CS-239 Software Security Engineering
1/74
There's no tags or description
Looks like no tags are added yet.
Name | Mastery | Learn | Test | Matching | Spaced |
|---|
No study sessions yet.
75 Terms
Cybersecurity
Deals with the prevention and detection of unauthorised actions of a computer system
Measures taken to deal with intentional actions done by parties behaving in some unwelcome fashion.
Threat
Possible means by which desired security properties may be violated.
Vulnerabilities
Expose assets and their value to threats.
Security Controls
Protect against threats and vulnerabilities.
Confidentiality
Preventing unauthorized disclosure of information.
Privacy
Protection of personal data.
Integrity
Prevent unauthorized modification of information or service.
Availability
Prevent unauthorized withholding of information or resources.
Access Control
Prevent unauthorized access to data or resources.
Authentication
Prevent users from falsifying their identity.
Authorisation
Prevent users from violating their privileges.
Elapsed Time
The total time taken from identifying the vulnerability to exploit to develop a method to deliver an exploit, and to sustain this to ultimately launching an attack.
Specialist Knowledge Required
Specialist technical expertise required to realize a threat. This is the prerequisite level of widely available knowledge needed to realise the threat effectively.
Knowledge of the Target
Design and operational knowledge needed to execute a threat. This is related to the knowledge of the target (identified for exploitation).
Window of Opportunity
The level of access and the time window where the target is available (opportunity) for an exploitation to be carried out.
Equipment and Resources Needed
Hardware, software, or equipment required for exploitation. The cost, nature and sophistication of the equipment and resources needed to realise the threat.
Stealth
Purposefully designed/delivered threats avoiding detection.
Attribution
The process of identifying the source of an attack.
Risk-Based Approach
Output is a measure of the risk associated with the unwanted event.
Threat Analysis
Asset identification
Threat scenario identification
Attack path analysis
Risk Assesment
Impact rating
Attack feasibility rating
Risk value determination
Cybersecurity Goals
Risk treatment decision
Item Definition
A pre-requisite for performing a TARA, identifying item boundary, interfaces, functions, architecture, and operational environment.
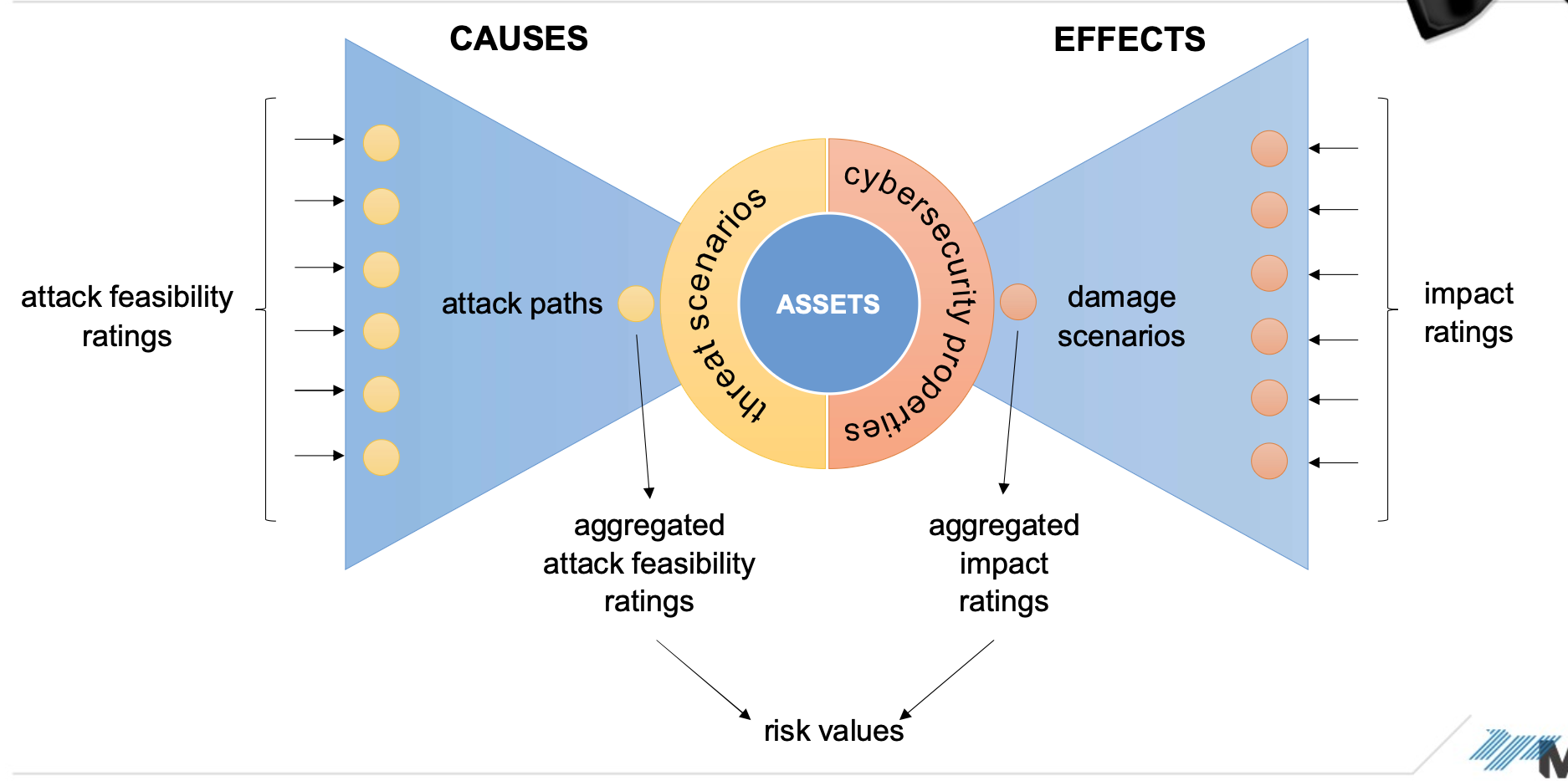
Asset
Object that has value, or contributes to value. An asset has one or more cybersecurity properties whose compromise can lead to one or more damage scenarios.
Cybersecurity Property
Attribute that can be worth protecting.
Damage Scenario (ISO/SAE 21434 definition)
Adverse consequence involving a vehicle or vehicle function and affecting a road user.
Threat Scenario
Potential cause of compromise of cybersecurity properties of one or more assets to realise a damage scenario.
How might an attacker compromise a cybersecurity property of an asset to achieve a damage scenario?
Spoofing (STRIDE)
A person or entity masquerades as another.
Tampering (STRIDE)
Insertion, modification, or deletion of data.
Repudiation (STRIDE)
An entity denies responsibility for an action.
Information Disclosure (STRIDE)
Provision or leak of information to an unauthorized entity.
Denial of Service (STRIDE)
Making a resource unavailable to authorized entities.
Elevation of Privilege (STRIDE)
An entity gains greater authorization than permitted.
Attack Paths
Represent the actions that could be taken by an attacker to realise a threat scenario.
Risk
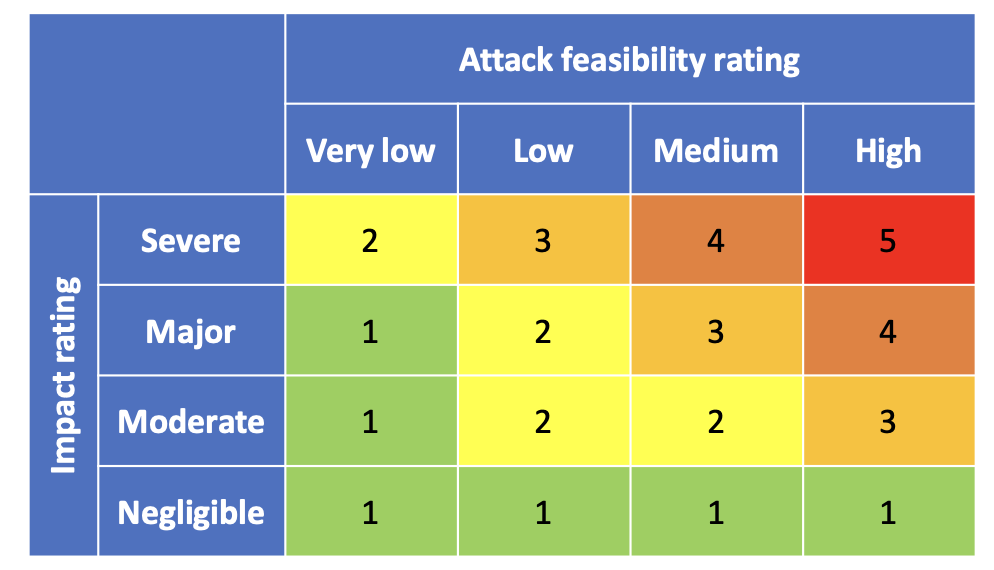
Risk is determined for a threat scenario as a combination of impact rating of the associated damage scenarios and attack feasibility rating of the associated attack paths.
Assessed by considering:
The impact of the unwanted event if it occurs
The likelihood of the unwanted event
Attack Potential
Indicates the cost or difficulty of a successful attack.
Impact Types (Risk Assessment)
Safety, Financial, Operational, and Privacy.
Impact Ratings (Risk Assessment)
Severe, Major, Moderate, and Negligible.
Risk Treatment Options (ISO 21434)
Avoid through redesign or remove a component or a feature in a system;
Reduce through security controls and mechanisms placed to reduce likelihood and/or impact;
Transfer or share the risk to another component or entity;
Accept the risk (along with any further appropriate measures such as monitoring).
Risk as Uncertainty
Systemic and inherent uncertainties leading to socio-technical vulnerability.
Residual Risk
Risk remaining once all mitigation is deployed for inherent risks.
Software Bug
Flaw or glitch in a system.
Security Testing
Software Evaluation against Security Requirements.
Static Testing
Review software development artifacts without executing them.
Dynamic Testing
Execute and Verify Software against expected behaviours from a finite set of Test Cases (test suite)
Vulnerability
A type of fault related to security properties.
Related to one or more assets and their corresponding security properties.
The existence means either missing or faulty security countermeasure(s) / mechanism(s).
Exploitation
malicious input/steps to make use of a vulnerability. Each vulnerability can have multiple exploitations.
Attack
perform an exploitation to violate related security property of an asset
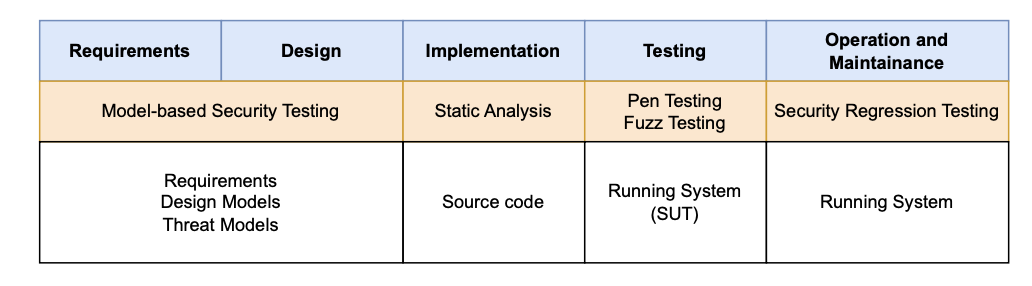
Model-Based [Security] Testing
Automatic and systematic generation of test cases from models of systems under test and their environments
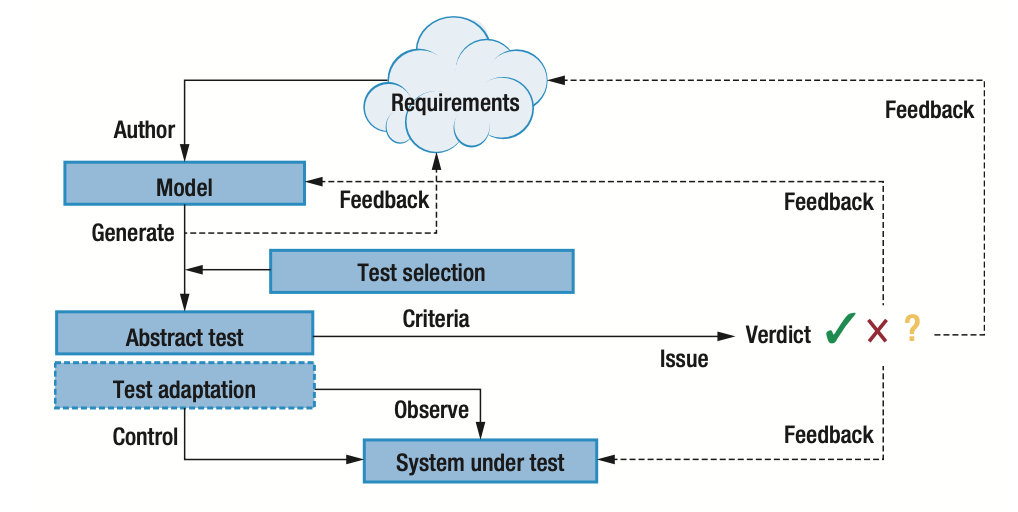
Abstract Test Cases
sequence of Attack Actions, pass if execution is not successful and fails otherwise
Coded-Base Security Testing
To detect vulnerabilities by examining the source code
Penetration Testing (Pen-Testing)
To mimic real-world attacks on real systems and data. To use tools and techniques commonly used by attackers. To circumvent the security features. To seek combinations of vulnerabilities on one or more systems to gain more access.
Fuzz Testing
Test system under stress with unexpected inputs and data structures through external interfaces.
Tainted Analysis
Tracking the propagation of tainted data through a program.
Security Threat
Possible means by which desired security properties may be violated
Security Control
A measure which can be put in place to address the security threat
Security Mechanism
Possible means to provide (implement) a security control
The V Model
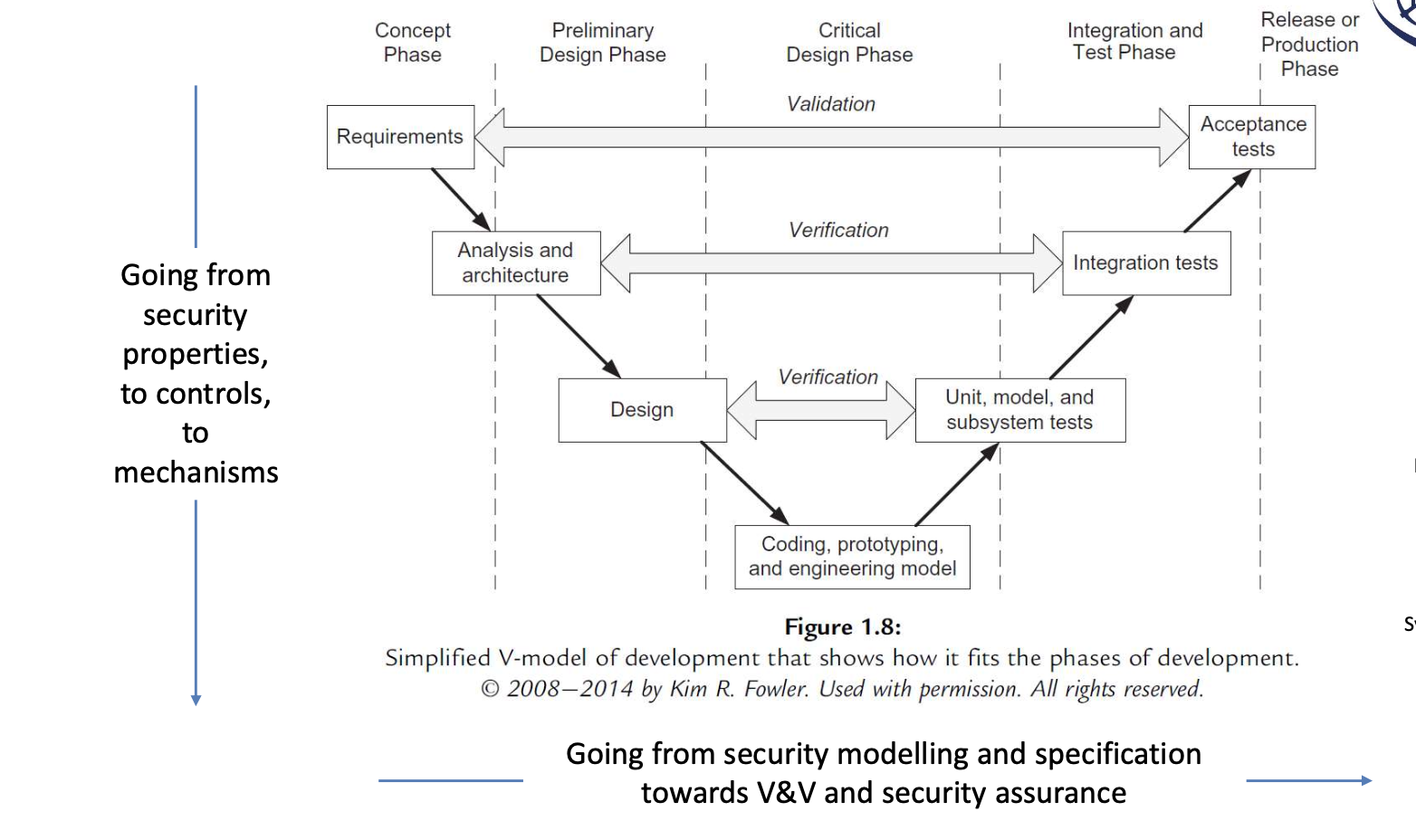
Security through the development cycle
Threat Analysis (Bowtie Model)
Threat Modelling
Determine the threats to the assets and how an attacker might realise those threats
WHERE in the system might the attacker target
WHEN in the vehicle lifecycle might the threat be realised
HOW might an attacker realise the threat
Asset Identification
A systematic approach that considers how an attacker might attack the system and how the system stakeholders are impacted
WHAT assets may be targeted, and what damage may occur
WHO are the potential attackers and stakeholders
WHY might they target the assets
Risk value determination matrix
Risk as potential threats
threats that are “definable, identifiable, immediate and often connected to specific threatening actors”
Safety-critical Systems
Typically functional integrity and availability properties leading to hazards.
Security-critical Systems
Information security aspects, typically as information flow and data theft.
Software Testing
Software Evaluation against (Functional/Non-functional) Requirements.
Security functional testing
To validate intended security functionality.
Do all intended security countermeasures function correctly? using well-defined expected inputs.
Security vulnerability testing
To identify unintended system vulnerabilities.
Does the system have any [known] vulnerabilities? using malicious, unexpected inputs.
Security Testers
play the role of a hacker to exploit system’s vulnerabilities.
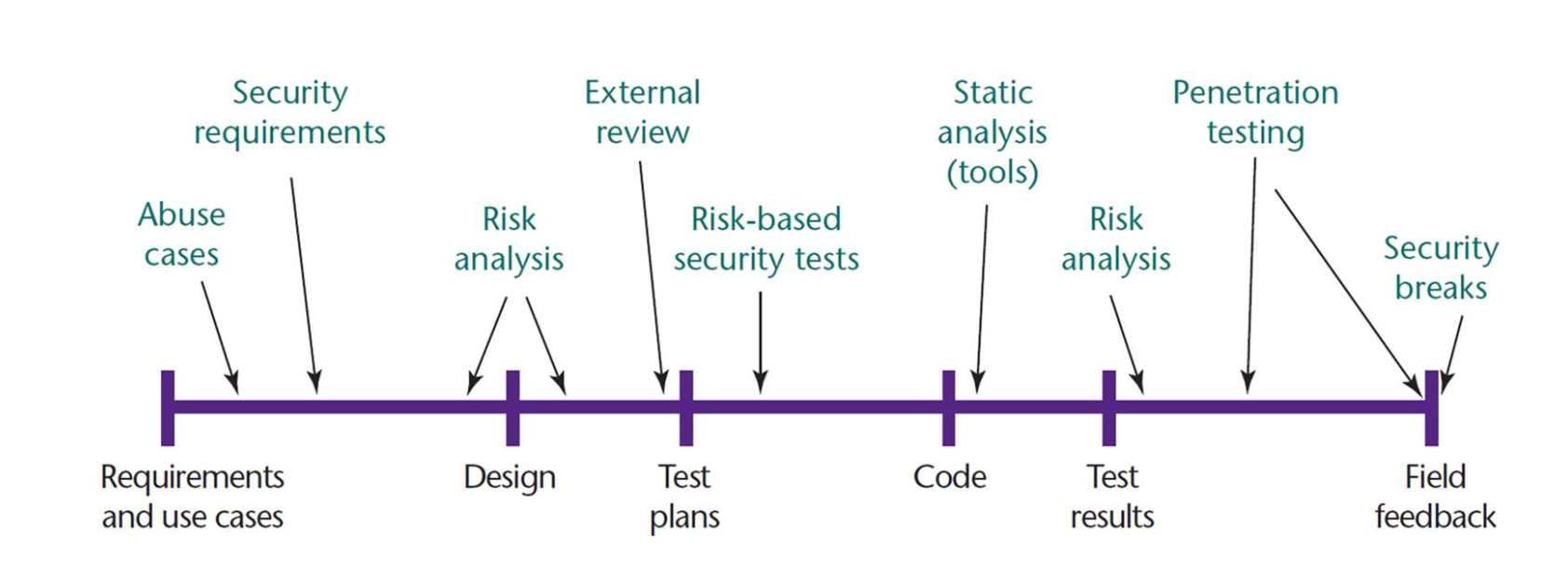
Security Testing Techniques in SDLC
MBT Benefits
Early and explicit review of system behaviours
Better documentation of test cases
The ability to automatically generate useful tests and measure, and optimise test coverage
The ability to evaluate and select regression test suites
Easier updates of test models and suites due to changes in requirements and designs
Higher test quality through model-based quality analysis
Shorter schedules and lower costs.
Manual Code Review
Expert to read source code line-by-line.
Static Application Security Testing
Syntactic checks: e.g., calling insecure APIs, using insecure configuration options.
Semantic checks: using models of data flow and/or control flow. E.g., SQL Injection vulnerability due to an unsanitised data flow from input to a SQL statement.
Pen-Testing Pros
Pen-testing helps determine:
The system tolerance under real-world attacks.
The level of sophistication an attacker needs.
Additional countermeasures to mitigate threats.
Defenders’ ability to detect and respond to attacks.
Pen-Testing Cons
Labour intensive.
Require great expertise.
Cause SUT (or even relevant systems) damaged or inoperative.
Need careful consideration, notification and planning.
Liability
should be assigned to the party involved that is best placed to manage the cybersecurity risk.