2.10 - CompTIA A+ Core 2
Router settings
Change default passwords
Change default password: Security practice for SOHO networks - implement to prevent an attacker from guessing your password based on a manufacturer’s default passwords/credentials.
IP filtering
IP filtering: SOHO network/router feature that allows administrators to control the flow of traffic between devices by specifying which IP addresses/FQDNs are permitted or denied access to the network.
Firmware updates
Firmware updates: Upgrades to the OS/software of a SOHO network router - typically contains bug fixes or security updates.
Content filtering
Content filtering: A SOHO network feature that denies access to certain websites due to their inherent insecurity, or their content being inappropriate for work purposes (e.g., gambling sites).
Physical placement/secure locations
Physical placement/secure locations: Ensuring that networking equipment is installed in areas that are safe from environmental threats and unauthorized access, such as locking server rooms or utilizing cable management to prevent physical tampering.
Universal Plug and Play (UPnP)
Universal Plug and Play (UPnP): SOHO network feature that allows automatic configuration when certain applications are used on a network - when an app uses this, it will communicate to the router and instruct it to start a port forward/firewall exception to allow access for an application service.
Screened subnet
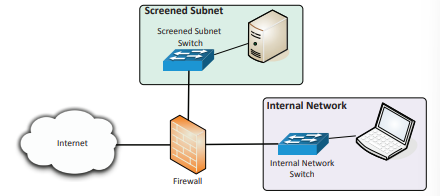
Screened subnet: Previously known as a demilitarized zone (DMZ) - an isolated segment of a private network that can access the internet while separating sensitive internal network resources from the external environment.
Configure and secure management access
Management access: Management access to a SOHO router must be tightly controlled - use a relatively complex management password, with an additional authentication factor, if possible.
Wireless specific
Changing the service set identifier (SSID)
Changing the service set identifier (SSID): Change the SSID to a not-so-obvious name (no locations or personal information).
Service Set Identifier (SSID): The unique identifier (name) for a wireless network - helps to distinguish it from other Wi-Fi networks.
Disabling SSID broadcast
Disabling an SSID broadcast: This setting prevents the network name from being publicly broadcast, making it less visible to casual users and potential intruders (via wireless network analysis).
PROJECT IDEA: Use Wireless Network Analysis to find an SSID.
Encryption settings
Open System: Wi-Fi encryption that uses no password/pre-shared key. Common for public Wi-Fi.
WPA2/3-PSK (WPA2/3-Personal): WPA2/3 encryption that uses a 256-bit pre-shared key (i.e., a password) for every connected device.
WPA2/3-802.1X (WPA2/3-Enterprise): WPA2/3 encryption that uses a centralized authentication server (e.g., Kerberos, RADIUS, Active Directory).
Configuring guest access
Configuring guest access: Limit guest network access to outsiders - guest access can be enabled for IoT devices or lab networks, but don’t enable without WPA2/3.
Firewall settings
Firewall settings: Ensure that firewall rules are configured to block unauthorized access to the guest network, and monitor traffic for unusual activity to maintain security.
Disabling unused ports
Disabling unused ports: This practice reduces potential vulnerabilities by limiting access points that could be exploited by attackers.
Network Access Control (NAC): Security controls for 802.1X networks - ensures only authenticated devices can connect to an 802.1X network.
Port forwarding/mapping
Port forwarding: Allows external devices to access services on a private network by redirecting traffic from an IP/specified port on the router to a designated port on a specific device, thus facilitating required communication while managing security risks.