
Practice Exam A
C. DNS Poisoning - Correct
A. USB data blocker - Correct
A. Reverse Proxy (study up on this term) - Correct
A. A phishing email stating a cash settlement has been awarded but will expire soon - Correct
C. SQLi -Correct
A. Data anonymization - Correct
A. Classify the data - Correct
C.XSRF - Correct
D. Password history - Correct
B. Wildcard - Correct
What to study for on 1-10 Section
Wildcard - covers unlimited subdomains with a single cert (example of a subdomain (support.google.com, it.google.com, shop.google.com)
- a wildcard certificate for *google.com would secure all these subdomains
Subject alternative name - (covers multiple domains or subdomains with a single certificate)
-www.google.com
-mail.google.com
-www.roblox.com
-rent.roblox.com
XSRF (Cross site request forgery, will inject the POST request to change email, address or shipping, or transfer funds)
XSS (Cross Site Scripting occurs when attackers try to inject JavaScript into the client’s website)
___________________________________________
Sections 2
A. DLP
A. Replacing the traditional key with an RFID key
C. Masking incorrect Hashing is correct answer
C.SSH
A. Perform a mathematical operation on the passwords that will convert them into unique strings.
A. Steganography
A. Password complexity
B. FIM
A. To validate the integrity of the files
C pathping 10.10.10.0 -p 80
What to study for on 11-21 Section
The difference between tokenization and masking
Which of the following can be used by a monitoring tool to compare values and detect passwords leaks without providing the actual credentials
A. Hashing Most Voted
B. Tokenization
C. Masking
D. Encryption
Hashing is a cryptographic technique that takes input data (in this case, passwords) and converts it into a fixed-size string of characters, which is the hash value. The hashing process is one-way, meaning it is not feasible to reverse the hash and obtain the original password from the hash value alone.
A company recently experienced an inside attack using a corporate machine that resulted in data compromise. Analysis indicated an unauthorized change to the software circumvented technological protection measures. The analyst was tasked with determining the best method to ensure the integrity of the systems remains intact and local and remote boot attestation can take place. Which of the following would provide the BEST solution?
A. HIPS
B. FIM
C. TPM Most Voted
D. DLP
TPM (Trusted Platform Module) is a hardware-based security component that is designed to provide secure cryptographic functions and protect sensitive data on a computer or server. It is commonly used to ensure the integrity and security of a system's boot process and to support local and remote attestation.
A security manager has tasked the security operations center with locating all web servers that respond to an unsecure protocol. Which of the following commands could an analyst run to find the requested servers?
A. nslookup 10.10.10.0
B. nmap -p 80 10.10.10.0/24 Most Voted
C. pathping 10.10.10.0 -p 80
D. ne -l -p 80
reasoning for answer B 1. nmap: nmap is a powerful network scanning tool used to discover hosts and services on a computer network. 2. -p 80: This option specifies that nmap should scan for open ports on port 80, which is the default port used for HTTP (unsecure web) communication. 3. 10.10.10.0/24: This is the target network range or IP address range that the analyst wants to scan. The /24 indicates a subnet mask of 255.255.255.0, meaning it will scan all IP addresses in the 10.10.10.0 network.
____________________________________________________
Section 3
False Acceptance
GDPR
B, A
C
A. Geographic dispersal
A. EAP correct answer was AES
B. SWG correct but I did not know what it was
C. Implement access control vestibules.
D. Diagrams
TLS (Transport Layer Socket/Secure) - encrypts network traffic that is in transit
A security engineer is deploying a new wireless network for a company. The company shares office space with multiple tenants. Which of the following should the engineer configure on the wireless network to ensure that confidential data is not exposed to unauthorized users?
A. EAP Most Voted
B. TLS
C. HTTPS
D. AES
AES - provides confidentiality to both data-at-rest and data-in-transit, preventing unauthorized users from seeing either
EAP - is an Authentication Protocol (authentication does not provide confidentiality) . Authentication encompasses processes that allows systems and networks to determine if a user is who they say they are
SWG is a proxy-based firewall, content filter, and intrusion detection/prevention system that mediates user access to Internet sites and service
29. Which of the following would BEST provide a systems administrator with the ability to more efficiently identify systems and manage permissions and policies based on location, role, and service level?
Answer: Standard naming conventions
These are naming frameworks used for naming hardware assets, and for digital assets such as accounts and virtual machines in a consistent way. The naming strategy should allow administrators to identify the type and function of any particular resource or location at any point.
=============================
Helpful Info:
Domain Services - Services that stores centralized directory information and lets users and domains communicate. When a user attempts to connect to a device or resource on a network, this service provides login authentication, verifying the user's login credentials and access permissions.
Baseline configuration - A documented set of specifications for an information system, or a configuration item within a system, that has been formally reviewed and agreed on at a given point in time, and which can be changed only through change control procedures.
____________________________________________________________
Section 4
C
C. what is a container? a container is a like a sandbox where one application can run all of its services
D. transference.
B
B
A
A
C. DDoS attack
C. Longer key longevity correct answer is High data entropy
C. A zero-day exploit is initially undetectable, and no patch for it exists.
Question #32
A security analyst is concerned about critical vulnerabilities that have been detected on some applications running inside containers. Which of the following is the BEST remediation strategy ?
Answer (B. Update the base container image and redeploy the environment
Updating the host in which the containers are running may not patch vulnerabilities inside the containers. Updating the base container image will ensure any known vulnerabilities are patched before the container is redeployed. This is going to save time and ensure all containers are patched securely and effectively.
Which of the following will increase cryptographic security?
A. High data entropy Most Voted
B. Algorithms that require less computing power
C. Longer key longevity
D. Hashing
Entropy refers to the randomness of a cryptographic algorithm. A higher level of randomness results in a higher level of security when using the algorithm. A lack of entropy results in a weaker algorithm and makes it
____________________________________________
Section 5
C
D
D
B
A
C
B
C. Unknown backdoor
B
C
Research- False Rejection Rate and False Acceptance Rate
Research - TAXXI
Question #46
D. Implement a TAXII server. Most Voted
An organization wants to participate in threat intelligence information sharing with peer groups. Which of the following would MOST likely meet the organization's requirement?
Reasoning for the answer | A TAXII server is a client that exchanges standardized and anonymized cyber threat intelligence among users. It works as a venue for sharing and collecting Indicators of compromise, which have been anonymized to protect privacy.
Question #50
An amusement park is implementing a biometric system that validates customers' fingerprints to ensure they are not sharing tickets. The park's owner values customers above all and would prefer customers' convenience over security. For this reason, which of the following features should the security team prioritize
FIRST?
A. Low FAR
B. Low efficacy
C. Low FRR Most Voted
D. Low CER
Reasoning For The Answer : False Acceptance Rate (FAR) is a metric for bio-metric performance that determines the number of instances where unauthorized persons were incorrectly authorized. False Rejection Rate (FRR) is a metric that determines the number of instances where an authorized person are incorrectly rejected.
If the emphasis is security, then making sure the False Acceptance Rate is low as a low FAR rate means a lower possibility for someone to be authorized who shouldn't. If the emphasis is convenience, then you'd want to make sure the False Rejection Rate is low as a low FRR means a lower possibility for someone to be rejected who should be authorized.
______________________________________________
D) NIST
D) Remote Access Trojan correct answer is Logic Bomb
B) what is CSIRT though?
D) Correct answer C)
A)
B)
C)
D)
A)
C) Answer is B which we thought at first research what SOAR is
Question #51
Which of the following organizations sets frameworks and controls for optimal security configuration on systems?
A. ISO
B. GDPR
C. PCI DSS
D. NIST Most Voted
Question #52
An organization discovered files with proprietary financial data have been deleted. The files have been recovered from backup, but every time the Chief Financial
Officer logs in to the file server, the same files are deleted again. No other users are experiencing this issue. Which of the following types of malware is MOST likely causing this behavior?
A. Logic bomb Most Voted
B. Cryptomalware
C. Spyware
D. Remote access Trojan
Answer Reasoning: A logic bomb is inserted code that will intentionally set off a malicious function when specified conditions are met. In this question, the logic bomb could be related to when the CFO logs in as no other user is experiencing this issue.
It is not a RAT because a RAT - malware an attacker uses to remotely control an infected computer
Question #54
During an incident response, an analyst applied rules to all inbound traffic on the border firewall and implemented ACLs on each critical server. Following an investigation, the company realizes it is still vulnerable because outbound traffic is not restricted, and the adversary is able to maintain a presence in the network.
In which of the following stages of the Cyber Kill Chain is the adversary currently operating?
A. Reconnaissance
B. Command and control
C. Actions on objective
D. Exploitation
B because they are maintaining or controlling the foothold they have on the victim's machine
Question #55
A recent security breach exploited software vulnerabilities in the firewall and within the network management solution. Which of the following will MOST likely be used to identify when the breach occurred through each device?
A. SIEM correlation dashboards
B. Firewall syslog event logs
C. Network management solution login audit logs
D. Bandwidth monitors and interface sensors
Question #56
Which of the following is the FIRST environment in which proper, secure coding should be practiced?
A. Stage
B. Development
C. Production
D. Test
Dont» Throw» Sausage» Pizza
Development » Testing» Staging » Production
Question #57
A cloud service provider has created an environment where customers can connect existing local networks to the cloud for additional computing resources and block internal HR applications from reaching the cloud. Which of the following cloud models is being used?
A. Public
B. Community
C. Hybrid
D. Private
Question #58
An organization has developed an application that needs a patch to fix a critical vulnerability. In which of the following environments should the patch be deployed
LAST?
A. Test
B. Staging
C. Development
D. Production
Question #59
An organization is building backup server rooms in geographically diverse locations. The Chief Information Security Officer implemented a requirement on the project that states the new hardware cannot be susceptible to the same vulnerabilities in the existing server room. Which of the following should the systems engineer consider?
A. Purchasing hardware from different vendors
B. Migrating workloads to public cloud infrastructure
C. Implementing a robust patch management solution
D. Designing new detective security controls
Question #60
A security analyst is working on a project to implement a solution that monitors network communications and provides alerts when abnormal behavior is detected.
Which of the following is the security analyst MOST likely implementing?
A. Vulnerability scans
B. User behavior analysis
C. Security orchestration, automation, and response
D. Threat hunting
Reason: As per Comptia objectives, User behavior Analysis comes under SIEM. Well as the Question asks whats most likely the solution being implemented hence User behavior analysis seems to be the direct answer. SOAR simply means you are adding automation and servers handle the security tasks automatically and take action. happy to discuss. Some of the question are to confuse so i ll stick to most direct connection in this case. B
C. Security orchestration, automation, and response (SOAR): SOAR platforms help automate and coordinate security operations tasks. While they can work with monitoring tools, they themselves are not primarily focused on detecting abnormal network behavior.
B. User behavior analysis: UBA involves monitoring the activities and behaviors of users on a network to detect anomalies that could indicate potential security threats. This fits the description of monitoring network communications and alerting on abnormal behavior.
_______________________________________________________-
Section 6
D, B
A. Malicious script
D. Smishing
A. Train the team to identify the difference between events and incidents.
D. WAF and NIPS
B. Perform a physical-to-virtual migration.
D. Block port 3389 inbound from untrusted networks.
B. Federation
C. Implement a SOAR with customizable playbooks.
A. PKI
Question #65
A cybersecurity administrator needs to implement a Layer 7 security control on a network and block potential attacks. Which of the following can block an attack at
Layer 7? (Choose two.)
B. NIPS (Network Intrusion Prevention System): A NIPS is an intrusion detection system that can actively block and prevent detected threats. It operates at Layer 7 of the OSI model, just like NIDS (Network Intrusion Detection System). However, NIPS goes beyond detection and takes proactive measures to block potential attacks at the network level.
- D. WAF (Web Application Firewall): A WAF is a security control that operates at Layer 7 of the OSI model. It is specifically designed to monitor, filter, and block HTTP/HTTPS traffic to and from web applications. By doing so, it can prevent web-based attacks, such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
Question #68
Which of the following uses SAML for authentication?
A. TOTP
B. Federation Most Voted
C. Kerberos
D. HOTP
Answer: B: Federation, or identity federation, defines policies, protocols, and practices to manage identities across systems and organizations. Federation’s ultimate goal is to allow users to seamlessly access data or systems across domains. Federation is enabled through the use of industry standards such as Security Assertion Markup Language (SAML).
TAKE A LOOK AT THESE QUESTIONS
HIDS
NIPS
HSM
WAF
NAC
NIDS
______________________________________________________________
SECTION 7
C. VDI
C. Proprietary
B. A CASB , C. An NG-SWG
C. COPE and VDI
A READ! Answer was B. Keylogger because
A
C
A
A
A
Go Over This Entire Section & Vocabulary
C. COPE and VDI
D. CYOD and VMs
Rainbow attack - uses tables of reversed hashes to crack passwords
Question #75Topic 1
Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities. After further investigation, a security analyst notices the following:
✑ All users share workstations throughout the day.
✑ Endpoint protection was disabled on several workstations throughout the network.
✑ Travel times on logins from the affected users are impossible.
✑ Sensitive data is being uploaded to external sites.
All user account passwords were forced to be reset and the issue continued.
Which of the following attacks is being used to compromise the user accounts?
A. Brute-force
B. Keylogger Most Voted
RC. Dictionary
D. Rainbow
Reasoning between the answer B
A keylogger or keystroke logger is a type of monitoring software that can be used to collect keystrokes that you type. A keylogger was likely used to capture various sensitive information and credentials. As the issue continued after the password reset, the keylogger was still capturing information as it wasn't removed.
=========================
Brute-force - trail and error attempts to guess login info
Dictionary - a form of brute force attack that uses common words, phrases and variations
Rainbow - uses tables of reversed hashes to crack passwords’
PROFESSOR MESSER TAKE AWAYS
Credential Harvesting
running a malicious script on a user local pc that pulls your credentials from browsers (Google Chrome, Firefox) and sends it to the attacker
What is the difference between a worm and a virus?
A virus needs human interaction
A worm does not
Rootkit
modifies core systems files
embeds itself in the kernel
becomes hard to hide one it is installed
Logic Bomb
Waits for a predefined event to launch malicious code
Hashes cannot be reverted to plaintext
Spraying Attack
tries a few passwords before moving on to the next
avoids account lockouts
non persistent xss attack
an attack that targets 1 user
an attacker usually sends an user an email and the user has to click the link in the email for the attack to be run
persistent xss attack
an attack that targets anyone
can be posted on a forum site and anyone who visits this site will execute the malicious script
what does XSRF mean ?
cross-site request forgery
what does SSRF mean?
server-side request forgery
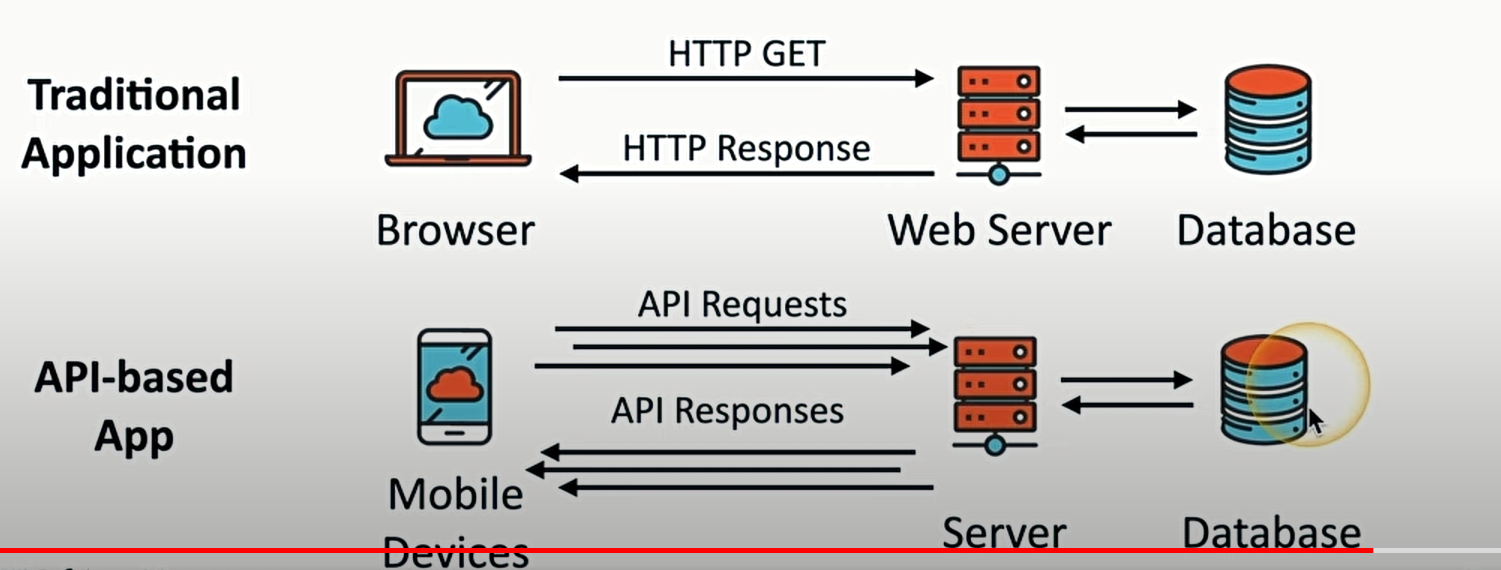
api attacks
are requests that are sent from a mobile device to a server to the database
instead of sending HTTP Get request the mobile device sends a API Requests and gets an API Responses back
what is a STIX ?
a language that is used to share cyber threat information
what transport is used to transport cyber threat information?
TAXII
academic journals?
detailed information about attacks and how other users have dealt with them
best security features
how the attack looks (breaks the attack down)
rfc |request for comment|
a way to track and formalize a set of standards anyone can use
what doe soar stand for
security orchestration automation response
whit team
not a side
manages the rules of a pen test exercise between red and blue team
2.0
diagrams
a diagram (map) of where everything is located on the network
ip schema
helps configure assign ip address to users, printers, routers
helps avoid duplicates ip addressing
data masking
is a data security technique used to protect sensitive information by obscuring or hiding the actual data
social security number
xxx-xxx-1345
tokenization
replace sensitive data with a non-sensitive placeholder
SSN 266-12-1112 is now 123-456-7890
hashing verifies?
integrity
what are sha-1, sha-2, and sha-3 and md5 all examples of?
Hashes
api considerations
these attacks are very similar to any other attack except the endpoint used in a phone and not a computer, so the information sent is (API Request)
security measures put in place to protect api interactions
fake telemetry
training the machine with fake data to the machine
dns sinkhole
attack can redirect users to malicious sites
provides false information to malicious traffic, redirecting it to a controlled IP address.
SaaS
example of this is google mail
the software is provided to you all you have to do is login
they maintained and anything related to that software is controlled by google
PaaS
gives you everything you need to focus on the application
all you need to do is focus on the application and data
you get the server, networking, etc.
Edge Computing
data is processed locally instead of going to the internet
Fog Computing
some of the data being processed will go to the cloud
Container
contains everything you need to run an application
apps can’t interact with each other
one operating system
Virtualization
can have multiple OS systems
Serverless Architecture
Developers can deploy code without managing server infrastructure, leading to faster development cycle
Pay only for the actual compute time and resources consumed, with no charges for idle time.
Transit Gateway
is used by a user to connect to multiple VPC's on the network, the transit gateway is also used to connect multiple VPC's that have different application running on them.
Service Integration
Streamlines operations by allowing different services and applications to work together seamlessly.
SDN
is an approach to networking that uses software-based controllers or application programming interfaces (APIs) to communicate with underlying hardware infrastructure and direct traffic on a network.
What is SDV?
Software Defined Visibility
What is SDN?
Software Defined Networking
VM Sprawl
happens when there are to many VMs being built and no one is keeping track of this deprovisioning of the VM’s
Where should code be tested first?
the sandbox
Don’t Throw Sausage Pizza
Development / Testing / Staging / Production
Scalability
the ability to increase the workload in a given infrastructure
Elasticity
the ability to increase or decrease the available resources as the workload changes
Stored Procedures
SQL procedures that cannot be modified
protects attacker from knowing the exact location of the database
Normalization
check and correct all input
a zip code should be only X characters long with a letter in the X column
Version control
used to make sure a file application/file has not been changed over time
used to track changes and revert back to previous version if needed
Federation
allows someone to access your network using credentials stored with a third party
example
Log in with Twitter
Log in with Facebook
Log in with Google
What authentication is used to allow someone to access your network using credentials stored with a third party?
Federation
Attestation
used to prove the hardware is really yours
HOTP
a one time password that changes
uses hmac and counter mode
Gait Analysis
This identifies a person based on how they walk
UPS
short term power supply for when power goes out this does not last for a very long time
Generators
long time power supply for when the power goes out
can power entire buildings
SAN
a network drive (provides storage for servers)
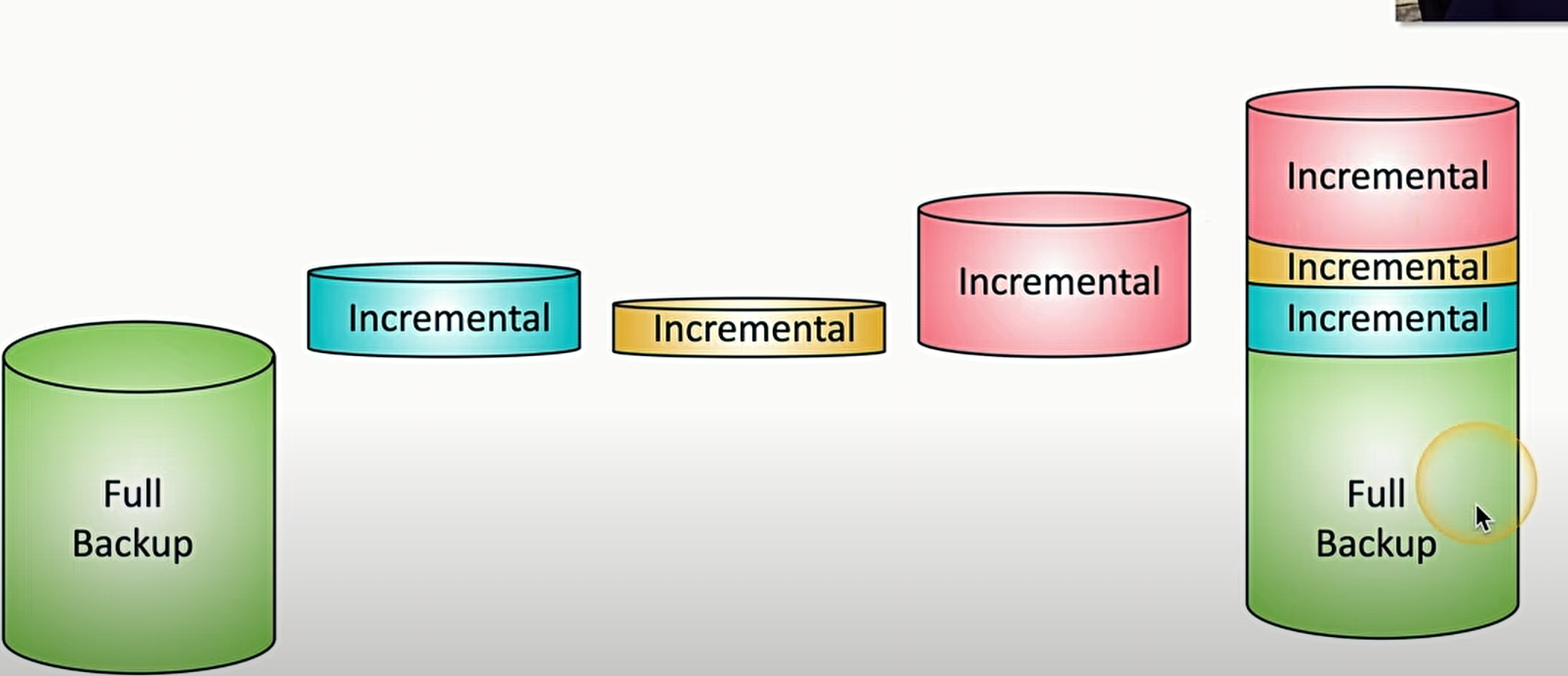
Incremental
this back up backs up everything since the last incremental backup
Tuesday = Tuesdays backups, Wednesday = Wednesday’s backup
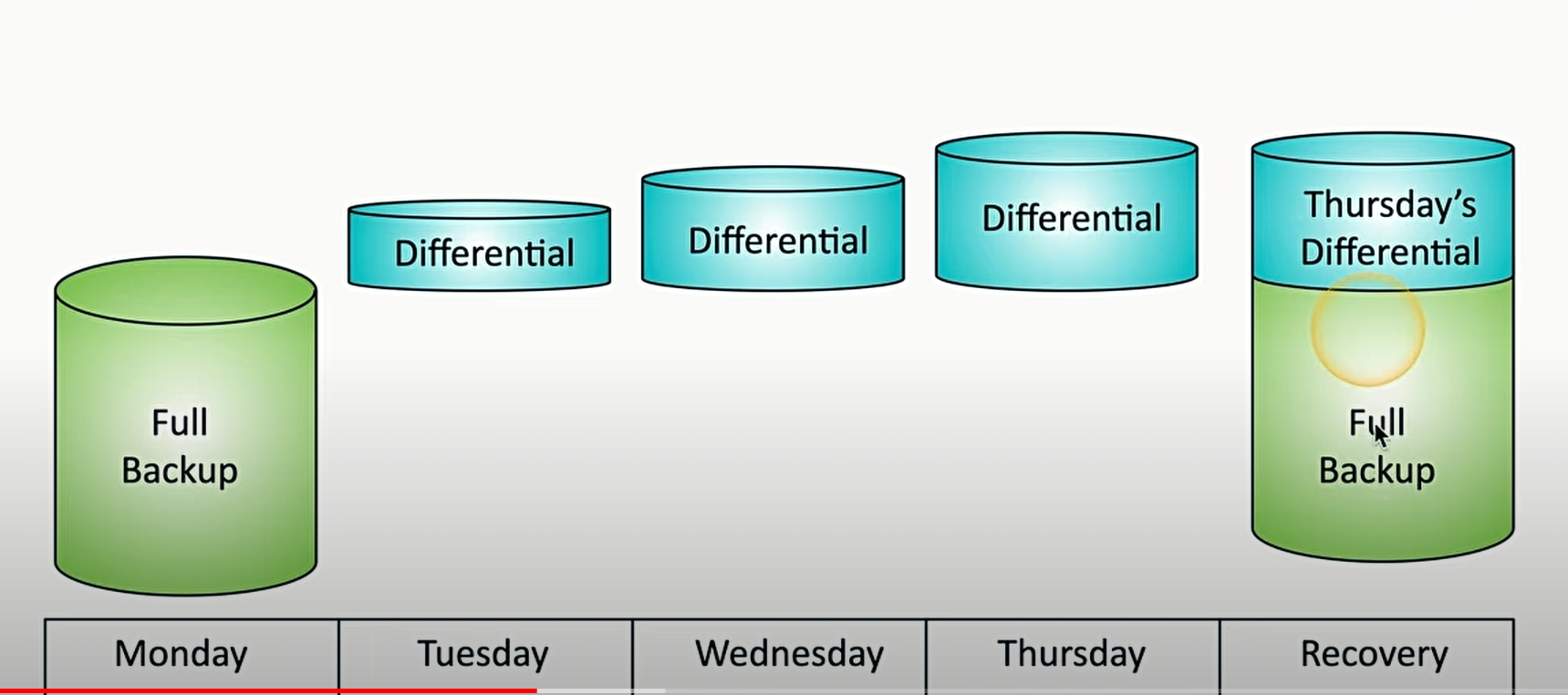
Differential
this back up backs up all files that have changed since the last full backup
Tuesday = Tuesdays backups, Wednesday = Tuesday’s and Wednesdays backups and so on
NAS provides
file level access
SAN provides
block level access
What is a FPGA
Field programmable gate array (FPGA)
Characterisitcs of a FPGA
is an integrated circuit that can be configured by a customer or a designer after manufacturing
Can be reprogrammed to update functionality or fix issues even after deployment
What is a Raspberry Pi?
is a small, affordable single-board computer
where are raspberry pi most often used ?
IOT devices
smart meter
measure power and water usage
zigbee
a high-level communication protocol using low power, low power data rate
based on the IEEE 802.15.4
used in IoT devices
mantraps
consists of two interlocking doors, where the first door must be closed and locked before the second door can be opened
faraday cages
blocks electromagnetic fields
air gap
physical separation between networks
secure network and insecure network
separate customer infrastructures
pulverizer
completely destroy the disk
degaussing
remove the magnetic field
destroys the drive data and renders the drive unusable
key stretching
how to make a key stronger?
hash the password. hash the hash of the password. and continue
lightweight cryptography
often found in IoT devices
provides cryptography to devices that have less cpu power
ECC
uses smaller keys than asymmetric encryption
provides strong cryptographic security with smaller key sizes making it suitable for device with limited computational resources
What is ECC best used on?
on devices with limited computation resources
What does ECC stand for?
Elliptic curve cryptography
perfect forward secrecy
ensures sessions keys will not be compromised even if the server’s private key is compromised
each session uses a unique session key that cannot be derived from any other session key
post-quantum cryptography
breaks our existing encryption mechanism
quantum computing
computers based on quantum physics
a new computing technology
ephemeral
refers to temporary keys that are generated and used for a single session
symmetric encryption
A single shared key
asymmetric encryption
public key cryptography
two or more keys
involves a public key and private key
blockchain
is a decentralized and distributed digital ledger technology that records transactions across many computers in such a way that the registered transactions cannot be altered retroactively.
homomorphic encryption
performs calculation on data while the data is still encrypted
entropy
key randomization
stream cipher suites
refers to a category of encryption algorithms that encrypt plaintext one bit or byte at a time
what encryption is used with stream ciphers?
symmetric encryption
block cipher suites
refers to a category of encryption algorithms that encrypt plaintext blocks at a time
what encryption is used with block ciphers?
symmetric encryption
asymmetric encryption is not used with
cipher suites
ecb
each block of plaintext is encrypted independently using the same key,
-using advanced encryption standard (AES)
cbc (cipher block chain)
block ciphers that enhance security by introducing dependencies between blocks,
each plaintext block is XOred with the previous ciphertext block before being encrypted
adds additional randomization
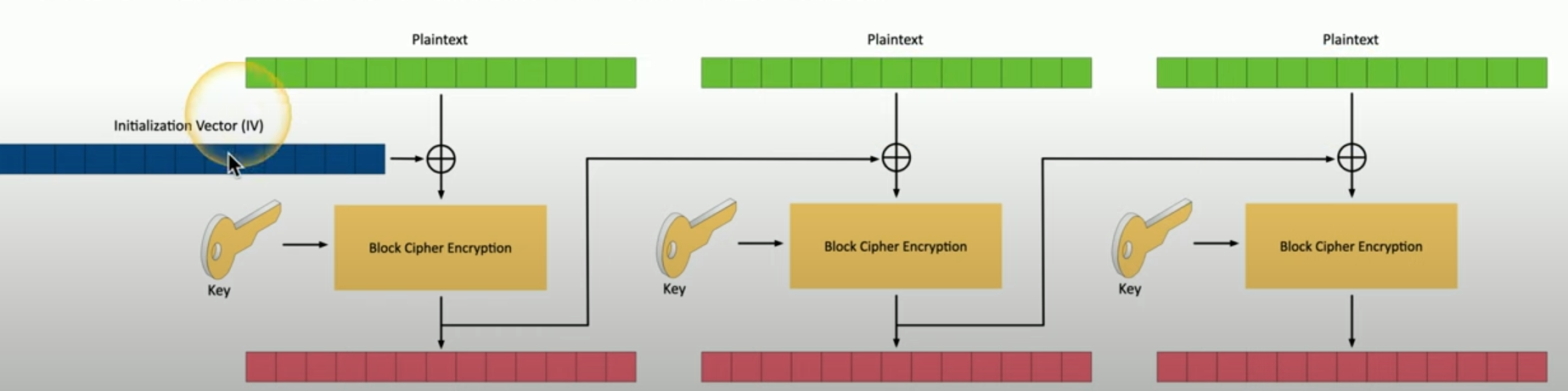
counter (ctr)
turns block cipher into a stream cipher
each block of plaintext is XOred with a unique keystream block, which is generated by encrypting a counter value
gcm (galois/counter mode)
a mode of block ciphers that provides both confidentiality and authenticity.
combines the counter mode for encryption with a galois field
secure real-time transport protocol / secure rtp
adds security features to rtp
keep conversations private
encryption
encryption used : AES
s/mime
a standard for public key encryption and signing of emails
ensures confidentiality, message integrity, authentication, and non-repudiation
requires a PKI or similar organization of keys
secure post office protocol (POP)
use a starttls extension to encrypt
secure imap
use SSL
https
using ssl/tls
uses public key encryption
uses symmetric encryption
ftps file transfer protocol
uses ssl/tls to transfer files
sftp
uses ssh instead of ftps
provides confidentiality and integrity
ldaps
a application protocol for accessing and maintaining distributed directory information services over an IP network
uses ssl/tls to ensure confidentiality and integrity of data transmitted over the network
dnssec
a way for us to validate the information we get from a dns server
snmpv3
designed to provide secure management of network devices
uses encryption that provides
confidentiality
integrity
authentication
what does snmpv3 mean?
simple network management protocol version 3
network address allocation
refers to the process of assigning ip addresses to devices on a network
A security feature that helps prevent rogue DHCP servers from distributing malicious IP addresses
boot security
involves measures and technologies to ensure that the boot process of a computer system is secure from threats such as malware and authorized changes
UEFI BIOS
BIOS includes the manufacturer’s public key
digital signature is checked during a bios update
bios prevents unauthorized writes to the flash
measured boot
a process that allows us to see if any changes have occurred with the operating system
records measurements of each component in the boot process, including firmware, bootloader, and operating system kernel.
boot attestation
a security mechanism that ensures the integrity of the boot process by verifying that all boot components have not been tampered with and are in a trusted state
static code analysis
analysis code before it is run to locate vulnerabilities in code
dynamic code analysis
is a security testing technique that involves analyzing a program’s behavior while it is running
fuzzing
send random input to an application
looking for something to happen like a (buffer overflow)
self encrypting drive (sed)
storage drives that automatically and transparently encrypt data at the hardware level
all data written to the drive is encrypted, and data read from the drive is decrypted, without requiring user intervention
encryption and decryption are handled by the driver’s hardware, making the process transparent to the user and operating system
full disk encryption (fde)
is a security mechanism that encrypts all the data on a disk drive, including the operating system, applications, and user data.
dhcp snooping
ensures that message from authorized dhcp servers are allowed
ensures that only authorized DHCP servers can provide ip addresses and network configurations to clients
utm
is a comprehensive security solution that integrates multiple security features and services into a single device or platform
Provides an all-in-one solution to protect against various types of network threats
what does utm mean?
unified threat management
nat
is a network service that allows multiple devices on a local network to access external networks, such as the internet, using a single public ip address
purpose: conserve the number of public ip addresses needed by an organization by allowing multiple devices to share a single public ip
wpa2
is a security protocol designed to secure wireless networks
encryption used: ccmp - counter/cbc-mac protocol
message integrity check used : cbc-mac
wpa3
is the latest security protocol designed to secure wireless networks
encryption used : Galois/Counter Mode Protocol
Message Integrity Check used : Galois Message Authentication Code (GMAC)
WPA3 Authentication Improvements
uses SAE
ensures both parties are authenticated
each session key is different
enhances security by ensuring that past sessions remain secure even if a session key is compromise
eap
is an authentication framework used in network access control scenarios
supports multiple authentication mechanisms
used in conjunction with 802.1X
ieee 802.1x
provides a method to authenticate devices and users before allowing network access
ieee 802.1x is used in conjunction with what database service ?
RADIUS, LDAP, TACACS+
eap-fast (flexible authentication via secure tunneling)
does not require a digital signature
uses a pac (protected access credential)
uses tls to ensure a secure tunnel between the client and the authentication server
peap
ensures that authentication information is securely transmitted by encapsulating it within a TLS
encryption used : tls
authentication : the server is authenticated using a digital certificate, while the client can be authenticated using various eap methods within the tunnel
eap-tls
requires digital certificates on all devices server and client side
the server presents its digital certicate to the client and the client presents its digital certificate to the server
a secure tls tunnel is then established after verifying certificates
eap-ttls
creates a tls tunnel and allows various inner authentication methods
the server presents a digital certificate to authenticate itself to the client (only one digital certificate)
within the tls tunnel various inner methods can be used pap, chap, ms-chap, and ms-chapv2
radius federation
allows users to authenticate across multiple domains or organizations using their existing credentials
radius
performs authentication and authorization of users
federation
establishes a trust relationship between different radius servers, enabling them to communicate and authenticate users from other domains
C. DNS Poisoning - Correct
A. USB data blocker - Correct
A. Reverse Proxy (study up on this term) - Correct
A. A phishing email stating a cash settlement has been awarded but will expire soon - Correct
C. SQLi -Correct
A. Data anonymization - Correct
A. Classify the data - Correct
C.XSRF - Correct
D. Password history - Correct
B. Wildcard - Correct
What to study for on 1-10 Section
Wildcard - covers unlimited subdomains with a single cert (example of a subdomain (support.google.com, it.google.com, shop.google.com)
- a wildcard certificate for *google.com would secure all these subdomains
Subject alternative name - (covers multiple domains or subdomains with a single certificate)
-www.google.com
-mail.google.com
-www.roblox.com
-rent.roblox.com
XSRF (Cross site request forgery, will inject the POST request to change email, address or shipping, or transfer funds)
XSS (Cross Site Scripting occurs when attackers try to inject JavaScript into the client’s website)
___________________________________________
Sections 2
A. DLP
A. Replacing the traditional key with an RFID key
C. Masking incorrect Hashing is correct answer
C.SSH
A. Perform a mathematical operation on the passwords that will convert them into unique strings.
A. Steganography
A. Password complexity
B. FIM
A. To validate the integrity of the files
C pathping 10.10.10.0 -p 80
What to study for on 11-21 Section
The difference between tokenization and masking
Which of the following can be used by a monitoring tool to compare values and detect passwords leaks without providing the actual credentials
A. Hashing Most Voted
B. Tokenization
C. Masking
D. Encryption
Hashing is a cryptographic technique that takes input data (in this case, passwords) and converts it into a fixed-size string of characters, which is the hash value. The hashing process is one-way, meaning it is not feasible to reverse the hash and obtain the original password from the hash value alone.
A company recently experienced an inside attack using a corporate machine that resulted in data compromise. Analysis indicated an unauthorized change to the software circumvented technological protection measures. The analyst was tasked with determining the best method to ensure the integrity of the systems remains intact and local and remote boot attestation can take place. Which of the following would provide the BEST solution?
A. HIPS
B. FIM
C. TPM Most Voted
D. DLP
TPM (Trusted Platform Module) is a hardware-based security component that is designed to provide secure cryptographic functions and protect sensitive data on a computer or server. It is commonly used to ensure the integrity and security of a system's boot process and to support local and remote attestation.
A security manager has tasked the security operations center with locating all web servers that respond to an unsecure protocol. Which of the following commands could an analyst run to find the requested servers?
A. nslookup 10.10.10.0
B. nmap -p 80 10.10.10.0/24 Most Voted
C. pathping 10.10.10.0 -p 80
D. ne -l -p 80
reasoning for answer B 1. nmap: nmap is a powerful network scanning tool used to discover hosts and services on a computer network. 2. -p 80: This option specifies that nmap should scan for open ports on port 80, which is the default port used for HTTP (unsecure web) communication. 3. 10.10.10.0/24: This is the target network range or IP address range that the analyst wants to scan. The /24 indicates a subnet mask of 255.255.255.0, meaning it will scan all IP addresses in the 10.10.10.0 network.
____________________________________________________
Section 3
False Acceptance
GDPR
B, A
C
A. Geographic dispersal
A. EAP correct answer was AES
B. SWG correct but I did not know what it was
C. Implement access control vestibules.
D. Diagrams
TLS (Transport Layer Socket/Secure) - encrypts network traffic that is in transit
A security engineer is deploying a new wireless network for a company. The company shares office space with multiple tenants. Which of the following should the engineer configure on the wireless network to ensure that confidential data is not exposed to unauthorized users?
A. EAP Most Voted
B. TLS
C. HTTPS
D. AES
AES - provides confidentiality to both data-at-rest and data-in-transit, preventing unauthorized users from seeing either
EAP - is an Authentication Protocol (authentication does not provide confidentiality) . Authentication encompasses processes that allows systems and networks to determine if a user is who they say they are
SWG is a proxy-based firewall, content filter, and intrusion detection/prevention system that mediates user access to Internet sites and service
29. Which of the following would BEST provide a systems administrator with the ability to more efficiently identify systems and manage permissions and policies based on location, role, and service level?
Answer: Standard naming conventions
These are naming frameworks used for naming hardware assets, and for digital assets such as accounts and virtual machines in a consistent way. The naming strategy should allow administrators to identify the type and function of any particular resource or location at any point.
=============================
Helpful Info:
Domain Services - Services that stores centralized directory information and lets users and domains communicate. When a user attempts to connect to a device or resource on a network, this service provides login authentication, verifying the user's login credentials and access permissions.
Baseline configuration - A documented set of specifications for an information system, or a configuration item within a system, that has been formally reviewed and agreed on at a given point in time, and which can be changed only through change control procedures.
____________________________________________________________
Section 4
C
C. what is a container? a container is a like a sandbox where one application can run all of its services
D. transference.
B
B
A
A
C. DDoS attack
C. Longer key longevity correct answer is High data entropy
C. A zero-day exploit is initially undetectable, and no patch for it exists.
Question #32
A security analyst is concerned about critical vulnerabilities that have been detected on some applications running inside containers. Which of the following is the BEST remediation strategy ?
Answer (B. Update the base container image and redeploy the environment
Updating the host in which the containers are running may not patch vulnerabilities inside the containers. Updating the base container image will ensure any known vulnerabilities are patched before the container is redeployed. This is going to save time and ensure all containers are patched securely and effectively.
Which of the following will increase cryptographic security?
A. High data entropy Most Voted
B. Algorithms that require less computing power
C. Longer key longevity
D. Hashing
Entropy refers to the randomness of a cryptographic algorithm. A higher level of randomness results in a higher level of security when using the algorithm. A lack of entropy results in a weaker algorithm and makes it
____________________________________________
Section 5
C
D
D
B
A
C
B
C. Unknown backdoor
B
C
Research- False Rejection Rate and False Acceptance Rate
Research - TAXXI
Question #46
D. Implement a TAXII server. Most Voted
An organization wants to participate in threat intelligence information sharing with peer groups. Which of the following would MOST likely meet the organization's requirement?
Reasoning for the answer | A TAXII server is a client that exchanges standardized and anonymized cyber threat intelligence among users. It works as a venue for sharing and collecting Indicators of compromise, which have been anonymized to protect privacy.
Question #50
An amusement park is implementing a biometric system that validates customers' fingerprints to ensure they are not sharing tickets. The park's owner values customers above all and would prefer customers' convenience over security. For this reason, which of the following features should the security team prioritize
FIRST?
A. Low FAR
B. Low efficacy
C. Low FRR Most Voted
D. Low CER
Reasoning For The Answer : False Acceptance Rate (FAR) is a metric for bio-metric performance that determines the number of instances where unauthorized persons were incorrectly authorized. False Rejection Rate (FRR) is a metric that determines the number of instances where an authorized person are incorrectly rejected.
If the emphasis is security, then making sure the False Acceptance Rate is low as a low FAR rate means a lower possibility for someone to be authorized who shouldn't. If the emphasis is convenience, then you'd want to make sure the False Rejection Rate is low as a low FRR means a lower possibility for someone to be rejected who should be authorized.
______________________________________________
D) NIST
D) Remote Access Trojan correct answer is Logic Bomb
B) what is CSIRT though?
D) Correct answer C)
A)
B)
C)
D)
A)
C) Answer is B which we thought at first research what SOAR is
Question #51
Which of the following organizations sets frameworks and controls for optimal security configuration on systems?
A. ISO
B. GDPR
C. PCI DSS
D. NIST Most Voted
Question #52
An organization discovered files with proprietary financial data have been deleted. The files have been recovered from backup, but every time the Chief Financial
Officer logs in to the file server, the same files are deleted again. No other users are experiencing this issue. Which of the following types of malware is MOST likely causing this behavior?
A. Logic bomb Most Voted
B. Cryptomalware
C. Spyware
D. Remote access Trojan
Answer Reasoning: A logic bomb is inserted code that will intentionally set off a malicious function when specified conditions are met. In this question, the logic bomb could be related to when the CFO logs in as no other user is experiencing this issue.
It is not a RAT because a RAT - malware an attacker uses to remotely control an infected computer
Question #54
During an incident response, an analyst applied rules to all inbound traffic on the border firewall and implemented ACLs on each critical server. Following an investigation, the company realizes it is still vulnerable because outbound traffic is not restricted, and the adversary is able to maintain a presence in the network.
In which of the following stages of the Cyber Kill Chain is the adversary currently operating?
A. Reconnaissance
B. Command and control
C. Actions on objective
D. Exploitation
B because they are maintaining or controlling the foothold they have on the victim's machine
Question #55
A recent security breach exploited software vulnerabilities in the firewall and within the network management solution. Which of the following will MOST likely be used to identify when the breach occurred through each device?
A. SIEM correlation dashboards
B. Firewall syslog event logs
C. Network management solution login audit logs
D. Bandwidth monitors and interface sensors
Question #56
Which of the following is the FIRST environment in which proper, secure coding should be practiced?
A. Stage
B. Development
C. Production
D. Test
Dont» Throw» Sausage» Pizza
Development » Testing» Staging » Production
Question #57
A cloud service provider has created an environment where customers can connect existing local networks to the cloud for additional computing resources and block internal HR applications from reaching the cloud. Which of the following cloud models is being used?
A. Public
B. Community
C. Hybrid
D. Private
Question #58
An organization has developed an application that needs a patch to fix a critical vulnerability. In which of the following environments should the patch be deployed
LAST?
A. Test
B. Staging
C. Development
D. Production
Question #59
An organization is building backup server rooms in geographically diverse locations. The Chief Information Security Officer implemented a requirement on the project that states the new hardware cannot be susceptible to the same vulnerabilities in the existing server room. Which of the following should the systems engineer consider?
A. Purchasing hardware from different vendors
B. Migrating workloads to public cloud infrastructure
C. Implementing a robust patch management solution
D. Designing new detective security controls
Question #60
A security analyst is working on a project to implement a solution that monitors network communications and provides alerts when abnormal behavior is detected.
Which of the following is the security analyst MOST likely implementing?
A. Vulnerability scans
B. User behavior analysis
C. Security orchestration, automation, and response
D. Threat hunting
Reason: As per Comptia objectives, User behavior Analysis comes under SIEM. Well as the Question asks whats most likely the solution being implemented hence User behavior analysis seems to be the direct answer. SOAR simply means you are adding automation and servers handle the security tasks automatically and take action. happy to discuss. Some of the question are to confuse so i ll stick to most direct connection in this case. B
C. Security orchestration, automation, and response (SOAR): SOAR platforms help automate and coordinate security operations tasks. While they can work with monitoring tools, they themselves are not primarily focused on detecting abnormal network behavior.
B. User behavior analysis: UBA involves monitoring the activities and behaviors of users on a network to detect anomalies that could indicate potential security threats. This fits the description of monitoring network communications and alerting on abnormal behavior.
_______________________________________________________-
Section 6
D, B
A. Malicious script
D. Smishing
A. Train the team to identify the difference between events and incidents.
D. WAF and NIPS
B. Perform a physical-to-virtual migration.
D. Block port 3389 inbound from untrusted networks.
B. Federation
C. Implement a SOAR with customizable playbooks.
A. PKI
Question #65
A cybersecurity administrator needs to implement a Layer 7 security control on a network and block potential attacks. Which of the following can block an attack at
Layer 7? (Choose two.)
B. NIPS (Network Intrusion Prevention System): A NIPS is an intrusion detection system that can actively block and prevent detected threats. It operates at Layer 7 of the OSI model, just like NIDS (Network Intrusion Detection System). However, NIPS goes beyond detection and takes proactive measures to block potential attacks at the network level.
- D. WAF (Web Application Firewall): A WAF is a security control that operates at Layer 7 of the OSI model. It is specifically designed to monitor, filter, and block HTTP/HTTPS traffic to and from web applications. By doing so, it can prevent web-based attacks, such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
Question #68
Which of the following uses SAML for authentication?
A. TOTP
B. Federation Most Voted
C. Kerberos
D. HOTP
Answer: B: Federation, or identity federation, defines policies, protocols, and practices to manage identities across systems and organizations. Federation’s ultimate goal is to allow users to seamlessly access data or systems across domains. Federation is enabled through the use of industry standards such as Security Assertion Markup Language (SAML).
TAKE A LOOK AT THESE QUESTIONS
HIDS
NIPS
HSM
WAF
NAC
NIDS
______________________________________________________________
SECTION 7
C. VDI
C. Proprietary
B. A CASB , C. An NG-SWG
C. COPE and VDI
A READ! Answer was B. Keylogger because
A
C
A
A
A
Go Over This Entire Section & Vocabulary
C. COPE and VDI
D. CYOD and VMs
Rainbow attack - uses tables of reversed hashes to crack passwords
Question #75Topic 1
Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities. After further investigation, a security analyst notices the following:
✑ All users share workstations throughout the day.
✑ Endpoint protection was disabled on several workstations throughout the network.
✑ Travel times on logins from the affected users are impossible.
✑ Sensitive data is being uploaded to external sites.
All user account passwords were forced to be reset and the issue continued.
Which of the following attacks is being used to compromise the user accounts?
A. Brute-force
B. Keylogger Most Voted
RC. Dictionary
D. Rainbow
Reasoning between the answer B
A keylogger or keystroke logger is a type of monitoring software that can be used to collect keystrokes that you type. A keylogger was likely used to capture various sensitive information and credentials. As the issue continued after the password reset, the keylogger was still capturing information as it wasn't removed.
=========================
Brute-force - trail and error attempts to guess login info
Dictionary - a form of brute force attack that uses common words, phrases and variations
Rainbow - uses tables of reversed hashes to crack passwords’
PROFESSOR MESSER TAKE AWAYS
Credential Harvesting
running a malicious script on a user local pc that pulls your credentials from browsers (Google Chrome, Firefox) and sends it to the attacker
What is the difference between a worm and a virus?
A virus needs human interaction
A worm does not
Rootkit
modifies core systems files
embeds itself in the kernel
becomes hard to hide one it is installed
Logic Bomb
Waits for a predefined event to launch malicious code
Hashes cannot be reverted to plaintext
Spraying Attack
tries a few passwords before moving on to the next
avoids account lockouts
non persistent xss attack
an attack that targets 1 user
an attacker usually sends an user an email and the user has to click the link in the email for the attack to be run
persistent xss attack
an attack that targets anyone
can be posted on a forum site and anyone who visits this site will execute the malicious script
what does XSRF mean ?
cross-site request forgery
what does SSRF mean?
server-side request forgery
api attacks
are requests that are sent from a mobile device to a server to the database
instead of sending HTTP Get request the mobile device sends a API Requests and gets an API Responses back

what is a STIX ?
a language that is used to share cyber threat information
what transport is used to transport cyber threat information?
TAXII
academic journals?
detailed information about attacks and how other users have dealt with them
best security features
how the attack looks (breaks the attack down)
rfc |request for comment|
a way to track and formalize a set of standards anyone can use
what doe soar stand for
security orchestration automation response
whit team
not a side
manages the rules of a pen test exercise between red and blue team
2.0
diagrams
a diagram (map) of where everything is located on the network
ip schema
helps configure assign ip address to users, printers, routers
helps avoid duplicates ip addressing
data masking
is a data security technique used to protect sensitive information by obscuring or hiding the actual data
social security number
xxx-xxx-1345
tokenization
replace sensitive data with a non-sensitive placeholder
SSN 266-12-1112 is now 123-456-7890
hashing verifies?
integrity
what are sha-1, sha-2, and sha-3 and md5 all examples of?
Hashes
api considerations
these attacks are very similar to any other attack except the endpoint used in a phone and not a computer, so the information sent is (API Request)
security measures put in place to protect api interactions
fake telemetry
training the machine with fake data to the machine
dns sinkhole
attack can redirect users to malicious sites
provides false information to malicious traffic, redirecting it to a controlled IP address.
SaaS
example of this is google mail
the software is provided to you all you have to do is login
they maintained and anything related to that software is controlled by google
PaaS
gives you everything you need to focus on the application
all you need to do is focus on the application and data
you get the server, networking, etc.
Edge Computing
data is processed locally instead of going to the internet
Fog Computing
some of the data being processed will go to the cloud
Container
contains everything you need to run an application
apps can’t interact with each other
one operating system
Virtualization
can have multiple OS systems
Serverless Architecture
Developers can deploy code without managing server infrastructure, leading to faster development cycle
Pay only for the actual compute time and resources consumed, with no charges for idle time.
Transit Gateway
is used by a user to connect to multiple VPC's on the network, the transit gateway is also used to connect multiple VPC's that have different application running on them.
Service Integration
Streamlines operations by allowing different services and applications to work together seamlessly.
SDN
is an approach to networking that uses software-based controllers or application programming interfaces (APIs) to communicate with underlying hardware infrastructure and direct traffic on a network.
What is SDV?
Software Defined Visibility
What is SDN?
Software Defined Networking
VM Sprawl
happens when there are to many VMs being built and no one is keeping track of this deprovisioning of the VM’s
Where should code be tested first?
the sandbox
Don’t Throw Sausage Pizza
Development / Testing / Staging / Production
Scalability
the ability to increase the workload in a given infrastructure
Elasticity
the ability to increase or decrease the available resources as the workload changes
Stored Procedures
SQL procedures that cannot be modified
protects attacker from knowing the exact location of the database
Normalization
check and correct all input
a zip code should be only X characters long with a letter in the X column
Version control
used to make sure a file application/file has not been changed over time
used to track changes and revert back to previous version if needed
Federation
allows someone to access your network using credentials stored with a third party
example
Log in with Twitter
Log in with Facebook
Log in with Google
What authentication is used to allow someone to access your network using credentials stored with a third party?
Federation
Attestation
used to prove the hardware is really yours
HOTP
a one time password that changes
uses hmac and counter mode
Gait Analysis
This identifies a person based on how they walk
UPS
short term power supply for when power goes out this does not last for a very long time
Generators
long time power supply for when the power goes out
can power entire buildings
SAN
a network drive (provides storage for servers)
Incremental
this back up backs up everything since the last incremental backup
Tuesday = Tuesdays backups, Wednesday = Wednesday’s backup

Differential
this back up backs up all files that have changed since the last full backup
Tuesday = Tuesdays backups, Wednesday = Tuesday’s and Wednesdays backups and so on

NAS provides
file level access
SAN provides
block level access
What is a FPGA
Field programmable gate array (FPGA)
Characterisitcs of a FPGA
is an integrated circuit that can be configured by a customer or a designer after manufacturing
Can be reprogrammed to update functionality or fix issues even after deployment
What is a Raspberry Pi?
is a small, affordable single-board computer
where are raspberry pi most often used ?
IOT devices
smart meter
measure power and water usage
zigbee
a high-level communication protocol using low power, low power data rate
based on the IEEE 802.15.4
used in IoT devices
mantraps
consists of two interlocking doors, where the first door must be closed and locked before the second door can be opened
faraday cages
blocks electromagnetic fields
air gap
physical separation between networks
secure network and insecure network
separate customer infrastructures
pulverizer
completely destroy the disk
degaussing
remove the magnetic field
destroys the drive data and renders the drive unusable
key stretching
how to make a key stronger?
hash the password. hash the hash of the password. and continue
lightweight cryptography
often found in IoT devices
provides cryptography to devices that have less cpu power
ECC
uses smaller keys than asymmetric encryption
provides strong cryptographic security with smaller key sizes making it suitable for device with limited computational resources
What is ECC best used on?
on devices with limited computation resources
What does ECC stand for?
Elliptic curve cryptography
perfect forward secrecy
ensures sessions keys will not be compromised even if the server’s private key is compromised
each session uses a unique session key that cannot be derived from any other session key
post-quantum cryptography
breaks our existing encryption mechanism
quantum computing
computers based on quantum physics
a new computing technology
ephemeral
refers to temporary keys that are generated and used for a single session
symmetric encryption
A single shared key
asymmetric encryption
public key cryptography
two or more keys
involves a public key and private key
blockchain
is a decentralized and distributed digital ledger technology that records transactions across many computers in such a way that the registered transactions cannot be altered retroactively.
homomorphic encryption
performs calculation on data while the data is still encrypted
entropy
key randomization
stream cipher suites
refers to a category of encryption algorithms that encrypt plaintext one bit or byte at a time
what encryption is used with stream ciphers?
symmetric encryption
block cipher suites
refers to a category of encryption algorithms that encrypt plaintext blocks at a time
what encryption is used with block ciphers?
symmetric encryption
asymmetric encryption is not used with
cipher suites
ecb
each block of plaintext is encrypted independently using the same key,
-using advanced encryption standard (AES)
cbc (cipher block chain)
block ciphers that enhance security by introducing dependencies between blocks,
each plaintext block is XOred with the previous ciphertext block before being encrypted
adds additional randomization

counter (ctr)
turns block cipher into a stream cipher
each block of plaintext is XOred with a unique keystream block, which is generated by encrypting a counter value
gcm (galois/counter mode)
a mode of block ciphers that provides both confidentiality and authenticity.
combines the counter mode for encryption with a galois field
secure real-time transport protocol / secure rtp
adds security features to rtp
keep conversations private
encryption
encryption used : AES
s/mime
a standard for public key encryption and signing of emails
ensures confidentiality, message integrity, authentication, and non-repudiation
requires a PKI or similar organization of keys
secure post office protocol (POP)
use a starttls extension to encrypt
secure imap
use SSL
https
using ssl/tls
uses public key encryption
uses symmetric encryption
ftps file transfer protocol
uses ssl/tls to transfer files
sftp
uses ssh instead of ftps
provides confidentiality and integrity
ldaps
a application protocol for accessing and maintaining distributed directory information services over an IP network
uses ssl/tls to ensure confidentiality and integrity of data transmitted over the network
dnssec
a way for us to validate the information we get from a dns server
snmpv3
designed to provide secure management of network devices
uses encryption that provides
confidentiality
integrity
authentication
what does snmpv3 mean?
simple network management protocol version 3
network address allocation
refers to the process of assigning ip addresses to devices on a network
A security feature that helps prevent rogue DHCP servers from distributing malicious IP addresses
boot security
involves measures and technologies to ensure that the boot process of a computer system is secure from threats such as malware and authorized changes
UEFI BIOS
BIOS includes the manufacturer’s public key
digital signature is checked during a bios update
bios prevents unauthorized writes to the flash
measured boot
a process that allows us to see if any changes have occurred with the operating system
records measurements of each component in the boot process, including firmware, bootloader, and operating system kernel.
boot attestation
a security mechanism that ensures the integrity of the boot process by verifying that all boot components have not been tampered with and are in a trusted state
static code analysis
analysis code before it is run to locate vulnerabilities in code
dynamic code analysis
is a security testing technique that involves analyzing a program’s behavior while it is running
fuzzing
send random input to an application
looking for something to happen like a (buffer overflow)
self encrypting drive (sed)
storage drives that automatically and transparently encrypt data at the hardware level
all data written to the drive is encrypted, and data read from the drive is decrypted, without requiring user intervention
encryption and decryption are handled by the driver’s hardware, making the process transparent to the user and operating system
full disk encryption (fde)
is a security mechanism that encrypts all the data on a disk drive, including the operating system, applications, and user data.
dhcp snooping
ensures that message from authorized dhcp servers are allowed
ensures that only authorized DHCP servers can provide ip addresses and network configurations to clients
utm
is a comprehensive security solution that integrates multiple security features and services into a single device or platform
Provides an all-in-one solution to protect against various types of network threats
what does utm mean?
unified threat management
nat
is a network service that allows multiple devices on a local network to access external networks, such as the internet, using a single public ip address
purpose: conserve the number of public ip addresses needed by an organization by allowing multiple devices to share a single public ip
wpa2
is a security protocol designed to secure wireless networks
encryption used: ccmp - counter/cbc-mac protocol
message integrity check used : cbc-mac
wpa3
is the latest security protocol designed to secure wireless networks
encryption used : Galois/Counter Mode Protocol
Message Integrity Check used : Galois Message Authentication Code (GMAC)
WPA3 Authentication Improvements
uses SAE
ensures both parties are authenticated
each session key is different
enhances security by ensuring that past sessions remain secure even if a session key is compromise
eap
is an authentication framework used in network access control scenarios
supports multiple authentication mechanisms
used in conjunction with 802.1X
ieee 802.1x
provides a method to authenticate devices and users before allowing network access
ieee 802.1x is used in conjunction with what database service ?
RADIUS, LDAP, TACACS+
eap-fast (flexible authentication via secure tunneling)
does not require a digital signature
uses a pac (protected access credential)
uses tls to ensure a secure tunnel between the client and the authentication server
peap
ensures that authentication information is securely transmitted by encapsulating it within a TLS
encryption used : tls
authentication : the server is authenticated using a digital certificate, while the client can be authenticated using various eap methods within the tunnel
eap-tls
requires digital certificates on all devices server and client side
the server presents its digital certicate to the client and the client presents its digital certificate to the server
a secure tls tunnel is then established after verifying certificates
eap-ttls
creates a tls tunnel and allows various inner authentication methods
the server presents a digital certificate to authenticate itself to the client (only one digital certificate)
within the tls tunnel various inner methods can be used pap, chap, ms-chap, and ms-chapv2
radius federation
allows users to authenticate across multiple domains or organizations using their existing credentials
radius
performs authentication and authorization of users
federation
establishes a trust relationship between different radius servers, enabling them to communicate and authenticate users from other domains