Network Fundamentals and Communication in Daily Life
1/20
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
21 Terms
Network
A collection of interconnected devices that communicate with each other to share resources and information.
Data Networking
The practice of connecting computers and other devices to share data and resources over a network.
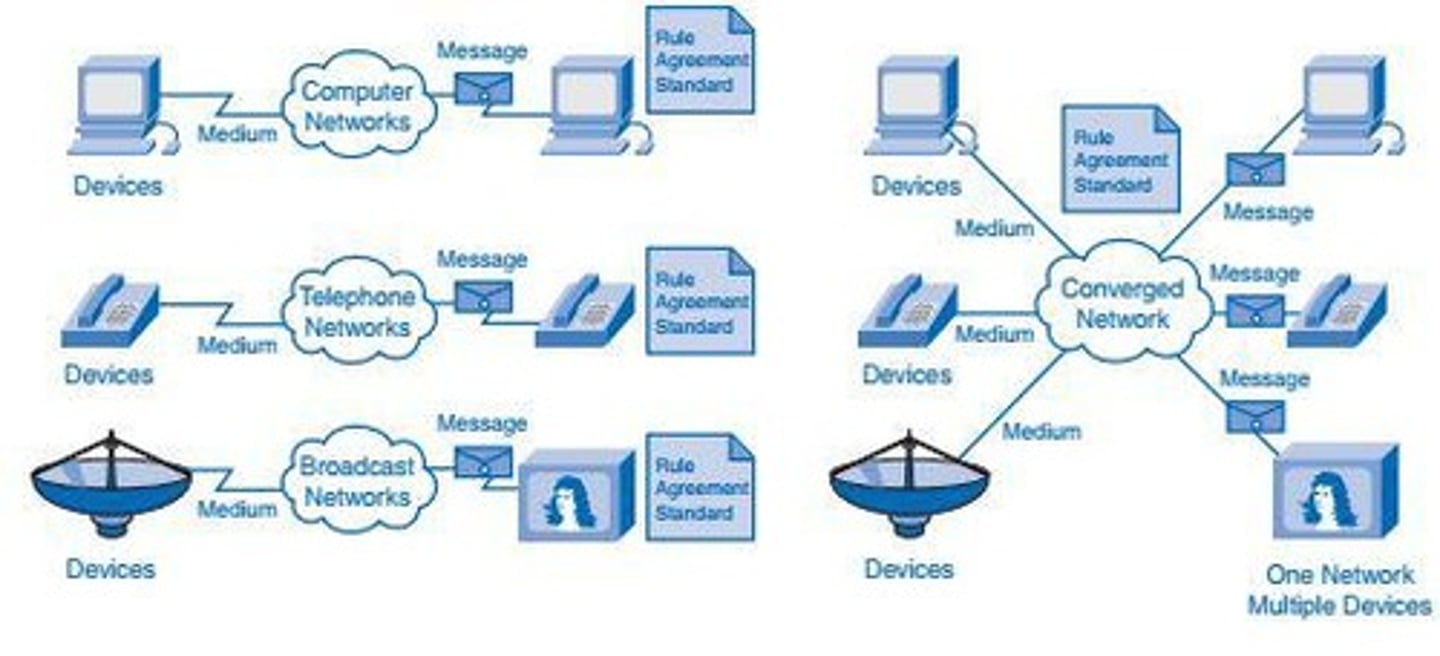
Converged Network
A network that integrates multiple types of data, voice, and video communications into a single infrastructure.
Fault Tolerance
The ability of a network to continue operating properly in the event of a failure of some of its components.
Scalability
The capability of a network to grow and manage increased demand without compromising performance.
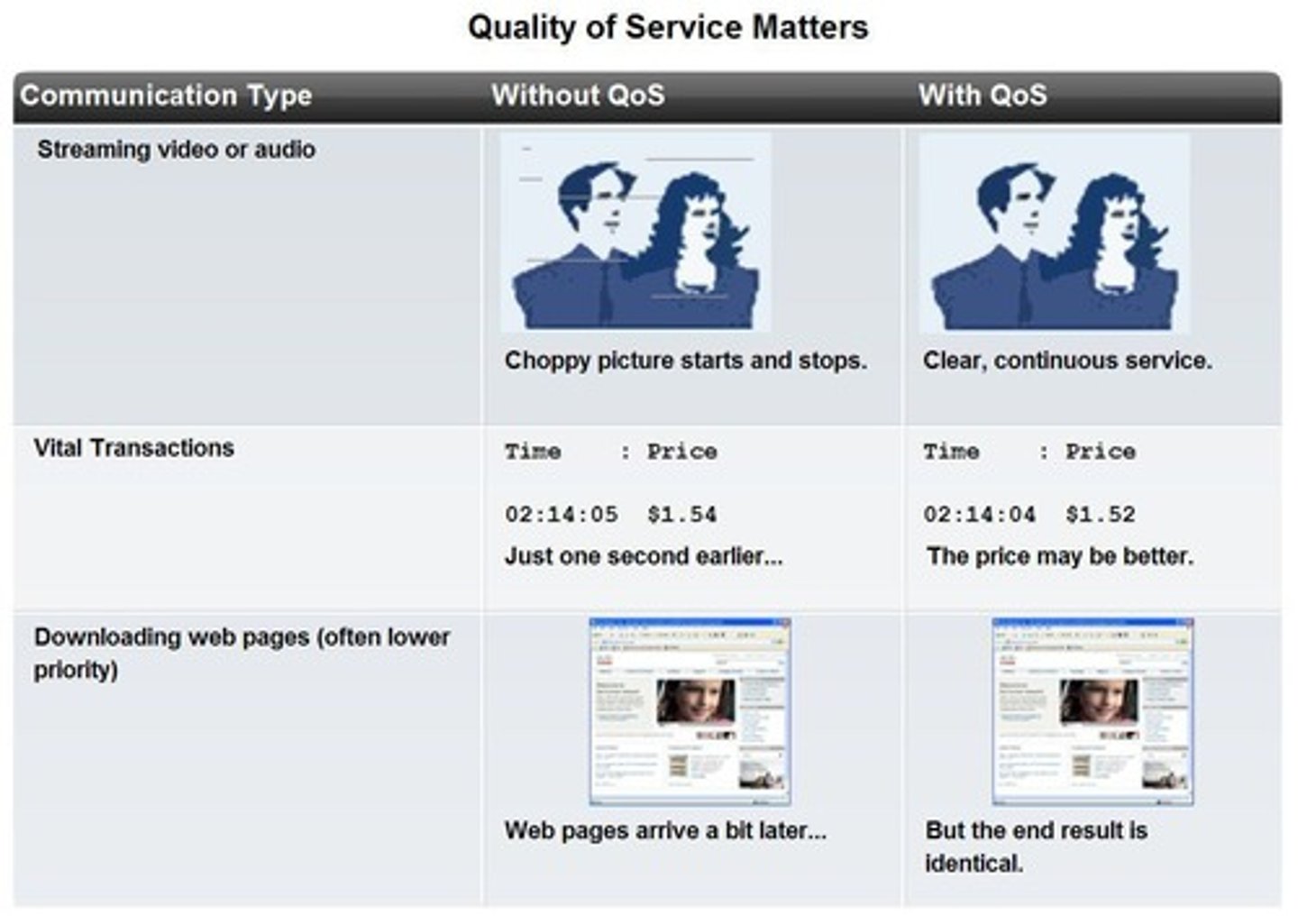
Quality of Service (QoS)
A set of technologies that manage data traffic to ensure a certain level of performance for specific applications.
Protocol
A set of rules that govern how data is transmitted and received over a network.
Instant Messaging (IM)
A form of real-time communication that allows users to send text messages to each other over the internet.
Weblog (Blog)
An online platform where individuals can publish their thoughts and opinions on various topics.
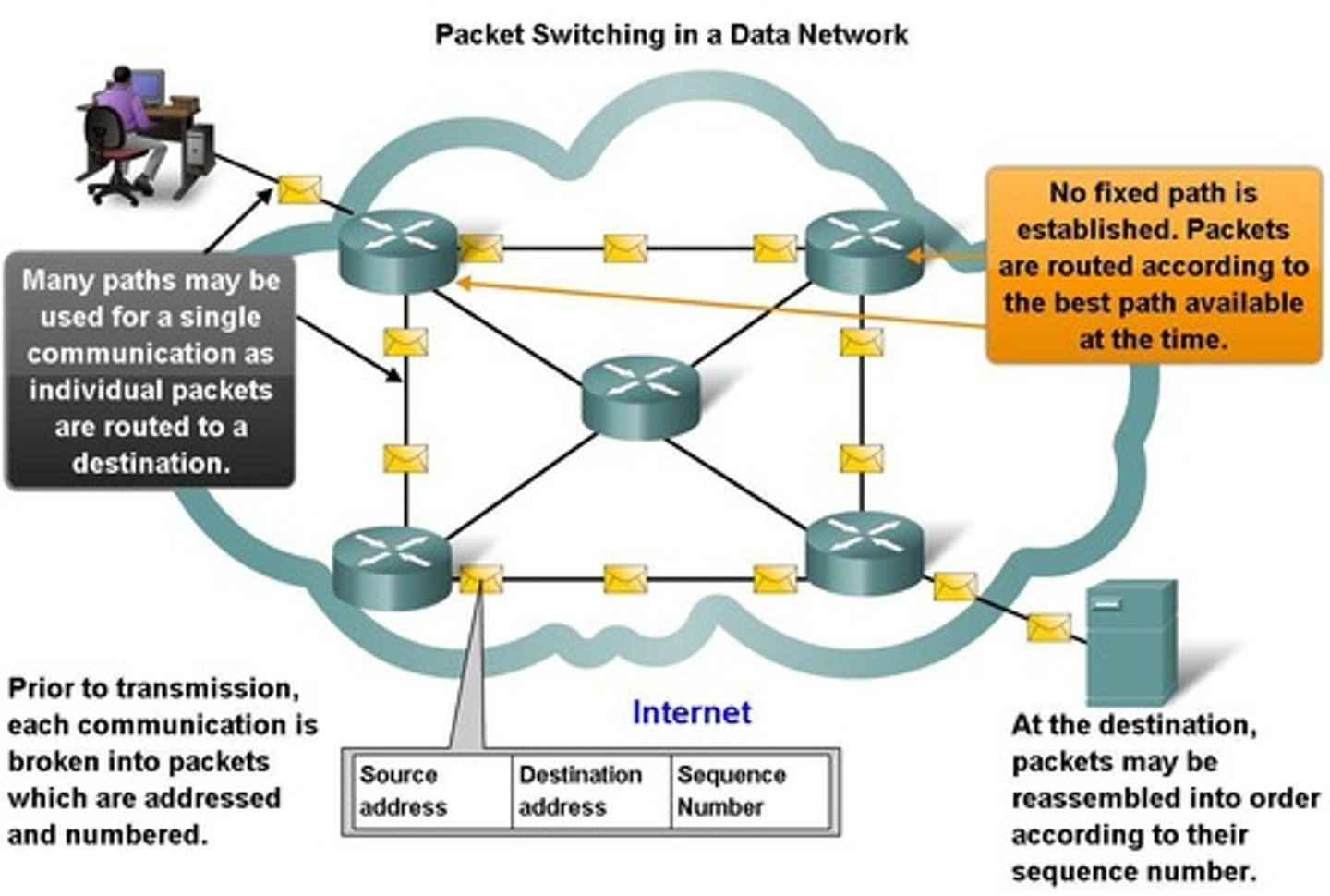
Packet Switching
A method of data transmission where messages are broken into packets that are sent independently over the network.
Medium
The physical or logical pathway through which data is transmitted in a network, such as copper cables or wireless signals.
Message
Information that is communicated over a network, which can take various forms such as emails, instant messages, or web pages.
Device
Any hardware component that is connected to a network, enabling communication and data exchange.
Security
Measures taken to protect data and resources in a network from unauthorized access and attacks.
User Authentication
The process of verifying the identity of a user before granting access to a network or system.
Data Encryption
The process of converting information into a code to prevent unauthorized access during transmission.
Digital Signature
An electronic signature that verifies the authenticity and integrity of a message or document.
Firewall
A network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Redundant Network Architecture
A design that includes additional components or pathways to ensure network availability in case of failure.
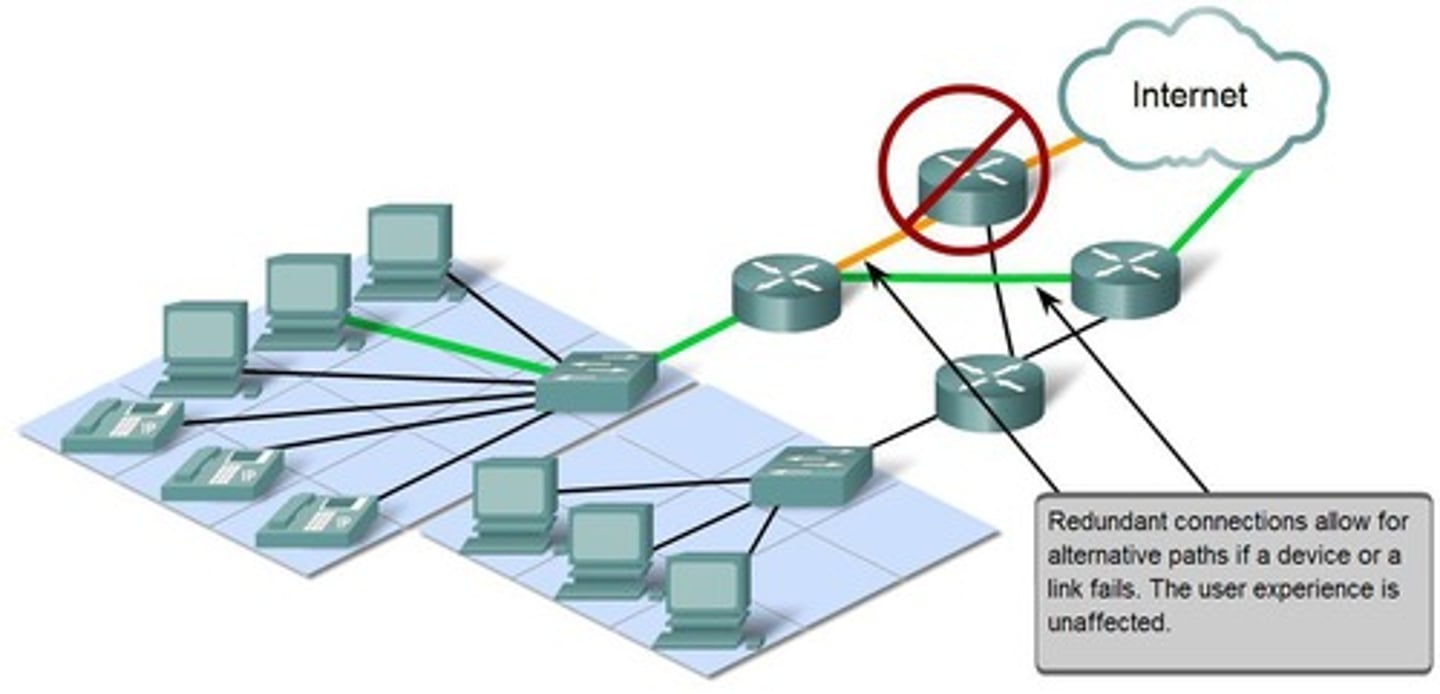
Hierarchical Network
A network design that organizes devices in a layered structure to improve scalability and management.
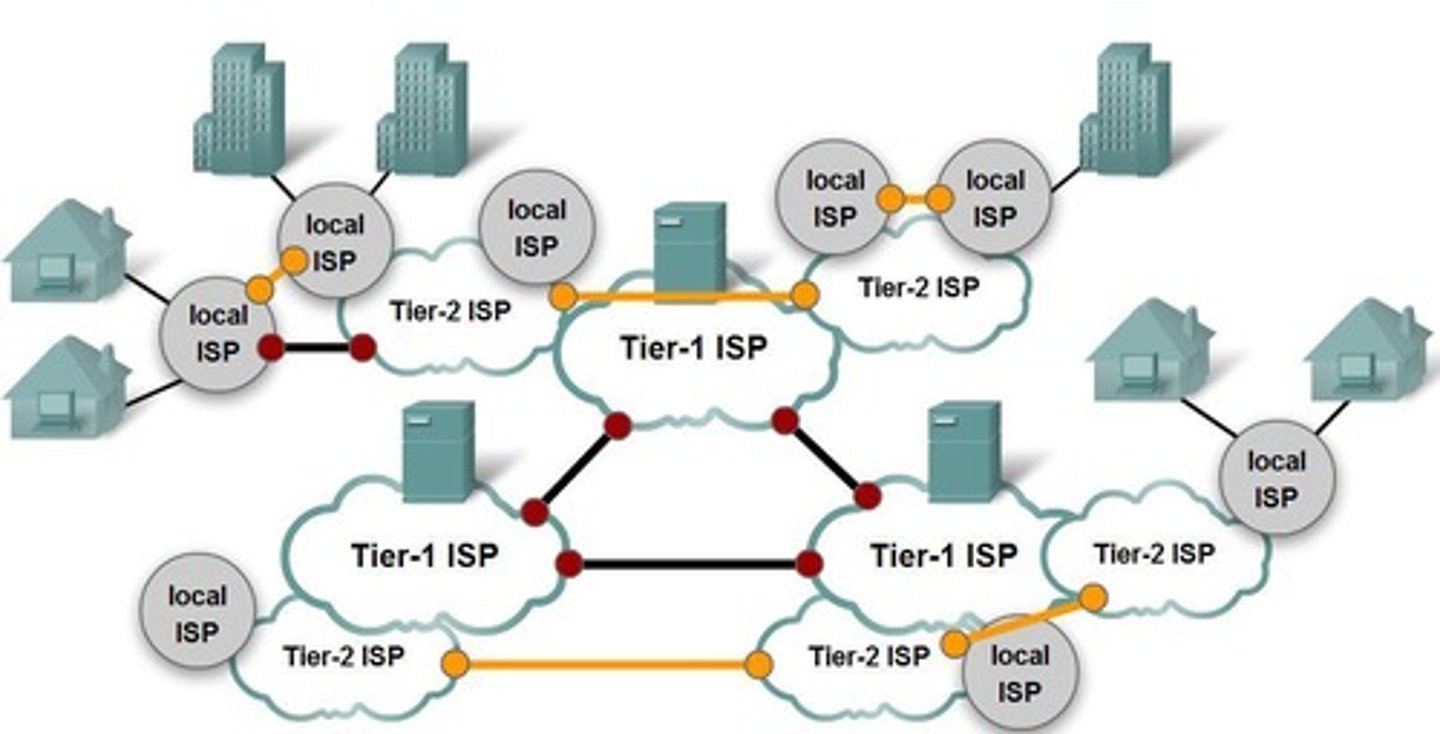
Common Standards
Agreed-upon specifications that ensure compatibility and interoperability between different network devices and protocols.