cookies will be deleted after the websites shut down
If user login again, web server checks and identifies persistent cookies stored on user's computer and match the data on the webpage
Understand the concept of a digital currency and how digital currencies are used:
A digital currency is money that only exists electronically, no physical form
Digital currency relies on a central banking system
The problem is centralisation is maintaining confidentiality and security. To fix this, they might use cryptocurrency by using decentralisation:
Cryptocurrency uses cryptography to track transactions, address with the problem associating with centralisation
Has no state control and control by the cryptocurrency community itself
Transactions are publicly available => can track the amount of money.
Work by being a blockchain
Understand the process of blockchain and how it is used to track digital currency transactions:
Blockchain, in its basic form, is a digital ledger, that is a time-stamped series of records that cannot be altered
How it works:
When a new transaction takes place, a block is created
A new hash value is created each time a block is created. This hash value is unique and it includes a timestamp, which identifies where the actual events take place and also the hash value of the previous block. This means the data will not be deleted.
Block 1 is called the genesis book since there isn't any block. Block 2 will change the hash ( this is applied to all the other blocks). When a new transaction takes place, this means all networks' computers will have a copy of the transaction; therefore, it can't be changed unless requesting all the computers -> prevent tampering (e.g: hacking)
The decentralized database managed by multiple database is called Distributed Ledger Technology (DLT)
Blockchain can be used in voting records, medical records, land records, smart contracts,...
To prevent the fact that a new chain is created without knowing the problem of the previous chain, a method proof-by-work is used to check the chain for 10 minutes for each block before adding to the chain. The miners is specialised users will get commission for checking
Describe the processes involved in, and the aim of carrying out, a range of cyber security threats:
Brute force attack:
If a hacker wants to ‘crack’ your password, they can systematically try all the different combinations of letters, numbers and other symbols until eventually they find your password.
To prevent :
Check if the password is common or not
Use strong password, strong word list
Use programmes that generates strong password
Data interception:
A form of stealing data by tapping into a wired or wireless communication link. The intent is to compromise privacy or to obtain confidential information
Interception can be carried out using a packet sniffer, which examines data packets being sent over a network. The intercepted data is sent back to the hacker.
WiFi data interception can be carried out by wardriving.
To prevent :
Encryption of data
Use wired equivalent privacy (WEP) encrypted protocol
Firewall
Having complex password for wireless route
Not connect to public wifi that is free
Distributed Denial of Service (DDoS) attacks:
An attempt at preventing users from accessing part of a network, notably an internet server.
This is usually temporary but may be a very damaging act or a large breach of security. It doesn’t just affect networks; an individual can also be a target for such an attack.
One method of attack is to flood the network with useless spam traffic (numerous access to one webpage at the same time)
Attacker me be able to prevent user from:
Accessing their emails
Accessing websites
Accessing online services
To prevent:
Using an up to date malware checker
Firewall
Email filter, spam
Hacking:
The act of gaining illegal access to a computer system without the user’s permission.
This can lead to identity theft or the gaining of personal information; data can be deleted, passed on, changed or corrupted.
To prevent:
Anti hacking
Firewall
Strong password, not download suspicious app
Malware:
Any malicious software, biggest risk of the computer
Keep all software, including operating system, up to date
Don’t download from unknown websites
Be careful when opening email attachments
Don’t click on pop ups
Keep web browser security level medium or higher
Use anti- malware app and multiple option to prevent
Virus:
A program or code that replicates itself; designed to amend, delete or copy data or files on a user’s computer;
Often causes the computer to crash or run slowly
Could stop hardware from being able to communicate; could spread to other devices on a network
To prevent :
Anti virus software
Not download suspicious app, be careful when opening email
Worms:
A type of stand-alone malware that can self-replicate.
Their intention is to spread to other computers and corrupt whole networks;
Unlike viruses, they don’t need an active host program to be opened in order to do any damage.
To prevent:
Anti virus software
Not download suspicious app, be careful when opening email
Trojan horse:
A program which is often disguised as legitimate software but with malicious instructions embedded within it.
A Trojan horse replaces all or part of the legitimate software with the intent of carrying out some harm to the user’s computer system.
The Trojan horse will give cyber criminals access to personal information on your computers
To prevent:
Not download suspicious app, be careful when opening email or webpages
Firewall, security systems
Spyware:
Software that gathers information by monitoring all the activity on the computer, the gathered data is sent back to person who sent the app
To prevent:
Anti-software application
Set alarm of weakness
Firewall
…
Adware:
Software that floods the computers with unwanted advertising, usually form as pop ups but can frequently appear in the browser website that can redirect to a fake website which contains promotional adverts
It can spot the weakness, hard to remove, hijack the browser
To prevent :
Not clicking the suspicious ad
Firewall
Anti-advertisement app
Ransomware:
Programs that encrypt the data on a user’s computer; a decryption key is sent back to the user once they pay a sum of money (a ransom)
Often sent via Trojan horse or by social engineering
To prevent:
Be careful with paying money
Prevent clicking
Phishing:
Creator sends out a legitimate-looking email; as soon as recipient clicks on link, user is sent to a fake website and they will ask to login some personal information
Spear phishing is when there is a specific target
To prevent:
Many ISPs filter out phishing emails
User should be cautious
Anti-phishing toolbar
Look for green padlock symbol
Check if any spelling or the source of email
Pharming:
Malicious code installed on a user’s hard drive or on the web server, code will redirect the user to a fake website
Creator of malicious code can gain personal data; bank account
Can lead to fraud or identity theft
To prevent :
Some anti-spyware can identify and remove pharming code from hard drive
User should be alert
Anti virus, firewall
Social engineering:
A cybercriminal creates a social situation that can lead to a potential victim dropping their guard.
It involves the manipulation of people into breaking their normal security procedures and not following best practice.
Explain how a range of solutions are used to help keep data safe from security threats:
Access level:
User accounts control a user’s rights. This often involves having different levels of access for different people.
When using databases, levels of access are particularly important; it is essential to determine who has the right to read, write and delete data
Four level :
public access (this refers to the data anyone from the general public can access)
friends (only people identified as ‘friends’ by the owner of the data can see certain data)
custom (this allows the user to further refine what data can be seen by ‘friends’ allowing them to exclude certain content from selected people)
data owner (this is data only the owner of the data can see).
Anti - malware:
Anti - virus:
Chapter 4
Anti-spyware:
Based on 2 two method:
Rules- look for typical features which are associated with spyware, identify potential security threats
File structures - Certain file structure that associated with spyware
Detect and remove spyware that are already installed on device
Prevent user downloading spyware
Encrypt files to make data more secure
Block access to user's computer or webcam
Authentication :
ability user can prove who they are, there are numerous way to authenticate:
Passwords and username:
Use to restrict the access to data or system when access email, banking, social networking sites
Biometrics:
type of authentication that uses a unique human characteristic, such as fingerprints, voice or retina blood vessel pattern
Retina scan:
Use infrared to scan the retina in the eyes
The scanned data is sent via an ADC (analogue-digital converter) to a microprocessor.
The microprocessor compares the data received with retina scan data already stored in a database.
If the two sets of data match, a signal is sent to turn a light from red to green and also unlock the security door.
The door is controlled by a DAC (digital-analogue converter) and an actuator.
Two step verification:
To improve security, an eight-digit PIN (called a one-time passcode) is sent back to her either in an email or as a text message
Mostly for purchasing online
Automatic software updates:
These updates are vital since they may contain patches that update the software security (to protect against malware) or improve the software performance (for example, removal of bugs and addition of new features).
Checking the spelling:
The email address
Tone of email and bad spelling words
Misspelling domain name, known as typosquatting
Suspicious links
Plain mistakes spelling
Firewalls:
sits between the user’s computer and an external network (internet) and filter information in and out of the computer
Tasks carried out by firewall:
Examining ‘traffic’
Checking whether incoming or outgoing data meets criteria
If data fails the criteria, the firewall blocks ‘traffic’
Firewall can keep a list of all undesirable IP addresses
Helping to prevent viruses or hackers entering the user’s computer
Proxy servers:
Act as an intermediary between the user and a web server
Functions of proxy servers:
Allowing the internet ‘traffic’ to be filtered
By using cache, they can speed up access to information from a website
Keeping the user’s IP address secret
Acting as a firewall
Privacy control :
The controls available on web browsers, social networks and other websites that are designed to limit who can access and see a user’s personal profile.
Functions of privacy control:
Do not track setting to stop websites collecting the user browsing data
Check to see if financial detail has been saved so the next time, user doesn't need to re-type the financial details (prevent data interception)
Safer browsing and alert
Prevent pop-ups
Can switch off the sharing of location
Secure socket layer (SSL):
Type of protocol that allows data to be sent and received securely over the internet
When a user logs onto a website, SSL encrypts the data
https or padlock in the status bar
When user wants to access a secure website:
User’s web browser sends a message so it can connect with required website which is secured by SSL
Web browser requests that the web server identifies itself
Web server responds by sending a copy of its SSL certificate
Web browser checks if certificate is authentic
Sends signal back to web browser
Starts to transmit data once connection is established
If not secure, browser will display an open padlock
6: Automated and emerging technologies
Describe how sensors, microprocessors and actuators can be used in collaboration to create automated systems
Automated system: a combination of software and hardware that is designed to work automatically without the need of human intervention
Input devices, usually sensors, send data readings to the microprocessor (computer) at set intervals
To be understood, this data may have to be converted using an ADC (analogue to digital converter)
The microprocessor compares the data readings against pre-set values that it has stored (using a control program)
The microprocessor then makes a decision as to whether any action is needed (e.g. is more heat needed to maintain the pre-set value?)
If needed, the microprocessor will send a signal to instruct an output device to do something (e.g. turn on heater, turn off oxygen pump etc)
This may involve an actuator (e.g. a motor to open the gates or shop doors)
This process repeats in a continuous loop
Describe the advantages and disadvantages of an automated system used for a given scenario
Industrial:
Advantages:
Much faster than a human operator to take any necessary action
Much safer - keeps humans away from potentially dangerous environment
Higher productivity
More efficient use of materials
Less expensive in the long run
Disadvantages:
Expensive to set up
Maintenance needed, which can be expensive
The system is subject to cyberattacks
Transport:
On-board sensors and cameras gauge the size of any parking spaces, and alerts the driver if a suitable space is available
The driver then selects auto-parking and the on-board computer takes over
Actuators are used to operate the steering track, brakes and throttles under control of the computer
Advantages:
Allows the same number of cars to use fewer parking spaces
Avoids traffic disruption in cities
Fewer dents and scratches to the cars
Consistent results
Disadvantages:
Over-reliance → loss of skills
Faulty/dirty sensors or cameras can send false data to on-board computer which may lead to malfunction
Expensive
Requires additional maintenance
Agriculture:
Data from automatic weather station is received by controller
Water level sensors are used to measure level of water in irrigation channels
Data is sent back via wireless transmitters
Data is picked up by wireless receiver, which sends data to controller
The controller uses data to decide whether to start the water pumps or not
This is done by sending signals to actuators, which operate the pumps
Although the system is automatic, a supervisor remotely monitors the processes and can make changes to the controller if needed
Advantages:
Reduced labor costs
Better and more efficient control of irrigation processes
Better control of resources
Faster response than humans
Disadvantages:
Expensive to set up
High maintenance costs
Weather:
The data from sensors is sent to microprocessor, any calculations are then done
The data from sensors and the calculated values are then stored on a central database
Advantages:
Save labor
Gather information from remote areas
Consistent and error free
Disadvantages:
Expensive to set up
High maintenance costs
Removes the observer from real experience
Gaming
Gaming devices include the use of:
Accelerometers: measure acceleration and deceleration
Proximity sensors: used in smart touch pads, can detect hand/finger position
Advantages:
Increase human interaction with the game
Allows players to take actions that simulate real events happening → a more immersive experience
Disadvantages:
Can become outdated faster than PCs
May not be able to run newer games
Lighting:
As it becomes dark, the light sensor value will change, and the microprocessor will send signals to the interface to control the array of LED lights
Data from infrared sensor would also be used as a security device when the house is unoccupied
Advantages:
Reduced energy consumption
Control light sources automatically
Wireless connection can be used → safer
Disadvantages:
Expensive to set up
More maintenance required → expensive
Science:
The level sensors measure how much liquid is being added from ‘A’
This data is sent to microprocessor
The microprocessor controls the opening and closing of tap in A
This is done by sending actuator that operates the tap
Advantages:
More consistent results
Less dangerous
Fewer staff needed
Faster results
Disadvantages:
Less flexible than when using human technicians
Can be expensive to set up
Understand what is meant by robotics:
Robotics is a branch of computer science that brings together the design, construction and operation of robots.
E.g.
In factories:
Welding parts together
Spray-painting panels on a car
Fitting windscreens to cars
Cutting metals
In the home:
Autonomous floor sweepers
Autonomous lawn mower
Ironing robots
Automatic window cleaners
Drones
Can be used to film/take photographs
Can be used to make parcel deliveries
Describe the characteristics of a robot:
3 main characteristics:
a mechanical structure or framework
electrical components, such as sensors, microprocessors and actuators
Programmable
In details:
Ability to sense their surroundings: (electrical components, such as sensors, microprocessors and actuators)
Done via sensors
Recognise intermediate environments and give its ability to determine objects
Have a degree in movements (a mechanical structure or framework )
Wheels and gears to carry out movements
Mechanical structures made of many parts
Contain electrical impulses and make use of end effectors (different attachments for specialized movement)
Programmable :
Controller determines action to be taken from the sensors
Allow robot to do specific tasks
IMPORTANT:
Many robots don’t possess Artificial Intelligence (AI) as they do repetitive tasks rather than adapt to human characteristics (unable to think by themselves)
Not confuse physical robots and software robotics, such as :
Searching engine bot or WebCrawlers ( these are used for scanning websites and categorizes them)
Chat bot ( conversation with web users like Chat GPT)
Independant robots:
have no direct human control (they are said to be autonomous, for example, an autonomous vehicle)
can replace the human activity totally (no human interaction is required for the robot to function fully)
Dependant robots:
have a human who is interfacing directly with the robot (the human interface may be a computer or a control panel)
can supplement, rather than totally replace, human activity (for example, in a car assembly plant where both humans and robots work together to produce a car).
Understand the roles that robots can perform and describe the advantages and disadvantages of their use:
Industry:
E.g: paint spraying of car bodies, welding bodywork of cars, manufacturing microchips, …
The control of robot is either through embedded, built in microprocessors or directly linked to the computer system
The robot is programmed with a sequence of instructions which allows it to carry out the series of tasks
Human operator will carry out the tasks manually and robot knows how to carry the task
Equipped with sensor to detect and gather information about surroundings and prevent doing stupid things
Good at repetitive tasks, however if there are specialist tasks, human is better
Medicine:
Uses in surgical procedures, which is safer and quicker
Monitoring patients to doing actual mini surgery
Highly hygiene
Take blood sample -> less painful and safer, more hygiene that human
Microbots in target therapy, so drugs or other therapy could get to the target site causing less damage to surrounding tissue
Prosthetic limbs are now mini robots in their own rights
Bionic skins and neutral implants that interface with human nervous system giving feedback to allow control the limb better
Domestic robot:
Use in household
Autonomous vacuum cleaner uses proximity sensor and camera to avoid obstacle and cover the whole room quickly
These robots have microprocessor to control the overall action
Actuators are used to allow motor to control movement
Autonomous grass cutter ( mowers) uses proximity sensor and camera to avoid obstacle and cover the whole room quickly
These robots have microprocessor to control the overall action
Actuators are used to allow motor to control movement
Personal assistant (vectors) is controlled by microprocessor and use cloud connectivity to connect to the internet
Able to understand voice command
Use HD camera and proximity sensor to recognise human faces and navigate in the room
Transportation:
Autonomous car and buses:
Use sensors, cameras, actuators, and microprocessor to carry actions
Sensors allows to control and perform critical movements by sensing the dynamic conditions on the road
Microprocessors process data received from cameras and sensors and send signal to actuators to perform physical actions such as: change gear, apply brakes, turning steering wheels
Cameras catch visual data from the surroundings, while radar and ultrasonics allow the vehicle to build up a 3D image of its surrounding
Since the traffic light shows red, or pedestrian, the microprocessor must send signals to actuators to apply brakes and put the gear into ‘park’.
Constant monitoring must take place until the light changes to green.
When this happens, the microprocessor will again instruct actuators to put the car into first gear, release the brakes and operate the throttle (accelerator).
Autonomous train:
make use of a system called LiDaR (Light Detection and Ranging);
LiDaR uses lasers which build up a 3D image of the surroundings.
Other sensors (such as proximity sensors on train doors) and cameras (including infrared cameras) are all used for various purposes to help control the train and maintain safety.
Makes use of global positioning satellite (GPS) technology, which allows accurate changes in speed and direction to be calculated.
actuators control the train’s speed, braking and the opening and closing of the train doors.
Autonomous airplanes:
sensors to detect turbulence to ensure smooth flights
an increase in self-testing of all circuits and systems
sensors that would automatically detect depressurisation in the cabin; thus
allowing for quick stabilisation of the airplane
use of GPS for navigation and speed calculations
use of actuators to control, for example, throttle, flaps (on the wings) and the rudder.
Agriculture:
Harvesting and picking:
Designed to do this labor-intensive work; they are more accurate and faster
Higher yields and less waste
Use a camera to scan and arm for removing vegetables, fruit, …
Weed control:
Distinguish weed and crop
Use GPS tracking to stay on course to move along the rows of vines and remove the weeds;
A weed removal blade is operated by an actuator under the control of the controller (microprocessor) in the robot
A drone is used first to collect data and aerial view of the yards
Phenotyping:
the process of observing physical characteristics of a plant in order to assess its health and growth
Sensors to produce 3D images of plant to monitor health and growth, machine learning used to see the condition of leaves
Faster and more accurate than human
Seed - planting drones and fertilizer distributors:
drones (flying robots) can produce an aerial image of a farm sending back a ‘bird’s eye view’ of the crops and land
they allow seed-planting to be done far more accurately
they also allow for more efficient fertiliser-spreading to reduce waste
and improve coverage
drones can also be used in cloud seeding where the drone can add silver iodide crystals to a cloud forcing it to give up its rainwate
the drones use a very complex camera system to target seeding and allow fertiliser spraying.
Autonomous agricultural devices:
grass mowers/cutter
weeding, pruning and harvesting robots
seeding robots
fertilizer spraying
All of these devices use sensors and cameras to go around obstacles, or they can even be programmed to ‘go to sleep’ if the weather turns bad.
Understand what is meant by artificial intelligence (AI):
AI is a branch of computer science dealing with the simulation of intelligent behaviors by computers
Describe the main characteristics of AI as the collection of data and the rules for using that data, the ability to reason, and can include the ability to learn and adapt:
The main characteristics of AI as the collection of data and the rules for using that data, the ability to reason, and can include the ability to learn and adapt
There are three types of AI:
Inductive reasoning: ability to draw reasoned conclusions based on given data/situations. Use patterns to arrive a conclusion
Deductive reasoning: a number of correct facts are built up to form a set of rules which can be applied to others problems. This uses rules, facts, definitions, property to give a conclusion
Examples of AI:
News generation based on live news feed
Smart home devices (Alexa, … ):
Interacts and learn from human voices and the data received, becoming increasingly sophisticated and responsive; able to learn repetitive tasks ( this is deductive learning)
Chatbot:
Interact with human through instant messages, artificially replicating patterns of human interactions using AI to respond the messages
Autonomous cars:
Above
Facial expression recognition:
Algorithms identify key facial landmarks (e.g: eyebrows, nose, .. )
A combination of this landmarks will identify the expressions
Explain the basic operation and components of AI systems to simulate intelligent behavior:
Expert systems have a knowledge base, a rule base, an inference engine and an interface.
It mimics the decision-making ability of human
Use AI to stimulate the human or organization that has expert knowledge and experience
Use of expert systems:
oil and mineral prospecting
diagnosis of a patient’s illness
fault diagnostics in mechanical and electronic equipment
tax and financial calculations
strategy games, such as chess
logistics (efficient routing of parcel deliveries)
identification of plants, animals and chemical/biological compounds.
Use interface:
Method that system interacts with a user
Interactions can be dialogue boxes, command prompts, or other input methods
Question being asked is Yes/No answer
Inference engine:
Main processing element of the experting system
Act like search engine: examining knowledge base for the information/ data that match the queries
Asking a series of questions and applying response
Problem solving part that make use of inferences rule and rule base
Since knowledge base is a collection of objects and attributes, he engine attempts to use information gathered from the user to fine an object matches
Knowledge base:
Repository of facts
Stored all the knowledge about an area of expertise obtained from a number of resources
A collections of objects and attributes
Rule base:
Set of inference rules
Used by inference engine to draw conclusions (method closely to human reasoning)
Use logical statement, mostly “IF” statements:
For example:
IF continent = “South Africa” AND language = “Portuguese” THEN country = “Brazil
Advantages:
Improve decisions quality
Cheaper
Maintain the significance of information
How to set up ?
Information needs to be gathered from human experts or written sources
This information will be used to create knowledge base
A set of rules need to be created, making inference rules, so that the searching engine can draw conclusions.
User interface needs to be developed to allow the user nd the expert team to communicate
Once the system is set up, it needs to be fully tested
Machine learning is when a program has the ability to automatically adapt its own processes and/or data:
Training computers with sample data so they can make prediction on new or given data without any specific programs
Able to learn without following explicit instruction by using algorithms and statistical models to analyses and draw interface
Computers can make predictions or take decisions based on previous scenarios
Computers can offer fast and accurate outcomes
Can be applied to:
Computational finance
Computer vision
Computational biology
Natural language response
THE END OF THEORY
Paper 2 : Algorithms, Programming, and Logic
Understand the program development life cycle, limited to: analysis, design, coding and testing:
analysis: abstraction, decomposition of the problem, identification of the problem and requirements
design: decomposition, structure diagrams, flowcharts, pseudocode
coding: writing program code and iterative testing
testing: testing program code with the use of test data
Understand that every computer system is made up of subsystems, which are made up of further sub-systems:
A computer system is made up of software, data, hardware, communications and people;
Every computer system is made up of subsystems, which are made up of further sub-systems.
Top-down design is the decomposition of a computer system into a set of sub- systems, then breaking each sub-system down into a set of smaller sub-systems, until each sub-system just performs a single action.
Understand how a problem can be decomposed into its component parts:
inputs – the data used by the system that needs to be entered while the system is active
processes – the tasks that need to be performed using the input data and any other previously stored data
outputs – information that needs to be displayed or printed for the users of the system
storage – data that needs to be stored in files on an appropriate medium for use in the future.
Use different methods to design and construct a solution to a problem:
Structure diagram:
Structure diagrams can be used to show top-down design in a diagrammatic form.
Structure diagrams are hierarchical, showing how a computer system solution can be divided into subsystems with each level giving a more detailed breakdown.
If necessary, each sub-system can be further divided.
Flowcharts:
Shows diagrammatically the steps required to complete a task and the order that they are to be performed. These steps, together with the order, are called an algorithm
Pseudocodes:
IGCSE COMPUTER SCIENCE
Chapter 1 : Data representation
1.1 Number system:
Binary is a base 2 system that only contain 1s and 0s
In digital data storage, memory or communications, or processing the 0 and 1 value are called “low" and “high" or “On” and “Off"
Hexadecimal is easier for humans to understand than binary, as it is a shorter representation of the binary
How does a computer understand binary ? (3 marks)
A computer consists of millions of tiny switches, known as micro transistors, which must be “On” or “Off" positions.
Any form of data needs to be converted to binary to be processed by a computer
Data is processed using logic gates and stored in registers
What is a bit? (2 marks)
The term “ bit “ is short for “binary digit". A bit is a basic unit of information for all computing memory terms and either 1s or 0s
1 BYTE = 8 BITS
Decimal: Denary is a base 10 system
Hexadecimal :
Uses : error codes, MAC address, IPv6 address, HTML color codes
Understand how and why hexadecimal is used as a beneficial method of data representation:
Areas within computer science that hexadecimal is used should be identified
Hexadecimal is easier for humans to understand than binary, as it is a shorter representation of the binary
MAC Address:
Media Access Control address: unique number that identifies the device that is connected to the network or internet, usually made of 48 bits
MAC doesn't change when you change device’s location
It is a part of NIC (Network Interface Card)
IPv6 Address (IP address):
Unique identification number given to every device that is connected to the internet
Identify the unique location on which you are connected to the internet
Help to transfer data globally
While connecting to the internet, you are assigned to the IP address to use for your session, this issues by network or ISP
Confusion between IP and MAC :
IP : location of devices; MAC: actual devices at location of devices
Errors code:
Hex number refers to the memory location of the error => programmers fix the problems
HTML :
HyperText Mark-up Language: used when writing and developing pages, markup language , used for presentation of a page. Using tags <> to bracket a piece of text
Calculation of binary:
Addition of binary:
Logical shift : moving binary to the left or right
Each shift left is equivalent to multiply the binary numbers by 2
Each shift left is equivalent to divide the binary numbers by 2
Bits shifted from the end of the register are lost and zeros are shifted in at the opposite end of the register
Ex: Shift denary 21 to the left
Shift left is equivalent to multiply the binary numbers by 2 = 21 x 2 = 42(10)
128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 | |
|---|---|---|---|---|---|---|---|---|
21(10) | 0 | 0 | 0 | 1 | 0 | 1 | 0 | 1 |
After shift to the left (42(10)) | 0 | 0 | 1 | 0 | 1 | 0 | 1 | 0 |
An overflow error will occur if the value is greater than 255 in an 8-bit register
A computer or a device has a predefined limit that it can represent or store, for example 16-bit
An overflow error occurs when a value outside this limit should be returned
Two compliment (Binary Numbers):
Find how -28 would be expressed in two's complement notation:
First we write out 28 in binary form: 000011100
Then we invert the digits. 0 becomes 1, 1 becomes 0: 111100010
Then we add 1: **11100010 (**That is how one would write -28 in 8 bit binary.)
1.2: Text, sound and image:
Understand how and why a computer represents text and the use of character sets, including American standard code for information interchange (ASCII) and Unicode:
Character sets: Made of letters, numbers and various symbol, that can be encoded in a computer as patterns of binary digit
The standard ASCII code character set consists of: 7 bit codes that represent the letters, number and characters found on standard keyboards together with 32 control codes
Extended ASCII code is an 8 bit character set that represents 256 different characters
Unicode use either 8,16,32 bits per character, so it can represent characters from languages from around the world
Unicode allows for a greater range of characters and symbols than ASCII, including different languages and emojis
Unicode requires more bits per character than ASCII
Understand how and why a computer represents sound, including the effects of the sample rate and sample resolution
Sound was recorded by microphone
A sound wave is sampled for sound to be converted to binary, which is processed by a computer (Analogue to Digital Converter - ADC)
To analogue the sound, the sound waves are sampled at regular time intervals, approximate amplitude/values will be stored
Increase the number of possible values used to represent sound amplitudes also increase the accuracy of sound (range of 0 to 100 is more accurate that 0 to 10)
The sample resolution is the number of bits per sample (bit depth), in the example, the bit depth is 4 binary bits (at amplitude 9 = 1001)
The sample rate is the number of samples taken in a second, measure in Hz
The accuracy of the recording and the file size increases as the sample rate and resolution increase
Understand how sampling used to record a sound clip and benefits and drawbacks of using sampling rate to record sound:
Amplitude of sound wave is first determined at a set time interval (sampling rate). The higher the sampling rate, the better the resolution, but the larger the file
This given an approximate representation of sound waves
Each sample of sound waves then encoded by binary digits
Understand how and why a computer represents an image, including the effects of the resolution and color depth:
An (bitmap) image is a series of pixels that are converted to binary, which is processed by a computer
Each pixels can be represented by binary digit (black is 0 and white is 1)
The more bits a pixel contains, the more color we can obtain. For example, if each pixel is represented by 2 bits, then each pictures can be one of four color (2^2 = 4)
The colour depth is the number of bits used to represent each colour
8 bit COLOUR depth means each pixel can be one of 256 colours (2^8 = 256)
Modern computers will have 24 bit COLOUR depth
The resolution is the number of pixels in the image
The file size and quality of the image increases as the resolution and colour depth increase
1.3 Data storage and compression:
Understand how data storage is measured:
The byte is the smallest unit of memory in computer
1 BYTE = 8 BITS. 4 BITS is nibble, half a byte
1 MEBIBYTE = 1024 KIBIBYTES AND CONTINUE
Calculate the file size of an image file and a sound file, using information given:
Understand the purpose of and need for data compression:
Compression exists to reduce the size of the file
The advantages:
Less bandwidth required
Less storage space required
Shorter transmission time (uploading, sending, etc.)
Understand how files are compressed using lossy and lossless compression methods:
Lossless compression reduces the file size without permanent loss of data, e.g. run length encoding (RLE) :
A compression algorithm is used
No data is removed in the process // Original file can be restored
Repeated patterns are identified // Patterns in the data are identified
Patterns in the data and are indexed/put into a table
Patterns in the data and are replaced with their index
Patterns in the data and their positions are stored in the table
Patterns in the data and the number of times the word/pattern appears is stored in the table
Lossy compression reduces the file size by permanently removing data, e.g. reducing resolution or color depth, reducing sample rate or resolution
Recreates the file size using the remaining data
For images (JPEG,...) similarly coloured pixels are all made the same
It finds groups of repeating data and only records the data only once along with the number of times it was repeated
When compressing, the image file doesn’t rebuild or restore in its original form.
2. Data transmission
Understand that data is broken down into packets to be transmitted and describe the structure of a packet:
Data is broken down into packets to be transmitted, the packet is quite small, 64KiB => easier to transfer, upload,...
A packet of data in a unit of data contains:
packet header (contains a value to determine how much packets to transmit)
payload
trailer
The packet header includes the:
IP destination address
Sequence number of packet
IP originator’s address
Packet size
The payload includes:
Actual data in the packet ( approximately 64KiB)
The trailer includes:
Method of identifying the end of the packet
Some form of error checking to ensure the packet is error-free (method of checking : cyclic redundancy checks (CRCs)
Understand how cyclic redundancy checks work:
Sending computer adding up all the 1-bits in the payload and store this as a hex value in the trailer
Once packet arrives, the receiving calculator will recalculate the number of 1-bits in the payload
The receiving computer checks the value of 1 bits against the one sent in trailer
If two values match -> no errors, otherwise, the packet must be resend
Describe the process of packet switching:
Data is broken down into packets
Each packet could take a different route
A router controls the route a packet takes, routing selection depends on the number of packets waiting to be processed at each node
The shortest possible paths will be chosen - this may not always be the shortest path could be taken, since certain paths may be too busy or not suitable
Packets may arrive out of order
Once the last packet has arrived, packets are reordered
Advantages:
No need to tie up a single communication line
Easy to expand the package usage
High data transmission rate
Email and texts can be sent simply by rerouting packets
Disadvantages:
Packet can be lost
Not so good for some type of data transmission (e.g: video call)
Delay when reordered
Packets might be lost because they keep bouncing between each router and never reach the destination -> to prevent, a method “ hopping” is used.
Method of hopping:
A hopping number is added to the header of the pocket, everytime the packet bounces to other router, this number will be reduced by one every times leaving the hopper
Each packet has a maximum number of hopping number
If the hopping number runs out when the packet doesn't reach the destination, the packet will be deleted when going to the next router
Receiving computer will send request to resend the packet
Describe how data is transmitted from one device to another using different methods of data transmission:
3 factors need to be consider :
direction of data transmission
method of transmission
how will be the data synchronised
Several methods:
Copper wires
Radio frequency
Optical fibre
Infrared
Bandwidth: the amount of data that can be transmitted in one time
Serial transmission: bits are sent sequentially (one after the other) down the same wire (channel). Can use optical fibre, rate from 50 Mbs to 100 Gbs or USB
Parallel transmission: multiple bits are sent simultaneously down different wires (channels) within the same cable. Can use Computer data ribbon
Serial transmission: data transmission in one direction only. Two directional transmission is not possible. e.g. a radio station broadcast
Half duplex : Data transmission in both directions is possible, but not at the same time. e.g. walkie talkies
Full duplex: Data transmission is possible in both directions at the same time (simultaneously). e.g. telephones.
Understand the universal serial bus (USB) interface and explain how it is used to transmit data:
USB : a type of cable and connector commonly used for half-duplex or full-duplex serial data transmission between a computer and attached devices
USB consists of :
A shielded casing containing four wires.
Two wires are used for power and earth, and the other two wires are used for data transmission.
The computer will automated detect if USB plug in as small changes of voltage
The device is recognised, appropriate devices drivers software is loaded up so the computer and devices can communicate effectively
Understand the need to check for errors after data transmission and how these errors can occur:
Errors can occur during data transmission due to interference, e.g. data loss, data gain and data change (interference, problem with packet switching, skewing of data)
Describe the processes involved in each of the following error detection methods for detecting errors in data after transmission: parity check (odd and even), checksum and echo check:
Parity check: An extra bit (parity bit) added to a string of binary code to ensure the number of 1-bits are either even or odd, depending upon the parity check system used.
Before checking, an agreement between sender and receiver regarding which type of parity check will be used (odd or even)
Mechanism:
The sending and receiving computers agree the protocol to be used (even or odd)
The sending computer adds the correct parity bit to the binary data (either an extra 1 or 0)
The sending computer sends the binary data, including the parity bit
The receiving computer checks to make sure the overall parity of the data received is as agreed (an even or odd number of 1 bits)
If the parity of the data is incorrect, the receiving computer will request that the data is transmitted again
Checksum: A block of data is sent alongside a calculated checksum value. The receiving computer also calculates what it believes should be the checksum. The checksum values are then compared to see if an error has occurred during transmission.
Method:
The sending computer uses the block of data to be sent, and a predefined mathematical algorithm, to calculate a checksum value
The sending computer sends the data, plus the checksum value
The receiving computer uses the data it receives to also calculate what it believes should be the checksum, using the same mathematical algorithm
The two checksum values are compared by the receiving computer
Due to the nature of the algorithm, it is highly unlikely that corruption has occurred if the checksum values match
If the checksum values don’t match, the receiving computer requests that the data is transmitted again
Example: How to find checksum
Our data is : 30 9 28 41 2 and divider is 10
Total value of data is 30 + 9+ 28 + 41 + 2= 110
Checksum is 110/10 = 11, this will be use as a checksum to check the data
Drawbacks:
Fail to catch many common errors
If the data transfer change the value but the remainder still same-> checksum still allows to pass through
Echo check:
Definition also the methods:
With an echo check, the receiving computer sends a copy of the data immediately back to the sending computer for comparison.
The sending computer compares the two sets of data to check if any errors occurred during the transmission process.
If an error has occurred, the data will be transmitted again.
Drawbacks:
If the two sets of data are different you will have no way of knowing whether the error occurred when originally sent, or when it was sent back
Echo checks require a lot of extra data to be transmitted
Describe how a check digit is used to detect errors in data entry and identify examples of when a check digit is used, including international standard book numbers (ISBN) and barcodes:
Check digit: the final digit in a code of numbers. It is calculated from all the other digits in the code. Its purpose is to spot human errors on data entry.
Found in barcodes, product codes or ISBN book numbers.
How to find a check digit?
Step 1: Add the values at even positions: 1 + 2+7+9+5+3 = 27
Step 2 : Multiple above with 3 : 27 * 3 = 81
Step 3 :Add the values at odd positions: 5+1+3+9+9+7= 34
Step 4: Add results from step 2 and 3 : 81 +34= 115
Step 5: If result in step 4 ends in 0, for eg: 50, 60, 110, then check digit is 0. Otherwise, subtract number in step 4 with the nearest multiple of 10: 120-115= 5
Method:
The check digit is calculated and added to the barcode, packaging, product code etc at the point of manufacture
A human types the long numerical code into a computer, e.g. the cashier will type the barcode number when a scanner fails or packaging is damaged
The computer calculates what it believes should be the check digit, based on the numbers entered by the human
The computer then **compares it’s calculated check digit with the check digit typed in by the human (**the last digit in the long code)
If the two don’t match, then the human has made an error when typing in the numerical code, e.g. barcode number
The human will be asked by the computer to re-enter the numerical code
Benefits: Good for spotting human errors such as:
Incorrect digit entered
Transposition error (two numbers change order)
Omitted digit or extra digit
Describe how an automatic repeat query (ARQ) can be used to establish that data is received without error:
Automatic Repeat Request or automatic repeat query (ARQ): This form of error detection uses a system of acknowledgements and timeouts. Automatic Repeat ReQuests are often used to ensure reliable transmissions over an unreliable service.
Method:
The sending computer transmits a block of data
The sending computer waits a period of time to see if the receiving computer acknowledges receipt of the data
After no acknowledgement for a set period of time, a timeout occurs which triggers the data to be automatically resent by the sending computer
A positive acknowledgement means that the data was received and it passed an error check.
A negative acknowledgement means that the data was received but it cannot be used as it failed an error check. It needs to be sent again.
The timeout is a predetermined period of time that the sending device will wait to get some form of acknowledgement for the data it sent.
This will continue until the receiving computer acknowledges the data has been received, or a max number of re-sends occurs
Understand the need for and purpose of encryption when transmitting data:
Encryption: the process of encoding data or a message so that it can’t be understand by anyone others than its independant recipient
Why:
purchased via online are encrypted to try prevent theft or credit details
tools enable a user to encrypt the documents, such as spreadsheet, before sending to a colleague via internet
satellite TV transmission are encrypted to prevent users who are not subscribed to the platform
allows us to protect data during transmission and make it useless if hacked from a server.
Understand how data is encrypted using symmetric and asymmetric encryption:
Original data is plaintext, the data after transcript is ciphertext.
Symmetric : uses the same secret key to encrypt and decrypt the data.
Symmetric requires a safe method to transfer the key from one to another
Communication party must have the same key to ensure the safety
Addvantage:
easy to use
Disadvantage:
Key distribution problem.
The receiver will need a copy of your secret key.
Sending the secret key over the internet causes a serious security risk – a hacker could intercept the key and decrypt the ciphertext data too
To strengthen the encryption, it can increase the length of the encryption key or use a more complex encryption key.
Asymmetric : form of encryption where a pair of keys are responsible for encrypting and decrypting data.
Asymmetric encryption includes the use of public and private keys:
Public keys:
Provided by the recipient
It can be given to anyone who wishes to send encrypted data to the recipient
Safe to share as all it can do is encrypt data
Private key:
Remains private on the computer, never sent or shared
Only this key can decrypt the data encrypted using the public key
How it works:
Encryption keys can be created manually, randomly or via an algorithm
Strong encryption keys are created using a hashing algorithm
A hashing algorithm is a non-reversible mathematical algorithm that converts a given input into an output. Once the output has been generated it is unable to be converted back to the original input
Encryption keys are created by supplying a message or key to the hashing algorithm which turns it into a string of characters usually shown in hexadecimal
Sending clients sends the receiving clients public keys
Receiving clients use the public keys to encrypt the data to ciphertext
Sending clients use the matching private key to decrypt the ciphertext
3. Hardware:
Understand the role of the central processing unit (CPU) or microprocessor in a computer:
Processes instructions and data that are input into the computer so that the result can be output
Understand what is meant by a microprocessor:
a type of integrated circuit on a single chip
Understand the purpose of the components in a CPU, in a computer that has a Von Neumann architecture:
The CPU contains the ALU, CU and a variety of registers**.
Units: arithmetic logic unit (ALU) and control unit (CU)
Registers: program counter (PC), memory address register (MAR), memory data register (MDR), current instruction register (CIR) and accumulator (ACC)
Buses: address bus, data bus and control bus
Von Neumann architecture is based-on stored program concepts
Arithmetic/Logic Unit:
Allows arithmetic (add, subtract etc) and logic (AND, OR, NOT etc) operations to be carried out.
Control Unit (CU):
Controls the operation of the computer’s ALU, memory and input/output devices,
Telling them how to respond to the program instructions it has just read and interpreted from the memory unit.
The memory unit consists of RAM, sometimes referred to as primary or main memory. Unlike a hard drive (secondary memory), this memory is fast and also directly accessible by the CPU (as carries out by read/write operations)
RAM is split into partitions. Each partition consists of an address and its contents (both in binary form).
How to store data:
Data to be stored is written in MDR, this data has to be written in location with address, so address is written at MAR
A “write signal” will be sent and store at correct memory location
Describe the process of the fetch–decode–execute cycle including the role of each component in the process:
Understand what is meant by a core, cache and clock in a CPU and explain how they can affect the performance of a CPU:
System clock : sends out regular electric signals which synchronizes
Frequency of the pulse is clock speed, higher frequency = more instruction
Can overclock to perform faster, however, need to cool down the CPU
A core: most crucial part that carry the instruction, “Intel Dual Core" means two cores
Single core:
In old computer, can only execute one instruction at a time -> can’t open multiple app and tab, unsuitable for word processing and light web browsing
Dual cores CPU:
basic task: word processing, browsing, and light gaming
Quad cores CPU:
gaming performance and responsive operation
Eight cores CPU:
for great productivity of work and heavy gaming
Ten or more cores CPU:
Expensive, for really intense productivity and workload , eg NASA, Google
A cache memory: located within the CPU itself -> faster data access than RAM, store frequent instruction and data that need to be accessed -> improve CPU performance
When CPU wants to read memory, first place to check : cache
Larger cache memory size -> better CPU performance
Understand the purpose and use of an instruction set for a CPU:
An instruction set is a list of all the commands that can be processed by a CPU and the commands are machine code
Each operation will instruct the ALU and CU (which are part of the CPU)
An operation is made up of an opcode and an operand:
Opcode: informs the CPU what operation needs to be done
Operand: the data which needs to be acted on or it can refer to a register in the memory
Describe the purpose and characteristics of an embedded system and identify devices in which they are commonly used :
An embedded system is a combination of hardware and software used to perform a dedicated function, e.g. domestic appliances, cars, security systems, lighting systems or vending machines.
This is different to a general purpose computer that is used to perform many different functions, e.g. a personal computer (PC) or a laptop
Consist of :
Feedback system: compares its output to a desired input and take corrective action to force output to follow input
How washing machine works:
Has a microcontroller to control all the tasks
Has a keypad or dial to select temperature, wash cycle, duration, …
This data is input data in the embedded system, which carries further tasks
How vending machines works:
actuators to operate the motors, which drive the helixes to give the customers their selected item(s)
signals to operate the cooling system if the temperature is too high
item description and any change due shown on an LCD display panel
data sent back to the vending machine company so that they can remotely check sales activity (which could include instructions to refill the machine) without the need to visit each machine.


the time of day or day of the week
whether the room is occupied
the brightness of the natural light.
Motor vehicles :
Set top box:
Security systems:
Understand what is meant by an input device and why it is required:
An input device is a peripheral device used to provide data and control signals to a computer.
Digital camera:
The image is captured when light passes through a lens onto a light sensitive cell, this cell is made of tiny million sensors which are acting as photodiodes
Each of the sensors are often referred to as pixels since they are tiny components that make up the image
The image is converted into tiny electric charges which are then passed through ADC to form digital array
ADC converts electrical charges to level of brightness, more pixels means higher quality
Embedded in cameras:
adjust the shutter speed
focus the image automatically
operate the flash gun automatically
adjust the aperture size
adjust the size of the image
remove ‘red eye’ when the flash gun has been used
Keyboard:
There is membrane or circuit board at the base of the keys
When key is pressed and completed a circuit
CPU can determine which keys has been pressed, referring to index file to identify which can press representing
Microphone:
Sound is created by vibration of air
When diaphragm of the microphone picks up the air vibrations, the diaphragm also begins to vibrate
A copper coil is wrapped around the cone which is connected to the diaphragm
As the diaphragm vibrates, the coil moves in and out causing the copper coil to move backwards and forwards
This backwards and forwards motion causes a electric current, the current is sent to a recording devices and is analog its nature
Optical mouse:
A red LED is used in the base of the mouse and the red light is bounced off the surface and the reflection is picked up by a complementary metal oxide semiconductor (CMOS)
CMOS generates electric pulses to represent the reflected red light and these pulses are sent to a digital signal processor (DSP)
Processor can now work out the coordinates of the mouse based on the changing image patterns as it is moved about on the surface
Benefits of an optical mouse over a mechanical mouse:
There are no moving parts, therefore it is more reliable.
Dirt can’t get trapped in any of the mechanical components.
There is no need to have any special surfaces.
Drawbacks of optical mouse over a mechanical mouse:
no signal loss since there is a constant signal pathway (wire)
cheaper to operate (no need to buy new batteries or charge batteries)
fewer environmental issues (no need to dispose of old batteries)
2D scanners:
Document is placed on a glass panel
A bright light illuminates the document
A scan head moves across the document until the whole page is scanned.
And image of the document is produced and sent to a lens using a series of mirrors
The lens focuses the document image
The focused image now falls onto a charge coupled device (CCD) which consists of a numbers of integrated circuits
Software produces a digital image from the electronic form
Optical Character Recognition (OCR) is a software which converts scanned documents into a text file format
Application of 2D :
Make use of (OCR) to produce digital images which represent the passport pages
Text can be stored in ASCII format The 2D photograph in the passport is also scanned and stored as jpeg image
The passenger’s face is also photographed using a digital camera and compared using face recognition software Key parts of the face are compared (distance between eyes, width of nose
3D scanners:
Scanners take images at several points, x, y and z (lasers, magnetic, white light)
The scanned images can be used in Computer Aided Design (CAD) or to a 3D printer to produce a working model
Touch screens:
Capacitive:
Surface capacitive screen:
Sensors are placed at the corners of a screen
A finger touching the screen surface will draw current from each corner reducing the capacitance
A microcontroller measures the decrease in capacitance and hence determines the point where the finger touched the screen
Projective capacitive screen:
The transparent conductive layer is now in the form of an X-Y matrix pattern, creating a 3D electrostatic field
A finger touches the screen, it disturbs the 3D electrostatic field allowing a microcontroller to determine the coordinates of the point of contact
Infrared touch screen:
Use a glass screen with an array of sensors and infrared transmitters
The sensors detect the infrared radiation, if any beams are broken, with a finger touching screen, the infrared radiation reaching the sensor induced
The signal will be sent to a microcontroller that calculates where the screen where the screen was touched
Resistive touch screen:
Multiple layers of material that transmit electrical currents.
When the top layer (made of polyethylene) of the screen is pushed/touched into the bottom layer (made of glass with resistive coating and inert gas layer between two layers) the electrical current changes.
This allows the location of the touch to be found.
Barcode reader:
A barcode is a series of dark and light parallel lines of varying thickness. The numbers 0 to 9 are each represented by a unique series of lines
The barcode is read by a red light or laser ( light emitting diode)
Light reflected to the barcode; dark area reflects little light
Reflected light reads by sensor
The pattern is generated, which is converted into a digital data and allows computer to understand
Benefits | Drawbacks |
|---|---|
Quick and easy to identify products | If it's broken, can't use |
The use of automated stock control and sales report | Required time for making database |
Information can be easily retrieved from database | |
Faster checkout time, less errors in bill and cost saving |
QR code:
Contain more data and more rapid response for customers
Content made is accessible
Hold up to 4269 characters while barcode is 30 characters
Three square at the corner is a form of alignment
Can scan by phone, table by facing it parallel to the code
However, there are several QR code and it might contain malicious code
Understand what is meant by an output device and why it is required:
Actuators:
A device that achieves the physical movement in the machines
DLP light projector:
Uses millions of micro mirrors
The number of micro mirrors and the way they are arranged on the DLP chip determines the resolution of the image
When the micro mirrors tilt towards the light source they are on
When the micro mirrors tilt away from the light source they are off
This creates a light or dark pixel on the projection screen
A bright white light source passes through a colour filter on its way to the DLP chip
White light splits into primary colours
LCD light projector:
A powerful beam of white light is generated from a bulb
This beam of light is then sent to a group of chromatic-coated mirrors; these reflect the light back at different wavelengths
When the white light hits the mirrors, the reflected light has wavelengths corresponding to red, green and blue
These three different light pass through three LCD screens; these screens show the image to be projected as millions of pixels in grayscale
When the coloured light passes through the LCD screens, a red, green and blue version of the grey image emerges
Finally, the image passes through the projector lens onto the screen
Inkjet printer :
Data from document sent to printer driver
Printer driver ensures data is in correct format
Check made by printer driver that chosen printer is available
Data is sent to printer, stored in a temporary memory (printer buffer)
Sheet of paper is fed; sensor detects if paper is available in paper tray
Print head moves across paper printing text/image, four ink colours sprayed in exact amount
Paper is advanced so next line is printed
Repeated until buffer is empty
Once it is done, printer send an interrupt to the processor (request for more data to be sent)
Laser printer:
Data from document sent to printer driver
Printer driver ensures data is in correct format
Check made by printer driver that chosen printer is available
Data is sent to printer, stored in a temporary memory (printer buffer)
Printing drum is given a positive charge; as the drum rotates, a laser beam is scanned across it removing the positive charge leaves negatively charged areas which match the text/image
Drum is then coated with positively charged toner**,** it only sticks to negatively charged parts of the drum
A negatively charged sheet is rolled over the drum
Toner on the drum now sticks to the paper to produce copy of page
Paper finally goes through a fuser (set of heated rollers); heat melts the ink so it is permanent
Discharge lamp removes all electric charge from the drum, ready to print next page
Producing the ink droplet:
Thermal bubble and piezoelectric
3D printers:
Print 3D object and design made by CAD
Ex: making wings and other part in aerospace, fashion and art design, prosthetic limbs,
LCD screen and monitors :
Front layer of monitor is made up of Liquid Crystal Display (LCD), these tiny diodes are grouped together in threes as pixels (LCD doesn’t emit any light)
LCD monitors are back lit using Light Emitting Diode (LED) because:
LEDs reach their maximum brightness immediately
LEDs sharpens image (higher resolution), CCFL has yellow tint
LEDs improve colour image
Monitors using LED are much thinner than CCFL
LEDs consume very little power
Before LEDs, LCD monitors were backlit using CCFL
CCFL uses two fluorescent tubes behind the LCD screen which supplies the light source
Before LEDs, LCD monitors were using CCFL
CCFL uses two fluorescent tubes behind the LCD screen which supplies the light source
OLED :
These use organic materials (made up carbon compound) to create semiconductors that are very flexible
Organic films are sandwiched between two charged electrodes
When electric field is applied to electrodes, they give off light -> no forming of backlighting
Advantages :
The OLED is thinner, lighter and more flexible than LEDs or LCDs
Brighter light than LEDs and LCDs
OLED do not require light backing light LCDs, use less power than LCDs
LED technology:
Light emitting diodes, the display is made up of pixels that are arranged together as a matrix. Each is formed of three LEDs/filters, shades of colour are achieved by mixing red, blue and green. The screen can be back-lit/edge-lit
Loudspeakers:
Sound is produced by through a DAC then through amplifier and then emerges from loudspeaker
When an electric current flows through the coil of wire that is wrapped around an iron core, the core becomes a temporary electromagnet; a permanent magnet is also positioned very close to this electromagnet.
As the electric current through the coil of wire varies**, the induced magnetic field in the iron core also varies.**
This causes the iron core to be attracted towards the permanent magnet and as the current varies this will cause the iron core to vibrate.
Since the iron core is attached to a cone (made of paper or thin synthetic material), this causes the cone to vibrate, producing sound waves.
Understand what is meant by a sensor and the purposes of sensors:
Devices which read or measure physical properties
Sensor sends data to the ADC
Data needs to be converted to digital
Analogue to Digital Converter (ADC) converts physical values into digital
Digitises data and sent to the microprocessor
Microprocessor samples data every minute
If data from sensor < value stored in memory:
Signal will be positively and switch on the mechanisms
If data from sensor > value store in memory”
No action
Common sensor:
Level:
Use ultrasonic for detect level in tank : gasoline tank in car
Capacitance: refrigerator, machine in pharmaceutical factory
Flow:
Rate of flow: respiratory devices
Proximity:
Detect nearby object: Face ID
Accelerometer:
Change speed in motion: car and airbags, mobile phones to change from portrait to landscape mode
pH sensor:
Measure how acidic and alkaline is: water treatment, pollution, greenhouse
Light sensor:
Change in light intensity: light street, automatic house
Gas sensor:
Change in the proportion of gas: pollution, greenhouse, fire alarm
Pressure:
Detect pressure: burglar, traffic light control, Chemical process, liquid through pipes
Moisture:
Detect amount of water in the air: clothes drying, greenhouses, forecast
Acoustic/sound sensor:
Detect sound (vibration of air): Burglar alarm system, leak detection
Temperature:
Detect change of heat, e.g : chemical process, central heating, greenhouses,...
Infra red (passive):
Use an invisible beam to detect the change of temperature : turn on the windscreen wiper
Motion (infra-red) sensor:
Detect movement and heat, e.g: automatic door, burglar alarm systems, gaming systems, car counting system in parking, …
Magnetic field :
To detect magnetic field changes, e.g: mobile phone, anti-locking, detection of car and light trafficking
Understand what is meant by primary storage:
Primary storage is computer's main memory, directly accessed by the CPU
Including the role of:
Random access memory (RAM) :
Features of RAM:
Volatile/temporary memory (contents lost if RAM is turned off)
Used to store; data, files
It can be written to or read from and the contents from the memory can be changed
Larger the size of the RAM, faster the computer will operate
RAM never runs out of memory, continues to run slow
As RAM becomes full, the processor has to continually access the hard drive to overwrite old data on RAM with new data
There are two types of RAM:
Dynamic RAM:
Consist of : capacitor (holds bits of information 0s and 1s), transistors (chip’s controller allows to read and write data in capacitor)
Need to refresh constantly ( capacitor needs to be recharged otherwise it lose its value, leaving the all the capacitor data to 0s)
Less expensive, less power, higher capacity than SRAM
Static RAM:
Doesn't need to refresh as use flip flop to hold the each bits of data
Faster access than DRAM
Read only memory (ROM):
Non volatile and permanent memories
Can’t change, only able to read
Often used for starting of the computers (the BIOS), these are known as bootstrap
Use of RAM and ROM in computer :
Understand what is meant by secondary storage :
Secondary storage is not directly accessed by the CPU and is necessary for more permanent storage of data
Describe the operation of magnetic, optical and solid-state (flash memory) storage and give examples of each :
Magnetic:
Hard disk drive (HDD):
Data is stored in a digital format on the magnetic surface of the disks (platter)
Number of read/write heads can access all of the surfaces of the disk
Each platter will have two surfaces which can be used to store the data
Data is stored on the surfaces in sectors and tracks
HDD have very slow data access compared to RAM
Solid state drive (SSD): Most common is USB
No moving parts and all data is received at the same time (not like HDD)
Store data by controlling the movement of electrons within NAND chips, as 1s and 0s
Non-volatile rewritable memory
Benefits of using SSD rather than HDD:
More reliable (no moving parts)
Considerably lighter (suitable for laptops)
Lower power consumption
Run much cooler than HDDs
Very thin
Data access is faster than HDD
Drawback – questionable longevity (20GB per day)
Optical :
CD/DVD Disks
Laser (red) light is used to read and write data in the surface of the disk
Use a thin layer of metal alloy to store data
Both systems use a single, spiral track which runs from the centre of the disk to the edge
DVD uses Dual-Layering which increases the storage capacity (two individual recording layers)
Blu-ray Disks
Uses blue laser to carry out read and write operations
Wavelength of laser light is less than CD and DVD (stores up to five times more data than DVD)
Automatically come with secure encryption (prevent piracy and copyright infringement)
Used as back-up systems
Describe what is meant by virtual memory, how it is created and used and why it is necessary:
Pages of data are transferred between RAM and virtual memory when needed
Virtual memory is created when a computer temporarily uses secondary storage (a hard disk) to act as RAM.
Virtual memory will allow you to continue multitasking and accessing large files despite your RAM being limited or full.
This is the virtual memory diagram (must remember):
Without virtual memory, program 4 is unable to access the RAM and computer will crash
With virtual memory, one data will be removed from RAM into HDD/SSD, allowing other data accesses the RAM from HDD/SSD
After putting the data into HDD/SSD, virtual memory will now move the oldest data from RAM to the HDD/SSD to allow new data into the RAM.
This will continue until the RAM is no longer being over-utilized by competing programs running in the memory
The process above is also known as paging:
In computer OS, paging is the name given to the process of storing and retrieving data between a HDD/SSD and RAM.
A page is a fixed length contiguous (consecutive) block (unit of data) of virtual memory.
Paging is the key part how virtual memory works allowing data blocks move in and out HDD/SSD
Advantages:
Program can be larger than physical memory but still fully executed
No waste data
Reduce need of installing more expensive RAM
Disadvantages:
Secondary storage can’t have immediate access to CPU and need to pass through virtual memory -> increase workload
Thrash point :
Thrash point is achieved when most processes come to a stop because the computer is too busy dealing with virtual memory paging (moving data in and out of memory)
To prevent thrash point :
Getting more RAM
Using an SSD, not HDD
Having less programs running
Understand what is meant by cloud storage:
Cloud storage: a method of data storage where data is stored on offsite servers; the physical storage may be on hundreds of servers in many locations
Data will be saved in more than one server at the same time, in case of maintenance, clients still able to access the data. This is called data redundancy
Cloud storage can be accessed remotely in comparison to storing data locally
Physical servers and storage are needed to store data in cloud storage and it owns by a hosting company
Explain the advantages and disadvantages of storing data on the cloud in comparison to storing it locally:
Understand that a computer needs a network interface card (NIC) to access a network:
NIC: a hardware component (circuit board or chip) that is required to allow a device to connect to a network, such as the internet, it contains MAC
Understand what is meant by and the purpose of a media access control (MAC) address, including its structure:
Media Access Control address: unique number that identifies the device that is connected to the network or internet, usually made of 48 bits
MAC doesn't change when you change device’s location, can be represented by hexadecimal
It is a part of NIC (Network Interface Card)
Manufacturer's code is the unique part, if NIC was replaced, MAC will also replaced
There are two types of MAC: Universally Administered MAC Address, Locally Administered MAC Address
Reasons to change MAC address using LAA
To ensure they follow the correct formula
To bypass MAC address filter on a router or a firewall
To get past certain types of network restrictions
Understand what is meant by and the purpose of an internet protocol (IP) address and understand that there are different types of IP address:
Each device on the internet is given a unique address known as the IP address
32-bit number written in the form: 109.108.158.1
IP address gives the location of a device on the internet
IPv4 address is 32 bit numbers written in denary or hexadecimal and use (.)
IPv6 address is 128 bits and broken into 16 bit chunks and used (:)
Static IP address applied to :
Remote server of hosting websites
Online database
File transfer protocol
Describe the role of a router in a network :
Router: a device that enables data packets to be moved between different networks, for example, to join a LAN to a WAN
A router sends data to a specific destination on a network
A router can assign IP addresses
A router can connect a local network to the internet
4: Software
Describe the difference between system software and application software and provide examples of each:
System software:
Set of programs to control and manage the operation of computer hardware
Provides a platform on which other software can run
Required to allow hardware and software to run without problems
Provides a human computer interface (HCI)
Controls the allocation and usage of hardware resources.
E.g. Operating system (Microsoft Windows, macOS), BIOS, Device drivers, compilers, utilities software (software designed to carry specific tasks on a computer, this helps computer to manage, maintain and control computer resources), linkers (programs that files and compile it so it can run on computer)
Anti virus (utilities software):
Offered by operating system
Must be constantly updated
How they work:
The software is constantly running in the background
Check software of files before they are run and loaded
Compare a possible virus against a database of known viruses
Any programs or files which are affected by virus are put into quarantine
Defragmentation software (utilities software):
When the HDD is full, blocks used for files will be scattered over the disk surface. Data accessing will be faster if files could be stored in contiguous sector to reduce HDD head movements
For example, we have three files 1, 2, 3 store on track 8
Now file 2 is deleted and add some data into file 1, file 2 space will be vacant,
File 1 has now been extended to write data is sectors 10 and 11; now suppose file 3 is extended with the equivalent of 3 blocks of data;
this now requires filling up sector 9 and then finding some empty sectors to write the remainder of the data – suppose the next free sectors are on track 11:
A disk defragmenter will rearrange the blocks of data to store files in contiguous sectors wherever possible
Backup software (utilities software)
It is good practice to use the operating system system (programs that make a copy of file in case the original file is lost)
Allow a schedule for backing up files to be made
Total security:
Working version stored in SSD/HDD
Locally backup stored in removable SSD/HDD
Cloud storage
OS:
Microsoft Windows: file history
MacOS: time machine
Device drivers :
Software that connects the hardware with computer’s operating system to communicate together
Security software:
+ manages access control and user accounts (using user IDs and passwords)
links into other utility software, such as virus checkers and spyware checkers
+ protects network interfaces (for example, through the use of firewalls)
+ uses encryption and decryption to ensure any intercepted data is meaningless without a decryption key
+ oversees the updating of software (does the update request come from a legitimate source, for example).
Screensaver:
programs that supply moving and still images on the monitor screen after a period of inactivity by the computer
Virus scan
Distributed computing applications
Application software:
Allows a user to perform specific tasks using the computer’s resources
User can execute the software as and when they require.
Perform various applications (apps) on a computer
User can execute the software as and when they require.
E.g. powerpoint, word, excel
Describe the role and basic functions of an operating system:
Operating system:
The computer program responsible for the operation and smooth running of a computer
Functions of operating system:
Managing files: a file system is created to organise files and directories, which gives programs a consistent way to store and retrieve information
Handling interrupts:
An interrupt is a signal sent from a device or software to operating system
The interrupt signal causes the operating system to temporarily stop what it is doing and ‘service’ the interrupt.
The interrupt handler prioritizes interruptions as they are received, placing them into a queue as necessary.
Providing an interface: a user interface provides a way for the user to interact with the computer.
Managing peripherals and drivers: the operating system is responsible for controlling all the devices connected to the computer. It tells them how to interact and operate correctly. Device drivers are used to manage these connections.
Managing memory:
The OS is responsible for transferring programs to and from memory
It keeps track of memory usage, and decides how much should be given to each program
Managing multitasking: allows computer to carry out more than 1 task
Providing a platform for running applications: the OS runs programs, allowing them to function as designed
Providing system security: using user accounts, passwords and many utility programs, e.g. firewall to ensure the security of computer system
Managing user accounts:
Computers allows more than 1 user to log onto the system
Users’ data are stored in separate parts of the memory
Each account will have a set of username and password
Understand how hardware, firmware and an operating system are required to run applications software
When computer starts up, a part of the operating system is loaded in RAM
The start-up of the computer is handled by BIOS/Firmware
The firmware tells the computer system where the OS can be found on the hard drive, then loads the part of the OS needed and executes it
Firmware: a program that provides low level control for devices
Describe the role and operation of interrupts
An interrupt is a signal sent from a device or software to the OS
Can be caused by input/output process, software errors, hardware faults, user interaction
The interrupt causes the OS to temporarily stops what it’s doing to ‘service’ the signal
The interrupt handler is the part of the operating system which is responsible for dealing with interrupt signals.
The interrupt handler prioritizes interruptions as they are received, placing them into a queue as necessary.
For every interruption, the current task needs to be stopped, with its status saved (so it can resume later).
Software interrupts: an attempt to divide by zero, 2 processes trying to access the same memory location
Hardware interrupts: pressing a key on keyboard, moving the mouse
Explain what is meant by a high-level language and a low-level language, including the advantages and disadvantages of each
High-level language: written in a form that is close to human language, enabling programmers to just focus on the problem being solved.
Low-level language**:** used to write programs that relate to the specific architecture and hardware of a particular type of computer
Understand that assembly language is a form of low-level language that uses mnemonics, and that an assembler is needed to translate an assembly language program into machine code
Assembly language: low-level language that is used for developing code for specialist hardware, e.g. device drivers, that uses mnemonic codes
Assembler: translates an assembly language program into machine code
Describe the operation of a compiler and an interpreter, including how high-level language is translated by each and how errors are reported
Explain the advantages and disadvantages of a compiler and an interpreter
Explain the role of an IDE (integrated development environment) in writing program code and the common functions IDEs provide
An IDE is used by programmers to aid the writing and development of code. They are designed to bring together all programming tasks in 1 application; they offer a central interface with all the tools a developer needs. E.g. PyCharm, BlueJ
Code editor:
allows a program to be written and edited without the need to use a separate text editor.
speeds up the program development process, as editing can be done without changing to a different piece of software
Translator:
most IDEs provide a translator, can be a compiler or interpreter.
The interpreter is used for developing the program and compiler is used to produce the final version of the program to be used
Run-time environment:
the environment in which a program or application is executed.
It’s the hardware and software infrastructure that supports the running of a particular program/application in real time.
Error diagnostics:
errors are detected as the program code is being typed, alerts the programmer at the time
Auto-correction:
used along with error diagnostics, suggests correction when an error is detected
Prettyprint:
most code editors colour code in the program and lay out the program in a meaningful way - this is called prettyprint
Auto-completion:
code editors can offer context-sensitive prompts with text completion for variable names and reserved words
5: The internet and its use
Understand the difference between the internet and the world wide web:
The internet is the infrastructure, it relies on PHYSICAL infrastructure that allows individual devices to connect
The world wide web is the collection of websites and web pages accessed using the internet
Understand what is meant by a uniform resource locator (URL):
A URL is a text-based address for a web page; it can contain the protocol, the domain name and the web page/file name
Protocol:[http://]
Web server/domain name:[www.amongus]
Webname:[/sussy]
Filename:[/impostor.html]
Describe the purpose and operation of hypertext transfer protocol (HTTP) and hypertext transfer protocol secure (HTTPS):
It is a protocol, set of rules in order to access, transfer files across internet
HTTPS is more secure as it uses encryption methods like SSL/TSL
HTTPS have a padlock next to their URL
HTTP don't have a verification certificate but HTTPS do
Explain the purpose and functions of a web browser:
It is a software used to connect to the internet, translating the html code, ensuring SSL & TLS security can be established
Offers additional features like search history & ad blockers
Functions include:
storing bookmarks and favourites
recording user history
allowing use of multiple tabs
storing cookies
providing navigation tools
providing an address bar
Describe how web pages are located, retrieved and displayed on a device when a user enters a URL:
The user opens their browser and types in the URL and the browser asks the DNS server (1) for the IP address of the website.
In this case, let’s assume the DNS server can’t find the URL, the DNS server (2) finds the URL and can map it to the IP address is sent back to the DNS server (1) which now puts this IP address and associated URL into its cache/database.
This IP address is then sent back to the user’s computer.
The computer now sets up a communication with the website server and the required pages are downloaded. HTML files are sent from the website server to the computer. The browser interprets the HTML, which is used to structure content, and then displays the information on the user’s computer.
Explain what is meant by cookies and how they are used, including session cookies and persistent cookies:
A packet of information sent by a web server to a web browser, generating each time the user visits the website
Every time a user visits a website, cookies will have collected some key information about the user. It checks if any cookies has available before, if yes, browser will read and regain the data
Session cookies :
Store in memory and not written on the disk
It remains when browsers remain active, if browser shut down, cookies will vanish
Persistent cookies:
Authenticate with the web browser
Store on hard drive, if browser shut down, cookies will not vanish
How cookies works:
User request to login the websites
Web server sends cookies back to the user’s browser
Persistent cookies stored on hard drive, session cookies will be deleted after the websites shut down
If user login again, web server checks and identifies persistent cookies stored on user's computer and match the data on the webpage
Understand the concept of a digital currency and how digital currencies are used:
A digital currency is money that only exists electronically, no physical form
Digital currency relies on a central banking system
The problem is centralisation is maintaining confidentiality and security. To fix this, they might use cryptocurrency by using decentralisation:
Cryptocurrency uses cryptography to track transactions, address with the problem associating with centralisation
Has no state control and control by the cryptocurrency community itself
Transactions are publicly available => can track the amount of money.
Work by being a blockchain
Understand the process of blockchain and how it is used to track digital currency transactions:
Blockchain, in its basic form, is a digital ledger, that is a time-stamped series of records that cannot be altered
How it works:
When a new transaction takes place, a block is created
A new hash value is created each time a block is created. This hash value is unique and it includes a timestamp, which identifies where the actual events take place and also the hash value of the previous block. This means the data will not be deleted.
Block 1 is called the genesis book since there isn't any block. Block 2 will change the hash ( this is applied to all the other blocks). When a new transaction takes place, this means all networks' computers will have a copy of the transaction; therefore, it can't be changed unless requesting all the computers -> prevent tampering (e.g: hacking)
The decentralized database managed by multiple database is called Distributed Ledger Technology (DLT)
Blockchain can be used in voting records, medical records, land records, smart contracts,...
To prevent the fact that a new chain is created without knowing the problem of the previous chain, a method proof-by-work is used to check the chain for 10 minutes for each block before adding to the chain. The miners is specialised users will get commission for checking
Describe the processes involved in, and the aim of carrying out, a range of cyber security threats:
Brute force attack:
If a hacker wants to ‘crack’ your password, they can systematically try all the different combinations of letters, numbers and other symbols until eventually they find your password.
To prevent :
Check if the password is common or not
Use strong password, strong word list
Use programmes that generates strong password
Data interception:
A form of stealing data by tapping into a wired or wireless communication link. The intent is to compromise privacy or to obtain confidential information
Interception can be carried out using a packet sniffer, which examines data packets being sent over a network. The intercepted data is sent back to the hacker.
WiFi data interception can be carried out by wardriving.
To prevent :
Encryption of data
Use wired equivalent privacy (WEP) encrypted protocol
Firewall
Having complex password for wireless route
Not connect to public wifi that is free
Distributed Denial of Service (DDoS) attacks:
An attempt at preventing users from accessing part of a network, notably an internet server.
This is usually temporary but may be a very damaging act or a large breach of security. It doesn’t just affect networks; an individual can also be a target for such an attack.
One method of attack is to flood the network with useless spam traffic (numerous access to one webpage at the same time)
Attacker me be able to prevent user from:
Accessing their emails
Accessing websites
Accessing online services
To prevent:
Using an up to date malware checker
Firewall
Email filter, spam
Hacking:
The act of gaining illegal access to a computer system without the user’s permission.
This can lead to identity theft or the gaining of personal information; data can be deleted, passed on, changed or corrupted.
To prevent:
Anti hacking
Firewall
Strong password, not download suspicious app
Malware:
Any malicious software, biggest risk of the computer
Keep all software, including operating system, up to date
Don’t download from unknown websites
Be careful when opening email attachments
Don’t click on pop ups
Keep web browser security level medium or higher
Use anti- malware app and multiple option to prevent
Virus:
A program or code that replicates itself; designed to amend, delete or copy data or files on a user’s computer;
Often causes the computer to crash or run slowly
Could stop hardware from being able to communicate; could spread to other devices on a network
To prevent :
Anti virus software
Not download suspicious app, be careful when opening email
Worms:
A type of stand-alone malware that can self-replicate.
Their intention is to spread to other computers and corrupt whole networks;
Unlike viruses, they don’t need an active host program to be opened in order to do any damage.
To prevent:
Anti virus software
Not download suspicious app, be careful when opening email
Trojan horse:
A program which is often disguised as legitimate software but with malicious instructions embedded within it.
A Trojan horse replaces all or part of the legitimate software with the intent of carrying out some harm to the user’s computer system.
The Trojan horse will give cyber criminals access to personal information on your computers
To prevent:
Not download suspicious app, be careful when opening email or webpages
Firewall, security systems
Spyware:
Software that gathers information by monitoring all the activity on the computer, the gathered data is sent back to person who sent the app
To prevent:
Anti-software application
Set alarm of weakness
Firewall
…
Adware:
Software that floods the computers with unwanted advertising, usually form as pop ups but can frequently appear in the browser website that can redirect to a fake website which contains promotional adverts
It can spot the weakness, hard to remove, hijack the browser
To prevent :
Not clicking the suspicious ad
Firewall
Anti-advertisement app
Ransomware:
Programs that encrypt the data on a user’s computer; a decryption key is sent back to the user once they pay a sum of money (a ransom)
Often sent via Trojan horse or by social engineering
To prevent:
Be careful with paying money
Prevent clicking
Phishing:
Creator sends out a legitimate-looking email; as soon as recipient clicks on link, user is sent to a fake website and they will ask to login some personal information
Spear phishing is when there is a specific target
To prevent:
Many ISPs filter out phishing emails
User should be cautious
Anti-phishing toolbar
Look for green padlock symbol
Check if any spelling or the source of email
Pharming:
Malicious code installed on a user’s hard drive or on the web server, code will redirect the user to a fake website
Creator of malicious code can gain personal data; bank account
Can lead to fraud or identity theft
To prevent :
Some anti-spyware can identify and remove pharming code from hard drive
User should be alert
Anti virus, firewall
Social engineering:
A cybercriminal creates a social situation that can lead to a potential victim dropping their guard.
It involves the manipulation of people into breaking their normal security procedures and not following best practice.
Explain how a range of solutions are used to help keep data safe from security threats:
Access level:
User accounts control a user’s rights. This often involves having different levels of access for different people.
When using databases, levels of access are particularly important; it is essential to determine who has the right to read, write and delete data
Four level :
public access (this refers to the data anyone from the general public can access)
friends (only people identified as ‘friends’ by the owner of the data can see certain data)
custom (this allows the user to further refine what data can be seen by ‘friends’ allowing them to exclude certain content from selected people)
data owner (this is data only the owner of the data can see).
Anti - malware:
Anti - virus:
Chapter 4
Anti-spyware:
Based on 2 two method:
Rules- look for typical features which are associated with spyware, identify potential security threats
File structures - Certain file structure that associated with spyware
Detect and remove spyware that are already installed on device
Prevent user downloading spyware
Encrypt files to make data more secure
Block access to user's computer or webcam
Authentication :
ability user can prove who they are, there are numerous way to authenticate:
Passwords and username:
Use to restrict the access to data or system when access email, banking, social networking sites
Biometrics:
type of authentication that uses a unique human characteristic, such as fingerprints, voice or retina blood vessel pattern
Retina scan:
Use infrared to scan the retina in the eyes
The scanned data is sent via an ADC (analogue-digital converter) to a microprocessor.
The microprocessor compares the data received with retina scan data already stored in a database.
If the two sets of data match, a signal is sent to turn a light from red to green and also unlock the security door.
The door is controlled by a DAC (digital-analogue converter) and an actuator.
Two step verification:
To improve security, an eight-digit PIN (called a one-time passcode) is sent back to her either in an email or as a text message
Mostly for purchasing online
Automatic software updates:
These updates are vital since they may contain patches that update the software security (to protect against malware) or improve the software performance (for example, removal of bugs and addition of new features).
Checking the spelling:
The email address
Tone of email and bad spelling words
Misspelling domain name, known as typosquatting
Suspicious links
Plain mistakes spelling
Firewalls:
sits between the user’s computer and an external network (internet) and filter information in and out of the computer
Tasks carried out by firewall:
Examining ‘traffic’
Checking whether incoming or outgoing data meets criteria
If data fails the criteria, the firewall blocks ‘traffic’
Firewall can keep a list of all undesirable IP addresses
Helping to prevent viruses or hackers entering the user’s computer
Proxy servers:
Act as an intermediary between the user and a web server
Functions of proxy servers:
Allowing the internet ‘traffic’ to be filtered
By using cache, they can speed up access to information from a website
Keeping the user’s IP address secret
Acting as a firewall
Privacy control :
The controls available on web browsers, social networks and other websites that are designed to limit who can access and see a user’s personal profile.
Functions of privacy control:
Do not track setting to stop websites collecting the user browsing data
Check to see if financial detail has been saved so the next time, user doesn't need to re-type the financial details (prevent data interception)
Safer browsing and alert
Prevent pop-ups
Can switch off the sharing of location
Secure socket layer (SSL):
Type of protocol that allows data to be sent and received securely over the internet
When a user logs onto a website, SSL encrypts the data
https or padlock in the status bar
When user wants to access a secure website:
User’s web browser sends a message so it can connect with required website which is secured by SSL
Web browser requests that the web server identifies itself
Web server responds by sending a copy of its SSL certificate
Web browser checks if certificate is authentic
Sends signal back to web browser
Starts to transmit data once connection is established
If not secure, browser will display an open padlock
6: Automated and emerging technologies
Describe how sensors, microprocessors and actuators can be used in collaboration to create automated systems
Automated system: a combination of software and hardware that is designed to work automatically without the need of human intervention
Input devices, usually sensors, send data readings to the microprocessor (computer) at set intervals
To be understood, this data may have to be converted using an ADC (analogue to digital converter)
The microprocessor compares the data readings against pre-set values that it has stored (using a control program)
The microprocessor then makes a decision as to whether any action is needed (e.g. is more heat needed to maintain the pre-set value?)
If needed, the microprocessor will send a signal to instruct an output device to do something (e.g. turn on heater, turn off oxygen pump etc)
This may involve an actuator (e.g. a motor to open the gates or shop doors)
This process repeats in a continuous loop
Describe the advantages and disadvantages of an automated system used for a given scenario
Industrial:
Advantages:
Much faster than a human operator to take any necessary action
Much safer - keeps humans away from potentially dangerous environment
Higher productivity
More efficient use of materials
Less expensive in the long run
Disadvantages:
Expensive to set up
Maintenance needed, which can be expensive
The system is subject to cyberattacks
Transport:
On-board sensors and cameras gauge the size of any parking spaces, and alerts the driver if a suitable space is available
The driver then selects auto-parking and the on-board computer takes over
Actuators are used to operate the steering track, brakes and throttles under control of the computer
Advantages:
Allows the same number of cars to use fewer parking spaces
Avoids traffic disruption in cities
Fewer dents and scratches to the cars
Consistent results
Disadvantages:
Over-reliance → loss of skills
Faulty/dirty sensors or cameras can send false data to on-board computer which may lead to malfunction
Expensive
Requires additional maintenance
Agriculture:
Data from automatic weather station is received by controller
Water level sensors are used to measure level of water in irrigation channels
Data is sent back via wireless transmitters
Data is picked up by wireless receiver, which sends data to controller
The controller uses data to decide whether to start the water pumps or not
This is done by sending signals to actuators, which operate the pumps
Although the system is automatic, a supervisor remotely monitors the processes and can make changes to the controller if needed
Advantages:
Reduced labor costs
Better and more efficient control of irrigation processes
Better control of resources
Faster response than humans
Disadvantages:
Expensive to set up
High maintenance costs
Weather:
The data from sensors is sent to microprocessor, any calculations are then done
The data from sensors and the calculated values are then stored on a central database
Advantages:
Save labor
Gather information from remote areas
Consistent and error free
Disadvantages:
Expensive to set up
High maintenance costs
Removes the observer from real experience
Gaming
Gaming devices include the use of:
Accelerometers: measure acceleration and deceleration
Proximity sensors: used in smart touch pads, can detect hand/finger position
Advantages:
Increase human interaction with the game
Allows players to take actions that simulate real events happening → a more immersive experience
Disadvantages:
Can become outdated faster than PCs
May not be able to run newer games
Lighting:
As it becomes dark, the light sensor value will change, and the microprocessor will send signals to the interface to control the array of LED lights
Data from infrared sensor would also be used as a security device when the house is unoccupied
Advantages:
Reduced energy consumption
Control light sources automatically
Wireless connection can be used → safer
Disadvantages:
Expensive to set up
More maintenance required → expensive
Science:
The level sensors measure how much liquid is being added from ‘A’
This data is sent to microprocessor
The microprocessor controls the opening and closing of tap in A
This is done by sending actuator that operates the tap
Advantages:
More consistent results
Less dangerous
Fewer staff needed
Faster results
Disadvantages:
Less flexible than when using human technicians
Can be expensive to set up
Understand what is meant by robotics:
Robotics is a branch of computer science that brings together the design, construction and operation of robots.
E.g.
In factories:
Welding parts together
Spray-painting panels on a car
Fitting windscreens to cars
Cutting metals
In the home:
Autonomous floor sweepers
Autonomous lawn mower
Ironing robots
Automatic window cleaners
Drones
Can be used to film/take photographs
Can be used to make parcel deliveries
Describe the characteristics of a robot:
3 main characteristics:
a mechanical structure or framework
electrical components, such as sensors, microprocessors and actuators
Programmable
In details:
Ability to sense their surroundings: (electrical components, such as sensors, microprocessors and actuators)
Done via sensors
Recognise intermediate environments and give its ability to determine objects
Have a degree in movements (a mechanical structure or framework )
Wheels and gears to carry out movements
Mechanical structures made of many parts
Contain electrical impulses and make use of end effectors (different attachments for specialized movement)
Programmable :
Controller determines action to be taken from the sensors
Allow robot to do specific tasks
IMPORTANT:
Many robots don’t possess Artificial Intelligence (AI) as they do repetitive tasks rather than adapt to human characteristics (unable to think by themselves)
Not confuse physical robots and software robotics, such as :
Searching engine bot or WebCrawlers ( these are used for scanning websites and categorizes them)
Chat bot ( conversation with web users like Chat GPT)
Independant robots:
have no direct human control (they are said to be autonomous, for example, an autonomous vehicle)
can replace the human activity totally (no human interaction is required for the robot to function fully)
Dependant robots:
have a human who is interfacing directly with the robot (the human interface may be a computer or a control panel)
can supplement, rather than totally replace, human activity (for example, in a car assembly plant where both humans and robots work together to produce a car).
Understand the roles that robots can perform and describe the advantages and disadvantages of their use:
Industry:
E.g: paint spraying of car bodies, welding bodywork of cars, manufacturing microchips, …
The control of robot is either through embedded, built in microprocessors or directly linked to the computer system
The robot is programmed with a sequence of instructions which allows it to carry out the series of tasks
Human operator will carry out the tasks manually and robot knows how to carry the task
Equipped with sensor to detect and gather information about surroundings and prevent doing stupid things
Good at repetitive tasks, however if there are specialist tasks, human is better
Medicine:
Uses in surgical procedures, which is safer and quicker
Monitoring patients to doing actual mini surgery
Highly hygiene
Take blood sample -> less painful and safer, more hygiene that human
Microbots in target therapy, so drugs or other therapy could get to the target site causing less damage to surrounding tissue
Prosthetic limbs are now mini robots in their own rights
Bionic skins and neutral implants that interface with human nervous system giving feedback to allow control the limb better
Domestic robot:
Use in household
Autonomous vacuum cleaner uses proximity sensor and camera to avoid obstacle and cover the whole room quickly
These robots have microprocessor to control the overall action
Actuators are used to allow motor to control movement
Autonomous grass cutter ( mowers) uses proximity sensor and camera to avoid obstacle and cover the whole room quickly
These robots have microprocessor to control the overall action
Actuators are used to allow motor to control movement
Personal assistant (vectors) is controlled by microprocessor and use cloud connectivity to connect to the internet
Able to understand voice command
Use HD camera and proximity sensor to recognise human faces and navigate in the room
Transportation:
Autonomous car and buses:
Use sensors, cameras, actuators, and microprocessor to carry actions
Sensors allows to control and perform critical movements by sensing the dynamic conditions on the road
Microprocessors process data received from cameras and sensors and send signal to actuators to perform physical actions such as: change gear, apply brakes, turning steering wheels
Cameras catch visual data from the surroundings, while radar and ultrasonics allow the vehicle to build up a 3D image of its surrounding
Since the traffic light shows red, or pedestrian, the microprocessor must send signals to actuators to apply brakes and put the gear into ‘park’.
Constant monitoring must take place until the light changes to green.
When this happens, the microprocessor will again instruct actuators to put the car into first gear, release the brakes and operate the throttle (accelerator).
Autonomous train:
make use of a system called LiDaR (Light Detection and Ranging);
LiDaR uses lasers which build up a 3D image of the surroundings.
Other sensors (such as proximity sensors on train doors) and cameras (including infrared cameras) are all used for various purposes to help control the train and maintain safety.
Makes use of global positioning satellite (GPS) technology, which allows accurate changes in speed and direction to be calculated.
actuators control the train’s speed, braking and the opening and closing of the train doors.
Autonomous airplanes:
sensors to detect turbulence to ensure smooth flights
an increase in self-testing of all circuits and systems
sensors that would automatically detect depressurisation in the cabin; thus
allowing for quick stabilisation of the airplane
use of GPS for navigation and speed calculations
use of actuators to control, for example, throttle, flaps (on the wings) and the rudder.
Agriculture:
Harvesting and picking:
Designed to do this labor-intensive work; they are more accurate and faster
Higher yields and less waste
Use a camera to scan and arm for removing vegetables, fruit, …
Weed control:
Distinguish weed and crop
Use GPS tracking to stay on course to move along the rows of vines and remove the weeds;
A weed removal blade is operated by an actuator under the control of the controller (microprocessor) in the robot
A drone is used first to collect data and aerial view of the yards
Phenotyping:
the process of observing physical characteristics of a plant in order to assess its health and growth
Sensors to produce 3D images of plant to monitor health and growth, machine learning used to see the condition of leaves
Faster and more accurate than human
Seed - planting drones and fertilizer distributors:
drones (flying robots) can produce an aerial image of a farm sending back a ‘bird’s eye view’ of the crops and land
they allow seed-planting to be done far more accurately
they also allow for more efficient fertiliser-spreading to reduce waste
and improve coverage
drones can also be used in cloud seeding where the drone can add silver iodide crystals to a cloud forcing it to give up its rainwate
the drones use a very complex camera system to target seeding and allow fertiliser spraying.
Autonomous agricultural devices:
grass mowers/cutter
weeding, pruning and harvesting robots
seeding robots
fertilizer spraying
All of these devices use sensors and cameras to go around obstacles, or they can even be programmed to ‘go to sleep’ if the weather turns bad.
Understand what is meant by artificial intelligence (AI):
AI is a branch of computer science dealing with the simulation of intelligent behaviors by computers
Describe the main characteristics of AI as the collection of data and the rules for using that data, the ability to reason, and can include the ability to learn and adapt:
The main characteristics of AI as the collection of data and the rules for using that data, the ability to reason, and can include the ability to learn and adapt
There are three types of AI:
Inductive reasoning: ability to draw reasoned conclusions based on given data/situations. Use patterns to arrive a conclusion
Deductive reasoning: a number of correct facts are built up to form a set of rules which can be applied to others problems. This uses rules, facts, definitions, property to give a conclusion
Examples of AI:
News generation based on live news feed
Smart home devices (Alexa, … ):
Interacts and learn from human voices and the data received, becoming increasingly sophisticated and responsive; able to learn repetitive tasks ( this is deductive learning)
Chatbot:
Interact with human through instant messages, artificially replicating patterns of human interactions using AI to respond the messages
Autonomous cars:
Above
Facial expression recognition:
Algorithms identify key facial landmarks (e.g: eyebrows, nose, .. )
A combination of this landmarks will identify the expressions
Explain the basic operation and components of AI systems to simulate intelligent behavior:
Expert systems have a knowledge base, a rule base, an inference engine and an interface.
It mimics the decision-making ability of human
Use AI to stimulate the human or organization that has expert knowledge and experience
Use of expert systems:
oil and mineral prospecting
diagnosis of a patient’s illness
fault diagnostics in mechanical and electronic equipment
tax and financial calculations
strategy games, such as chess
logistics (efficient routing of parcel deliveries)
identification of plants, animals and chemical/biological compounds.

Use interface:
Method that system interacts with a user
Interactions can be dialogue boxes, command prompts, or other input methods
Question being asked is Yes/No answer
Inference engine:
Main processing element of the experting system
Act like search engine: examining knowledge base for the information/ data that match the queries
Asking a series of questions and applying response
Problem solving part that make use of inferences rule and rule base
Since knowledge base is a collection of objects and attributes, he engine attempts to use information gathered from the user to fine an object matches
Knowledge base:
Repository of facts
Stored all the knowledge about an area of expertise obtained from a number of resources
A collections of objects and attributes
Rule base:
Set of inference rules
Used by inference engine to draw conclusions (method closely to human reasoning)
Use logical statement, mostly “IF” statements:
For example:
IF continent = “South Africa” AND language = “Portuguese” THEN country = “Brazil
Advantages:
Improve decisions quality
Cheaper
Maintain the significance of information
How to set up ?
Information needs to be gathered from human experts or written sources
This information will be used to create knowledge base
A set of rules need to be created, making inference rules, so that the searching engine can draw conclusions.
User interface needs to be developed to allow the user nd the expert team to communicate
Once the system is set up, it needs to be fully tested
Machine learning is when a program has the ability to automatically adapt its own processes and/or data:
Training computers with sample data so they can make prediction on new or given data without any specific programs
Able to learn without following explicit instruction by using algorithms and statistical models to analyses and draw interface
Computers can make predictions or take decisions based on previous scenarios
Computers can offer fast and accurate outcomes
Can be applied to:
Computational finance
Computer vision
Computational biology
Natural language response
THE END OF THEORY
Paper 2 : Algorithms, Programming, and Logic
Understand the program development life cycle, limited to: analysis, design, coding and testing:
analysis: abstraction, decomposition of the problem, identification of the problem and requirements
design: decomposition, structure diagrams, flowcharts, pseudocode
coding: writing program code and iterative testing
testing: testing program code with the use of test data
Understand that every computer system is made up of subsystems, which are made up of further sub-systems:
A computer system is made up of software, data, hardware, communications and people;
Every computer system is made up of subsystems, which are made up of further sub-systems.
Top-down design is the decomposition of a computer system into a set of sub- systems, then breaking each sub-system down into a set of smaller sub-systems, until each sub-system just performs a single action.
Understand how a problem can be decomposed into its component parts:
inputs – the data used by the system that needs to be entered while the system is active
processes – the tasks that need to be performed using the input data and any other previously stored data
outputs – information that needs to be displayed or printed for the users of the system
storage – data that needs to be stored in files on an appropriate medium for use in the future.
Use different methods to design and construct a solution to a problem:
Structure diagram:
Structure diagrams can be used to show top-down design in a diagrammatic form.
Structure diagrams are hierarchical, showing how a computer system solution can be divided into subsystems with each level giving a more detailed breakdown.
If necessary, each sub-system can be further divided.

Flowcharts:
Shows diagrammatically the steps required to complete a task and the order that they are to be performed. These steps, together with the order, are called an algorithm
Pseudocodes:
