3.1 - CompTIA Security+
Architecture and infrastructure concepts
Cloud
Responsibility matrix
Responsibility matrix: A diagram that defines the security responsibilities of both the cloud service provider and the customer, ensuring clarity in the security roles and obligations for cloud deployments.
Software as a service (SaaS): A cloud service model where the service provider hosts applications and makes them available to customers over the internet, allowing end-users to access software without managing the underlying infrastructure.
Platform as a Service (PaaS): A cloud service model that provides a platform allowing customers to develop, run, and manage applications without dealing with the complexities of building and maintaining the infrastructure typically associated with developing and launching apps.
Infrastructure as a Service (IaaS): A cloud service model that offers virtualized computing resources over the internet, enabling customers to rent servers, storage, and networks on a pay-as-you-go basis while maintaining control over the operating systems and applications they deploy.
Hybrid considerations
Hybrid cloud: Cloud deployment model that combines both public and private cloud infrastructures.
Hybrid cloud considerations: Managing public/private cloud security policies, integrating cloud environments with existing on-premise infrastructure.
Third-party vendors
Third-party vendors: External entities in cloud computing, third-party vendors refer to the providers offering cloud services to businesses using infrastructure, platform, or software-as-a-service models. As a third party, careful consideration regarding cloud service provider selection, contract negotiation, service performance, compliance, and communication practices is paramount.
Infrastructure as code (IaC)
Infrastructure as Code (IaC): A software engineering practice that manages computing infrastructure using machine-readable definition files. These files contain code written in a specific format that can be read and executed by machines.
Serverless
Serverless architecture: Cloud deployment where the cloud provider manages infrastructure and scales resources up or down based on demand.
Microservices
Microservices: Independent components that run each application process as a service. These services communicate via a well-defined interface using lightweight APIs. Function by clients talking to the API gateway, which would then send the request to the appropriate microservice.
Network infrastructure
Physical isolation
Air-gapped: A type of network isolation that physically separates a host from other hosts or a network from all other networks.
Logical segmentation
Logical segmentation: Network topology enforced by switch, router, and firewall configuration, where hosts on one network segment are prevented from or restricted in communicating with hosts on other segments. Applied to Layer 3 (Network) or the OSI model.
Software-defined networking (SDN)
Software-defined networking (SDN): Centralized, application-based control over a network’s structure and behavior, allowing for dynamic network configuration, and improved network management/monitoring. Separates functionality within three distinct “planes” - management, control, and data.
Management plane: Highest layer - monitors traffic conditions and network status.
Control plane: Makes decisions about how data should be forwarded/secured.
Data plane: Handles traffic switching/routing, and implementation of security controls.
On-premises
On-premises network: A private network facility that is owned and operated by an organization for use by its employees only. Also referred to as an enterprise local area network (LAN), it often includes wall ports, structured cabling, and patch panels.
Centralized vs. decentralized
Centralized computing architecture: A model where all data processing/storage is performed in a single location, typically a central server.
Decentralized computing architecture: A model where data processing and storage are distributed across multiple locations, allowing for greater flexibility and scalability by enabling individual nodes to operate independently.
Containerization
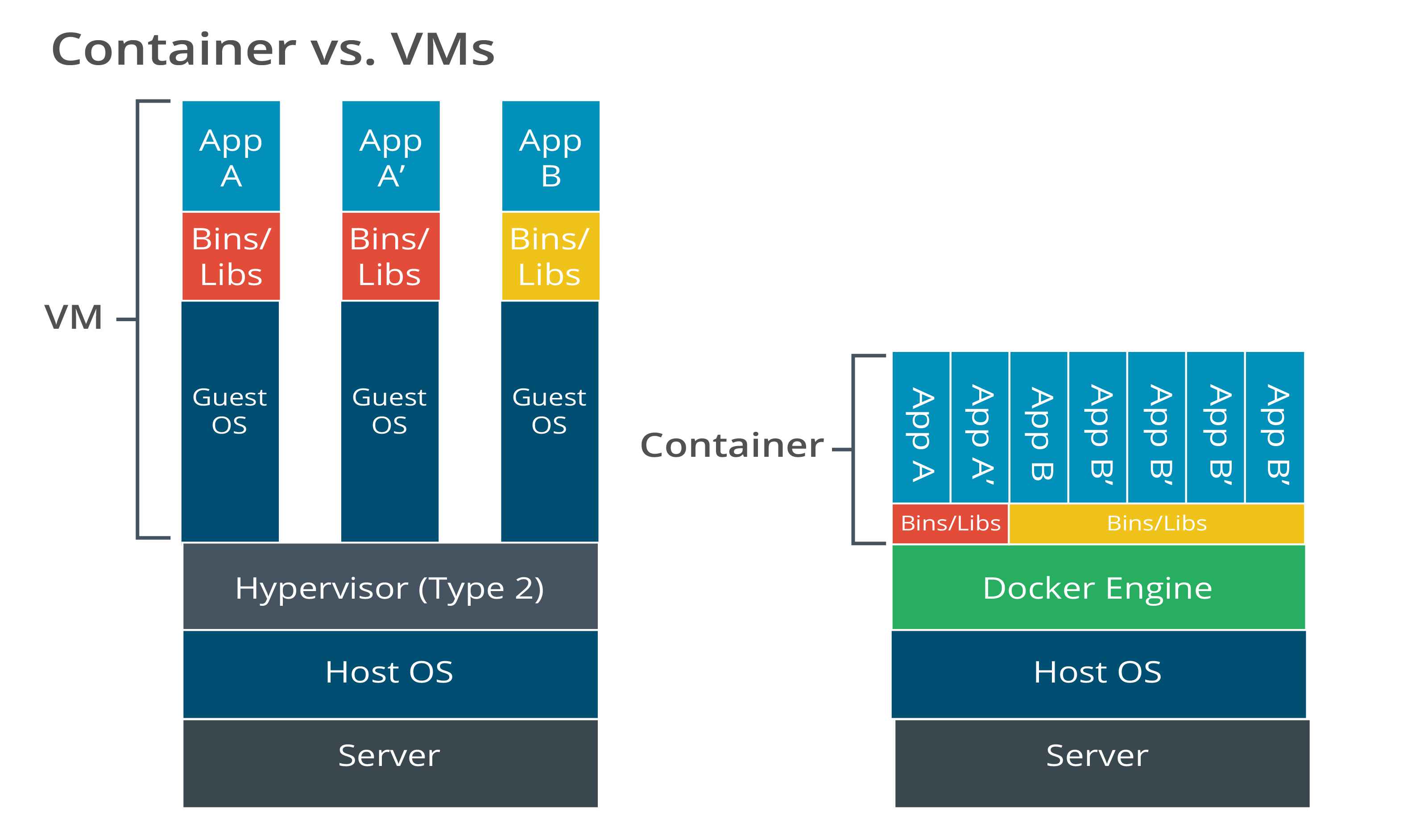
Containerization: Virtualization technology that allows applications to be packaged into containers, which store everything needed to run, ensuring consistency across multiple environments and facilitating easier deployment and management. For example, all components required to deliver a web application could be deployed in containers and managed using a container platform such as Docker.
Virtualization
Application virtualization: A software delivery model where the code runs on a server and is streamed to a client.
Desktop virtualization: Technology that allows a desktop operating system and its applications to run in a virtual environment on a server, enabling remote access and centralized management.
IoT
Internet of Things (IoT): A network of interconnected devices that communicate and exchange data over the internet, enhancing automation and data collection in various sectors.
Industrial control systems (ICS)/supervisory control and data acquisition (SCADA)
Industrial control systems (ICS): Networks that manage embedded devices, and control workflow/process automation.
Supervisory control and data acquisition (SCADA): A type of industrial control system that manages large-scale, multiple-site devices and equipment spread over geographically large areas from a host computer.
Real-time operating system (RTOS)
Embedded systems
Embedded systems: Electronic systems designed to perform a specific, dedicated function, such as a microcontroller in a medical drip or components in a control system managing a water treatment plant.
High availability
High availability: An approach that ensures a system remains operational and accessible for maximum uptime, often achieved through redundancy and failover strategies.
Considerations (cloud service providers)
Availability
Availability (CSPs): Cloud Service Providers (CSPs) must implement robust architectures that support high availability by distributing resources across multiple regions and within their local region, utilizing load balancing techniques to minimize downtime.
Resilience
Resilience (CSPs): Cloud providers use redundant hardware, fault tolerance capabilities (such as clustering), and data replication to store data across multiple servers and data centers, ensuring that data remains available if one server or data center fails.
Cost
Cost: Cost considerations for CSPs include the expenses related to maintaining confidentiality, integrity, and availability of data, not simply the cost of cloud adoption.
Responsiveness
Scalability
Scalability: The ability to dynamically expand and contract capacity in response to demand, with no downtime.
Scale-up/vertical scaling: Scaling type that involves adding capacity to an existing resource (e.g., more processors or memory).
Scale-out/horizontal scaling: Scaling type that involves adding more resources to work in parallel (e.g., more instances/virtual machines), and increasing resources.
Ease of deployment
Ease of deployment: Features that allow easy implementation of cloud infrastructure, including automation, standardization (templates, image deployments), and portability.
Risk transference
Risk transference: The process of shifting the financial burden of security risk to another party, often achieved through insurance policies or third-party services, this can help organizations mitigate risks connected to cloud deployments.
Ease of recovery
Ease of recovery: Features that allow organizations to regularly backup data and restore functionality in case of system failures/data breaches.
Patch availability
Patch availability: Includes how accessible patches are for cloud environments, including automated patch management, regular software updates, centralized patch management, security monitoring, third-party software support.
Inability to patch
Inability to patch: This refers to the challenges organizations face in applying necessary updates due to factors such as lack of resources, incompatible systems, or vendor limitations, which can lead to increased vulnerability risks.