NIST Framework Summary
What does the NIST Framework do?
NIST Framework aims to provide a cost-effective, high performing, reliableand flexible cybersecurity framework which reduces and manages potential risks to critical infrastructure.
Intended to be used to complement an organizations current system.
Can serve as a foundation for new cybersecurity programs.
NIST Framework provides:
A description of an organizations current cybersecurity management and practices.
A description of their target state.
Continuous and repeatable improvements.
Feedback on an organizations cybersecurity progression.
A easy method to communicate with stakeholders.
How does the NIST Framework function?
NIST Framework Structure
The framework is broken up into 3 sections which enhance cybersecurity resilience:
1. Core
The Core provides a set of industry standards, guidelines and practices.
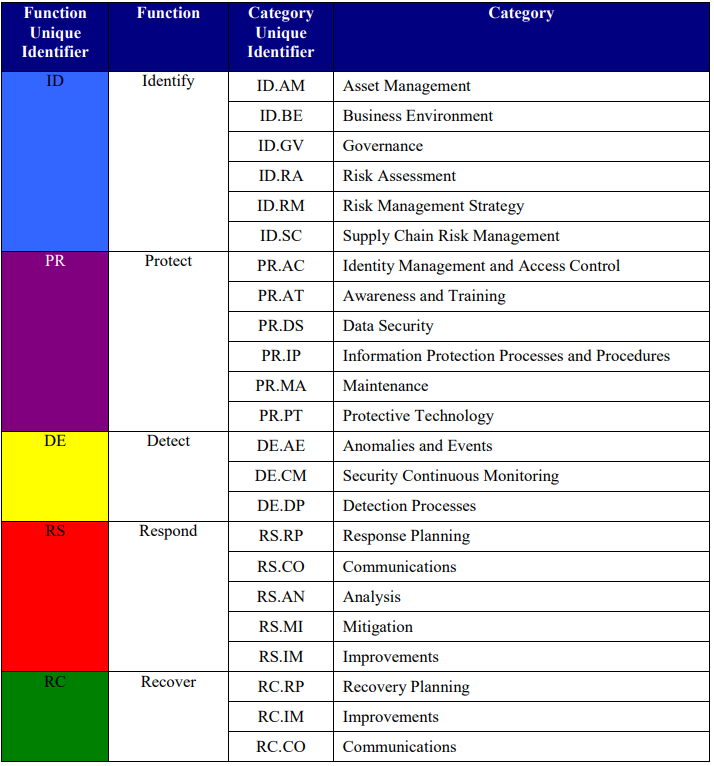
This is broken up into 4 main categories:
Functions
There are 5 functions which are used to provide a structured approach when managing cybersecurity risks.
Identify - Understand what needs to be protected (E.g., critical infrastructure, assets, system data).
Protect - Develop & implement safeguards to minimize and manage risks. (E.g., security controls, policies).
Detect - Develop & implement a solution to identify the occurrence of a cybersecurity risk.
Respond - Develop & Implement a methodology to combat the risk.
Recover - Maintain and restore the effect of the risk. (E.g., data back-ups)
Categories
Categories are a subsection of the functions which refer to specific cybersecurity outcomes associated with one of the five functions.
For instance, the Identify function has a variety of categories such as Asset Management, Risk Assessment, and Business Environment.
Sub-categories
Categories are broken down further into Sub-categories. This allows different aspects of each Category to be covered in more depth.
For instance, the Protect function has a Category called Data Security and examples of Sub-categories which belong to Data Security would be Encryption, Data-loss prevention and Access Controls.
Informative References
Informative References are external resources outside of the organization which help to provide additional information on a sub-category. The information included can vary from industry standards to research publications.
High-Level View of Framework Core Structure
2. Implementation Tiers
Framework Implementation Tiers are used to identify an organization’s current cybersecurity risk management and prevention. They also set an expectation of how risks should be managed.
There exist 4 tiers which categorize an organizations current standing:
Note: The degree of rigor in cybersecurity management is measured by 1 being the worst and 4 being the optimal level of competence.
Tier Number | Tier Name | Characteristics |
|---|---|---|
1 | Partial |
|
2 | Risk-Informed |
|
3 | Repeatable |
|
4 | Adaptive |
|
3. Profiles
Framework Profiles are used to act as a organizations roadmap by showing outcomes and objectives achieved. There exist two types, Current and Target profiles.
The Current profile represents an organizations current outcomes and objectives achieved by their risk management plan.
A Target profile is the organizations goal outcomes and objectives.
A current profile is created by conducting a risk assessment, taking into account the objectives, Categories and Subcategories. By creating goals to strive for and outcomes that should be achieved a target profile can also be created.
By comparing the current and target profiles it reveals potential gaps and allow for cost-effective continuous improvements via self-assessment.
Examples of the NIST Framework being applied
The NIST Framework can be applied to various scenarios due to its flexible nature. Here are some examples listed with scenarios to show how it can be utilized.
Communicating with Stakeholders
Current profiles convey the organizations current capabilities and outcomes
Target profiles express the requirements expected of an organization from the stakeholder
Target profiles can be used as baseline profile for critical infrastructure users
Allows the stakeholder to understand the organizations cybersecurity risk management
Cyber Supply Chain Risk Management (C-SCRM)
C-SCRM is the process of identifying, mitigating and managing cybersecurity risks within a supply chain
To manage risks profiles can be used to set expectations of partners to meet an organizations outcomes.
Identify threats using Functions and Categories
Buying Decisions
Organizations can evaluate a product or services value or necessity by comparing its outcomes to the Target profile.