Unit 6.1 Data Security
Aims
Understand the difference between security, privacy and integrity of data.
Understand the different cybersecurity threats that computer systems face and the measures that can be taken to defend against these.
Data Security
Protecting computers? consider:
Security - measures taken to protect computer system/network/data from unauthorised access/attacks/breaches.
Privacy - Rights and regulations surrounding collection/use/dissemination of personal info/sensitive data.
Integrity - accuracy/consistency/reliability of data
NEED TO SECURE BOTH DATA & COMPUTER SYSTEM!!
Cyber Threats
Malware
Software containing malicious code that damages computer systems and files, it can get on by
Attaching itself to email attachments
Phishing by influencing the user to download files that appear genuine
Visiting untrustworthy websites
Exchanging memory sticks between users.
Malware Types
Virus - Corrupt data/delete files/disrupt computers operations or simply annoy, needs a user action to spread e.g. sending infected files by email or memory stick
Computer Worm - Similar to virus but can spread on its own
Spyware - software that gathers info about users activities e.g browsing history and keystrokes
Trojan Horse - Software pieces that look genuine to users, when opened run malicious code that can damage computer systems.
Ransomware - Software that encrypts users computer so it cant be accessed, user asked to make a ransom payment in exchange for restoring files.
Malware can be stopped by Anti-Virus or Anti-Malware software
Hacking
Can be stopped by using usernames, passwords and firewall software
White-Hat | Grey-Hat | Black-Hat |
Hacker needs permission | Operate between White & Black-Hat | Hacker doesn’t have permission |
Uses skills to ID vulnerabilities in the organisations system and reports these back | May choose to hack without permission but still report to organisation to help improve their security | Exploits computer system for personal gain e.g. make profit |
Follows ethical guidelines and standards | May choose to hack without permission but not carry out malicious actions | Doesn’t follow ethical guidelines or standards |
Phishing
Way of gaining sensitive info by influencing people to give it away illegally e.g. name/address/bank details etc. e.g. phone by impersonating employee or email impersonating business with a link to form.
Once info obtained may be used for malicious purposes
Can be stopped by:
Not opening/responding to email from unknown sources
Blocking email address
Pharming
Malware used to direct user from genuine to fake website without knowledge/consent where they then enter personal info.
Measures to Protect Computer Systems
User Accounts
Set of credentials given to user who has authorised access to computer/network
Usually paired with password/other authentication
Users can have different access levels
Passwords
Set of characters used to verify/authenticate user identity
Usually paired with User Accounts
Strong passwords important! General rules:
8 char min,
Mix of no/lower/uppercase
Special symbols
Don’t include personal details
Change regularly (every 2-3 months)
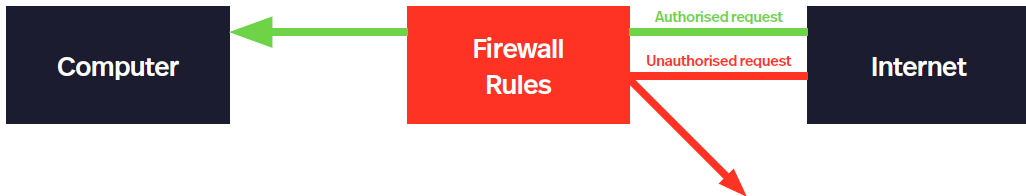
Firewalls
Software that checks all incoming traffic from pc/network before it reaches computer
(Settings based) blocks access to source if it detects unauthorised access
Examines all requests made externally e.g. websites visited and compares them against allowable rules list, if its in its allowed access, if then blocked
Anti-Virus
Software that runs in the background virus checking by:
Signature Detection - scans every single data/request accessing pc and compares data/request against known virus database
Heuristic Analysis - analyses behaviour of files to ID previously unknown virus without signature, see if it acts maliciously e.g. deleting files
If a Virus is detected:
Quarantines - isolates virus so it cant spread and do further damage
Repairs - attempts to disinfect the infected files by removing malicious code
Deletes - if it poses significant risk to PC it deletes the virus
Alert User - tells user about virus and actions taken to handle the virus.
Needs to be updated frequently so database is updated and it can detect new viruses

Anti-Spyware
Works similarly to Anti-Virus by scanning files to ID traces of spyware/unwanted programs and matches these against known spyware signatures/behaviours
Then removes/quarantines files, Anti-Spyware also needs to be updated regularly (same as Anti-Virus reason)
Encryption
Encoded (scrambled) data so it cant be easily understood, should be encrypted when:
Being transmitted - includes over the internet & over wi-fi network
Being stored - actual storage device used to store data, adds extra security in case someone else accesses it physically.
Type Symmetric Encryption Asymmetric Encryption | ||
Key amounts | One Key | Two keys |
Key types | Single key to Encrypt & decrypt | 1 Encryption (Public) key and 1 Decryption (Private) key |
How it works | Both parties need to know the key. (Rarely used for sensitive info) | Public key exchanged between sender/recipient, public key encrypts then recipient decrypts data with private key. |
Secure? |
|
|
Authentication
Able to confirm identity of person
Type What is Input Example | ||
One Factor | Something you know |
|
Two Factor (AKA MFA) | Something you have |
|
Three Factor (AKA MFA) | Something you are |
|
Digital signatures can verify authenticity of digital message sent by known sender to know its not been altered.
To create digital signature, sender uses cryptographic algorithm and their private key to generate unique digital signature.
Recipient can verify by using senders public key, typically available to anyone who wants to verify
Biometrics can also be used to verify ID e.g.
Fingerprint recognition - capture fingerprint patterns using special scanners, then they are analysed.
Facial recognition - uses algorithms to analyse facial features e.g. eye distance, nose & mouth
Voice recognition - analyse unique characteristics of a voice, including pitch, tone, pronunciation.
Access Rights
Allows different groups/users to access/denied specific parts of network
Access Rights include: Read, Write, Delete & Create