Chapter 8
A student has set up a password for his laptop computer. The password he has chosen is Px2zY!Cg3?bd
(a) Discuss the benefits and drawbacks of using this password.
Benefits
It is a strong password
Hard to crack
More secure
Password is long therefore shoulder surfing is reduced
Does not contain personal information so harder to crack
Drawbacks
Easy to forget as it has many different characters
Even though it is still strong it is easy for a computer to crack
The user would have to look at the keyboard when entering the password
The user may have to write it down to remember it Letters and numbers could be confused… …such as 1 and I, 2 and Z, 5 and S
As it is long/complex it could be mis-typed
(b) The student could have protected his laptop computer by using two-factor authentication. This could have combined his password with a biometric method. State two examples of biometric methods he could use.
1 retina scan
2 Fingerprint
—> Iris scan, facial recognition, voice recognition
A company requires its employees to regularly change their login passwords for the company’s computer systems. Passwords must be strong and cannot be reused.
(a) Explain three problems that may occur when the employees change their passwords regularly
1 The passwords could become similar hence security/passwords could be weakened
2 May be more difficult to find a different password so the passwords/security could be weakened
3 Users could easily forget the current password leading to system lock out
—> It may be typed incorrectly as the password is like the previous one which could lead to login errors
—> Users may have to write the passwords down so they are not forgotten and this may lead to others seeing the passwords
(b) The company has a website which uses a digital certificate. Explain the purpose of the digital certificate.
To ensure a website is trusted/authentic/genuine
Verifies if the company owns the website
To share a public key for encryption when communicating with the website
(c) A digital certificate is attached to an email. State three items contained in a digital certificate.
1 Company/owner's name
2 Date issued
3 Expiry date
—> Owner's/company public key
—> Company/owner's digital signature
—> Issuer's/Sender’s name
—> Serial number
Two-factor authentication can use a number of different forms of identification. One form of identification is to use ‘where the user is’. An example of this would be the user’s GPS location.
(a) State two other forms of identification. Give an appropriate example of each
Form of identification: something the user owns:
Example: card reader / pen drive / dongle / mobile phone
Form of identification: something the user knows:
Example: password / PIN / TAN / email address / CVV on back of a credit card / answers to security questions
Form of identification: something the user has:
Example: biometrics
(b) Explain the purpose of two-factor authentication
To protect user’s data / credentials
To reduce the possibility of unauthorised access
Combines two different forms of identification
Makes it more secure by adding an extra layer of security
Social media can be used to communicate with friends. Give four precautions that young people should take when using social media.
Block/report unwanted users
Do not arrange to meet online strangers face to face
Do not meet people you do not know alone
Do not disclose personal data
—>Do not use your real name for the social media name, Do not post images that can link directly to you, Do not post inappropriate images, Do not use inappropriate language, Respect people's confidentiality/privacy, Set status to private
A student has downloaded a file which contains a virus.
(a) Describe the possible effects on his computer system if he opens the file
Pop up messages can appear on the computer screen
Causes the computer processing to slow down
Causes the computer to crash
Deletes/corrupts files/programs/data
(b) Explain how the student could prevent the computer from being infected by viruses.
Download/use up to date anti-virus software
Regularly scan the computer for viruses
Only open email attachments from people you trust
Scan all portable storage media before downloading files/software
(c) Some files containing viruses have to be quarantined as they cannot be deleted.
(i) State the type of files that may have to be quarantined rather than deleted.
System files
(ii) Explain how the software detects and quarantines the file.
Scan the computer for viruses
If a virus is found in the file it alerts the user that the file needs to be quarantined
Re-scan the computer to check for further viruses
Allows the user to accept/reject the quarantining of the file/
The file is moved to a hidden directory
The user does not have access to the quarantined file
Some confidential personal data can be classed as sensitive data.
Name three items of personal data that could also be sensitive data.
Ethnic/racial origin
Religion/philosophical beliefs
Political views/opinions
—> Membership of a political party, Membership of a trade union, Sexual orientation, Criminal record, Health/medical record, Genetic data/DNA, Biometric data
A student uses social media to keep in contact with other people. Describe four strategies that the student could use to stay safe when using social media to communicate with others.
Don’t give out other people’s personal information such as address or phone number
Don’t send inappropriate images to anyone
Don’t open/click on suspicious links/adverts on social media
Don’t become online ‘friends’ with people you do not know//don’t contact/chat to people you do not know
Never arrange to meet someone in person who you only met online
If anything you see or read online worries you, you should tell someone about it/block them
Use appropriate language
Set security so only friends can contact you
According to research carried out on passwords the top three most used passwords are 12345, qwerty and sunshine. Describe, using other examples, the difference between a weak password and a strong password.
Weak password is easy to guess
Weak passwords consist of all letters or all digits or all digits with one letter/all
letters with one digit/words found in a dictionary/Strong passwords use a
mixture of upper case, lower case, symbols and digits
Weak password is one that has less than 8 characters
Weak password has repeated characters
Weak password has characters next to each other on a QWERTY keyboard
Weak passwords are ones that are similar to the username
Weak passwords can use personal information
All of the examples given in the question are weak passwords
There have been major issues regarding the accuracy of facial recognition systems for identifying suspects by the police. Tawara Airport has installed biometric security including facial recognition systems to help the police recognise known criminals entering and leaving the country. Previously video was taken of all passengers and then checked manually.
(a) Discuss the effectiveness of using facial recognition systems rather than the manual video system to increase security in this way.
For
Face can be identified faster
Face can be identified by electronic comparison therefore relative higher level of accuracy
Facial recognition can uniquely identify individuals
Can automatically compare faces from older images
System can work continuously but a human checker would need to take breaks
Against
Dark glasses/facial hair/face coverings may cause the facial recognition systems to not work
More difficult to change biometric data
Recognising a person can be slower as more checking is carried out
Harder to set up the facial recognition system
Takes longer to add new people to the system
Biometrics can use a lot of memory to store the data
Intrusive as personal details have to be stored
More likely to be affected by the environment
With the video system each frame needs to be checked with known images which can lead to errors
(b) Give three examples of biometric data
Finger print
Hand print
Vein geometry
—> Retina, Iris, Speech/Voice
Instant messaging involves users sending text messages to each other. Evaluate how you would use eSafety strategies in your own use of instant messaging.
I block unwanted messages/suspicious users and report the sender
Before using the messaging system, I check how to block and report unwanted users, this stops predators
I never arrange to meet strangers alone
I always tell a responsible adult if I plan to meet someone
I always meet in a public place
I avoid giving away personal information
I report abusive messages from a sender of the messages
I report cyber-bullying
When sending messages I always use appropriate language
If someone messages me with private and personal information about themselves I respect their confidentiality/privacy
I always read carefully the messages before I send
I avoid sarcasm
I am not offensive when replying
I carefully check that I am replying to the correct person
I do not enable my location when messaging
Due to data protection laws, personal data should be kept confidential and secure. Explain why personal data should be kept confidential and secure.
The data will have the name/medical information attached therefore it needs protecting
The data is confidential as it links directly to the person
The data will be sensitive
To prevent blackmail/bullying from using medical results
To prevent fraud from using financial information
To prevent identity theft using contact details
To avoid the doctor’s surgery getting fined if it got made public
The doctor’s surgery’s reputation would suffer
Patients would lose trust
Workers in an office log onto the office computer network using a password. Aaron is using his name as his password.
(a) Give reasons why this is not a good idea.
Password is too short
Easy to guess
Contains personal information
Doesn’t contain a mixture of uppercase, lowercase letters, numbers, and
symbols
Contains repeated letters
(b) One method that hackers use to find people’s passwords is to install key-logging spyware onto computers. Give methods that could be used to safely enter passwords even if key-logging spyware has been installed on a computer.
Use drop-down lists
Use biometric passwords
Use one use tokens/OTP
Use a device instead of a password
As our use of the cloud increases, new ways of accessing it safely need to be developed. The use of typed passwords is being replaced by biometric methods.
Discuss the benefits and drawbacks of using biometric methods.
Benefits
Faster way of accessing systems
Cannot forget the biometric data
Must be physically at the device to access it
More secure as it uses unique data
Difficult to copy/forge
Drawbacks
Invasion of privacy
User may not know they have logged off
Biometrics may change therefore data will need to be kept up to date
Expensive method/technology to set up
Environment can affect measurements
Over usage can affect the measurements
Difficult to reset once compromised
Difficult to set up
Time consuming to set up as measurements must be taken
Facial coverings/changes can prevent system from working
An organisation has changed the way in which members of staff can enter the building. Previously they typed in a four-digit code on a keypad; now they use a device that reads a handprint.
Discuss the effectiveness of using a handprint to enter the building rather than keying in a code.
Positives
Data can be read/identified faster
Data can be read/identified by electronic comparison therefore relative higher
level of accuracy
Increases security as the hand is unique whereas a four-digit code easier to guess
Can’t forget your handprint, unlike a code
The person must be present to enter the building
Negatives
If the hand is damaged, then may not work
More difficult to change biometric data
Only works with one hand therefore difficult for right-handed people
Recognition could be slower as system is more complex
Harder to set up the biometric system
Takes longer to add new people/change biometric data to the system
Biometrics can use a lot of memory to store the data
Intrusive as personal details must be stored in biometrics
More likely to be affected by the environment
Handprint scans are an example of a biometric method to enter a building.
(b) Give other examples of biometric methods that could be used in this scenario.
Fingerprint
Vein geometry
Retina
Iris
Face
A teacher is concerned that students are playing online computer games at home without considering eSafety. The teacher is going to create a set of rules that he feels they should be following. Write down a list of eSafety rules that he could include
Do not give away personal information
Do not use your real name as your username
Do not use your face image as your avatar
If you receive messages from unwanted users block and report them
Do not meet unknown users in real life/use a chaperone
Do not give financial information to other users
If you receive unwanted and abusive messages report the sender of the messages
When sending messages always us appropriate language
Think before you reply to a message
Describe what is meant by the term encryption and why it is used.
what is meant:
Scrambling data
Changing plain text into cipher
Encryption converts text into a meaningless form
why it is used:
To prevent data/information from being understandable to people who
access/intercept the data
Protects data
Arjun can log directly into his office system from his home computer. The office system only requires users to enter their user id and a password
(a) Explain why this is not very secure.
User id and password can sometimes be easily guessed
Passwords can be hacked with key logging software
Passwords can be hacked by using random password generators
Others can see the details being typed in
If the home computer saves the log in information, then anyone can access
If the user does not logout, then others can access data
(b) Describe the other ways the office system could identify the user securely.
Way 1: One-use code/token
Arjun logs in then software generates a one-use code/token
Arjun enters the code/token into the system
Even if hacker intercepts code/token is no use as can only be used once
Token is time limited
Way 2: Card/dongle
The user has a dongle/card which is inserted into the computer
The dongle/card is read by the computer
The dongle/card data is unique
Way 3: Biometrics
Using biometric scanner to capture digital image of fingerprint/retina/iris/face
Each biometric is unique
Biometrics are nearly impossible to forge
Protocols are associated with the internet and an intranet. Identify the protocols and for each one, identify a use.
HTTP/HyperText Transfer Protocol
Transfer data between a webserver and the browser displays/loads pages/connect to a webpage
HTTPS/ HyperText Transfer Protocol Secure variant
Transfer data between a webserver and the browser securely//display/loads
secure pages//connect to a secure webpage
Secure variant of HTTP
FTP/File Transfer Protocol
Transfers files between computers/website
VOIP/Voice Over Internet Protocol
Makes phone calls over the internet
SSL/TLS
determines variables of the encryption for both the link and the data being transmitted
SMTP
Communication protocol for email
SLS
Protocol used on the internet
When customers shop online, they can pay using a debit card. Describe measures that customers could use to reduce fraud when using a debit card online.
Use up to date anti-spyware/anti-virus to stop phishing and pharming attacks
Using websites that encrypt data when sent/green padlock/use HTTPS/SSL
Ensuring that strong passwords are used
Passwords used for the online shopping account should be different to other passwords you use
Check all transactions carried out with the store/receipts
Type in the web address of the supermarket rather than copy and paste/click on links from an email
Do not buy from untrusted websites/apps
Ensure that the wireless password to the router is strong
Report any phishing attempts
Disable cookies/delete cookies frequently
Smishing, pharming and phishing are three security threats that can occur when using the internet for shopping. Tick whether the following statements refer to pharming, phishing or smishing
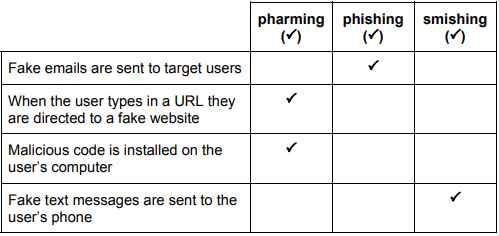
An employee in a company has used QWERTY123 as his login password for some time.
(a) Give three reasons why this is not advisable
Password is not strong
It is easy to guess
The letters and numbers are in sequence on the keyboard
Easy to shoulder surf
It should be changed regularly to secure his login
(i) A method which scrambles the data so that it cannot be understood is
Encryption
(ii) A fingerprint is an example of
Biometrics
(iii) A method of guaranteeing a website is authentic is
A digital certificate
(iv) A hardware device that filters the information coming through the Internet connection into a LAN is
Firewall
An employee in the company uses his company password for other accounts. Explain why this is not a good idea.
If someone finds the password for one of the systems/accounts other systems/accounts are compromised
If someone finds the password for one of the systems/accounts then he has gained the company password
A company’s computer system is protected by both a user ID and a password.
(a) Explain how a user ID and a password are used to increase the security of data
User IDs and passwords combined protect against unauthorised access.
Combined user ID and password is unique to the computer system.
The user ID ensures the correct account is accessed, the password then protects the account
If someone knew the user ID they could only gain access with the correct password
Typing in incorrect user ID/password a number of times could lock the user out
User IDs give different access levels in the computer system
User IDs are unique and allow the system manager to monitor usage on the system
The password is masked and displayed as stars
A strong password is a combination of upper and lower case characters/numbers/symbols
Passwords could be biometrics ensuring greater security
Passwords increase security as they are only known by the user
The company plans to improve the security of its computer system by using biometric methods. Describe what is meant by biometric methods. Give two examples of biometrics.
Description
Uses parts of the body/physical attributes as a password
Unique to the user
Form of authentication
Examples
Fingerprint
Retina
Voice
Face
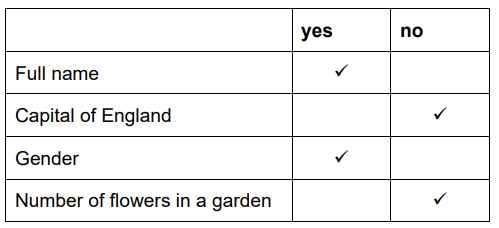
Tick (✓) whether the following are examples of personal data.
 The data stored on the computer system needs to be protected from unauthorised access. Discuss the effectiveness of different methods of increasing security of this data.
The data stored on the computer system needs to be protected from unauthorised access. Discuss the effectiveness of different methods of increasing security of this data.
Factors increasing effectiveness
Strong passwords are difficult to crack
Biometric passwords are harder to crack
Regularly changing passwords increases security
Use of two-factor authentication
Using different passwords for parts of the computer system makes it more
difficult to gain access to the full system
Firewall required to stop attacks from computers
Firewall stops fraudulent sites attacking the computer
Anti-spyware stops passwords being seen when typed in
Factors reducing effectiveness
Too complex a password can be easily forgotten
Passworded files may not be backed up
Using a number of different passwords can become cumbersome
Regularly changing passwords means that passwords may be forgotten
May be difficult to choose unique password if it is changed every few weeks
Passwords may become more easy to guess if regularly changed
Hackers can breach most passwords
The firewall can affect the operation of the computer and stop some uploads
The firewall may need to be shut down at times to upload files therefore making computer unsafe
Some legitimate software can be blocked by the firewall
To gain full marks both sides of the discussion are needed
Data stored on a computer system is at risk of being hacked.
Explain what is meant by the term hacking. Include in your answer two examples of the effects this can have on the computer system
Gaining unauthorised access to a computer system – 1 mark
Examples
Can lead to the identity theft of data
Can lead to the misuse of/access to personal data
Data can be deleted
Data can be changed
Data can be corrupted
Place malicious files/software
Describe the measures that could be taken to protect the data from being hacked
Use of firewalls to block unauthorised computer systems
Use of passwords
Use of intrusion detection software/anti-spyware
Use two-factor authentication
Switch off WiFi/computer when not in use
A common use of home computers is online gaming. Describe the e-Safety measures which should be taken when playing games on the internet.
Report/block cyberbullies
Respect other players
Check game ratings for age
Reduce the amount of time spent gaming
Be careful of in-app purchases
Turn on privacy settings
Don’t use your real name//use a nick name
Don’t give away personal information
In order to log onto online gaming a user ID and password is needed. Explain what is meant by a user ID and password and why they are needed
Max two from:
Part of the authentication system
Needed to improve security
Max three from:
Combined they are unique
User ID is an identifier for the user
Password is a string of characters
Passwords verify the user in the authentication process
 Many young people play online games. One problem with online gaming is that it is easy to give out personal details accidentally. Some users create weak passwords which could lead to their personal details being accessed.
Many young people play online games. One problem with online gaming is that it is easy to give out personal details accidentally. Some users create weak passwords which could lead to their personal details being accessed.
(a) Name two pieces of personal data that could be accessed
Email address
Real names
DOB
Home address
Contact phone number
Membership card number
Location data
Internet Protocol (IP) address
Picture of yourself
Gender
(b) Write down three rules that should be applied when setting a strong password
Password should not relate to personal details
Should be a long password
Not previously used password
Should not include repeating/obvious patterns//predictable words
Password should be strong
(c) Describe safety measures that should be taken by gamers to ensure their data is safe other than using strong passwords.
Use anti-spyware/up to date antivirus software
Play the games with the firewall operational
Play only with authorised versions of games which you have purchased from
the correct sources and for which you have a licence
Download/buy files and new software from reputable sources
Do not forget to delete your account details when you are not playing again
Keep the game software up to date.
When disposing of your gaming device ensure all of your personal information has been deleted.
Choose a username that does not reveal any personal information
Be aware of criminals buying or selling ‘property’ that exists inside a computer game, in the real world
Discuss the disadvantages of policing the internet.
Removes freedom of speech
International therefore would be difficult to police
Laws are different in each country/state
The dark net would increase
Electronic crimes would move away from the internet to other places, making
them harder to intercept
Internet users can be anonymous therefore it will be difficult to track down
Who chooses what is blocked could affect day to day browsing
Concern that everything you do is being watched therefore privacy is lost
Could be breaches in sending/receiving confidential/personal data as others
could not see it
Increase in cost of security
Reduction in speed of browsing/search
Could lead to corruption/bribery//police may use the data
No one owns the internet so it would be impossible to police effectively
Very expensive to police the internet as extra police force has to be set up
As the internet it so big it is hard to keep track on all the activity
As the internet is dynamic it would be impossible to check everything
The internet has both moderated and unmoderated forums. Explain what is meant by a moderated forum
Online discussion forum/social platform/website
Where the posts are controlled/monitored by an administrator
Those that break the rules are banned
Filters out inappropriate posts
Moderated forums have rules/policy
Students in Tawara College are using the internet to find information for a project. They have been told that the college has a firewall.
(a) Explain what is meant by a firewall and why it is used.
Two from:
Could be hardware or software
Sits between the computer/network and the router
Filters/controls/monitors data/traffic coming in and out of the college network
Four from:
Checks whether the data passing through it meets a given set of rules
Blocks data that does not satisfy the rules
Alerts user about unwanted data
Can log all incoming and outgoing data/traffic to check later
Can prevent/block access to undesirable/inappropriate websites/IP addresses
Keeps a list of undesirable IP addresses
Can prevent hackers gaining access to the system
Can send out warnings
Can block the unwanted traffic in and out of the network
Keeps a list of desirable IP addresses/websites
It can block IP addresses
The students visit different websites to get information for their project.
(b) Explain why it is not always easy for the students to find reliable information on the internet.
Anyone can post information on the internet
Websites may contain incorrect information
Any information found will need to be checked against reliable sources
Similar websites may have conflicting data on the same topic
The search engines tend to be generalised
Search engines do not necessarily give the most reliable searches at the top
of the list//paying to have information at the top of the list
Data on the website could be out of date
Complete the sentences below using the most appropriate word from the list.
cookies hacking pharming phishing smishing spam spyware virus
(a) The act of gaining unauthorised access to a computer system is called
Hacking
(b) The software that gathers data by monitoring key presses on a user’s keyboard is called
Spyware
(c) A fake text message, that could contain a link, sent to a mobile phone is called
Smishing
When an email is sent, it could have a digital certificate attached. Explain why a digital certificate is required. Include in your answer items that could be found in a digital certificate.V
Max four from:
Adds a level of security
Verifies the email comes from a known and trusted source
Provides the receiver with a means of reply/private key
Used for initialising secure SSL connections between web browsers and web servers
Max three from:
Details of the owner of the digital certificate
Serial number
Public key
Digital signature
Subject name
Valid from
Valid to//Expiry date
One way of communicating with other people is to use emails. It is very important that when you send and receive emails you are aware of esafety. Evaluate your own use of email in terms of esafety and describe the strategies you will need to minimise the potential esafety risks.
I never send personal data to people I do not know because people can use it against me as other people can access my personal details
I do not reply by using reply button unless I know the person because it may be a scam
I use a list of known email addresses so I don’t accidently send it to the wrong email address
I check before opening an email/email attachment because it might be a phishing attack
I scan both the email and attachment in order to avoid viruses
I never send images of myself to people I do not know so they cannot recognise me in the street
I do not set auto reply to my email system as this could alert a spammer that the email is active
I use email filtering this stops spam emails
I always report any phishing emails so the authorities can take action
I change my email password regularly so that others cannot access my email account
I use a strong password so that others cannot access my email account
I logout of email after I have finished using it to stop others gaining access to my emails
I keep my password safe so that others cannot access my account
A parent is concerned about his children sending texts. When sending a text, it is important to follow netiquette.
(a) Explain what is meant by the term netiquette.
Internet etiquette
Set of social conventions
They show common courtesy when communicating online
(b) The parent is planning to produce a number of rules to ensure that his children follow etiquette when texting other people.
Write down rules that he could include in his list.
Do not use capital letters as it relates to shouting
Do not use abusive/vulgar language/threatening behaviour
Be clear in the text sent
Always check spelling and grammar
Remember that sarcasm does not communicate well
Respect other’s privacy
Respect other people’s views
Do not use too many emoticons
Do not use text language/slang
Do not spam
Do not send inappropriate links
A company has placed a firewall between their Local Area Network (LAN) and their internet connection. This is used to increase security in their computer systems.
Discuss the effectiveness of using this firewall to increase security
Benefits
Monitors traffic into and out of the network to make sure that all data passing is safe.
Checks whether the data passing through it meets a given set of rules if they do not then the data is blocked
Can block the unwanted traffic in and out of the network
It can log all incoming and outgoing traffic to check later
Can block certain undesirable websites/IP addresses
Keeps a list of desirable IP addresses/websites
It can block IP addresses to stop hackers
Drawbacks
It cannot stop individuals on internal networks by-passing the firewall
It cannot stop employees hacking the computer from within the system
Users own devices can by-pass the firewall therefore meaning the
computer/network is in danger
It cannot stop hackers only devices that hackers are using
To gain full marks on the question at least one benefit and drawback are needed
Data stored in a computer needs to be protected. Describe what is meant by encryption.
This is the scrambling of data
Makes the data not understandable/meaningless
This system uses an encryption key to encrypt the data
This system uses an encryption/decryption key to decrypt the data
Protects sensitive data
There have been a number of incidents where laptop computers containing highly sensitive data have been left on trains. Manufacturers are now developing new ways of protecting laptop computers and their data. Discuss the effectiveness of different methods which could be used to protect the data.
Portable devices and cloud
Storing the data on a portable hard/SSD/Pen drive/cloud means that the device is with you at all times and not with the laptop computer
No data is stored on the laptop computer if a portable SSD/HDD/pen drive/cloud is used so if the laptop computer is stolen nothing is lost
If the pendrive is lost then all your data is lost
The access to the cloud can be password protected
If the laptop gets stolen the data will be safe on the cloud
Passwords and encryption
The data on the computer can be encrypted to increase security
Data can use strong passwords making it more secure
Passwords to the data can be forgotten and lost especially if the laptop password needs to be remembered
Security methods prevent users who do not know password from gaining access
Passwords could be difficult to remember which could lock the device
Physical security
Use of a dongle to log onto the laptop ensures that only the person with the
device gains access
Devices like pendrives/dongles tend to be small and can easily be lost/stolen
If the dongle is stolen/lost then access to the laptop is difficult
Security software may malfunction rendering the laptop impossible to access
Biometrics
Biometrics can be used to access the laptop/data this means that the user
needs to be present
Difficult to fake/replicate biometrics
Biometric data cannot be reset once compromised
Biometrics are unique therefore it is an added security method