
1.1 Explain concepts related to the Open System Interconnection (OSI) reference model.
1.1 Compare and contrast the Open Systems Interconnection (OSI) model layers and encapsulation concepts
OSI Model
Concepts You Need To Know
Layer 1 - Physical
Layer 2 - Data Link
Layer 3 - Network
Layer 4 - Transport
Layer 5 - Session
Layer 6 - Presentation
Layer 7 - Application
Data encapsulation and decapsulation within the OSI model context
Ethernet Header
Internet Protocol (IP) Header
Transmission Control Protocol (TCP) / User Datagram Protocol (UDP) headers
TCP Flags
Payload
Maximum Transmission Unit (MTU)
How does data on a network (or on the Internet) get from one point to another?
There are seven layers:
Layer 1 - Physical
Layer 2 - Data Link
Layer 3 - Network
Layer 4 - Transport
Layer 5 - Session
Layer 6 - Presentation
Layer 7 - Application
So, a device or program on the Application layer creates content and addresses it to a device on the Application layer at the other side. It gives this content to a device Presentation layer, which packages it, addresses it to the device in the Presentation layer on the other side, and sends it a device on the Session layer. This goes on until we get to the Physical layer.
Layer 7 - Application Layer
You want to send an e-mail. The Layer 7, Application Layer is the software that a user sees (Microsoft Word, Google Chrome etc). You type up the e-mail in Microsoft Outlook and send it off. But what is really happening.
Layer 6 - Presentation Layer
Layer 6 is the presentation Layer. It takes the data from Layer 7 and makes sure that the Application layer of the recipient can understand it. What if the recipient’s computer has a Mac or Unix operation system? What if the user doesn’t use HTML to display e-mails? What if the user’s computer is in a different language?
If you open the same e-mail on your phone, or tablet, or 24” monitor, it will look different. The Presentation Layer on each device understands the capabilities of that device and translates the gibberish into a format that is suitable for its application layer.
Layer 5 - Session Layer
What is a Session? A session is when two devices agree to communicate with each other for a period. When you send the e-mail, your computer calls up the receiving computer and says, “hey, I want to send you an e-mail”. The two computers use the session to exchange data and keep it open until one or both decide to close it.
Layer 4 - Transport Layer
Takes the data from the Session Layer and packages it or breaks it into pieces. So, it might cut up your e-mail into chunks, give each one a number, and send each chunk separately to the recipient. The recipient has already agreed to receive these chunks because it has an established session. The Transport Layer on the other side would put them back 38 together in the correct order. If some of those chunks don’t show up, the sending Transport Layer can send them again. The Transport Layer also puts the IP address of the recipient on each chunk
Layer 3 - Network Layer
Responsible for the routing and forwarding of data packets across different networks.
Primary function - determine the best path for data to travel from the source to the destination
Uses Logical Addressing such as IP addresses to identify devices on a network.
Say you are in New York City and you are sending an e-mail to a device in Los Angeles. Layer 4 put the IP address of the recipient on each “chunk”. How does the data get to the destination? Throughout the internet are many routers and many cables. So, there are many pathways for data to get from NYC to LA. The router in your office looks at the destination IP address and decides about the next router to send the e-mail to (probably the main NYC router for your ISP). That router receives the data and makes its own decision sending it to a router in California. A main router in California sends the data to a router in LA. Finally, a router in LA forwards that e-mail to the recipient’s office router. Routers have algorithms that make these decisions efficient (as we will learn about later). In the Layer 3, we call each “chunk” of data a packet.
What is the size of a packet known as ?
Maximum Transmission Unit
The sender and recipient agree on the largest size of packet
that they can handle.
Layer 2 - Data Link Layer
Allows two directly devices to communicate. Every network device has a unique address called a MAC address. This address is burned in to the device from the factory.
Uses MAC address to forward traffic
Remember those chunks called packets? Well , your computer doesn’t send packets. It creates the packet and puts the destination IP address on it, but your computer doesn’t know how to get it to California. So, the destination IP address is kind of useless to your computer
Instead, your computer thinks about the next destination of the packet. It might be the same office, an office across the street, or an office in another country.
Your computer just needs to think about whether the destination is within the office or outside the office
Your computer finds out the MAC address of the packet’s destination. Then the computer packages this packet into a frame and adds the destination MAC address
If the destination is somewhere else, your computer won’t be able to figure out the destination MAC address, so it puts the destination MAC address of the router as the recipient.
How do switches work ?
Your computer might be connected directly to your office router, but most likely it will connect to a switch. The switch understands and forwards frames based on the MAC address. We will find out more about how switches work later. When you send a frame to a device within your office, the switch can deliver that frame without having to talk to the router. When you send a frame addressed to the router (i.e. a frame containing a packet that has a destination outside of your office), the switch delivers that frame to the router.
How do emails get delivered ?
Your computer encapsulates the packets containing pieces of your e-mail into frames and adds the destination MAC address. It puts the MAC address of your office router as the destination. The office switch delivers those frames to the router. The router removes the packet from the frame. The router finds the MAC address of the next router and packages the packet into a new frame. It puts the MAC address of the next router into the destination field on the new frame and sends it along. This process continues until the frame is finally delivered to the destination
What are FRAMES and PACKETS?
Packets are
What They Are: Small chunks or pieces of data. When you send an email or any data over the internet, your computer breaks it down into smaller, manageable pieces. Each piece is a packet.
Why We Use Packets: Sending data in smaller chunks is more efficient and reliable. If one piece gets lost or damaged, only that piece needs to be sent again, not the entire email
Packets are like the pieces of the data itself, such as parts of an email, a webpage, or a video you're watching.
Frames are
What They Are: envelopes that hold these packets. Each frame wraps around a packet, adding important information, like the destination MAC address and the source MAC address (where it came from).
Why We Use Them: Ensure that the data can travel through the local network, like from your computer to the router. They help the network devices (like switches and routers) know where to send the data next.
Frames are like the envelopes that these packets are wrapped in to help them move across the local network.
Layer 1 - Physical
What It Is: The tangible part that you can touch, like the cables, switches, and routers. It handles the physical connection between devices, such as your computer and a switch
What It Does: This layer is responsible for transmitting raw data (0s and 1s) over a physical medium. This could be through electrical signals in copper wires, light pulses in fiber-optic cables, or even radio waves in wireless connections
Manages Physical Connections: When two devices, like your computer and a switch, are directly connected, they need to agree on how fast they can send data to each other (called the transmission speed). If one device can’t handle a speed that’s too high, they’ll negotiate a lower speed that both can manage.
Why the Physical Layer Matters?
There would be no way for devices to send data to each other.
Data Encapsulation and Decapsulation within the OSI model context
Encapuslation
What is it: When the router wraps the data (packet) into a frame to send it across the network
Think of it like putting a letter (the packet) into an envelope (the frame).
Decapsulation
What is it: When the router or receiving device removes the data from the frame to look at the packet inside
Think of it like opening the envelope to read the letter
What does a Ethernet Header have?

Preamble
The wake up call for the devices, telling them that a new frame is about to start. It helps devices sync up so they don’t miss any information
Delimiter
Marks the end of the preamble and the start of the actual data
MAC Destination and Source
These are the addresses of the devices involved. The MAC address is like the physical address of the device on the network. The destination MAC is where the data is going, and the source MAC is where its coming from.
Length
Tells how long the frame is
What does an Internet Protocol (IP) header have?
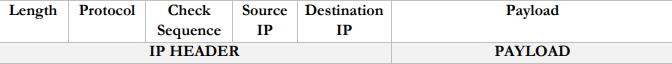
Length
The size of the packets
Protocol
Indicates the rules uses to transmit the data (like TCP or UPD)
Check Sequence
Another safety check for the packet
Source and Destination IP
These are the IP addresses (like phone numbers) of the sending and receiving devices
Payload
The actual data we are sending
TCP flags
What is it: A small piece of information used within the TCP protocol to manage and control the flow of data during a connection. TCP uses these flags to help establish connections, manage data transfer, and ensure that communication between devices is reliable
SYN (Synchronize):
Purpose: Used to initiate a connection between two devices.
When Used: When a device wants to start a TCP connection, it sends a packet with the SYN flag set to 1. This is the first step in the "three-way handshake" used to establish a connection.
ACK (Acknowledgment):
Purpose: Used to acknowledge the receipt of data.
When Used: After receiving data, the receiving device sends a packet back with the ACK flag set, indicating that it successfully received the data.
FIN (Finish):
Purpose: Used to gracefully close a connection.
When Used: When a device is done sending data and wants to close the connection, it sends a packet with the FIN flag set.
RST (Reset):
Purpose: Used to immediately terminate a connection.
When Used: If there’s an error or an unexpected condition, a device might send a packet with the RST flag to abruptly end the connection.
PSH (Push):
Purpose: Tells the receiving device to process the data immediately, rather than waiting to fill up a buffer.
When Used: If data needs to be processed right away (like real-time communication), the sender sets the PSH flag.
URG (Urgent):
Purpose: Indicates that the data in the packet is urgent and should be prioritized.
When Used: If a piece of data is particularly important and should be processed immediately, the sender sets the URG flag.
TCP flags help manage the reliability and order of data transfer. By using these flags, devices can ensure that data is sent, received, acknowledged, and managed correctly, even if there are issues like packet loss or network congestion.
Maximum Transmission Unit (MTU)
What is MTU?
This is the largest size, in bytes, of a single data unit that can be transmitted over a network
Why MTU matters?
Efficiency: If the data being sent exceeds the MTU, it has to be broken down into smaller pieces, a process called fragmentation. Fragmentation can slow down the network and increase the chances of error, so it’s more efficient to send data in sizes that fit within the MTU
Fragmentation: If a packet is larger than the MTU of the network it’s traveling over, it must be broken down into smaller fragments. These fragments are sent separately and reassembled at the destination.
MTU and Path MTU Discovery: Devices use a process called Path MTU Discovery to determine the smallest MTU along the path to avoid fragmentation as much as possible.
1.1 Compare and contrast the Open Systems Interconnection (OSI) model layers and encapsulation concepts
OSI Model
Concepts You Need To Know
Layer 1 - Physical
Layer 2 - Data Link
Layer 3 - Network
Layer 4 - Transport
Layer 5 - Session
Layer 6 - Presentation
Layer 7 - Application
Data encapsulation and decapsulation within the OSI model context
Ethernet Header
Internet Protocol (IP) Header
Transmission Control Protocol (TCP) / User Datagram Protocol (UDP) headers
TCP Flags
Payload
Maximum Transmission Unit (MTU)
How does data on a network (or on the Internet) get from one point to another?
There are seven layers:
Layer 1 - Physical
Layer 2 - Data Link
Layer 3 - Network
Layer 4 - Transport
Layer 5 - Session
Layer 6 - Presentation
Layer 7 - Application
So, a device or program on the Application layer creates content and addresses it to a device on the Application layer at the other side. It gives this content to a device Presentation layer, which packages it, addresses it to the device in the Presentation layer on the other side, and sends it a device on the Session layer. This goes on until we get to the Physical layer.
Layer 7 - Application Layer
You want to send an e-mail. The Layer 7, Application Layer is the software that a user sees (Microsoft Word, Google Chrome etc). You type up the e-mail in Microsoft Outlook and send it off. But what is really happening.
Layer 6 - Presentation Layer
Layer 6 is the presentation Layer. It takes the data from Layer 7 and makes sure that the Application layer of the recipient can understand it. What if the recipient’s computer has a Mac or Unix operation system? What if the user doesn’t use HTML to display e-mails? What if the user’s computer is in a different language?
If you open the same e-mail on your phone, or tablet, or 24” monitor, it will look different. The Presentation Layer on each device understands the capabilities of that device and translates the gibberish into a format that is suitable for its application layer.
Layer 5 - Session Layer
What is a Session? A session is when two devices agree to communicate with each other for a period. When you send the e-mail, your computer calls up the receiving computer and says, “hey, I want to send you an e-mail”. The two computers use the session to exchange data and keep it open until one or both decide to close it.
Layer 4 - Transport Layer
Takes the data from the Session Layer and packages it or breaks it into pieces. So, it might cut up your e-mail into chunks, give each one a number, and send each chunk separately to the recipient. The recipient has already agreed to receive these chunks because it has an established session. The Transport Layer on the other side would put them back 38 together in the correct order. If some of those chunks don’t show up, the sending Transport Layer can send them again. The Transport Layer also puts the IP address of the recipient on each chunk
Layer 3 - Network Layer
Responsible for the routing and forwarding of data packets across different networks.
Primary function - determine the best path for data to travel from the source to the destination
Uses Logical Addressing such as IP addresses to identify devices on a network.
Say you are in New York City and you are sending an e-mail to a device in Los Angeles. Layer 4 put the IP address of the recipient on each “chunk”. How does the data get to the destination? Throughout the internet are many routers and many cables. So, there are many pathways for data to get from NYC to LA. The router in your office looks at the destination IP address and decides about the next router to send the e-mail to (probably the main NYC router for your ISP). That router receives the data and makes its own decision sending it to a router in California. A main router in California sends the data to a router in LA. Finally, a router in LA forwards that e-mail to the recipient’s office router. Routers have algorithms that make these decisions efficient (as we will learn about later). In the Layer 3, we call each “chunk” of data a packet.
What is the size of a packet known as ?
Maximum Transmission Unit
The sender and recipient agree on the largest size of packet
that they can handle.
Layer 2 - Data Link Layer
Allows two directly devices to communicate. Every network device has a unique address called a MAC address. This address is burned in to the device from the factory.
Uses MAC address to forward traffic
Remember those chunks called packets? Well , your computer doesn’t send packets. It creates the packet and puts the destination IP address on it, but your computer doesn’t know how to get it to California. So, the destination IP address is kind of useless to your computer
Instead, your computer thinks about the next destination of the packet. It might be the same office, an office across the street, or an office in another country.
Your computer just needs to think about whether the destination is within the office or outside the office
Your computer finds out the MAC address of the packet’s destination. Then the computer packages this packet into a frame and adds the destination MAC address
If the destination is somewhere else, your computer won’t be able to figure out the destination MAC address, so it puts the destination MAC address of the router as the recipient.
How do switches work ?
Your computer might be connected directly to your office router, but most likely it will connect to a switch. The switch understands and forwards frames based on the MAC address. We will find out more about how switches work later. When you send a frame to a device within your office, the switch can deliver that frame without having to talk to the router. When you send a frame addressed to the router (i.e. a frame containing a packet that has a destination outside of your office), the switch delivers that frame to the router.
How do emails get delivered ?
Your computer encapsulates the packets containing pieces of your e-mail into frames and adds the destination MAC address. It puts the MAC address of your office router as the destination. The office switch delivers those frames to the router. The router removes the packet from the frame. The router finds the MAC address of the next router and packages the packet into a new frame. It puts the MAC address of the next router into the destination field on the new frame and sends it along. This process continues until the frame is finally delivered to the destination
What are FRAMES and PACKETS?
Packets are
What They Are: Small chunks or pieces of data. When you send an email or any data over the internet, your computer breaks it down into smaller, manageable pieces. Each piece is a packet.
Why We Use Packets: Sending data in smaller chunks is more efficient and reliable. If one piece gets lost or damaged, only that piece needs to be sent again, not the entire email
Packets are like the pieces of the data itself, such as parts of an email, a webpage, or a video you're watching.
Frames are
What They Are: envelopes that hold these packets. Each frame wraps around a packet, adding important information, like the destination MAC address and the source MAC address (where it came from).
Why We Use Them: Ensure that the data can travel through the local network, like from your computer to the router. They help the network devices (like switches and routers) know where to send the data next.
Frames are like the envelopes that these packets are wrapped in to help them move across the local network.
Layer 1 - Physical
What It Is: The tangible part that you can touch, like the cables, switches, and routers. It handles the physical connection between devices, such as your computer and a switch
What It Does: This layer is responsible for transmitting raw data (0s and 1s) over a physical medium. This could be through electrical signals in copper wires, light pulses in fiber-optic cables, or even radio waves in wireless connections
Manages Physical Connections: When two devices, like your computer and a switch, are directly connected, they need to agree on how fast they can send data to each other (called the transmission speed). If one device can’t handle a speed that’s too high, they’ll negotiate a lower speed that both can manage.
Why the Physical Layer Matters?
There would be no way for devices to send data to each other.
Data Encapsulation and Decapsulation within the OSI model context
Encapuslation
What is it: When the router wraps the data (packet) into a frame to send it across the network
Think of it like putting a letter (the packet) into an envelope (the frame).
Decapsulation
What is it: When the router or receiving device removes the data from the frame to look at the packet inside
Think of it like opening the envelope to read the letter
What does a Ethernet Header have?

Preamble
The wake up call for the devices, telling them that a new frame is about to start. It helps devices sync up so they don’t miss any information
Delimiter
Marks the end of the preamble and the start of the actual data
MAC Destination and Source
These are the addresses of the devices involved. The MAC address is like the physical address of the device on the network. The destination MAC is where the data is going, and the source MAC is where its coming from.
Length
Tells how long the frame is
What does an Internet Protocol (IP) header have?

Length
The size of the packets
Protocol
Indicates the rules uses to transmit the data (like TCP or UPD)
Check Sequence
Another safety check for the packet
Source and Destination IP
These are the IP addresses (like phone numbers) of the sending and receiving devices
Payload
The actual data we are sending
TCP flags
What is it: A small piece of information used within the TCP protocol to manage and control the flow of data during a connection. TCP uses these flags to help establish connections, manage data transfer, and ensure that communication between devices is reliable
SYN (Synchronize):
Purpose: Used to initiate a connection between two devices.
When Used: When a device wants to start a TCP connection, it sends a packet with the SYN flag set to 1. This is the first step in the "three-way handshake" used to establish a connection.
ACK (Acknowledgment):
Purpose: Used to acknowledge the receipt of data.
When Used: After receiving data, the receiving device sends a packet back with the ACK flag set, indicating that it successfully received the data.
FIN (Finish):
Purpose: Used to gracefully close a connection.
When Used: When a device is done sending data and wants to close the connection, it sends a packet with the FIN flag set.
RST (Reset):
Purpose: Used to immediately terminate a connection.
When Used: If there’s an error or an unexpected condition, a device might send a packet with the RST flag to abruptly end the connection.
PSH (Push):
Purpose: Tells the receiving device to process the data immediately, rather than waiting to fill up a buffer.
When Used: If data needs to be processed right away (like real-time communication), the sender sets the PSH flag.
URG (Urgent):
Purpose: Indicates that the data in the packet is urgent and should be prioritized.
When Used: If a piece of data is particularly important and should be processed immediately, the sender sets the URG flag.
TCP flags help manage the reliability and order of data transfer. By using these flags, devices can ensure that data is sent, received, acknowledged, and managed correctly, even if there are issues like packet loss or network congestion.
Maximum Transmission Unit (MTU)
What is MTU?
This is the largest size, in bytes, of a single data unit that can be transmitted over a network
Why MTU matters?
Efficiency: If the data being sent exceeds the MTU, it has to be broken down into smaller pieces, a process called fragmentation. Fragmentation can slow down the network and increase the chances of error, so it’s more efficient to send data in sizes that fit within the MTU
Fragmentation: If a packet is larger than the MTU of the network it’s traveling over, it must be broken down into smaller fragments. These fragments are sent separately and reassembled at the destination.
MTU and Path MTU Discovery: Devices use a process called Path MTU Discovery to determine the smallest MTU along the path to avoid fragmentation as much as possible.