IB Digital Society - The Ultimate Study Guide
Chapter 1: What is Digital Society?
Introduction
In today's rapidly evolving world, the concept of a digital society has become increasingly relevant. The International Baccalaureate (IB) syllabus for Digital Society aims to explore this phenomenon in depth. This study note will provide a detailed overview of what constitutes a digital society, breaking down complex ideas into digestible sections and using examples for clarity.
What is a Digital Society?
Definition
A digital society is a community that is heavily influenced and shaped by digital technologies. These technologies include the internet, mobile devices, social media, and other forms of digital communication and data processing.
Note:
Understanding the concept of a digital society is crucial for grasping the broader implications of technology on human interactions, economics, and governance.
Key Characteristics
Connectivity
One of the defining features of a digital society is the high level of connectivity among its members. This connectivity is facilitated by:
Internet Access: The backbone of a digital society is widespread internet access, allowing people to connect and communicate globally.
Mobile Devices: Smartphones and tablets enable constant connectivity, making information and communication tools available at our fingertips.
Example:
For instance, in South Korea, over 95% of the population has internet access, making it one of the most connected societies in the world.
Digital Communication
Digital societies rely heavily on digital forms of communication. This includes:
Social Media: Platforms like Facebook, Twitter, and Instagram allow for instant sharing of information and social interaction.
Email and Messaging Apps: Tools like Gmail, WhatsApp, and Slack facilitate both personal and professional communication.
Tip:
Mastering digital communication tools is essential for effective participation in a digital society.
Data-Driven Decision Making
In a digital society, data is a valuable resource. It is used to inform decisions in various sectors such as:
Business: Companies use data analytics to understand consumer behavior and improve their products and services.
Government: Governments utilize data for policy-making, public services, and improving governance.
Example:
Amazon uses data analytics to recommend products to users based on their browsing and purchase history.
Digital Economy
Digital technologies significantly influence the economy in a digital society. This includes:
E-commerce: Online shopping platforms like Amazon and Alibaba have revolutionized retail.
Digital Payments: Services like PayPal, Apple Pay, and cryptocurrency facilitate cashless transactions.
Common Mistake:
Assuming that a digital economy only includes online shopping is a misconception. It also encompasses digital banking, online services, and more.
Social Implications
Social Interaction
Digital technologies have transformed how we interact socially. This can be seen in:
Virtual Communities: Online forums and social media groups allow people to connect based on shared interests, regardless of geographical location.
Remote Work: Digital tools enable people to work from anywhere, changing the traditional office environment.
Example:
The rise of remote work during the COVID-19 pandemic has shown the potential for digital tools to maintain productivity outside traditional office settings.
Privacy and Security
With increased connectivity comes concerns about privacy and security. Key issues include:
Data Privacy: The collection and use of personal data by companies and governments raise questions about privacy rights.
Cybersecurity: Protecting digital systems from cyber attacks is crucial to maintaining trust in a digital society.
Tip:
Regularly updating passwords and using two-factor authentication can enhance personal cybersecurity.
Ethical Implications
Digital Divide
The digital divide refers to the gap between those who have access to digital technologies and those who do not. This divide can be based on:
Geography: Rural areas often have less access to high-speed internet compared to urban areas.
Socioeconomic Status: Wealthier individuals are more likely to have access to the latest technologies.
Note:
Addressing the digital divide is essential for ensuring equitable access to the benefits of a digital society.
Ethical Use of Data
The ethical use of data involves considerations such as:
Consent: Ensuring that individuals consent to the collection and use of their data.
Transparency: Companies and governments should be transparent about how they use data.
Example:
GDPR (General Data Protection Regulation) in the European Union is a regulation that aims to protect individuals' data privacy and increase transparency.
Digital Literacy
Definition: The ability to use digital technologies effectively and responsibly.
Components:
Technical Skills: Knowing how to use digital tools and platforms.
Critical Thinking: Evaluating digital content for credibility and relevance.
Ethical Understanding: Being aware of the ethical implications of digital technology use.
Impact on Education
E-learning Platforms: Tools like Coursera, Khan Academy, and Zoom have made education more accessible.
Digital Classrooms: Integration of technology in classrooms enhances learning experiences through interactive content and real-time feedback.
Smart Cities
Definition: Urban areas that use digital technologies to enhance performance and well-being.
Components:
Smart Infrastructure: Efficient energy use, smart grids, and waste management.
Transportation: Intelligent traffic systems and autonomous vehicles.
Public Services: Digital platforms for public services and citizen engagement.
Conclusion
Understanding what constitutes a digital society is fundamental to navigating the complexities of our modern world. By examining its key characteristics, social implications, and ethical considerations, we gain a comprehensive view of how digital technologies shape our lives.
Note:
As digital technologies continue to evolve, so too will the concept of a digital society. Staying informed and adaptable is key to thriving in this ever-changing landscape.
Chapter 2: Data
Introduction
In the context of the Digital Society, data plays a crucial role in shaping how we interact, make decisions, and understand the world around us. This study note will delve into various aspects of data, including its types, collection methods, storage, analysis, and ethical considerations. By breaking down these complex ideas into smaller sections, we aim to provide a comprehensive understanding of the topic.
Types of Data
Data can be broadly classified into two categories: qualitative and quantitative.
Qualitative Data
Qualitative data is descriptive and conceptual. It is used to capture information that is not easily reduced to numbers. This type of data includes:
Text: Written words, such as interview transcripts or open-ended survey responses.
Images: Photographs, drawings, or any visual representations.
Audio: Recordings of speech, music, or other sounds.
Video: Moving images, often combined with audio.
Example:
An example of qualitative data is customer feedback collected through open-ended survey questions. Responses like "The product is very user-friendly" provide insights that are not easily quantifiable.
Quantitative Data
Quantitative data is numerical and can be measured. It includes:
Discrete Data: Countable data, such as the number of students in a class.
Continuous Data: Measurable data, such as temperature or height.
Example:
An example of quantitative data is the number of visitors to a website per day. This data can be represented as a numerical value, such as 500 visitors.
Data Collection Methods
Collecting data accurately is essential for reliable analysis. Common methods include:
Surveys and Questionnaires
Surveys and questionnaires are tools used to gather information from a large number of respondents. They can be administered online, by phone, or in person.
Note:
Ensure questions are clear and unbiased to avoid skewed results.
Observations
This method involves systematically recording behaviors or events as they occur.
Experiments
Experiments involve manipulating one variable to see its effect on another, often in a controlled environment.
Secondary Data
Secondary data is information that was collected by someone else for a different purpose but is being utilized for a new analysis.
Tip:
Always verify the reliability and validity of secondary data before using it.
Data Storage
Storing data securely and efficiently is critical. Common storage methods include:
Databases
Databases are organized collections of data that allow for easy access, management, and updating. They can be relational (SQL) or non-relational (NoSQL).
Cloud Storage
Cloud storage services, such as Google Drive or AWS, provide scalable and accessible storage solutions.
Local Storage
Local storage refers to data stored on physical devices like hard drives or USB sticks.
Common Mistake:
Relying solely on local storage without backups can lead to data loss in case of hardware failure.
Data Analysis
Analyzing data helps to extract meaningful insights. Common techniques include:
Inferential Statistics
Inferential statistics make predictions or inferences about a population based on a sample of data. Techniques include hypothesis testing, regression analysis, and correlation.
Data Visualization
Visualizing data through charts, graphs, and maps helps to communicate findings effectively.
Tip: Tools like Tableau, Power BI, and Excel are useful for creating data visualizations.
Ethical Considerations
Handling data ethically is paramount. Key considerations include:
Privacy
We are respecting the privacy of individuals by anonymizing data and protecting personal information.
Consent
Ensuring informed consent is obtained from participants when collecting data.
Transparency
Being transparent about how data is collected, used, and shared.
Note: Ethical breaches can lead to legal consequences and loss of trust.
Conclusion
Understanding the different aspects of data—from types and collection methods to storage, analysis, and ethical considerations—is essential in the digital age. By mastering these concepts, you can make informed decisions and contribute positively to the digital society.
This study note provides a foundational understanding of data in the context of the Digital Society. For further reading, consider exploring additional resources on data science, statistics, and ethical data practices.
Chapter 3: Computer Algorithm
Algorithm Design and Analysis
Algorithm Design and Analysis is a fundamental aspect of computer science for creating efficient solutions to problems. This section of the IB Computer Science HL syllabus focuses on understanding, designing, and evaluating algorithms. Here's an in-depth look at the key concepts:
Understanding the Concept of an Algorithm
Definition: An algorithm is a step-by-step procedure or a set of rules to be followed in calculations or other problem-solving operations, especially by a computer.
Characteristics:
Unambiguous: Each step is clearly defined.
Finite: The algorithm terminates after a finite number of steps.
Effective: Each step is basic enough to be carried out (computable).
Writing and Understanding Pseudocode
Pseudocode: A high-level description of an algorithm using the structural conventions of programming languages but intended for human reading.
Purpose: Helps plan and conceptualize an algorithm before coding.
Structure:
Uses common programming constructs like loops, conditionals, and variables.
Avoids syntactical details of actual programming languages.
Example:
// A is an array of integers
BEGIN
max ← A[0]
FOR i ← 1 TO length(A) - 1 DO
IF A[i] > max THEN
max ← A[i]
END IF
END FOR
RETURN max
ENDAnalyzing the Efficiency of Algorithms using Big-O Notation
Big-O Notation: A mathematical notation that describes the upper bound of an algorithm's running time or space requirements in terms of the input size (n).
Purpose: To classify algorithms according to their worst-case or average-case performance and to compare the efficiency of different algorithms.
Common Big-O Classifications:
O(1): Constant time – the operation's time is independent of the input size.
O(log n): Logarithmic time – the operation's time grows logarithmically with the input size.
O(n): Linear time – the operation's time grows linearly with the input size.
O(n log n): Linearithmic time – the operation's time grows log-linearly with the input size.
O(n^2): Quadratic time – the operation's time grows quadratically with the input size.
O(2^n): Exponential time – the operation's time grows exponentially with the input size.
O(n!): Factorial time – the operation's time grows factorially with the input size.
Basic Algorithm Constructs
Sequence: Executing statements one after another in a specific order.
Example: Setting variables, performing arithmetic operations.
Selection: Making decisions based on conditions (if-else statements).
Example:
IF (condition) THEN
// execute this block
ELSE
// execute this block
END IFIteration: Repeating a block of code (loops).
Example:
FOR i ← 1 TO n DO
// execute this block
END FORRecursion: A function calls itself to solve smaller instances of the same problem.
Example:
Factorial computation
FUNCTION factorial(n)
IF n = 0 THEN
RETURN 1
ELSE
RETURN n * factorial(n - 1)
END IF
END FUNCTIONPractical Applications
Real-World Problem Solving: Algorithms are applied in various domains like sorting data, searching for information, network routing, and more.
Algorithmic Thinking: Developing the ability to break down problems into smaller, manageable parts and solving them systematically.
Basic Algorithm Constructs:
In computer science, algorithms are built using fundamental constructs that allow for the execution of instructions in a specific order. The basic constructs are sequence, selection, iteration, and recursion. Here is a detailed explanation of each:
Sequence
The sequence construct involves executing statements one after another in a specific order. This is the most straightforward control structure.
Example:
x ← 5
y ← 10
sum ← x + y
PRINT sumIn this example, the operations are performed in sequence: setting x to 5, y to 10, calculating the sum, and then printing the result.
Selection
Selection (also known as decision-making) allows the algorithm to choose different paths based on certain conditions. The most common selection constructs are if, else if, and else statements.
Example:
IF (temperature > 30) THEN
PRINT "It's hot outside."
ELSE IF (temperature > 20) THEN
PRINT "It's warm outside."
ELSE
PRINT "It's cold outside."
END IFIn this example, the algorithm selects different actions depending on the value of temperature.
Iteration
Iteration (or looping) allows the algorithm to repeat a block of code multiple times. There are several types of loops, including for, while, and do-while loops.
For Loop Example:
FOR i ← 1 TO 5 DO
PRINT i
END FORThis loop prints the numbers 1 to 5. The loop variable i starts at 1 and increments by 1 until it reaches 5.
While Loop Example:
i ← 1
WHILE (i ≤ 5) DO
PRINT i
i ← i + 1
END WHILEThis while loop achieves the same result as the for loop but checks the condition before each iteration.
Recursion
Recursion is a technique where a function calls itself to solve a smaller instance of the same problem. This is particularly useful for problems that can be broken down into similar sub-problems.
Factorial Example:
FUNCTION factorial(n)
IF (n = 0) THEN
RETURN 1
ELSE
RETURN n * factorial(n - 1)
END IF
END FUNCTIONIn this example, the factorial function calculates the factorial of a number n by calling itself with n - 1 until it reaches the base case (n = 0).
Practical Implementation
Understanding these constructs allows you to develop and implement algorithms for various tasks. Here are a few practical implementations using these constructs:
Example 1: Find the Maximum Number in an Array (Selection and Iteration)
FUNCTION findMax(array)
max ← array[0]
FOR i ← 1 TO length(array) - 1 DO
IF (array[i] > max) THEN
max ← array[i]
END IF
END FOR
RETURN max
END FUNCTIONThis function iterates through the array to find the maximum value.
Example 2: Sum of First n Natural Numbers (Recursion)
FUNCTION sum(n)
IF (n = 0) THEN
RETURN 0
ELSE
RETURN n + sum(n - 1)
END IF
END FUNCTIONThis recursive function calculates the sum of the first n natural numbers.
Linear Data Structures
Linear data structures are collections of elements arranged sequentially, where each element has a unique successor except the last element. These structures are fundamental in computer science for organizing data and facilitating various operations such as searching, sorting, and modifying elements. Here are the main types of linear data structures:
1. Arrays
An array is a collection of elements, each identified by an index. Arrays store elements of the same type in a contiguous memory location.
Declaration:
// ARRAY numbers[5] OF INTEGER
Initialization:
numbers[0] ← 10
numbers[1] ← 20
numbers[2] ← 30
numbers[3] ← 40
numbers[4] ← 50Accessing Elements:
PRINT numbers[2] // Outputs 30Advantages:
Simple to use and implement.
Efficient access to elements via indexing (O(1) time complexity).
Disadvantages:
Fixed size; cannot dynamically grow or shrink.
Insertion and deletion operations can be expensive (O(n) time complexity) if elements need to be shifted.
Linked Lists
A linked list is a collection of elements called nodes, where each node contains a data part and a reference (or link) to the next node in the sequence.
Types:
Singly Linked List: Each node points to the next node.
Doubly Linked List: Each node points to both the next and the previous nodes.
Circular Linked List: The last node points back to the first node.
Node Structure (Singly Linked List):
NODE
data: INTEGER
next: NODEExample Operations:
Insertion at the Beginning:
newNode ← CREATE_NODE(data)
newNode.next ← head
head ← newNodeDeletion from the Beginning:
IF head ≠ NULL THEN
temp ← head
head ← head.next
DELETE temp
END IFAdvantages:
Dynamic size; can grow and shrink as needed.
Efficient insertion and deletion operations (O(1) time complexity) if done at the beginning.
Disadvantages:
Inefficient access to elements (O(n) time complexity) since nodes must be traversed sequentially.
Extra memory is required for storing references.
Stacks
A stack is a linear data structure that follows the Last-In-First-Out (LIFO) principle. Elements can be added and removed only from the top of the stack.
Basic Operations:
Push: Add an element to the top of the stack.
Pop: Remove and return the top element of the stack.
Peek/Top: Return the top element without removing it.
isEmpty: Check if the stack is empty.
Example (Using an Array):
STACK stack[SIZE]
top ← -1
FUNCTION push(element)
IF top = SIZE - 1 THEN
PRINT "Stack Overflow"
ELSE
top ← top + 1
stack[top] ← element
END IF
END FUNCTIONFUNCTION pop()
IF top = -1 THEN
PRINT "Stack Underflow"
ELSE
element ← stack[top]
top ← top - 1
RETURN element
END IF
END FUNCTIONAdvantages:
Simple and easy to implement.
Useful in scenarios requiring backtracking (e.g., function calls, undo mechanisms).
Disadvantages:
Limited access to elements; only the top element can be accessed directly.
Queues
A queue is a linear data structure that follows the First-In-First-Out (FIFO) principle. Elements are added at the rear and removed from the front.
Basic Operations:
Enqueue: Add an element to the rear of the queue.
Dequeue: Remove and return the front element of the queue.
Front/Peek: Return the front element without removing it.
isEmpty: Check if the queue is empty.
Example (Using an Array):
QUEUE queue[SIZE]
front ← -1
rear ← -1FUNCTION enqueue(element)
IF rear = SIZE - 1 THEN
PRINT "Queue Overflow"
ELSE
IF front = -1 THEN
front ← 0
END IF
rear ← rear + 1
queue[rear] ← element
END IF
END FUNCTIONFUNCTION dequeue()
IF front = -1 OR front > rear THEN
PRINT "Queue Underflow"
ELSE
element ← queue[front]
front ← front + 1
RETURN element
END IF
END FUNCTIONAdvantages:
Useful for scheduling and managing tasks in order (e.g., CPU scheduling, print queue).
Disadvantages:
Limited access to elements; only the front and rear elements can be accessed directly.
Non-linear Data Structures
Non-linear data structures are used to represent data that does not follow a sequential order. Unlike linear data structures (arrays, linked lists, stacks, queues), elements in non-linear data structures are connected in a hierarchical or networked manner. This allows for more complex relationships between data elements. The most common non-linear data structures are trees and graphs.
Trees
A tree is a hierarchical data structure consisting of nodes connected by edges. Each tree has a root node, and each node has zero or more child nodes. Trees are used to represent hierarchical data, such as file systems, organizational structures, and more.
Basic Terminology:
Root: The topmost node in a tree.
Parent: A node that has one or more child nodes.
Child: A node that has a parent node.
Leaf: A node with no children.
Sibling: Nodes that share the same parent.
Subtree: A tree consisting of a node and its descendants.
Binary Trees: A type of tree where each node has at most two children, referred to as the left child and the right child.
Binary Search Trees (BST): A binary tree where for each node, the left child's value is less than the node's value, and the right child's value is greater than the node's value. This property makes searching, insertion, and deletion efficient.
Tree Traversal Methods:
In-order Traversal: Visit the left subtree, the node, and then the right subtree.
Pre-order Traversal: Visit the node, the left subtree, and then the right subtree.
Post-order Traversal: Visit the left subtree, the right subtree, and then the node.
Level-order Traversal: Visit nodes level by level from top to bottom.
Example (Binary Search Tree):
CLASS Node
VALUE: INTEGER
LEFT: Node
RIGHT: Node
FUNCTION insert(root, value)
IF root = NULL THEN
RETURN new Node(value)
END IF
IF value < root.VALUE THEN
root.LEFT = insert(root.LEFT, value)
ELSE
root.RIGHT = insert(root.RIGHT, value)
END IF
RETURN root
END FUNCTIONGraphs
A graph is a non-linear data structure consisting of vertices (nodes) and edges (connections between nodes). Graphs are used to represent networks, such as social networks, transportation systems, and the Internet.
Basic Terminology:
Vertex (Node): A fundamental part of a graph, representing an entity.
Edge: A connection between two vertices.
Adjacent Vertices: Vertices connected by an edge.
Degree: The number of edges connected to a vertex.
Path: A sequence of vertices connected by edges.
Cycle: A path that starts and ends at the same vertex.
Types of Graphs:
Directed Graph (Digraph): A graph where edges have a direction, going from one vertex to another.
Undirected Graph: A graph where edges do not have a direction.
Weighted Graph: A graph where edges have weights (values) representing cost, distance, or other metrics.
Unweighted Graph: A graph where edges do not have weights.
Graph Representations:
Adjacency Matrix: A 2D array where the element at row i and column j indicates the presence (and possibly weight) of an edge between vertices i and j.
AdjacencyMatrix[3][3] = {
{0, 1, 0},
{1, 0, 1},
{0, 1, 0}
}Adjacency List: An array of lists where each list contains the adjacent vertices of a particular vertex.
AdjacencyList = {
0: [1],
1: [0, 2],
2: [1]
}Graph Traversal Algorithms:
Breadth-First Search (BFS): Explores vertices level by level, using a queue.
FUNCTION BFS(graph, startVertex) CREATE queue ENQUEUE startVertex MARK startVertex as visited WHILE queue IS NOT EMPTY vertex = DEQUEUE FOR EACH adjacentVertex IN graph[vertex] IF adjacentVertex NOT visited THEN ENQUEUE adjacentVertex MARK adjacentVertex as visited END IF END FOR END WHILE END FUNCTIONDepth-First Search (DFS): Explores as far as possible along each branch before backtracking, using a stack or recursion.
FUNCTION DFS(graph, vertex, visited) MARK vertex as visited FOR EACH adjacentVertex IN graph[vertex] IF adjacentVertex NOT visited THEN DFS(graph, adjacentVertex, visited) END IF END FOR END FUNCTION
Searching Algorithms
Searching algorithms are fundamental in computer science, used to retrieve information stored within a data structure or database. They are categorized based on the type of data structure they operate on and their efficiency. Here are the main types of searching algorithms covered in the IB Computer Science HL syllabus:
Linear Search
Linear search is the simplest searching algorithm. It works by sequentially checking each element of a list until a match is found or the whole list has been searched.
Algorithm:
Start from the first element.
Compare each element with the target value.
If a match is found, return the index.
If the end of the list is reached without finding the target, return an indication that the target is not found.
Time Complexity: O(n), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION linearSearch(array, target)
FOR i ← 0 TO length(array) - 1 DO
IF array[i] = target THEN
RETURN i
END IF
END FOR
RETURN -1 // target not found
END FUNCTIONBinary Search
Binary search is a more efficient algorithm than linear search but requires that the list be sorted. It works by repeatedly dividing the search interval in half.
Algorithm:
Start with the middle element of the sorted list.
If the middle element is the target, return its index.
If the target is less than the middle element, narrow the search to the lower half.
If the target is greater than the middle element, narrow the search to the upper half.
Repeat the process until the target is found or the interval is empty.
Time Complexity: O(log n), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION binarySearch(array, target)
left ← 0
right ← length(array) - 1
WHILE left ≤ right DO
middle ← (left + right) / 2
IF array[middle] = target THEN
RETURN middle
ELSE IF array[middle] < target THEN
left ← middle + 1
ELSE
right ← middle - 1
END IF
END WHILE
RETURN -1 // target not found
END FUNCTIONDepth-First Search (DFS)
Depth-first search is used primarily on graphs and trees. It explores as far as possible along each branch before backtracking.
Algorithm:
Start at the root (or any arbitrary node for a graph).
Mark the node as visited.
Recursively visit all the adjacent unvisited nodes.
Backtrack when no unvisited nodes are adjacent.
Time Complexity: O(V + E), where V is the number of vertices and E is the number of edges.
Example (Pseudocode):
FUNCTION DFS(graph, startVertex, visited)
visited[startVertex] ← TRUE
FOR EACH vertex IN graph[startVertex] DO
IF NOT visited[vertex] THEN
DFS(graph, vertex, visited)
END IF
END FOR
END FUNCTIONBreadth-First Search (BFS)
Breadth-First Search is also used on graphs and trees. It explores all the nodes at the present depth level before moving on to nodes at the next depth level.
Algorithm:
Start at the root (or any arbitrary node for a graph).
Mark the node as visited.
Add the node to a queue.
While the queue is not empty:
Dequeue a node.
Visit all its adjacent unvisited nodes.
Mark them as visited and enqueue them.
Time Complexity: O(V + E), where V is the number of vertices and E is the number of edges.
Example (Pseudocode):
FUNCTION BFS(graph, startVertex)
CREATE queue
visited[startVertex] ← TRUE
ENQUEUE startVertex
WHILE queue IS NOT EMPTY DO
vertex ← DEQUEUE
FOR EACH adjVertex IN graph[vertex] DO
IF NOT visited[adjVertex] THEN
visited[adjVertex] ← TRUE
ENQUEUE adjVertex
END IF
END FOR
END WHILE
END FUNCTIONSorting Algorithms
Sorting algorithms are fundamental in computer science, used to arrange data in a specific order, typically ascending or descending. Efficient sorting is crucial for optimizing the performance of other algorithms that require sorted data as input. Here's an in-depth look at some common sorting algorithms covered in the IB Computer Science HL syllabus:
Bubble Sort
Bubble Sort is a simple comparison-based sorting algorithm. It repeatedly steps through the list, compares adjacent elements, and swaps them if they are in the wrong order. The pass through the list is repeated until the list is sorted.
Algorithm:
Compare each pair of adjacent elements.
Swap them if they are in the wrong order.
Repeat the process until no swaps are needed.
Time Complexity: O(n^2), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION bubbleSort(array)
n ← length(array)
FOR i ← 0 TO n-1 DO
FOR j ← 0 TO n-i-2 DO
IF array[j] > array[j+1] THEN
SWAP array[j] WITH array[j+1]
END IF
END FOR
END FOR
END FUNCTIONSelection Sort
Selection Sort divides the list into two parts: the sorted part at the left end and the unsorted part at the right end. It repeatedly selects the smallest (or largest) element from the unsorted part and moves it to the sorted part.
Algorithm:
Find the minimum element in the unsorted part.
Swap it with the first element of the unsorted part.
Move the boundary between the sorted and unsorted parts one step to the right.
Repeat until the entire list is sorted.
Time Complexity: O(n^2), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION selectionSort(array)
n ← length(array)
FOR i ← 0 TO n-1 DO
minIndex ← i
FOR j ← i+1 TO n-1 DO
IF array[j] < array[minIndex] THEN
minIndex ← j
END IF
END FOR
SWAP array[i] WITH array[minIndex]
END FOR
END FUNCTIONInsertion Sort
Insertion Sort builds the sorted array one item at a time. It picks each element from the unsorted part and inserts it into the correct position in the sorted part.
Algorithm:
Start with the second element.
Compare it with the elements in the sorted part.
Insert it into the correct position.
Repeat for all elements.
Time Complexity: O(n^2), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION insertionSort(array)
n ← length(array)
FOR i ← 1 TO n-1 DO
key ← array[i]
j ← i-1
WHILE j ≥ 0 AND array[j] > key DO
array[j+1] ← array[j]
j ← j-1
END WHILE
array[j+1] ← key
END FOR
END FUNCTIONMerge Sort
Merge Sort is a divide-and-conquer algorithm. It divides the list into halves, recursively sorts each half, and then merges the sorted halves to produce the sorted list.
Algorithm:
Divide the list into two halves.
Recursively sort each half.
Merge the sorted halves.
Time Complexity: O(n log n), where n is the number of elements in the list.
Example (Pseudocode):
FUNCTION mergeSort(array)
IF length(array) > 1 THEN
mid ← length(array) / 2
leftHalf ← array[0 TO mid-1]
rightHalf ← array[mid TO length(array)-1]
mergeSort(leftHalf)
mergeSort(rightHalf)
i ← 0
j ← 0
k ← 0
WHILE i < length(leftHalf) AND j < length(rightHalf) DO
IF leftHalf[i] < rightHalf[j] THEN
array[k] ← leftHalf[i]
i ← i + 1
ELSE
array[k] ← rightHalf[j]
j ← j + 1
END IF
k ← k + 1
END WHILE
WHILE i < length(leftHalf) DO
array[k] ← leftHalf[i]
i ← i + 1
k ← k + 1
END WHILE
WHILE j < length(rightHalf) DO
array[k] ← rightHalf[j]
j ← j + 1
k ← k + 1
END WHILE
END IF
END FUNCTIONQuick Sort
Quick Sort is another divide-and-conquer algorithm. It picks a "pivot" element, partitions the array into elements less than the pivot and elements greater than the pivot, and then recursively sorts the partitions.
Algorithm:
Choose a pivot element.
Partition the array around the pivot.
Recursively apply the above steps to the sub-arrays.
Time Complexity:
Average case: O(n log n)
Worst case: O(n^2) (if the smallest or largest element is always chosen as the pivot)
Example (Pseudocode):
FUNCTION quickSort(array, low, high)
IF low < high THEN
pivotIndex ← partition(array, low, high)
quickSort(array, low, pivotIndex - 1)
quickSort(array, pivotIndex + 1, high)
END IF
END FUNCTIONFUNCTION partition(array, low, high)
pivot ← array[high]
i ← low - 1
FOR j ← low TO high - 1 DO
IF array[j] < pivot THEN
i ← i + 1
SWAP array[i] WITH array[j]
END IF
END FOR
SWAP array[i + 1] WITH array[high]
RETURN i + 1
END FUNCTIONChapter 4: Computers
Overview of Computers
Definition and Basic Function
Computers are complex electronic devices that are made to process data in accordance with instructions.
From the early days of massive mainframes to the sophisticated, portable gadgets of today like smartphones and tablets, they have seen significant evolution. A wide range of tasks are carried out by modern computers, such as calculations, data storage, communication, and entertainment.
They primarily carry out four tasks at their core: storing data for later use, processing data, and producing results. Users can enter data using input devices such as keyboards and mouse, and the Central Processing Unit (CPU) processes the data.
The CPU manipulates data in response to software commands and algorithms by carrying out instructions that are kept in memory (RAM).
Users can view or print the processed findings on output devices like printers and displays. Hard drives and solid-state drives are examples of storage devices that store data even when a computer is shut off, allowing for long-term data storage and retrieval.
Historical Evolution and Development
The earliest electronic computers, such as the ENIAC (Electronic Numerical Integrator and Computer), were created in the middle of the 20th century to carry out complex computations.
These first devices required a great deal of electrical power and were large. The discovery of the transistor in the late 1940s sped up the development of computers, resulting in the creation of mainframes and minicomputers—smaller, more efficient computers—in the 1960s and 1970s.
Personal computers (PCs) became more popular in the 1980s, mainly because of the efforts of companies like Apple and IBM, bringing up computing to both small and individual users.
The World Wide Web turned computers into global platforms for communication and information sharing, resulting in the internet boom of the 1990s.
The future of computing technology is being shaped by the ongoing evolution of computers today due to developments in wearable technology, quantum computing, and artificial intelligence.
Hardware Components
Central Processing Unit (CPU)
Often called the "brain" of the computer, the CPU interprets and carries out commands to carry out instructions from programs.
Multiple cores are included into modern CPUs that perform multiple tasks at once, improving both speed and efficiency.
For example, the excellent performance of AMD Ryzen 9 and Intel Core i9 processors in professional and gaming applications is well-known.
Memory (RAM and ROM)
Data that the CPU needs to access fast is temporarily stored in RAM (Random Access Memory). It enables computers to operate several programs at once without experiencing noticeable delays.
The current RAM standard, known as DDR4 (Double Data Rate 4) offers better energy efficiency and higher data transfer rates than earlier versions.
Essential applications and data are stored in ROM (Read-Only Memory), which is similar to firmware in devices like BIOS (Basic Input/Output System). This data is stored in ROM and is not lost even when the computer is turned off.
Input Devices
These allow users to communicate with computers and enter data. Common input devices include touchscreens, keyboards, and mice.
Stylus pens for graphic design and speech recognition software for hands-free operation are examples of advanced input devices.
Output devices
These are devices that show or generate the outcomes of processing data. Examples of these include speakers, printers, and monitors.
For gaming and multimedia applications, high-resolution monitors with features like HDR (High Dynamic Range) and adaptive sync technology improve visual clarity and responsiveness.
Storage Devices
The two main types of storage in computers are solid state drives (SSDs) and hard disk drives (HDDs).
HDDs offer large capacity at a reduced cost per GB by storing data on spinning drives using magnetic storage.
SSDs are the best option for operating systems and frequently accessed data since they use flash memory technology that offers faster data access speeds and enhanced durability.
Operating Systems and Software
Software Types
Operating systems like Windows 11 and macOS Monterey, as well as Linux distributions like Fedora and Ubuntu, are examples of system software.
It also controls the hardware resources of computers.
Certain user demands and tasks are satisfied by application software, such as Adobe Premiere Pro, Microsoft Office, and Adobe Creative Cloud.
Operating Systems (OS)
Operating Systems are programs that control the hardware resources of computers and offer standard services to application software.
Windows 11 supports a large variety of apps and devices and is well-known for its user-friendly interface and gaming features. With features like Universal Control that improve work across Macs and iPads, macOS Monterey integrates with Apple products in a natural approach.
Utility programs
These applications carry out particular functions associated with optimization and system administration.
Software for antivirus defense, such as Norton and McAfee, guards against internet dangers and malware. File compression programs and disk cleanup tools maximize storage capacity and enhance system performance.
Data Presentation
Binary System
Binary digits, or bits, which represent values as 0s and 1s, are used by computers to process data. Binary digits, or bits, are the fundamental units of all digital data. Each bit can represent one of two states: 0 or 1.
For instance, the number 7 is represented as 0111 in binary code.
Hexadecimal System
To more compactly represent binary data, hexadecimal (base 16) is commonly used in computing. It makes data management and comprehension easier for programmers by using sixteen symbols (0–9 and A–F) to represent values.
For example, in hexadecimal, the binary number 1010 is represented as 'A'.
Unicode and ASCII
Computer text is represented by the character encoding standards Unicode and ASCII (American Standard Code for Information Interchange).
ASCII represents characters in the English alphabet and other symbols using binary codes that are either 7-bit or 8-bit.
By enabling a larger range of characters from different languages and symbols worldwide, Unicode expands on ASCII and ensures cross-platform and cross-language compatibility.
Networks and Communication
Network Types
Local Area Networks (LANs) use Ethernet cables or Wi-Fi to link devices inside a restricted area, such as a house, workplace, or college.
Wide Area Networks (WANs) use leased lines and routers to link local area networks (LANs) over long geographic distances. With the use of wireless technology (Wi-Fi), wireless LANs (WLANs) provide flexible and mobile device connections in place of physical wires.
Internet Protocols
Data transmission across networks, including the internet, is based on the fundamental protocol suite known as TCP/IP (Transmission Control Protocol/Internet Protocol).
Application-layer protocols called HTTP (Hypertext Transfer Protocol) and HTTPS (HTTP Secure) are used to transfer web pages and secure online communication, respectively.
Cloud-Based Computing
With cloud computing, customers can have on-demand internet access to computer resources (such servers, storage, and databases).
Businesses and individuals can benefit from scalable solutions provided by services like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform, which lessen the need for physical hardware and infrastructure maintenance.
Cybersecurity
Cybersecurity measures guard against damage, attacks, and illegal access to computer systems, networks, and data.
Data confidentiality, integrity, and availability are ensured by security measures like intrusion detection systems (IDS), firewalls, and encryption, which protect against dangers like malware, phishing, and denial-of-service (DoS) assaults.
Programming and Algorithms
Languages for Programming
Developers can write computer-executable instructions (code) by using programming languages.
Applications involving artificial intelligence, data analysis, and web development are conducted using high-level languages such as Python, which are renowned for their readability and simplicity.
Low-level languages, like C and C++, are utilized in embedded systems and system-level programming because they provide direct hardware control.
Algorithms
Algorithms are systematic processes or equations that are applied to data processing, automated reasoning, and calculations.
Common algorithms include those for organizing data (e.g., Bubble Sort, Merge Sort) and discovering specific objects in a collection (e.g., Binary Search). For complicated computing issues to be solved and performance to be maximized, efficient algorithms are essential.
Flowcharts and Pseudocode
An algorithm or process's flow of control is visually represented using flowcharts, which use arrows and symbols to show decision points, actions, and data flow.
Pseudocode is a high-level explanation of a computer program or algorithm that helps with program design and clarity by outlining logic before real coding using structured English and syntax similar to programming languages.
Social and Ethical Concerns
Privacy Issues
The gathering, storing, and use of personal data by governments and organizations gives rise to privacy concerns.
The goal of data protection laws such as the California Consumer Privacy Act (CCPA) in the US and the General Data Protection Regulation (GDPR) in Europe is to preserve people's right to privacy by enforcing stringent rules on how data is handled.
Intellectual Property
The rights of creators to their original creations and innovations are safeguarded by intellectual property laws.
Authors, artists, and inventors are granted exclusive rights to their creative works by copyright, whilst new ideas and innovations are protected by patents. Creative Commons licenses give authors a framework that is flexible enough to share their work with some restrictions.
Digital Divide
The term "digital divide" describes differences in how people utilize and have access to digital technology, such as computers, the internet, and digital literacy.
In order to advance equitable chances in employment, education, and socioeconomic growth internationally, it is essential that the digital divide be overcome.
Cybercrime
Cybercrime is the term used to describe illegal activities carried out through digital platforms, such as ransomware attacks, phishing scams, identity theft, and hacking.
To counter cyberthreats and defend people, companies, and vital infrastructure from cyberattacks, law enforcement organizations, cybersecurity experts, and international collaboration are necessary.
Emerging Trends
Artificial Intelligence (AI)
Artificial intelligence (AI) is the imitation of human intellect in devices that are capable of tasks that normally require human intelligence, like speech recognition, visual perception, decision-making, and language translation.
Without explicit programming, computers may learn from data and gradually get better at what they do thanks to machine learning (ML) techniques.
Applications of AI include healthcare diagnostics, driverless cars, virtual assistants (like Siri and Alexa), and tailored suggestions for entertainment and e-commerce.
The Internet of Things (IoT)
The term "Internet of Things" (IoT) describes a network of networked objects that are implanted with sensors, software, and connection features to gather and share data via the internet.
IoT devices span a wide range of categories, from wearable health monitoring and smart home appliances (such security cameras and thermostats) to industrial machinery and smart city infrastructure.
IoT technology improves productivity, automation, and decision-making in a number of sectors, including manufacturing, transportation, healthcare, and agriculture.
Augmented Reality (AR) and Virtual Reality (VR)
Through the use of headgear or goggles, virtual reality (VR) submerges viewers in a simulated world and offers an intense sensory experience.
Augmented Reality (AR) enhances real-time engagement with the environment by superimposing digital information and virtual objects onto the real world.
Applications for virtual reality and augmented reality include gaming and entertainment, education and training (such as surgical simulations and virtual classrooms), architectural and design visualization, and travel experiences.
Chapter 5: Content (3.4: Networks and The Internet)
3.4: Networks and The Internet
Key ideas
Networks connect computers, people and communities, allowing data to be created, accessed and shared in a distributed manner.
Networks and the internet are defining features of digital society.
Networks and the internet pose significant opportunities and dilemmas for life within a digital society.
Network: a series of interconnected nodes (connection points) that transmit, receive and exchange data, which can range from text, sound to video.
Examples of nodes include computers, servers and routers.
3.4A Types of computing networks
Networks are categorized depending their physical size, type of connectivity or how data is shared. Different networks are suitable for different purposes and situations.
Networks by size
Personal area network (PAN): the smallest type of network, consisting of connected devices in close proximity to an individual.
Examples: wirelessly connecting to a phone, a laptop connected to a printer, a smartwatch wirelessly synching data to a phone.
Local area network (LAN): a group of computers or devices connected on a single site, which is set up to help the sharing of resources.
This can be done on a small scale (a home with more than two users) or a larger scale (office or school, with hundreds of users)
Examples: sharing resources to centralized data in an office, giving access to printer at home
Metropolitan area network (MAN): network that covers a larger geographical area, ranging from 5 to 50 km.
Examples: cities that provide free WiFi, municipalities that connect traffic lights
MAN could be used in road infrastructure transited by autonomous vehicles.
Real-World Example: New York’s Free Wi-Fi
New York City provides free Wi-Fi to all their residents, as well as wirelessly connecting traffic lights and parking meters.
Wide area network (WAN): the largest type of network, which is commonly used by businesses through a collection of LANs.
The collection of LANs can either be available to the public or may be limited to be used by an organization.
For organizations and businesses, WANs present an advantage - it eliminates the need to have servers in each of their offices. Additionally, they can lease an exclusive line from their internet service provider (ISP), to avoid sharing their network.
Example: the largest publicly available WAN is the internet - a collection of networks and networking technologies which connects users.
Type of connectivity
Wired networks: devices connected with copper ethernet cables which plug into an ethernet port (which were either integrated onto the motherboard or installed as a separate interface card). It also uses a router or a switch
Fiber-optic cables are now being used, given they provide better connectivity over greater distances.
Some businesses and governments still used wired networks - these are considered to be more reliable to transfer data and work at a faster speed.
Wireless networks: devices embedded with wireless network interface cards connect either through a wireless access point or router.
Wireless connections use radio signals to send data across the network, although it still uses cables to connect access points to a wired backbone.
The major difference is that devices (laptops, printers) can connect wirelessly.
Wireless networks are widely used - they are easy to set up (no need to connect devices through cables) and offer flexibility, since devices can connect from within a geographical range.
Cloud networks: incorporate some or all network capabilities to a cloud platform,
Cloud-based networks still use access points on site, but cloud platforms have the ability to be managed or host data off-site.
This type of network can be configured by accessing the IP (internet protocol) address of the hardware controlling the network.
Cloud networks are used by organizations - they are easy to station, save costs and allow for scalability.
Sharing data
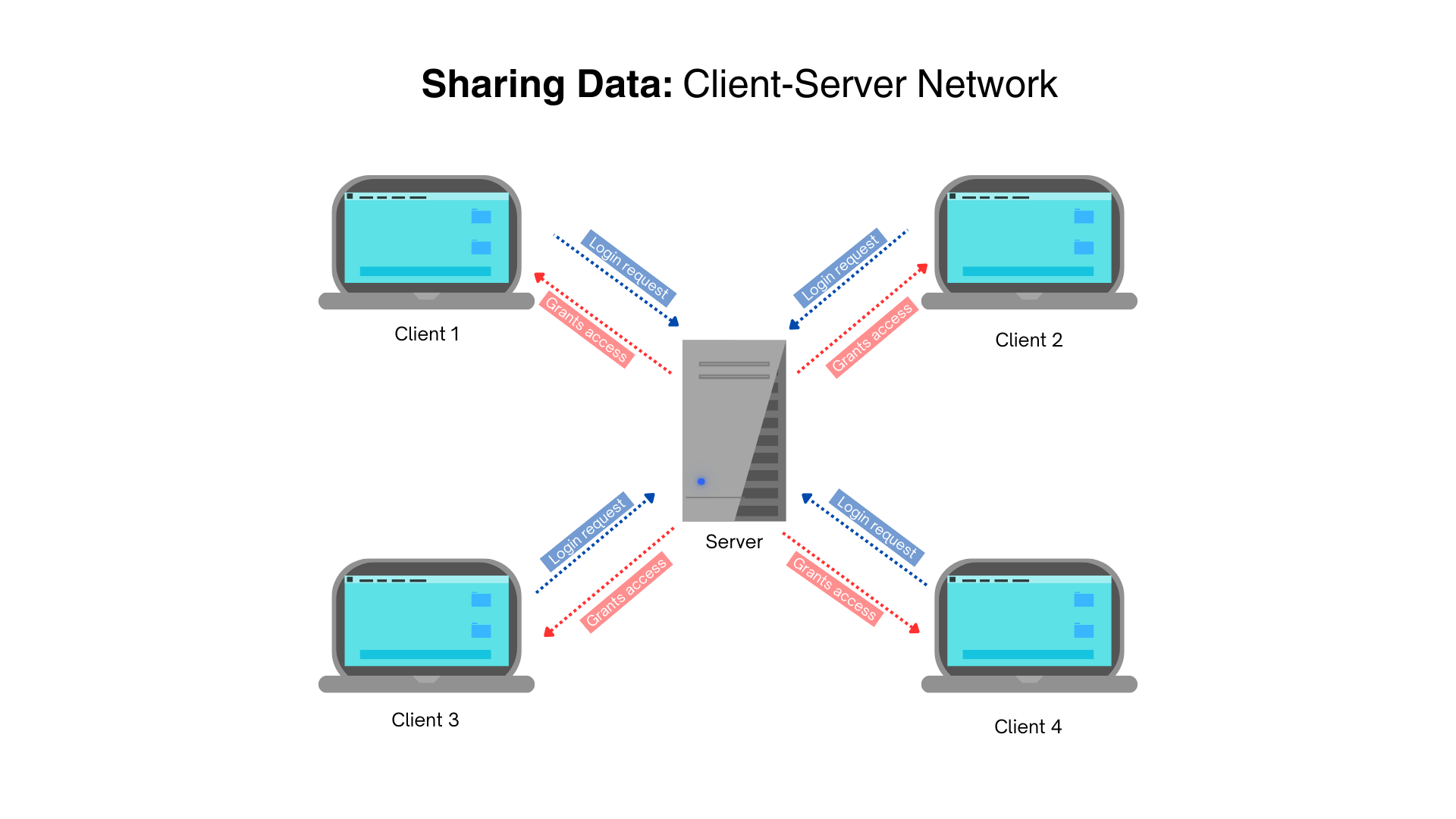
Client-server networks: data is stored centrally on a server and access is granted to connected devices (also referred as ‘clients’)
Servers can either be hosted internally (e.g. by an organization) or externally in the cloud.
Many organizations see an advantage in this network - it allows them to prioritize IT resources that will secure and backup data.
Nonetheless, there are some disadvantages - setting up and configuration are expensive which requires expert staff. Additionally, adequate bandwidth is needed to ensure equal access is given to all clients.
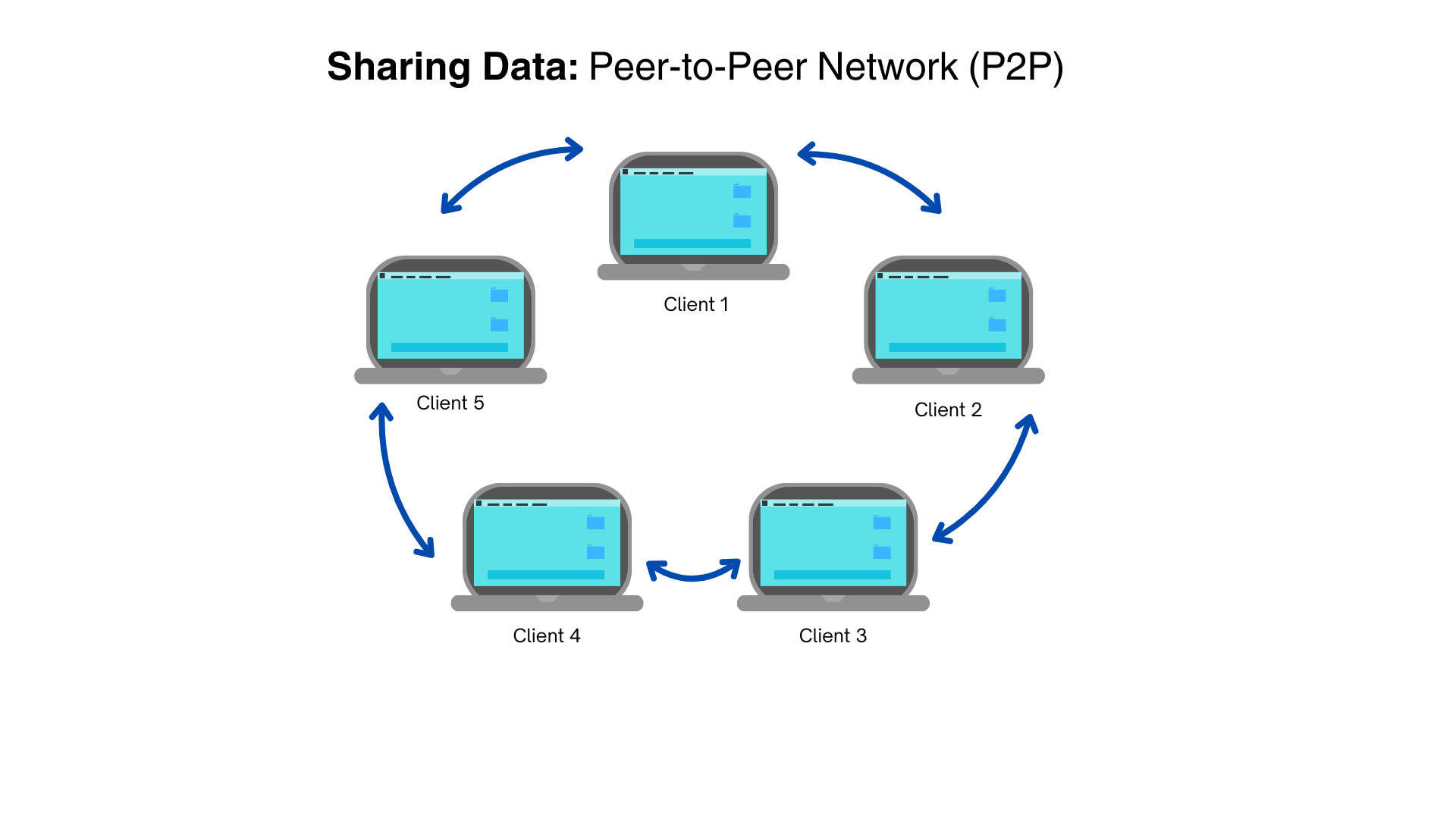
Peer-to-peer network (P2P): a decentralized network - each device is equally responsible for sharing and storing data.
A major advantage is that the network is not dependent on one server. Likewise, it is easy to set up.
P2P is therefore popular for sharing large files over the internet, although at the expense of not being able to manage or control the security of the data.
Example: online gaming platforms - Blizzard Entertainment and Wargaming
A downside to P2Ps is the ease of sharing illegal copyright material. Since it does not depend on a server, it is difficult for authorities to track them and shut them down.
3.4B: Components of computing networks
Network interface card: a device (typically a circuit board or chip) which is either installed (wired) or not (wireless) on a computer (or node).
The card is responsible for converting data into a digital signal and communicating this data to a network.
MAC address: Media Access Control Address - a unique number assigned to every network device.
Usually, MAC addresses are stored within a device’s ROM (Read-Only Memory), thus the are sometimes called a ‘hardware address’
MAC addresses are unique (unlike IP addresses) and are not designed to be changed although it is easy for a skilled user to alter or spoof theirs.
Router: a networking device which connects two or more separate networks.
This is done by transferring data from one network from another - routers forward data packets through the most efficient route available.
The router acts as a gateway, where all data entering and leaving the network passes, therefore, it enables a router to perform additional tasks such as filtering information.
Example: a router at a school will connect the school network to an external one, such as the internet.
Modem: a device which converts digital data into analogue data. It usually converts data to an ethernet connection, which allows ISP to provide WiFi to a user’s home.
Wireless access point (WAP): a device that creates a wireless local area network to improve coverage throughout a building.
A WAP works by setting up a number of dedicated radio channels that the computers can connect to.
Each WAP will be connected to either a hub or a switch.
Hub: the most basic and cheapest network device - when it receives data, it re-broadcasts the data to all connected devices.
There is a downside to this device - it uses a lot of bandwidth because it sends unnecessary data all over the network, including to non-intended devices.
Example: game consoles for a local multiplayer game.
Switches: a more upgraded version of hubs - they inspect data they receive before sending it to the intended recipient.
Switches saves bandwidth and also gives more control over how data is shared.
*Hubs, routers and switches perform similar basic tasks but they differ in the way they broadcast data.
3.4C: Characteristics of computing networks
Network standards and protocols
Network protocol: a set of rules which outlines how data is sent, formatted and received.
The protocols include different layers which govern different parts of a communication. These four layers are:
Application layer: set of protocols used by applications. Example: web browser
Transport layer: oversee communication between hosts using the following protocols:
Transmission Control Protocol (TCP): ensures data is sent and received correctly. TCP needs to make a request if data is lost in order to re-send it.
Internet Protocol (IP): deals with the addressing of individual devices and routing data.
Collectively, the Transmission Control Protocol/Internet Protocol (TCP/IP) is a set of rules which governs how data is sent within a network and also demands that an IP address is used to identify machines on said network.
Internet layer: concerned with the sender and the recipients’ IP address. Additionally, it routes the data packets across a network.
IP (Internet Protocol) address: a numeric address assigned to every node (device) which identifies them within a network.
IP address is assigned by the Dynamic Host Configuration Protocol Server (DHCP), to avoid address conflict (having more than one device with the same IP address number) and to keep track of each assigned number.
Physical network layer: protocols which allow different networking technologies to work together.
Example: networking technologies - ethernet
When a user types a website address into a web browser, it consists of a domain name. The domain name is send as a request a;
Domain name server (DNS): a server which translates the domain name into IP addresses.
The server searches for an IP address in its database and will forward data to that address.
Example: Twitter’s IP address is 104.244.42.1.
Network capacity
This takes in consideration how much data can be transferred in any given time.
Bandwidth: the amount of data a network can transfer at once. It is measured in hertz (Hz).
Speed: the length of time it takes for data to be transferred. It is measured in megabits per second (Mbps).
Data Compression: process which reduces size of a file by re-coding it with fewer bits of storage.
This process is commonly done to reduce the amount of space needed to store a file.
There are two types of compression algorithms;
Lossy Compression: reduces file size by permanently removing unimportant data.
Example: JPG and MP4
Lossless Compression: reduces file size but without losing data and the possibility of turning the file to its original data.
Example: PNG and BMP
Net neutrality: the notion that all data requests on the internet are equally important and thus should be treated as such by internet service providers (ISPs) companies.
Net neutrality is encouraged to avoid some websites running faster than others and to avoid ISPs from proposing to charge extra to view specific content.
Security
Data on a network is always vulnerable to threats.
Networking and security professionals need to ensure all measures are taken to protect data. Users have the obligation to be educated and responsible on how they protect their data.
Controlling access from within
A network can be configured to control how users access physical resources and data.
The simplest form was through authentication - a user uses a unique username and strong password.
Authentication has been replaced by the more reliable multi-factor authentication;
Multi-factor authentication: a user is subject to multiple methods of authentication to verify its identity.
Two or more credentials are used, which can include a mix of physical or biometric measures:
Examples: physical - token, card or text message, biometric - faceprint, PIN, or phrase.
Controlling access from outside threats
Firewall: a hardware or software which determines which data is allowed to enter the network.
Hardware firewalls may be used by large organizations, while a software firewall is part of an operating system and can be turned on.
A firewall works by inspecting incoming and outgoing data, thereby preventing unauthorized access to a network and controlling which users and programs are allowed to connect to the network.
Proxy Server: a computing system which acts as an intermediary between the client on the network and the internet.
Because all communication passes through a proxy, it is able to perform additional tasks such as caching, filtering and logging data, adding a layer of security.
3.4D: Computing network providers and services
To gain access to the internet a user must be registered to a mobile service provider (MSP) or an internet service provider (ISP).
Mobile service provider (MSP): commonly known as mobile carrier or mobile phone operator — a company that offers cellular connection to mobile phone subscribers.
MSPs purchase a license to transmit radio signals over a specific range and within a particular frequency.
Radio signals between 1800 to 2100 MHz are 4G and 5G networks.
MSP subscribers use this service to make phone calls, send, receive messages and use data to navigate the internet. It is now possible to make calls using the internet with VoIP
VoIP (Voice Over Internet Protocol): allows users to make calls using a broadband internet connection instead of an analogue phone line.
In a VoIP, audio data is transformed into digital packets which are sent via the internet to other devices.
Examples: VoIP services - Skype, WhatsApp, Facebook Messenger.
Internet Service Provider (ISP): a company which provides access to the internet and other related services, which include email, domain registration and web hosting.
3.4E: The World Wide Web
Internet: global collection of networks and networking technologies that link users.
World Wide Web (WWW): collection of websites and web services which can be viewed and that are hosted on web servers.
Three technologies have allowed the interoperability between all technologies on the internet;
URL (Unique Resource Locator): a unique address for each resource on the web, which can include the address of a web page or a file hosted by a web server.
HTTP (Hypertext Transfer Protocol) or HTTPS (Secure Hypertext Transfer Protocol): determines how web resources are transmitted between the web browser and the web server.
HTTPS is more secure and now a requirement for many web browsers.
Web-hosting companies add a security certificate to their web servers, guaranteeing sensitive data is encrypted.
HTML (Hyper Text Markup Language): format of web pages - allows documents to be displayed as web pages and web pages to be linked together.
3.4F: Evolution of the internet and the web
The early days of the internet (1969–2000)
1965: First computer network established - a computer from the University of California, Los Angeles, sent a message to a computer at Stanford University, causing a system crash.
1969: Creation of the ARPANET (Advanced Research Projects Agency), the second (and only successful) attempt to create the internet.
The ARPANET included 30 academic, military and research institutions across the world (Hawaii, Norway and the UK).
The TCP/IP Protocol was introduced and operational until 1990.
1989: The WWW (World Wide Web) created by Sir Tim Berners-Lee - by this time, the nodes connected to the internet grew from 2000 to 30,000.
Berners-Lee proposed that the information being shared should be structured and linked in a way that made it quicker and easier to access.
The web browser was introduced, making the WWW more accessible.
1994: World Wide Web Consortium (W3C) formed - the organization aims to promote the evolution and interoperability of the WWW through the development of protocols and guidelines.
The W3C consults a wide range of members who work for organizations before implementing any protocols or guidelines.
1996: The number of websites grew to 100,000. In 1993, there were only 130 websites.
The expansion of the web (2000–20)
Web 1.0: A version of the web which was characterized by static web pages. During this time, a change of content within web pages required programming, a skill few people knew.
Web 2.0 (2000): Also known as ‘social web’, a version of the web which saw a democratization of the internet.
Users could generate their own content, without programmers through the use of XML and RSS to structure and format websites.
Additionally, users could upload their own content to web pages.
These changes were also possible due to the development of new technologies and protocols.
Social media platforms, blogging, podcasting, social bookmarking and tagging were introduced during this period, many which are still popular today.
Web 3.0: the semantic web (2020–present)
An era which aimed to innovate the user experience - focused shifted to back end (data and logistics of how an app works), with the promise of being more intelligent.
One feature is the focus on generating a greater understanding of the meaning of the words used when creating, sharing and searching content.
This generation heavily uses artificial and natural language processing - websites can display 3D graphics and demand for internet of things (IoT) is growing.
The internet of things (IoT)
IoT: Refers to all devices which are connected to the internet - this does not only include phones or laptops but also smart appliances and autonomous vehicles.
Other items such a smart light bulb or a jet engine are also included - devices could be either small or large.
IoT devices work by using sensors which collect data and communicate with each other over the network, with the purposes of providing assistance or increasing efficiency.
Example: smart home technologies - smart door locks allow delivery drivers to drop off packages.
Some criticism and concerns over IoT revolve around the issues of privacy and security.
3.4G: Internet dilemmas
Understanding the risks to data
Specific risk which threat to lose, damage and misuse data include;
Spamming: sending unsolicited emails with the purpose of advertising.
With development in email filters, a user can eliminate unwanted messages before reaching their inbox.
Hacking: defined as the unauthorized access to a computer or network, which can be accomplished through tools such as:
Social engineering: tricking a user into sharing credentials (username and password). It is an umbrella term to refer to all techniques aiming to obtain user’s data.
Example: hackers impersonating an IT staff, offering to conduct routine maintenance.
Phishing: a type of social engineering - hackers send fraudulent emails designed to trick users into revealing sensitive information.
Real-World Example: Phishing at Google and Facebook (2013 - 2015)
Evaldas Rimasauskas, a Lithuanian national, established a fake computer manufacturer company which pretended to work with Google and Facebook.
Rimasauskas sent phishing emails with invoices to employees, deceiving both companies into paying US$ 100 million.
Viruses: a type of malicious software (or malware) composed of small pieces of code.
Viruses are often attached to legitimate programs or emails and are activated when the user launches or opens either.
Real-World Example: Bangladesh Bank Hack (2016)
Lazarus group, a North Korea group of hackers, launched an attack with the aim of stealing US$1 billion.
The group used a range of social engineering methods, including viruses - these were attached to the CV of a hacker who presented himself as an intern.
The hackers needed to reach and shut down the printer, which had a paper backup system of all bank transactions, risking exposing the hackers’ scheme.
Ransomware: a malware which locks a user out of their device, demanding a payment to release them.
Ransomware can be activated when clicking an email attachment, visiting a malicious website or link and can be hidden when downloading a software.
Real-World Example: WannaCry Ransomware (2017)
A global attack which affected 230,000 computers. Users needed to pay a ransom in Bitcoins.
The hackers used ransomware to take advantage of a vulnerability in the Windows operating system.
Although Windows released a security patch, many institutions had not updated their computers, resulting in US$4 billion losses worldwide.
Distributed denial of service (DDOS): an attack which overwhelms (disrupts the normal traffic) a site or service, making it unavailable to intended users.
Hackers who carry out this attack install malware in a network of computers (botnet) which are instructed to make a connection to the target web server. The web server can’t cope with the increased demand, preventing users from accessing the website.
Example: DDOS attack on Amazon (February 2020) - resulted in loss of revenue and reputation.
Example: The Meris Botnet (2021): The Meris, which was the largest botnet available to hackers (with 250,000 infected devices) was taken down after an attack by the security division of Rostelecom, the largest provider of digital services in Russia.
Hacking a website/Penetrating a network: methods which can include gaining back-end database of user information or redirecting users to a different website.
Exploiting a security flaw: a network is vulnerable if it doesn’t have adequate malware, virus protection or firewall.
Real-World Example: Log4J attack (2021):
A security flaw in the Java code ‘Log4shell’ made many corporate networks vulnerable to hackers.
The flaw gained prominence after it was revealed that it affected some sites hosting Minecraft.
Consequences of the risks to data
This includes measures to counter exposure; such as (although it includes ill-intentioned)
Anonymity: the use of digital technology to conceal a person’s true identity.
This is the most extreme form of privacy and can be potentially liberating for users which can confidently express themselves.
However, some users can take advantage of anonymity with malicious intent, such as cyberbullies and internet trolls.
Internet trolls: people who deliberately leave provocative or offensive messages with the intention to draw attention, cause trouble or upset someone.
Real-World Example: Online harassment survey (Australia)
A survey showed 1 in every 3 Australians have experienced online harassment, resulting in US$ 2.6 billion in health costs and lost income for the government.
Identity theft: when a person steals another’s personal information with the intention of committing fraud.
The information can be used to apply for a credit card, gaining access to medical services and/or other financial benefits.
Many users go into anonymity as a way to counter identity theft, especially because many sites and services now require users to sign up.
Some governments are enforcing the right to be forgotten (RTBF), to help users keep their data safe.
Right To Be Forgotten (RTBF): right to have personal information removed from internet searches and other directories under certain circumstances
Example: GDPR: the organizing which governs data protection in Europe states personal information should be removed when:
The user’s consent has been withdrawn
The personal data is no longer needed
Chapter 6: Content (3.5: Media)
3.5: Media
Key ideas: Digital media are:
defined by the convergence of computing, communication and content.
created and distributed through multiple channels and platforms
associated with significant opportunities and dilemmas in digital society
Media: any communication channel that serves as a medium to enable information to reach a wide group of people.
Some types of media include: print media (published newspapers, books) and mass media (news channel on TV and radio)
With the widespread use and availability of internet, our media consumption has moved online, which is known as;
Digital media: information (such as video, audio, images and other content) which is consumed online. Additionally, information can also be created, encoded and stored before sharing.
Anytime a user accesses a website or app, it is either consuming or creating media.
3.5A: Types of digital media
Media and Web 1.0
In the early days of the internet, digital media mostly consisted of web pages which contained text and images.
As bandwidth increased, the internet had the ability to host video, animation and audio recordings.
Although digital technology changed the speed and volume of media it still fulfilled its traditional role - entertain, educate and be a channel for public discussion.
Media and Web 2.0
Introduction of Web 2.0 technologies such as blogs, podcasts, wikis and social media.
Enabled increase in volume of user-generated content and changed the way the public perceived local and global news.
Real-World Example: News from Social Media
2010: CNN reported that 75% of surveyed users got their news from email and social media platforms (Facebook, Twitter).
This prompted media companies to adapt, seeking trending subjects and employing hashtags
Trending: topics which experience a sudden surge in popularity on social media for a limited amount of time.
Hashtag: word or phrase used to classify or categorize the accompanying text. Preceded by (#) symbol.
2015: Traditional media companies were producing more content targeted at social media, especially live video streaming.
Real-World Example: First Viral Meme (1996)
Animation of a baby dancing, created by graphic designer Michael Girard.
The animation was created to demonstrate the capabilities of software but soon converted into a gif and shared.
Memes can easily gain popularity through social media. They have developed from political or cultural topics to anything that is funny or relatable.
Media and Web 3.0
The advent of artificial intelligence has influenced the media industry, from content creator to consumer experience.
Content Creation
Content creation and our ability to manipulate images, audio and video has been possible due to the advancement in artificial intelligence, cloud computing and graphics technology.
Tools which are able to face-swap (superimposing one face into another) or lip-sync, are readily available and often referred as deepfake;
Deepfake: synthetic media created with the use of deep learning and/or artificial intelligence.
Initially, the tools had innocent uses, such as the popularity of face-swapping filters in Snapchat. However, malicious uses of deepfake have contributed to fake news;
Fake news: false or misleading information presented as news.
Deepfake used for fake news have the aim of damaging reputations, fabricating evidence and defrauding the public.
Real-World Example: INVISIBLE Music Video (2021)
Band Duran Duran teamed up with Nested Mind to generate a music video using artificial intelligence.
The artificial intelligence used lyrics, pictures, music and other information in order to create the video
Real-World Example: UK Energy Firm (2019)
An unnamed UK company was tricked into transferring £220,000 (US$260,000) after they received a deepfake audio technology impersonating the CEO.
Real-World Example: Jordan Peele impersonation (2018)
Actor Jordan Peele worked with Buzzfeed to create a deep fake video of Barack Obama.
The video intention was to raise awareness about the potential harm of deepfakes in spreading fake news.
Artificial intelligence and the consumer’s media experience
Artificial intelligence can be used positively by media companies to predict demand and adjust their media production.
For example, Netflix can use it to offer recommendations, therefore enhancing the user experience.
Media companies still need to search for ways to effectively manage data which can train artificial intelligence algorithms.
Electronic games
The electronic games industry is another digital technology which has evolved alongside social media.
The development of internet-enabled gaming consoles and personals computers has enabled the game industry;
To reach untapped audiences - such as senior citizens or middle-aged adults who play games on their smartphones
Create a lucrative industry - ESports had grown since 2000, and in 2019 a US$ 100 million prize was awarded at the Fortnite World Cup.
Additionally, the wide use of platforms such as YouTube and Twitch have supported the growth of professional gamers.
3.5B: Characteristics of digital media
Although digital media serves the same purpose as traditional media (entertain, educate, provide platform for expression), it has some unique characteristics like:
Rapid sharing: either through uploading (e.g. a video on YouTube) or reposting it (e.g. X (formerly Twitter).
Efficient storage: data can be stored in one place, due to development of storage technologies. For instance, a user can store mobile phone data in cloud computing while using social media.
Interactivity: media is more engaging due to interactive media in web design, which could potentially motivate users to revisit web pages, post comments and make recommendations to friends.
This is different from traditional media which is ‘one way’ - audiences could receive media but could not respond or interact.
Non-linear content or hypertextuality: Webpages use hyperlinks, which allows users to click and visit pages, giving them the option to navigate media how they want and in any order.
Traditional media used to be linear and media companies dictated how users navigate media.
Global networks: users can interact more globally - they can pool sources together more easily and have a wider range of sources of information.
Virtual: users can communicate virtually through a range of technologies and in different ways, choosing how to present themselves.
Convergence of digital media: users now communicate using more than one form of digital media at once.
Examples: calls, which can include voice and live video or message, which include text, voice message, emojis or an image.
3.5C: Immersive digital media
Digital media can go beyond user interactivity and provide immersive experiences for users in a virtual life, based on simulations.
Virtual reality (VR)
Definition: a simulation that provides a completely immersive environment for the user.
Users typically use a virtual reality headset, goggles or can make a headset out of cardboard at home.
Virtual reality is possible by programming 3D objects, through the use of spatial computing;
Spatial computing: when physical actions are used as inputs to receive inputs in a 3D space.
Actions can receive outputs in three degrees of freedom (3DoF), like 360 video or six degrees of freedom (6DoF), where a user can move freely (backwards and forward) in a virtual space.
Business are employing VR to be more competitive in some areas, including:
Employee safety training: allows the possibility to make mistakes in a controlled environment without any real-life threats or consequences.
Examples: BP and ExxonMobil - employ VR to train employees in work scenarios, such as emergency procedures.
Sales and marketing presentation: prospective customers have a better idea of proposals or products by experiencing and interacting with them.
Example: Zimmer Biomet - a dental technology provider which creates a virtual dental lab. It allowed dentists to experience and understand how new technologies impacted dental procedures.
Design decisions: test and visualize various decisions before making final choice.
Virtual workspaces: offer an office-like experience to employees working from home. Companies predict these workspaces will provide a space for casual work discussion which may promote problem solving and creative solutions.
Augmented reality (AR)
Definition: a digital content is overlaid on real world elements or experiences.
A readily-available example are filters on Snapchat or similar apps.
This technology is mostly used with mobile devices.
Industries which are employing AR include:
Manufacturing, mining and maritime industries: during the inspection process of machinery, which minimizes interruptions to operations.
Education: teachers can present real situations through 3D modeling, making learning more engaging.
Mixed reality (MR)
Definition: a blending of the real world with the digital world to create new experiences.
The simulation of real-world system is sometimes called digital twin;
Digital twin: a virtual representation of an object or system which represents a real-world/physical object or system.
MR and digital twin are widely used in industries which seek to visualize, analyze, maintain and control their valuable assets through a dynamic set of tools.
A mix of virtual, augmented and mixed reality are used by industries such as
Automotive industry: prospective buyers can try different car customization options.
Medicine: doctors can train in a 3D environment before performing surgeries.
Tourism: tourists can make virtual tours before booking.
Real-World Example: Royal Dutch Shell:
Shell created a digital twin for their oil rigs, which are used to effectively manage the real structures, improve safety of the workers, and develop predictive maintenance.
3.5D: Digital media dilemmas
Media addiction and other psychological concerns
Users use social media for entertainment and a way of staying in touch, but an increased used can derive in a
Social media addiction: an example of behavioral addiction, which is an uncontrollable urge to use social media for a long period of time.
Social media use is linked to short-term dopamine hits, which when quelled can lead to:
Low self-esteem, anxiety and depression, a fear of missing out (FOMO).
Impact on journalism
Journalism has transformed to online, real-time reporting, multimedia content and access to global information.
In addition, users can personalize their news, going against the monopoly previously held by mass media.
Journalists now have to be trained in technical and digital literacy skills.
The rapid-nature of digital media also means journalists have to comply with tighter deadlines, write for multiple types of media and avoid misinformation;
Misinformation: false or inaccurate information that is mistakenly or negligently created or spread. The intent is not to deceive.
Social media had a positive impact for journalists, who can post stories instantly and also create their own following through their personal social media profiles.
However, social media also allows amateur journalists (or bad-intentioned users) to post without the same rigorous editorial control or training.
Fake news and ‘alternative facts’ damage the credibility of journalistic work.
Although these could be easily countered by forming peer-review networks, where journalists review and check each other’s work.
Real-World Example: QAnon
An American conspiracy theory movement which made unfounded claims allegedly from within the US government administration.
Social media companies have taken down many QAnon supporter accounts which coordinated harassment to perceived enemies (politicians, celebrities, journalists) and spread conspiracy theories.
Media authenticity
Rapid advancements in creation and distribution of media is making it more difficult to verify the authenticity of media.
Users are using the same source for news and entertainment, allowing fake news (or disinformation) to spread more easily
Disinformation: false information deliberately created and spread, with the intent of influencing public opinion or blocking the truth.
Fake news normally has a political or criminal nature, and its goal is to promote a political agenda.
For instance, Deeptrace, a start-up company, found 7964 deepfake videos circulating in 2019.
Real-World Example: Fake news (MIT Research)
Data from 126,000 stories tweeted by 3 million users from 2006 to 2017 concluded that fake news spread faster as they stimulate emotions such as surprise, fear and disgust.
This study is relevant, since it was published at the time when it was confirmed fake news distorted the 2016 US Presidential elections.
Ownership of media
Intellectual property (IP): outcome of thought or intellectual effort which can range from a new invention to designs or brand names.
Intellectual property is also the term used to refer to the legal protection of said creation.
IP aims to reward creativity and encourage inventors to share their innovations.
Legal rights, such as patents, trademarks and copyright grant the creator the rights to their work and protect them from unauthorized use for a specific period of time.
Copyright: legal protection for creators of literary and artistic works (books, music, paintings, films and computer programs), which may also be digital.
Copyrights laws operate differently depending on the country, but unauthorized use is considered theft.
Copyrighted material can be used by gaining permission from the owner, although there are two licenses which allow materials to be freely modified or distributed
Public domain: work is available to the public and is not subject to copyright
Fair use: work can be used for study, research, commentary or criticism.
Copyrighted work used under ‘fair use’ should be limited by the following considerations:
Is work used to create something new?
Will it impact the market value of the original work?
How much of the original work is being used?
Real-World Example: Blurred Lines - Robin Thicke, Pharrell Williams and TI (2013)
A court ruled that the song ‘Blurred Lines’ infringed copyright of Marvin Gaye’s ‘Got to give it up’ (1977).
Thicke and Williams had to pay a US$5 million fine.
Copyleft: owners of original work allow others to use their copyrighted property freely under specific conditions.
Example: copyleft software allows users to copy, modify and share their code, with the condition the source code remains open and publicly available.
Copyleft licensing is a solution to copyright permissions which are sometimes time-consuming and difficult to obtain. Moreover, these licensing aims to build a community which can collaborate to improve creative works.
Creative commons licensing is a type of copyleft. The two most common types of licensing include;
CC BY: users can distribute, remix, adapt and build on work as long as attribution is given to the original creator.
This is the least restrictive license.
CC BY NC ND: users can download and share work while crediting the original creator.
The work can not be modified or used commercially.
NC ND stands for non-commercial and no derivatives.
This is the most restrictive license.
Censorship and control of media
Some users may be in uneven access to digital media due to some governments imposing censorship for the following reasons;
Political content: content of political nature which defies or challenges the government narrative.
Real-World Example: Cambodia (2018)
The government blocked independent new sites two days before the elections.
Social content: content which is deemed socially offensive or perceived to be offensive, which can include content related to sexuality, gambling, alcohol and/or illegal drugs.
This measure is taken by governments who aim to ‘protect’ citizens from exposure to undesired content.
Real-World Example: Uganda (2018)
Ugandan communication regulators demanded internet service providers to block access to pornographic sites.
Conflict and security: content related to conflicts, militant groups and border conflicts, to avoid citizens from being involved or contributing.
Real-World Example: Sri Lanka (2019)
Social media access was shut down after a series of bombings, to prevent misinformation and further acts of violence.
Internet tools: some governments surveille communications in order to search for keywords within conversations in emails, messages or internet searches.
Digital media preservation
Given the rapid development of digital media, some devices, storage media and data formats have become obsolete.
Example: people used to record on video cameras and the video was stored in a magnetic tape during the 1990s.
More than a decade later, someone would need to convert the file into a DVD format to be able to access the video.
Digital preservation is essential to ensure information is safe, and readable in newer formats or devices when its original formats become obsolete.
For instance, computers can launch an older operating system, which can run older software. Files can be opened and saved in a new format.
Chapter 7: Content (3.7: Robotics and Autonomous Technologies)
3.7: Robotics and Autonomous Technologies
Key ideas: Robots and autonomous technologies;
Demonstrate a capacity to sense, think and/or act with some degree of independence.
Have evolved over time. They are increasingly ubiquitous, pervasive and woven into everyday lives of peoples and communities.
Introduce significant opportunities and dilemmas in digital society.
Robot: a programmable machine that can complete a set task with little to no human intervention.
3.7A: Types of Robots and Autonomous Technologies
The introduction of robots transformed manufacturing by increasing efficiency, safety and accuracy, although at the cost of threatening jobs.
Robots have evolved overtime in two categories: robots used in manufacturing and robots designed for human interaction
Industrial robots
Demand for robots in the manufacturing sector has existed since the 1960s.
Robots would normally perform tasks such as drilling, painting, welding, assembly and material handling.
Businesses incorporate industrial robots to achieve greater efficiency and accuracy in their production lines.
Industrial robots differ from service robots – they replace human workers on the production line, while service robots assist humans by performing tasks.
Real - World Example: Automation in car production:
2014 - Great Wall Motors: A Chinese automotive manufacturer increased its efficiency by having robots collaborate in different parts of production.
For instance, one robot would position a panel and a second one would do the welding.
Foxconn, a Taiwanese electronics company, announced its intention to increase automation by 30%, resulting in the loss of 60,000 jobs.
Service robots
Service Robots: robots designed to assist humans in completing less desirable or dangerous tasks.
This type of robots can either be for domestic or professional use, such as:
Personal Service Robots: used at home. Robots can be programmed to autonomously complete a task.
Demand for them is growing, as they are more affordable and because they can assist elderly people.
Example: Robot Vacuum - they are programmed to clean the house and some even have a self-emptying bin feature, which makes it more autonomous.
Virtual Personal Assistants: voice-controlled helpers which are typically found in smart speakers or mobile phones.
Once connected, a user can command different activities like providing weather updates or setting a timer.
Examples: Google Home, Amazon Echo, Apple HomePod
Real-World Example: Virtual Assistants - Hampshire, UK (2018)
The Hampshire County Council trialed the use of virtual assistants to help carers for elderly people and people with disabilities.
The use of virtual assistant was beneficial to users, especially those with limited mobility and enabled the carers to focus on other tasks.
Professional Service Robot: semi-autonomous or fully autonomous robots which assist humans in commercial settings.
Most of these robots have some mobility and can interact with people.
They are used in a range of industries, such as retail, hospitality but can also perform harsh work in challenging environments like space, defense and agriculture.
A benefit of using service robots is that they can handle dangerous and repetitive tasks efficiently with little downtime.
Examples: Robots which make deliveries, assist in surgery.
Real - World Example: Flippy 2 (2017)
CaliBurger, an American fast-food chain, introduced Flippy, a ‘grill chef’ robot to counter staff problems and assist in the kitchen
Flippy 2, the second generation of the robot, expanded its tasks and features to incorporate an integrated kitchen ticket system. Additionally, it had sensors and machine learning to instruct itself how to fry food.
Social robots
Robots developed to interact and communicate with humans in a friendly manner.
These types of robots are in increasing demand in the workplace, to assist in customer service and at home, to be companions for elderly people.
The main setback is the robot’s lack of empathy or emotion, unexpected response to unknown situations and the potential threat of becoming fully autonomous.
Social robots differ from service robots, which are mainly used to perform undesired (either dangerous or unpleasant) tasks.
Real - World Example: Jibo
A social robot designed for the home environment, to provide friendship and companionship through facial and voice recognition.
Real - World Example: Aerobot
A robot assistant at Istanbul Sabiha Gökçen International Airport which reminds passengers on health policies, answers inquiries and guides passengers to boarding gates.
Passengers can receive a more personalized experience, since the robot can communicate in 20 languages and uses AI to identify approaching passengers to tailor its conversations.
Internet of Things (IoT)
Business previously used earlier forms of IoT, such as radio-frequency identification (RFID) tags to track delivery orders.
IoT uses have expanded, with the top five industrial uses being;
Predictive maintenance: use of wireless IoT to alert employees when a machine needs maintenance.
Location tracking: use of wireless technology such as GPS, RFID in order to track stock, components and/or equipment.
Since data is obtained in real-time, it allows employees to find items faster.
Workplace analytics: use of data analytics software to provide information to optimize operations and increase efficiency.
Remote quality monitoring: use of IoT devices to monitor quality of resources and products.
For instance, an organization can examine water or air quality and offer a faster response to potential pollution.
Energy optimization: use of IoT devices to measure energy consumption.
This technology is normally seen in manufacturing. It can warn of excessive consumption so employees adjust equipment to use less electricity.
Autonomous vehicles (AV)
Autonomous vehicle: a vehicle that has the ability to operate without human intervention.
There are different levels of autonomy.
Levels 0 - 3 are designed to assist a driver and show low levels of autonomy. Levels 4 to 5, on the other hand, do not require a driver.
Levels of autonomy:
Level 0: A traditional car which may have features such as cruise control activated for long distance or warning signs, when reversing. It has zero automation.
Level 1 - Driver Assistance: Has features such as adaptive cruise control to keep a safe distance between cars and lane keep assistance, to prevent vehicles from veering out of its lane. The majority of newer cars have these features.
Level 2 - Partial Automation: Enhanced assistance to drivers by having features such as controlling steering and speed. It is similar to autopilot but requires drivers to be aware of when they need to take control.
Real - World Example: Mercedes-Benz PARKTRONIC system
Mercedes-Benz launched a self-parking car using its PARKTRONIC system which uses a range of sensors to determine if a car can fit into spot and which automatically steer the car.
Drivers still need to control brakes and gears.
Level 3 - Conditional Automation: vehicles that can drive themselves under certain conditions but still need drivers to be behind the wheel.
Example: a vehicle driving automatically in a traffic jam.
Level 4 - High Automation: vehicles with no human driver, steering wheels or pedals and that are available for public use.
Such vehicles would only operate on certain conditions, for instance, they can only work under certain weather conditions.
Trialed services include driverless taxis and public transport, instances when a vehicle can be programmed to travel between two points.
Real - World Example: Driverless Taxis - Singapore (2016)
Singapore tried driverless taxis in 2016 in 12 locations and was planned to be widely available in 2018. Users needed to call the taxi through a smartphone app.
However, the service was limited to 10 people and available to non-peak hours.
Level 5 - Full Automation: has no restriction and would be fully responsive to real-time conditions such as weather and aware of other vehicles. Additionally, the vehicle could travel to any geographical location, without the need to program it.
This level has not been achieved but would be the highest level of automation.
Despite the rapid technological advances, there are obstacles which prevent full and high automation from happening
Sensors: which work by ‘seeing’ their environment, thus can be affected by bad weather, heavy traffic and road signs with graffiti.
Machine Learning: which is used to detect and classify objects, informing the vehicle how to act. However, there is a lack of consensus on industry standards for training and testing artificial intelligence.
Deep Learning: the vehicle continuously learns on the road, therefore the industry needs to draw standards that will make the vehicle safe to others.
Regulations and Standards: agreements between government and manufacturers which can allow autonomous vehicles to operate. International standards need to be considered for vehicles to operate across borders.
Social Acceptability: the general public needs to trust these vehicles, especially after several high-profile accidents.
Drones
Drone: also known as unmanned aerial vehicle (UAV) – a remote controlled or autonomous flying robot.
Initially, these were used in the military in three main activities: anti-aircraft practice, gathering data from sensors and used as weapons in military attacks.
Nowadays, drones are for commercial and private use and have two main functions: flight and navigation.
Examples: commercial drones - used for delivery, search and rescue operations, private drones - capturing video footage.
Real-World Example: Commercial Drones
Drones are used to make deliveries, especially to remote locations.
For example, Zipline, a company in Ghana, used drones to deliver medical supplies to 2000 medical centers.
3.7B: Characteristics of Robots and Autonomous Technologies
Robots have become more intelligent and can move with fluidity.
This is due to developments in artificial intelligence, which makes robots perceive and understand data.
Sensory Inputs for Spatial, Environmental and Operational Awareness
Technologies nowadays have made robots perceive surrounding by emulating humans’ five senses:
Vision: robots use digital cameras to capture images but need two cameras (or stereo vision camera) to create depth perception, enabling image recognition.
In addition, other technologies are needed to make robots aware of their surroundings.
Light Sensors: used to detect light levels, informing robots whether it is day or night.
Simple robots use infrared or ultrasound sensors, which emit beams of infrared light or sound signals. These calculate distance between objects after measuring the time it takes for light to bounce off an object.
More sophisticated robots (e.g. autonomous vehicles) use other sensors such as;
Lidar: light detection and ranging - measures shape, contour and height of objects
Sonar: sound navigation and ranging - measures the depth of water.
Radar: radio detection and ranging - detects moving objects and draws out the environment.
Although these sensors perform specialized tasks, they work like an infrared sensor, bouncing off light.
Hearing: use of a microphone to collect sound which is converted into electrical signals. When coupled with voice recognition, robots can ‘understand’ what is being spoken.
Smell and taste: robots use a chemical sensor, which collects data later transformed into an electrical signal. Robots use pattern recognition to identify the origin of smell or taste.
Touch: robots feature end effectors, which are grippers with pressure sensors or resistive touch sensors. These sensors help robots determine how much strength they need to hold an object
Capacitive touch sensors, on the other hand, detect objects which conduct electricity (including humans).
The Ability to Logically Reason with Inputs, Often Using Machine Vision and/or Machine Learning
Robot’s computerized control systems are used for decision-making – the actions are communicated to sensors, which collect data, process it and send an instruction to actuators and end effectors.
Robots with basic artificial intelligence are designed to solve problems in limited domains.
Example: inspection robot (production line) - determine if a produce is within approved limits
Modern robots use machine learning to develop a new skill within a limited capacity. This feature makes robots more intelligent, thus more useful in addition to improving and adapting to their environments.
Example: industrial robots - can learn to select different part types, especially through supervised learning, a subcategory of machine learning which uses a labeled database to produce algorithms.
Machine vision has enhanced depth and image recognition, making robots more useful and accurate on a production line.
The Ability to Interact and Move in Physical Environments
Robots have the ability to move in a physical space, whether they have a robotic arm or motorized wheels.
Actuator: a part of a device that moves or controls a mechanism. These control the ‘joints’ of a robot.
Actuators can be an electric motor, a hydraulic system (driven by incompressible fluid) or a pneumatic system (driven by compressed gas). All need power to operate.
Example: mobile robots used a battery to move
End effector: a peripheral device attached at the end of an actuator in order to grip objects and attach tools or sensors. End effectors can be either mechanical or electromechanical.
This device can include the following at their end;
Grippers: allow robots to pick up and manipulate objects. These are the most common form of end effectors.
Process tools: tools designed for specific tasks - e.g. welding, spray, drilling.
Sensors: used for applications such as robot inspections.
The Demonstration of Some Degree of Autonomy
Level of autonomy is determined by how independently a robot can operate without human intervention (a controller).
Semi-autonomous Robots
Have some level of intelligence - they can react to some conditions without the need of guidance.
Example: basic robotic vacuum - work autonomously with sensors to map space, path and detect debris. However, to change its settings it needs human intervention.
Fully Autonomous Robots
Operate independently, can accomplish complex tasks and have greater mobility.
Nonetheless they are still restricted to one working environment.
3.7C: Evolution of Robots and Autonomous Technologies
Early Forms of Robots and Autonomous Technology
The idea of robots is not new, being recorded in Egyptian and Greek civilizations. It is through the development of science, technology and artificial intelligence that robots have become a reality.
By 1500 BC, Egyptian water clocks (such as the Al-Jazari's Scribe Clock) worked by rotating figurines placed on top when water was poured. The figurine acted like clock hands.
Around 400 BC, Greek mathematician Archytas built a steam-powered mechanical bird.
1948: William Grey Walter creates Elmer and Elsie, autonomous robots which used wheels for mobility and could return to their recharging station when needed.
1958: A Stanford Research Institute team led by Charles Rosen develops Shakey, a robot which had some mobility through the use of wheels and had television ‘eyes’ to inspect the roam
Additionally, Shakey could make simple responses to its surroundings.
Robots in Science Fiction and Philosophy
The idea of robots was commonly found in science fiction stories.
1921: Czech author Karel Capek formally introduces the term ‘robot’ in his play Rossum’s Universal Robot.
The play’s protagonist created a robot and was later killed by it - a common theme reflecting anxieties which are still present.
1941: Russian author Isaac Asimov wrote three laws of robotics, which stressed robots must not attack humans although it also allowed robots to protect their existence and disobey orders if these threaten to harm humans.
Robots Designed for Industry and Manufacturing
Robots have been preferred in manufacturing since they are able to perform repetitive tasks and are capable of lifting heavy objects.
Some landmark developments include:
1951 - SNARC by Marvin Minsky: First neural network simulator.
1954-61 - Unimate by Georg Devol (USA): First programmable industrial robot, which was capable of transporting diecast and welding. It was designed for General Motors, a car manufacturer
1974 - IRB-6 by ABB (Sweden): First electric industrial robot controlled by a microcomputer. It was used for welding and polishing steel tubes.
1981 - Consight, General Motors: Three separate robots were set up to select up to six different auto parts at a time. The robots used visual sensors.
1981 - SCARA: Selective Compliance Robot Arm (Japan): An articulated robotic arm which was capable of loading and unloading items from one part of the manufacturing process to another.
1994: Motomarman MRC System, Yaskawa America, Inc: Robotic arms with up to 21 axes (degree of freedom) and the ability to synchronize two robots.
2008: UR5, Linatex (Denmark): The first collaborative robot (or ‘cobot’, intended to engage in direct human-robot interaction) to be placed in a production floor.
Robots Designed to Interact with Humans
Machine Consciousness, Cognitive Robotics and Robot Rights
Cognitive robotics: an emerging field which aims to design robots with human-like intelligence, which can perceive their environment, plan their actions and deal with uncertain situations.
The goal for this field is to develop predictive capabilities and the ability to view the world from different perspectives.
Earlier versions of robots are thought to lack consciousness and to only simulate intelligence.
As developments enable more sophisticated robots, the rights of robots are being discussed.
Real-World Example: Sophia (2016)
Sophia, a robot originally designed to help elderly people given its human-like features, became the first robot to be granted legal personhood after Saudi Arabia granted her citizenship.
This event propelled her to fame but also raised concern of the limitations of rights and autonomy granted to robots.
3.7D: Robots and Autonomous Technology Dilemmas
Anthropomorphism and The Uncanny Valley
Anthropomorphism: giving human-like characteristics to non-human entities.
Traditionally, animal characters in the media (e.g. Winnie the Pooh) were given such features. Robots are now given ‘friendly’ appearances to make interaction with humans more natural.
Examples: Sophia - displays uncanny lifelike expressions, ‘Pepper’ - adorable facial expression
Uncanny Valley: hypothesized emotional response to robots’ anthropomorphism, describing the unsettling feeling a human has when interacting with lifelike humanoid robots.
The concept was introduced by professor Masahiro Mori in 1970. He argued human-like robots would be more appealing until a certain point (i.e. uncanny valley) otherwise it will produce a negative reaction.
The proposition of the uncanny valley presents dilemmas for robot designers – while lifelike robots can be accepted in certain circumstances (e.g. training sessions) , they will likely not be generally accepted.
Complexity of Human and Environmental Interactions
The field of robotics aims to create robots that can effectively work with humans as well as being able to predict changes in their environment.
Cobots: robots designed to work alongside humans and augment their capabilities.
Because most cobots will work in the service sector (e.g. shop), they must be capable of understanding human emotions, language and behavior.
Nonetheless, it is challenging to both develop robots to interact with the environment and imitate human action.
Usually, when a robot is trained in a particular environment a minimal alteration might require robots to relearn and adapt to the modified environment.
In addition, walking requires complex technologies to mimic human mobility.
Real - World Example: Autonomous vehicle accident (2018)
A pedestrian was killed by an autonomous car after its safety driver failed to pay attention to the road and thus, did not stop the steering wheel on time.
Uneven and Undeveloped Laws, Regulations and Governance
Most guiding principles on robots are still based in Asimov’s 1940 Laws of robotics. However, recent development have risen new concern and need for clarification:
Nowadays, robots are more varied, therefore an agreed definition needs to be established.
Laws would not apply to all robots - for example, a military robot would not comply with Asimov’s first law (robots should not harm humans).
Countries with advances in robotics are prioritizing legislation, especially for drones, autonomous vehicles and manufacturing robots. Some examples include:
Robot Ethics Charter - South Korea (2007): inspired by Asimov laws, it was envisioned as an ethical guide on robot development and designed to reduce problems associated with service and social robots for the elderly.
UK (2016): published a standards guide for ethical design and application of robots. Although the document is not legally binding, it aimed to raise awareness of dilemmas faced in the future.
Laws might change in different countries, although robot designers are still held accountable.
Robot applications are considered to be products and therefore would be prosecuted under product liability laws (e.g. US Restatement of Torts, Third and European Product Liability Directive).
Displacement of Humans in Multiple Contexts and Roles
Real - World Example: Automation and job losses (2019)
Oxford Economics predicted that 20 million manufacturing jobs worldwide could be replaced by robots in 2030.
Automation is replacing lower-skilled jobs. Therefore, governments need to find a balance between promoting innovation but avoiding unemployment growth.
The study focused on manufacturing jobs, however, other industries are also vulnerable to undergo automation, such as:
Food Industry: mainly relying on repetitive physical activity in a predictable environment – conditions in which a robot can thrive.
Education and health care: interpersonal work could potentially be performed by cobots.
Law Enforcement and Security: cobots are already used alongside humans in patrolling, but could soon do this task autonomously.
Nonetheless, as robots become more sophisticated, there will be demand for high-skilled jobs such as: robot engineers, robotic technicians, software developers, robotic operators and robotics sales people.
Chapter 8: Artificial Intelligence
Artificial Intelligence
A branch of computer science that aims to create systems capable of performing tasks that typically require human intelligence.
Tasks include reasoning, learning, problem-solving, perception, language understanding, and decision-making.
The simulation of human intelligence processes by machines, especially computer systems.
Processes include learning (the acquisition of information and rules for using it), reasoning (using rules to reach approximate or definite conclusions), and self-correction.
Goals of AI
Automation of Intelligent Behavior: Creating systems that can perform tasks without human intervention.
Understanding Human Intelligence: Gaining insights into human cognition by modeling intelligent behavior.
Enhancing Human Capabilities: Augmenting human abilities in various domains through intelligent systems.
Evolution Over Time
Early Foundations (1940s-1950s):
Alan Turing: Proposed the concept of a machine that could simulate any conceivable mathematical computation, laying the groundwork for AI. His famous Turing Test, introduced in 1950, is a measure of a machine's ability to exhibit intelligent behavior indistinguishable from a human.
John von Neumann: Contributed to the development of digital computers, which are essential for AI.
Birth of AI (1950s-1960s):
Dartmouth Conference (1956): Considered the birthplace of AI, where John McCarthy, Marvin Minsky, Nathaniel Rochester, and Claude Shannon coined the term "Artificial Intelligence" and discussed the possibility of creating intelligent machines.
Early Programs: Logic Theorist and General Problem Solver (GPS) by Allen Newell and Herbert A. Simon demonstrated that machines could perform tasks requiring symbolic reasoning.
First AI Winter (1970s):
Disappointment and Funding Cuts: Early AI systems, like expert systems, failed to meet the high expectations, leading to reduced funding and interest in AI research.
Expert Systems (1980s):
Renewed Interest: Development of expert systems that could mimic the decision-making abilities of human experts in specific domains, such as MYCIN for medical diagnosis.
Second AI Winter (Late 1980s-1990s):
Limitations and Over-promises: Expert systems proved brittle and expensive to maintain, leading to another period of reduced AI funding and enthusiasm.
Resurgence and Modern AI (2000s-Present):
Machine Learning and Big Data: Advances in machine learning, fueled by the availability of large datasets and increased computational power, led to breakthroughs in AI capabilities.
Deep Learning: Development of deep neural networks that significantly improved performance in tasks like image recognition, natural language processing, and game playing.
AI in Everyday Life: AI technologies like virtual assistants (e.g., Siri, Alexa), recommendation systems, autonomous vehicles, and AI-driven medical diagnostics have become integral parts of daily life.
Turing Test
The Turing Test is a concept introduced by Alan Turing in 1950 as a measure of a machine's ability to exhibit intelligent behavior that is indistinguishable from that of a human. It is a foundational idea in the philosophy of artificial intelligence and has influenced how we think about machine intelligence.
The Turing Test involves an interaction between a human (the "interrogator"), a machine, and a human "confederate" (another human). The interrogator communicates with both the machine and the confederate through a computer interface (to prevent any physical or vocal clues) and must determine which is which based solely on their responses to questions.
The goal is to assess whether the machine can engage in conversation in such a way that the interrogator cannot reliably distinguish it from the human confederate.
How It Works
Setup:
Interrogator: A human who asks questions to both the machine and the human confederate.
Machine: An AI system designed to respond to questions and engage in conversation.
Human Confederates: Human participants who also respond to the interrogator’s questions.
Interaction:
All communication occurs through text to prevent any clues based on voice or appearance.
The interrogator poses a series of questions to both the machine and the human confederate.
Judgment:
After a set period, the interrogator must decide which of the two respondents is the machine and which is the human based on their responses.
If the interrogator is unable to reliably distinguish between the machine and the human (i.e., the machine is mistaken for the human at least as often as the human confederate), the machine is said to have passed the Turing Test.
Significance
Benchmark for AI: The Turing Test provides a practical and human-centric benchmark for evaluating the performance of AI systems. It focuses on the quality of interaction and the machine's ability to mimic human-like responses.
Philosophical Implications: It raises important questions about the nature of intelligence, consciousness, and whether machines can truly "think" or merely simulate thought processes.
Limitations:
Narrow Scope: The Turing Test only evaluates conversational ability and does not account for other aspects of intelligence, such as learning, reasoning, or creativity.
Deception: A machine may pass the Turing Test by using clever strategies or pre-programmed responses without actually understanding or possessing general intelligence.
Examples and Applications
Chatbots and Virtual Assistants:
Modern chatbots and virtual assistants (e.g., Siri, Alexa) are often evaluated against the Turing Test. While they can handle specific tasks and maintain a conversation, they may still struggle with complex or abstract queries.
AI Competitions:
Various competitions and demonstrations, such as the Loebner Prize, use variations of the Turing Test to evaluate AI systems' conversational capabilities.
Types of AI
Narrow AI (Weak AI):
Definition: AI systems designed to perform a specific task or a narrow range of tasks.
Examples:
Virtual assistants like Siri and Alexa.
Recommendation systems used by Netflix and Amazon.
Autonomous vehicles that can navigate and drive.
Characteristics: Highly specialized, limited to predefined functions, does not possess general intelligence or understanding beyond its specific domain.
General AI (Strong AI):
Definition: AI systems with generalized cognitive abilities that can understand, learn, and apply knowledge across a wide range of tasks, similar to human intelligence.
Examples:
Hypothetical future AI that can perform any intellectual task a human can.
Characteristics: Capable of reasoning, problem-solving, and learning in a way that is indistinguishable from human intelligence. Still a theoretical concept and has not been realized.
Superintelligent AI:
Definition: AI systems that surpass human intelligence in all aspects, including creativity, problem-solving, and emotional intelligence.
Examples:
Hypothetical future AI that exceeds the cognitive performance of humans in all domains.
Characteristics: Far beyond current technological capabilities. The concept raises significant ethical and existential questions regarding control, safety, and impact on humanity.
Types and Uses of Machine Learning
Supervised Learning
Supervised Learning is a type of machine learning where the algorithm learns from a labeled dataset. This means that the dataset includes both the input data and the corresponding correct output. The goal is for the algorithm to learn the mapping from inputs to outputs so that it can make accurate predictions or classifications on new, unseen data.
Here's a more detailed breakdown:
Key Concepts
Labeled Data:
Inputs (Features): These are the attributes or properties of the data that the model will learn from. For example, in a dataset of houses, features could include the number of bedrooms, size of the house, and location.
Outputs (Labels): These are the correct answers or outcomes for each input. For the house dataset, labels could be the price of each house.
Training Process:
The algorithm uses the labeled data to learn the relationship between the inputs and outputs.
This involves optimizing a function that maps the inputs to the outputs by minimizing the difference between the predicted outputs and the actual labels.
Prediction:
Once trained, the model can take new, unseen inputs and predict their corresponding outputs based on what it has learned.
Common Algorithms
Decision Trees:
A decision tree is a flowchart-like structure where each internal node represents a decision based on the value of a feature, each branch represents the outcome of the decision, and each leaf node represents a class label (or regression value).
Example: Predicting whether a person will buy a product based on age, income, and browsing history.
Neural Networks:
Neural networks are composed of layers of interconnected nodes (neurons) that process input data to make predictions. Each connection has a weight that is adjusted during training.
Example: Recognizing handwritten digits, where the input is an image of a digit and the output is the digit itself (0-9).
Steps in Supervised Learning
Data Collection:
Gather a large and representative labeled dataset.
Data Preprocessing:
Clean the data (handle missing values, remove duplicates).
Normalize or scale features if necessary.
Split the data into training and testing sets.
Model Selection:
Choose an appropriate algorithm based on the problem (classification or regression).
Training:
Feed the training data into the model and allow it to learn by adjusting its parameters.
Evaluation:
Test the model on the testing set to evaluate its performance using metrics like accuracy, precision, recall, or mean squared error.
Prediction and Deployment:
Use the trained model to make predictions on new data.
Deploy the model in a real-world application if needed.
Example Application
Spam Email Classification:
Inputs (Features): Email content, subject line, sender's address, frequency of certain words.
Output (Label): Whether the email is spam or not spam.
Process: The model is trained on a dataset of emails labeled as spam or not spam. It learns patterns and characteristics of spam emails. Once trained, it can classify new incoming emails as spam or not based on these learned patterns.
Unsupervised Learning
Unsupervised Learning is a type of machine learning where the algorithm learns from data that does not have labeled responses. The goal is to identify patterns, structures, or relationships within the data without any prior knowledge of what the output should be. This contrasts with supervised learning, where the algorithm is trained on labeled data.
Key Concepts
Unlabeled Data:
Inputs (Features): These are the attributes or properties of the data that the model will analyze. In unsupervised learning, there are no labels or target values provided.
No Outputs (Labels): The data does not include corresponding correct answers, so the algorithm must find the structure in the data on its own.
Learning Objectives:
The main objective is to explore the data and identify patterns, groupings, or associations without any supervision.
Common tasks include clustering, association, and dimensionality reduction.
Common Algorithms
Clustering:
Clustering algorithms group similar data points together based on certain characteristics.
K-Means Clustering: Partitions data into K clusters, where each data point belongs to the cluster with the nearest mean.
Example: Customer segmentation in marketing, where customers are grouped based on purchasing behavior.
Association:
Association algorithms find rules that describe large portions of the data.
Apriori Algorithm: Identifies frequent itemsets in transactional data and generates association rules.
Example: Market basket analysis, where the goal is to find products that frequently co-occur in transactions.
Dimensionality Reduction:
These techniques reduce the number of random variables under consideration, making the data easier to visualize and analyze.
Principal Component Analysis (PCA): Transforms data into a new coordinate system, reducing the dimensions while retaining most of the variance.
Example: Reducing the complexity of high-dimensional data like images while preserving important information.
Steps in Unsupervised Learning
Data Collection:
Gather a large and representative dataset without labels.
Data Preprocessing:
Clean the data (handle missing values, remove duplicates).
Normalize or scale features if necessary.
Model Selection:
Choose an appropriate algorithm based on the problem (clustering, association, or dimensionality reduction).
Training:
Feed the data into the model, allowing it to analyze and identify patterns or groupings.
Evaluation:
Evaluate the results using techniques like silhouette score for clustering or variance explained for dimensionality reduction.
Interpret the identified patterns or groupings to gain insights.
Application:
Use the results to inform decisions or as a preprocessing step for other machine learning tasks.
Example Application
Customer Segmentation:
Inputs (Features): Customer demographics, purchase history, browsing behavior.
Process: Use clustering algorithms like K-Means to group customers into segments based on similarities in their behavior and characteristics.
Outcome: Identify distinct customer segments (e.g., budget shoppers, frequent buyers, premium customers) that can be targeted with personalized marketing strategies.
Reinforcement Learning
Reinforcement Learning (RL) is a type of machine learning where an agent learns to make decisions by performing actions in an environment to achieve maximum cumulative reward. Unlike supervised learning, where the model learns from labeled data, or unsupervised learning, where the model identifies patterns in unlabeled data, reinforcement learning is based on the concept of learning through interaction and feedback.
Key Concepts
Agent: The learner or decision-maker that interacts with the environment.
Environment: The external system with which the agent interacts. It provides the agent with feedback in the form of rewards and observations.
State: A representation of the current situation of the environment. The state provides the necessary context for the agent to make decisions.
Action: A set of all possible moves the agent can make in the environment. The agent chooses an action based on the current state.
Reward: A scalar feedback signal that tells the agent how good or bad its action was in the context of the overall task.
Policy: A strategy used by the agent to decide which actions to take, given the current state. It can be deterministic or stochastic.
Value Function: A function that estimates the expected cumulative reward of being in a given state (or state-action pair) and following a particular policy.
The Reinforcement Learning Process
Initialization: The agent starts by initializing its policy and value function (if used).
Interaction: The agent observes the current state of the environment.
Action Selection: The agent selects an action based on its policy.
Environment Response: The environment transitions to a new state and provides a reward based on the action taken.
Learning: The agent updates its policy and/or value function based on the received reward and the new state.
Iteration: Steps 2-5 are repeated until the agent converges to an optimal policy or a predefined stopping criterion is met.
Types of Reinforcement Learning
Model-Free RL: The agent learns directly from interactions with the environment without a model of the environment's dynamics.
Q-Learning: An off-policy algorithm that learns the value of taking a specific action in a specific state by updating Q-values (state-action values).
SARSA (State-Action-Reward-State-Action): An on-policy algorithm that updates Q-values based on the action actually taken by the current policy.
Model-Based RL: The agent builds a model of the environment's dynamics and uses it to plan by simulating different scenarios.
Dynamic Programming: Uses a model of the environment to iteratively compute the value function and derive the optimal policy.
Policy Gradient Methods: These directly adjust the policy based on the gradient of expected reward with respect to the policy parameters.
REINFORCE Algorithm: Uses the gradient of the expected return to update the policy parameters.
Example Application
Playing a Game (e.g., Chess):
Agent: The AI player.
Environment: The chessboard and the rules of the game.
State: The current configuration of the chess pieces on the board.
Action: Legal moves the player can make.
Reward: Positive reward for winning, negative reward for losing, and possible smaller rewards for advantageous positions or capturing pieces.
Policy: A strategy for choosing moves based on the current board state.
Learning: The agent plays numerous games, learning which strategies lead to wins (positive rewards) and which lead to losses (negative rewards).
Neural Networks and Deep Learning
Neural Networks are computational models inspired by the human brain, consisting of layers of interconnected nodes, or neurons. They are particularly useful for complex tasks such as image and speech recognition. Deep Learning refers to neural networks with many layers, also known as deep neural networks, which can model high-level abstractions in data.
Key Concepts
Neurons and Layers:
Neurons: Basic units of a neural network that receive inputs, process them, and pass the output to the next layer.
Layers: Structures that contain neurons. There are typically three types:
Input Layer: Takes in the initial data.
Hidden Layers: Intermediate layers where computations are performed. A network with many hidden layers is considered "deep."
Output Layer: Produces the final output of the network.
Weights and Biases:
Weights: Parameters that are adjusted during training. They determine the strength of the connection between neurons.
Biases: Additional parameters that allow the activation function to shift to the left or right, improving the model’s flexibility.
Activation Functions:
Functions that introduce non-linearity into the network, allowing it to learn more complex patterns. Common activation functions include:
Sigmoid: Outputs values between 0 and 1.
ReLU (Rectified Linear Unit): Outputs the input directly if positive, otherwise zero.
Tanh: Outputs values between -1 and 1.
Forward Propagation:
The process of passing input data through the network layers to obtain an output. Each neuron processes the input, applies the weights, adds the bias, and passes the result through the activation function.
Loss Function:
A function that measures the difference between the predicted output and the actual output. Common loss functions include mean squared error (MSE) for regression tasks and cross-entropy loss for classification tasks.
Backpropagation:
The process of updating the weights and biases based on the loss function. It involves calculating the gradient of the loss function with respect to each weight (using the chain rule of calculus) and adjusting the weights to minimize the loss.
Optimization Algorithms:
Methods used to update the weights and biases during training. Common algorithms include:
Gradient Descent: Updates weights in the direction that reduces the loss.
Stochastic Gradient Descent (SGD): Updates weights using a subset of the data, which is faster and can escape local minima.
Adam: Combines the advantages of two other extensions of SGD, improving training efficiency and stability.
Deep Learning Architectures
Convolutional Neural Networks (CNNs):
Specialized for processing grid-like data such as images.
Convolutional Layers: Apply convolution operations to extract features from input images.
Pooling Layers: Reduce the dimensionality of the data, making the computation more manageable.
Recurrent Neural Networks (RNNs):
Designed for sequential data such as time series or text.
Recurrent Layers: Maintain a hidden state that captures information from previous time steps.
LSTM (Long Short-Term Memory) and GRU (Gated Recurrent Unit): Variants of RNNs that address the vanishing gradient problem, allowing the network to capture long-term dependencies.
Autoencoders:
Networks used for unsupervised learning tasks such as dimensionality reduction or denoising.
Encoder: Compresses the input into a lower-dimensional representation.
Decoder: Reconstructs the input from the lower-dimensional representation.
Generative Adversarial Networks (GANs):
Consist of two networks, a generator and a discriminator, that compete with each other.
The generator creates fake data, and the discriminator tries to distinguish between real and fake data.
Used for generating realistic images, videos, and other data.
Example Application
Image Classification with CNNs:
Input Layer: Takes an image as input.
Convolutional Layers: Extract features from the image, such as edges, textures, and patterns.
Pooling Layers: Reduce the spatial dimensions of the data, preserving important features while reducing computational load.
Fully Connected Layers: Flatten the output from the convolutional layers and apply weights to make the final classification.
Output Layer: Produces the probability of the image belonging to each class.
AI Dilemma. Ethical Dilemmas
Bias and Fairness
Issue: AI systems can perpetuate or even exacerbate existing biases if they are trained on biased data. For example, facial recognition systems may have higher error rates for certain demographic groups.
Impact: This can lead to unfair treatment or discrimination in areas like hiring, law enforcement, and lending.
Solution: Implementing techniques to detect and mitigate bias, using diverse and representative training data, and ensuring transparency in AI systems.
Privacy
Issue: AI technologies, such as surveillance systems and data analytics, can infringe on individual privacy by collecting, analyzing, and storing personal data without adequate consent.
Impact: Risk of unauthorized access, data breaches, and misuse of personal information.
Solution: Enforcing strong data protection regulations, obtaining informed consent, and employing privacy-preserving technologies.
Autonomy and Control
Issue: AI systems making decisions autonomously can lead to situations where humans lose control over critical processes, such as autonomous vehicles or military drones.
Impact: Risks of unintended consequences and reduced human oversight.
Solution: Design systems with clear human-in-the-loop mechanisms, robust safety protocols, and transparency.
Social Dilemmas
Job Displacement
Issue: Automation and AI can replace certain jobs, leading to significant economic and social challenges for affected workers.
Impact: Increased unemployment and economic inequality.
Solution: Investing in reskilling and upskilling programs, creating new job opportunities, and considering policies for economic support.
Security
Issue: AI can be used for malicious purposes, such as creating deepfakes, conducting cyberattacks, or developing autonomous weapons.
Impact: Threats to national security, public safety, and personal security.
Solution: Strengthening cybersecurity measures, international regulations on AI weapons, and developing detection methods for malicious AI activities.
Technical Dilemmas
Explainability and Transparency
Issue: Many AI systems, particularly those based on deep learning, operate as "black boxes," making it difficult to understand how they make decisions.
Impact: Challenges in trusting and validating AI decisions, especially in critical applications like healthcare and finance.
Solution: Developing methods for explainable AI, improving transparency in algorithms, and ensuring that decision-making processes are understandable and accountable.
Robustness and Reliability
Issue: AI systems can be vulnerable to adversarial attacks or unexpected failures, leading to incorrect or harmful outcomes.
Impact: Risks to system reliability and safety, particularly in high-stakes environments.
Solution: Enhancing the robustness of AI models through rigorous testing, adversarial training, and continuous monitoring.
Existential Dilemmas
Superintelligent AI
Issue: The hypothetical development of superintelligent AI, which would exceed human intelligence across all domains, raises concerns about control and the future of humanity.
Impact: Potential for uncontrollable AI systems with unforeseen consequences.
Solution: Engaging in long-term research on AI safety, developing frameworks for controlling advanced AI, and promoting international cooperation on AI governance.
Alignment Problem
Issue: Ensuring that advanced AI systems’ goals and actions are aligned with human values and interests.
Impact: Risk of AI pursuing goals that are misaligned with human well-being.
Solution: Researching value alignment, incorporating ethical guidelines into AI design, and ensuring that AI systems are designed to prioritize human values.
Chapter 9: Global Well-Being
Introduction
In the context of the Digital Society course within the International Baccalaureate (IB) syllabus, the topic of global well-being is essential. It encompasses understanding how digital technologies impact various aspects of human life, from health to economic prosperity. This study note will break down the complex ideas related to global well-being into digestible sections, providing examples, tips, and notes to aid comprehension.
Global Well-being
Definition of Global Well-being
Global well-being refers to the overall health, happiness, and prosperity of individuals and communities worldwide. It includes various dimensions such as physical health, mental health, economic stability, social relationships, and environmental quality.
Dimensions of Global Well-being
Physical Health
Physical health is a crucial component of global well-being. Digital technologies have significantly impacted healthcare by:
Telemedicine: Remote diagnosis and treatment of patients using telecommunications technology.
Wearable Health Devices: Devices like smartwatches that monitor vital signs and activity levels.
Electronic Health Records (EHRs): Digital versions of patients' paper charts, providing real-time, patient-centered records.
Example:
Example: During the COVID-19 pandemic, telemedicine became a vital tool for providing healthcare services while maintaining social distancing. Patients could consult doctors via video calls, reducing the risk of virus transmission.
Mental Health
Mental health is another critical aspect of global well-being. Digital technologies influence mental health in both positive and negative ways:
Positive Impacts:
Online Counseling: Access to mental health professionals through online platforms.
Mental Health Apps: Apps that provide meditation, stress relief, and mental health tracking.
Negative Impacts:
Social Media: Excessive use can lead to anxiety, depression, and low self-esteem.
Tip:
Tip: Encourage balanced use of digital devices to maintain mental health. Regular breaks and mindful usage can mitigate negative impacts.
Common Mistake:
Common Mistake: Assuming that all digital interactions are beneficial for mental health. It is essential to differentiate between supportive and harmful digital content.
Economic Stability
Economic stability is influenced by digital technologies through:
E-commerce: Online platforms that facilitate buying and selling of goods and services.
Remote Work: Technology enabling people to work from anywhere, increasing job opportunities and flexibility.
Digital Financial Services: Online banking, mobile payments, and cryptocurrencies.
Example:
Example: The rise of e-commerce giants like Amazon has revolutionized the retail industry, providing consumers with more choices and convenience while creating new economic opportunities.
Social Relationships
Digital technologies affect social relationships by:
Social Media: Platforms that connect people globally, fostering relationships and communication.
Online Communities: Groups with shared interests that provide support and information.
Note:
Note: While digital technologies can enhance social relationships, they can also lead to superficial interactions and a sense of isolation if not used mindfully.
Environmental Quality
Digital technologies can both positively and negatively impact environmental quality:
Positive Impacts:
Smart Technologies: Smart grids, smart homes, and IoT devices that optimize resource usage.
Environmental Monitoring: Sensors and data analytics to monitor and manage environmental conditions.
Negative Impacts:
E-waste: The disposal of electronic devices contributes to environmental pollution.
Energy Consumption: Data centers and digital devices consume significant amounts of energy.
Example:
Example: Smart thermostats like Nest help reduce energy consumption by learning users' habits and adjusting temperatures accordingly, contributing to energy efficiency.
Measuring Global Well-being
Global well-being can be measured using various indices and tools, such as:
Human Development Index (HDI): Measures a country's average achievements in health, education, and income.
Gross National Happiness (GNH): Assesses the collective happiness and well-being of a population.
World Happiness Report: Ranks countries based on factors like social support, income, and healthy life expectancy.
Challenges and Considerations
Digital Divide
The digital divide refers to the gap between those who have access to digital technologies and those who do not. This divide can exacerbate existing inequalities in global well-being.
Note:
Bridging the digital divide is crucial for ensuring that all individuals and communities can benefit from digital technologies.
Privacy and Security
With the increasing use of digital technologies, concerns about privacy and data security have become paramount. Protecting personal information and ensuring secure digital interactions are essential for maintaining trust and well-being.
Tip:
Use strong passwords, enable two-factor authentication, and be cautious about sharing personal information online to enhance digital security.
Ethical Considerations
The ethical implications of digital technologies must be considered. Issues such as data ownership, algorithmic bias, and the ethical use of AI need to be addressed to ensure that technologies contribute positively to global well-being.
Common Mistake:
Common Mistake: Overlooking the ethical implications of digital technologies. It is essential to consider the broader impact of technology on society and individual well-being.
Conclusion
Global well-being in the digital age is a multifaceted concept that encompasses physical and mental health, economic stability, social relationships, and environmental quality. Digital technologies have the potential to enhance global well-being, but they also pose challenges that need to be addressed. By understanding these dimensions and their impacts, we can work towards a more equitable and prosperous digital society.
Chapter 10: Governance and Human Rights
Introduction
In the digital age, the intersection of governance and human rights has become a critical area of study. As technology continues to evolve, so do the ways in which governments and organizations interact with individuals and their rights. This study note will delve into the key aspects of governance and human rights within the context of a digital society, as outlined in the International Baccalaureate (IB) syllabus.
Governance in the Digital Society
Definition and Scope
Governance in the digital society refers to the frameworks, policies, and practices that guide the use and management of digital technologies. This includes how governments, organizations, and individuals interact with and regulate digital platforms and data.
Key Components
Digital Policies and Regulations:
Data Protection Laws: Regulations like the General Data Protection Regulation (GDPR) in the European Union set standards for data privacy and protection.
Cybersecurity Measures: Policies to protect against cyber threats, including hacking and data breaches.
Intellectual Property Rights: Laws that protect the ownership of digital content and innovations.
Digital Governance Models:
Centralized Governance: A model where a central authority, such as a government, controls digital policies and infrastructure.
Decentralized Governance: A model where control is distributed among various stakeholders, such as in blockchain technology.
Public-Private Partnerships:
Collaborations between government entities and private companies to develop and implement digital infrastructure and services.
Tip:
Understanding the differences between centralized and decentralized governance models can help in analyzing their impact on digital society.
Examples
Estonia's e-Government: Estonia is known for its advanced digital governance, offering services like e-residency, online voting, and digital signatures.
China's Internet Censorship: The Chinese government employs a centralized model to control internet access and content through the Great Firewall of China.
Human Rights in the Digital Society
Definition and Scope
Human rights in the digital society pertain to the protection and promotion of fundamental rights and freedoms in the context of digital technologies. This includes privacy, freedom of expression, and access to information.
Key Components
Privacy Rights:
The right to control personal information and data.
Protection against unauthorized surveillance and data breaches.
Freedom of Expression:
The right to express opinions and share information freely online.
Balancing this right with the need to prevent hate speech and misinformation.
Access to Information:
Ensuring equitable access to digital resources and information.
Addressing the digital divide that affects marginalized communities.
Note:
Privacy rights are often in tension with government surveillance programs aimed at ensuring national security.
Examples
Edward Snowden Revelations: Highlighted the extent of government surveillance on individuals' digital communications.
Internet Shutdowns: Governments in countries like India and Myanmar have shut down internet access to control information flow during political unrest.
Balancing Governance and Human Rights
Challenges
Surveillance vs. Privacy:
Governments argue that surveillance is necessary for national security, but it often infringes on individuals' privacy rights.
Censorship vs. Freedom of Expression:
Efforts to curb hate speech and misinformation can sometimes lead to unjust censorship of legitimate expression.
Digital Divide:
Ensuring that all individuals have access to digital technologies while addressing disparities in digital literacy and infrastructure.
Solutions
Transparent Policies:
Governments and organizations should develop clear and transparent policies that balance security needs with human rights protections.
Multi-Stakeholder Approach:
Involving various stakeholders, including civil society, in the development of digital governance frameworks.
Technological Innovations:
Leveraging technology to enhance privacy protections, such as through encryption and anonymization techniques.
Common Mistake:
Assuming that more surveillance always leads to better security can overlook the potential for abuse and infringement on privacy rights.
Conclusion
Governance and human rights in the digital society are complex and interrelated topics that require careful consideration and balanced approaches. As digital technologies continue to advance, it is crucial to develop frameworks that protect individual rights while enabling effective governance. By understanding the key components and challenges, we can work towards a digital society that is both secure and respectful of human rights.
Chapter 11: Sustainable Development
Introduction
Sustainable development is a critical concept in the modern world, particularly in the context of a digital society. It refers to meeting the needs of the present without compromising the ability of future generations to meet their own needs. This concept has significant implications in the digital age, where technology and innovation can both drive and hinder sustainable practices. In this study note, we will explore various aspects of sustainable development within the digital society, breaking down complex ideas into manageable sections.
Understanding Sustainable Development
Definition and Principles
Sustainable development encompasses three core principles:
Economic Sustainability: Ensuring that economic growth is inclusive and provides opportunities for all, without depleting resources.
Social Sustainability: Promoting social well-being and equity, ensuring that all individuals have access to basic needs and opportunities.
Environmental Sustainability: Protecting and conserving natural resources and ecosystems for future generations.
The Role of Technology
Technology can play a dual role in sustainable development:
Positive Impact: Innovation in technology can lead to more efficient resource use, renewable energy solutions, and improved quality of life.
Negative Impact: Conversely, technology can contribute to environmental degradation, e-waste, and social inequalities if not managed properly.
Example:
Example: Solar panels are a technological innovation that supports environmental sustainability by providing renewable energy. However, the production and disposal of solar panels need to be managed to avoid environmental harm.
Digital Society and Sustainable Development
Digital Transformation
Digital transformation refers to the integration of digital technology into all areas of business and society, fundamentally changing how we operate and deliver value. This transformation can support sustainable development in several ways:
Efficiency and Productivity: Digital tools can improve efficiency, reducing waste and resource consumption.
Access to Information: The internet and digital platforms provide access to information and education, promoting social sustainability.
Innovation: Digital technologies foster innovation, leading to new solutions for sustainability challenges.
Note:
Digital transformation must be inclusive to ensure that all segments of society benefit from technological advancements.
Challenges and Risks
Despite its potential, the digital society faces several challenges in achieving sustainable development:
Digital Divide: Inequitable access to digital technologies can exacerbate social inequalities.
E-Waste: The rapid turnover of electronic devices leads to significant e-waste, posing environmental hazards.
Energy Consumption: Data centers and digital infrastructure consume substantial amounts of energy, contributing to environmental degradation.
Common Mistake:
Common Mistake: Assuming that all digital advancements are inherently sustainable. It's essential to evaluate the broader impact of technology on society and the environment.
Sustainable Development Goals (SDGs) and Digital Society
The United Nations' Sustainable Development Goals (SDGs) provide a comprehensive framework for sustainable development. Digital technologies can support several SDGs, including:
SDG 4: Quality Education: Online learning platforms can enhance access to education.
SDG 7: Affordable and Clean Energy: Smart grids and IoT can optimize energy use.
SDG 9: Industry, Innovation, and Infrastructure: Digital infrastructure can drive innovation and economic growth.
SDG 11: Sustainable Cities and Communities: Smart city technologies can improve urban sustainability.
Tip:
Leverage open-source platforms and collaborative tools to promote inclusive and sustainable digital solutions.
Case Studies
Smart Cities
Smart cities use digital technologies to enhance the quality of urban life while promoting sustainability. Key features include:
Smart Grids: Efficient energy distribution systems.
IoT Sensors: Monitoring and managing urban infrastructure.
Sustainable Transportation: Electric vehicles and smart traffic management.
Example:
Example: Barcelona, Spain, has implemented smart city technologies to improve energy efficiency, reduce traffic congestion, and enhance public services.
Green IT
Green IT involves designing, manufacturing, using, and disposing of computers, servers, and associated subsystems efficiently and effectively with minimal or no impact on the environment. Practices include:
Energy-Efficient Hardware: Using devices that consume less power.
Virtualization: Reducing the number of physical servers required.
Recycling Programs: Proper disposal and recycling of electronic waste.
Note:
Green IT not only benefits the environment but can also reduce operational costs for organizations.
Conclusion
Sustainable development in a digital society requires a balanced approach that leverages technology to promote economic, social, and environmental sustainability. By understanding the principles of sustainable development and the role of digital transformation, we can address the challenges and harness the opportunities presented by digital technologies. Through careful planning, innovation, and collaboration, we can achieve a sustainable future for all.